|
|
原文链接:安卓逆向 -- POST数据解密
一、通过上几节课我们知道要找的加密数据如下
{"Encrypt":"NIszaqFPos1vd0pFqKlB42Np5itPxaNH\/\/FDsRnlBfgL4lcVxjXii4KhogG\/C4u8yj2BCWdrDBlE\nm\/tlCFbgkTeVrEwGYpBtmuwEYeSFr7zfAr\/2Gtv7Sw4Wz9u3unWuTw34VLT\/1mbgDILNi9D8Ajku\nTRKnYuVNl7sINjvCbcAvBfcj8kJLeTyot7GVH4h6jQw\/BzC5GW2wjO91F0AFa8fEr\/g\/8gYnisBB\n3gxZ5J8=\n"}
二、通过动态调试时,知道v2存放了加密值
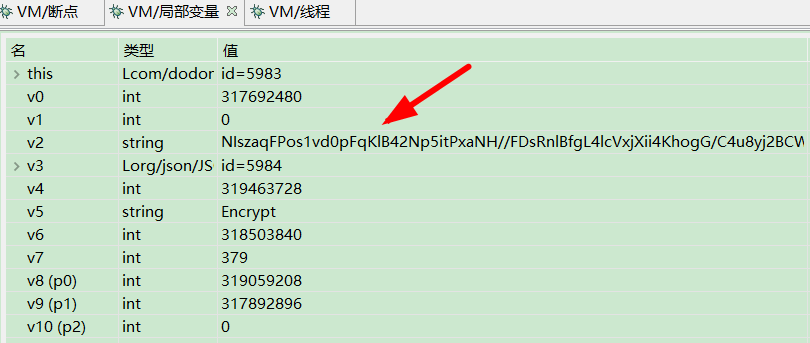 
三、在smali代码处,按table键,切换到java代码,把鼠标移动到encrypt处会看到加密后的结果
 
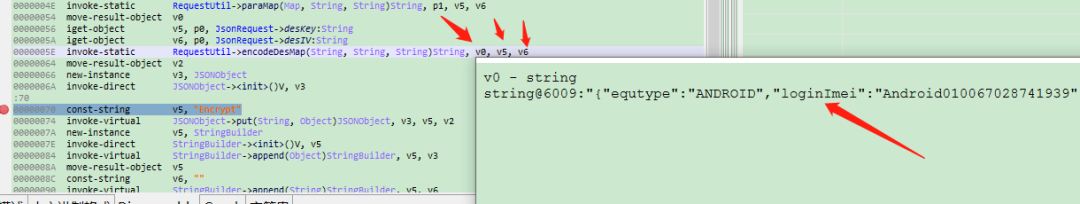
四、看到deskeye,desIV,基本可以判断是des加密方式,返回smali代码,v0是明文,v5和v6正好对应deskkey和desIV
- v5="65102933"
- v6="32028092"
- v0={"equtype":"ANDROID","loginImei":"Android010067028741939","sign":"F89CAB514B907A69CFE0A476EEF4AD32","timeStamp":"1628078089688","userPwd":"123456","username":"15836353612"}
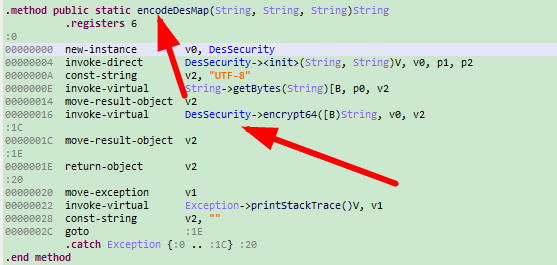
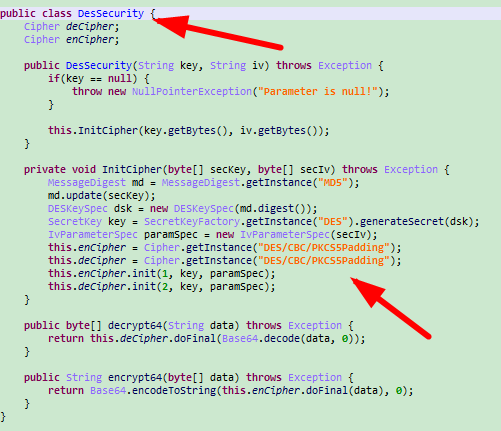
五、双击encodeDESMap进入,再双击DESSecurity进入,按table切换到java代码,是CBC模式的DES加密,key进行了一次md5,
六、最后提交的的加密内容(需要JS加密库),下面还需要分析sign值
- function jimitj(user, pass) {
- var time = new Date().getTime();
- var sign = getSign(user, pass, time);
- var mw = '{"equtype":"ANDROID","loginImei":"Android359250050380441","sign":"' + sign + '","timeStamp":"' + time + '","userPwd":"' + pass + '","username":"' + user + '"}';
- var key=CryptoJS.enc.Hex.parse(CryptoJS.MD5('65102933').toString());
- var iv=CryptoJS.enc.Utf8.parse('32028092');
- var res= CryptoJS.DES.encrypt(mw,key,{
- iv:iv,
- mode:CryptoJS.mode.CBC,
- padding:CryptoJS.pad.Pkcs7
- }).toString();
- return res;
- }
七、sign值代码(需要JS加密库)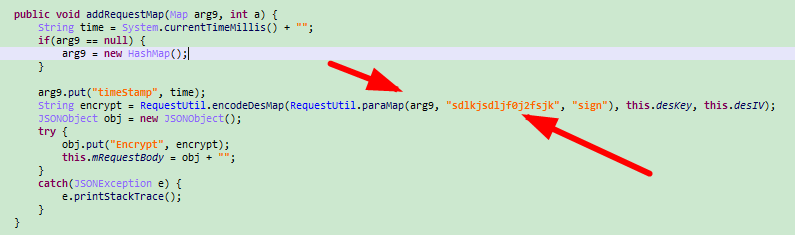 
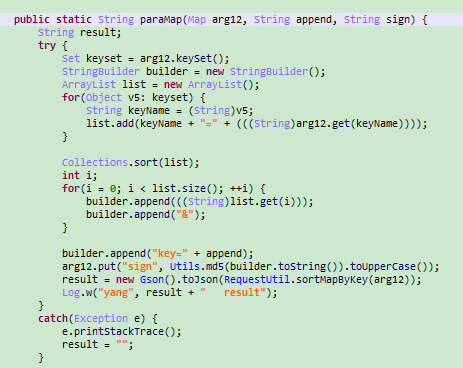 
- function getSign(user,pass,time){
- var signstr="equtype=ANDROID&loginImei=Android359250050380441&timeStamp="+time+"&userPwd="+pass+"&username="+user+"&key=sdlkjsdljf0j2fsjk";
- return CryptoJS.MD5(signstr).toString().toUpperCase();
- }
|
|