|
|

楼主 |
发表于 2021-11-19 09:59:25
|
显示全部楼层
已知P高位:
[对RSA-Factoring with High Bits Known理解](https://www.jianshu.com/p/1a0e876d5929)
这篇文章把原理讲解了,我只会用脚本,格基规约还在学习中.....
以这道CTF题目为例:
- from Crypto.Util.number import *
- import binascii
- import gmpy2
- flag = '*****************************************'
- hex_flag=int(flag.encode("hex"),16)
- p=getPrime(256)
- q=getPrime(256)
- n=p*q
- e=getPrime(100)
- c=pow(hex_flag,e,n)
- p=((p>>60)<<60)
- print("n=",hex(n))
- print("p=",hex(p))
- print("e=",hex(e))
- print("c=",hex(c))
- '''
- ('n=', '0x558477ce1d081f831cfa159290ee4fd14888422c216a16ad86e2b2d4335e3cb18ed0120a955f970b17b229a8e7d0ae1b6f0c40213ad0e127eba99ae0d8a82397L')
- ('p=', '0x8fbcbb7d1e9f393ee21b537d6e0bd2cf8629e315f4e356c1e000000000000000L')
- ('e=', '0xf7278179324b11fd83d08aa6fL')
- ('c=', '0x36e1c09ccad45cd63a0f07e704d3811c39d70cdfdad999d2df90255a76c58cf6fe99ac1ab1d5d99a4ce1a2ebdbfbc49ce72df2a0b90766ff84ab0ef62068d46bL')
- '''
[在线运行sage](https://sagecell.sagemath.org/)
- n = 0x558477ce1d081f831cfa159290ee4fd14888422c216a16ad86e2b2d4335e3cb18ed0120a955f970b17b229a8e7d0ae1b6f0c40213ad0e127eba99ae0d8a82397L
- p_fake = 0x8fbcbb7d1e9f393ee21b537d6e0bd2cf8629e315f4e356c1e000000000000000L
- # pbits = p_fake.nbits()
- pbits = 256
- kbits = 60 #p失去的低位
- pbar = p_fake & (2^pbits-2^kbits)
- print("upper %d bits (of %d bits) is given" % (pbits-kbits, pbits))
-
- PR.<x> = PolynomialRing(Zmod(n))
- f = x + pbar
-
- x0 = f.small_roots(X=2^kbits, beta=0.4)[0] # find root < 2^kbits with factor >= n^0.3
- p= x0 + pbar
- print(p)
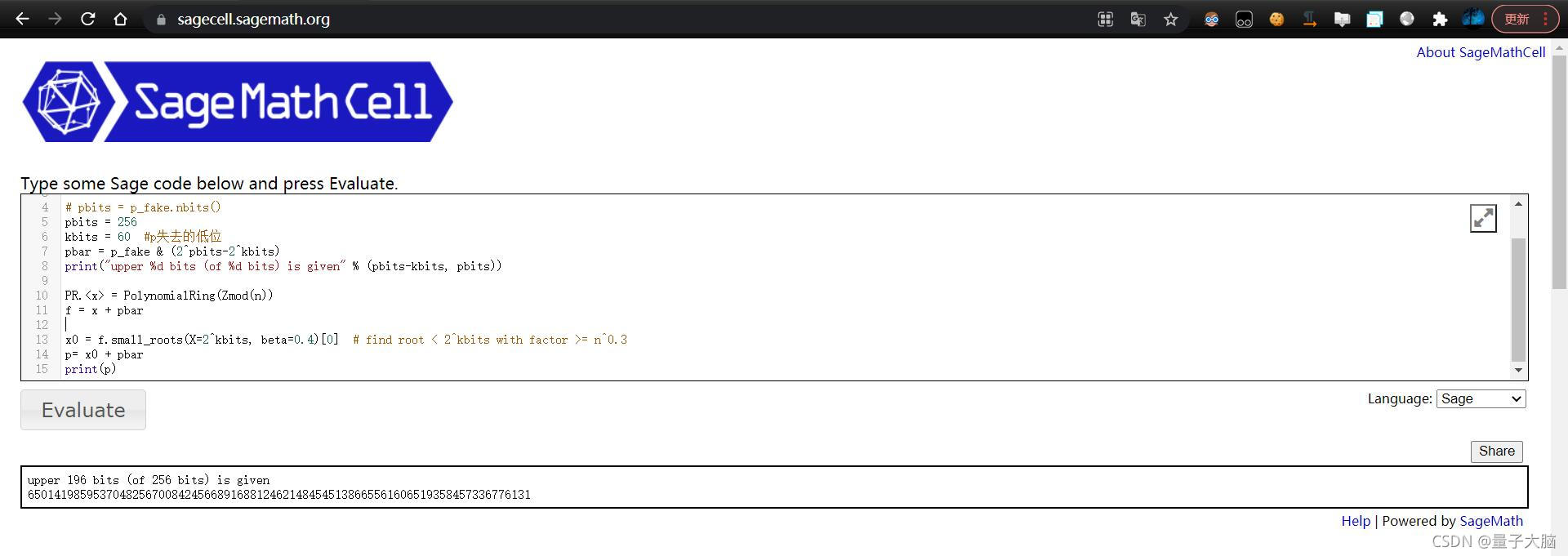 
这样就得到了p,接下来就是常规解题了:
- from Crypto.Util.number import *
- import gmpy2
- import binascii
- # from sage import *
- n = 0x558477ce1d081f831cfa159290ee4fd14888422c216a16ad86e2b2d4335e3cb18ed0120a955f970b17b229a8e7d0ae1b6f0c40213ad0e127eba99ae0d8a82397
- p = 65014198595370482567008424566891688124621484545138665561606519358457336776131
- e = 0xf7278179324b11fd83d08aa6f
- c = 0x36e1c09ccad45cd63a0f07e704d3811c39d70cdfdad999d2df90255a76c58cf6fe99ac1ab1d5d99a4ce1a2ebdbfbc49ce72df2a0b90766ff84ab0ef62068d46b
- pp = binascii.b2a_hex(long_to_bytes(p)).decode()
- print(pp)
- ppp = 0x8fbcbb7d1e9f393ee21b537d6e0bd2cf8629e315f4e356c1e7c5e22d8cff45c3
- q = n // ppp
- phi = (ppp-1)*(q-1)
- d = gmpy2.invert(e, phi)
- m = pow(c, d, n)
- print(long_to_bytes(m))
|
|