|
|
原文链接:内网渗透-判断内网连通性
判断内网的连通性是指判断机器能否上外网等。需要综合判断各种协议(TCP、HTTP、DNS、ICMP等)及端口通信的方式。
查看本机防火墙规则netsh advfirewall firewall show rule name=all
基于ICMP协议使用ping命令:
ping <IP地址或域名>
TCP协议netcat(简称nc)被誉为网络安全界的”瑞士军刀”,是一个短小精悍的工具,通过使用TCP或UDP协议的网络连接读取数据。
使用方法:
nc -zv <IP地址 端口号>
Windows机器不自带nc,因此在Windows机器上需要使用Telnet,而Telnet也需要我们自己开启。
Windows10下开启Telnet命令:
- #开启
- dism /online /Enable-Feature /FeatureName:TelnetClient#关闭
- dism /online /Disable-Feature /FeatureName:TelnetClient

Telnet使用方法:
telnet <IP地址 端口号>
UDP协议使用脚本 Test-PortConnectivity.ps1
下载地址:https://gist.github.com/PrateekKumarSingh/61532b4f48edac1d893b
- #Test-PortConnectivity -Source '127.0.0.1' -RemoteDestination 'dc1' -Port 57766#Test-PortConnectivity '127.0.0.1' 'dc1' 57766 -Protocol UDP -Iterate#Test-PortConnectivity 'localhost' 'dc2' 51753 -Protocol UDP#Test-PortConnectivity -Source $EUCAS -RemoteDestination $EUMBX -Port 135 -Iterate#Test-PortConnectivity -Source 'localhost' -RemoteDestination '127.0.0.1' -Port 135 -Iterate -protocol TCPFunction Test-PortConnectivity(){Param(
- [Parameter(Position=0)] $Source,
- [Parameter(Mandatory=$true,Position=1)] $RemoteDestination,
- [Parameter(Mandatory=$true,Position=2)][ValidateScript({
-
- If($_ -match "^[0-9]+$"){
- $True
- }
- else{
- Throw "A port should be a numeric value, and $_ is not a valid number"
- }
- })
- ]$Port,
- [Parameter(Position=3)][ValidateSet('TCP','UDP')] $Protocol = 'TCP',
- [Switch] $Iterate
- )
- #If $source is a local name, invoke command is not required and we can test port, withhout credentials
- If($Source -like "127.*" -or $source -like "*$(hostname)*" -or $Source -like 'localhost')
- {
- Do
- {
- Telnet-Port $RemoteDestination $Port $Protocol;
- Start-Sleep -Seconds 1 #Initiate sleep to slow down Continous telnet
- }While($Iterate)
-
- }
- Else #Prompt for credentials when Source is not the local machine.
- {
- $creds = Get-Credential
- Do
- {
- Foreach($Src in $Source)
- {
- Invoke-command -ComputerName $Src -Credential $creds -ScriptBlock ${Function:Telnet-Port} -ArgumentList $RemoteDestination,$port, $Protocol
- }
- #Initiate sleep to slow down Continous telnet
- Start-Sleep -Seconds 1
- }While($Iterate)
-
- }}
- Function Telnet-Port($RemoteDestination, $port, $Protocol){
- foreach($Target in $RemoteDestination)
- {
- Foreach($CurrentPort in $Port)
- {
- If($Protocol -eq 'TCP')
- {
-
- try
- {
- If((New-Object System.Net.Sockets.TCPClient ($Target,$currentPort) -ErrorAction SilentlyContinue).connected)
- {
- Write-host "$((hostname).toupper()) connected to $($Target.toupper()) on $Protocol port : $currentPort " -back green -ForegroundColor White
- }
- }
- catch
- {
- Write-host "$((hostname).toupper()) Not connected to $($Target.toupper()) on $Protocol port : $currentPort" -back red -ForegroundColor white
- }
- }
- Else
- {
-
- #Create object for connecting to port on computer
- $UDPClient = new-Object system.Net.Sockets.Udpclient
-
- #Set a timeout on receiving message, to avoid source machine to Listen forever.
- $UDPClient.client.ReceiveTimeout = 5000
-
- #Datagrams must be sent with Bytes, hence the text is converted into Bytes
- $ASCII = new-object system.text.asciiencoding
- $Bytes = $ASCII.GetBytes("Hi")
-
- #UDP datagram is send
- [void]$UDPClient.Send($Bytes,$Bytes.length,$Target,$Port)
- $RemoteEndpoint = New-Object system.net.ipendpoint([system.net.ipaddress]::Any,0)
-
- Try
- {
- #Waits for a UDP response until timeout defined above
- $RCV_Bytes = $UDPClient.Receive([ref]$RemoteEndpoint)
- $RCV_Data = $ASCII.GetString($RCV_Bytes)
- If ($RCV_Data)
- {
-
- Write-host "$((hostname).toupper()) connected to $($Target.toupper()) on $Protocol port : $currentPort " -back green -ForegroundColor White
- }
- }
- catch
- {
- #if the UDP recieve is timed out
- #it's infered that no response was received.
- Write-host "$((hostname).toupper()) Not connected to $($Target.toupper()) on $Protocol port : $currentPort " -back red -ForegroundColor White
- }
- Finally
- {
- #Disposing Variables
- $UDPClient.Close()
- $RCV_Data=$RCV_Bytes=$null
- }
- }
- }
- }}

使用方法:
powershell -exec bypass -command "& {import-module C:\Users\GU\Desktop\Test-PortConnectivity.ps1; Test-PortConnectivity 'localhost' '127.0.0.1' 7777 -Iterate -protocol UDP}"
我们先在本机使用ncat开启udp监听,再运行此脚本。
 
只要监听处出现Hi字样,即表示连通。
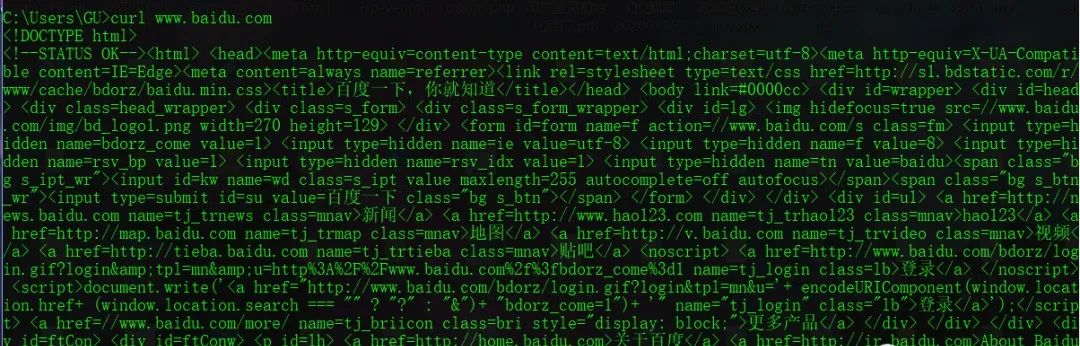
HTTP协议使用工具curl,有的Windows自带curl,有的需要自己安装。
使用方法:
curl www.baidu.com
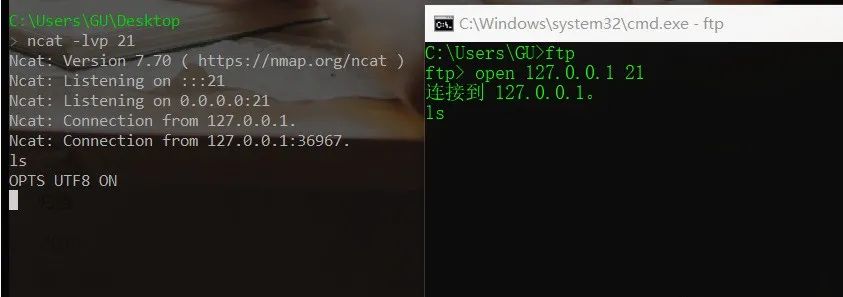
FTP协议远程开启21端口,并使用ftp连接。
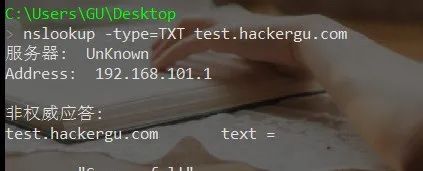
DNS协议Windows下使用nslookup,linux下还可以使用dig。
#Windowsnslookup www.baidu.com#Linuxdig www.baidu.com
或者给自己加一个txt记录
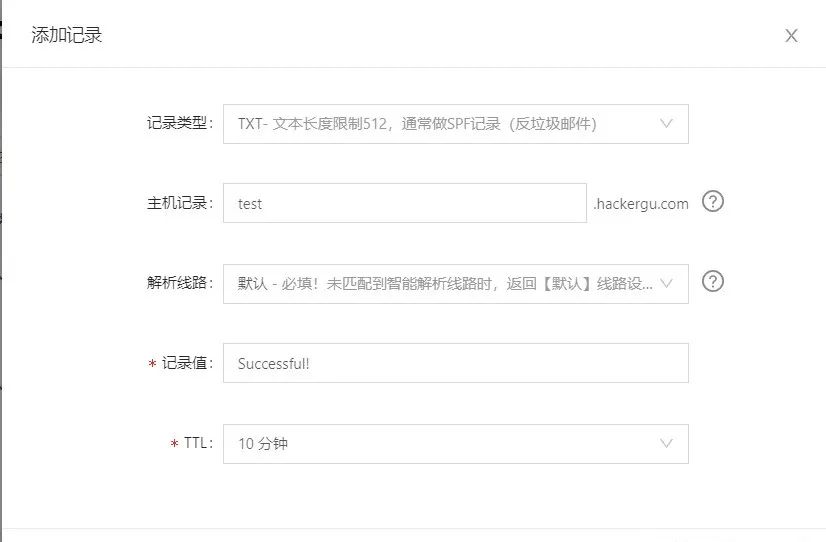 
使用命令:
nslookup -type=TXT test.hackergu.com
利用工具查看开放端口HostRecon
下载地址:https://github.com/dafthack/HostRecon
使用命令:
Import-Module .\HostRecon.ps1Invoke-HostRecon -Portscan -TopPorts 128
代理服务器在内网中的机器,也可能是通过代理连接内网。
检查方法:
- 查看内网中,与其他机器的网络连接。
- 查看内网中是否有主机名类似于proxy的机器。
- 根据pac文件的路径,将其下载下来并查看。
- 执行如下命令,进行确认。
curl -x proxy-ip:port www.baidu.com
|
|